In today’s cyber attack scene, data often takes a detour – straight through hackers’ systems. Unlike phishing or ransomware, which aim to trick users into handing over credentials or stealing data directly from systems, a Man-in-the-Middle (MitM) attack involves an unseen intermediary trying to fool each of two parties into thinking he’s the other one, capturing and/or altering information communicated between the parties, etc.
Attackers can intercept web sessions, such as between a user and an online payment service, data transferred between machines, applications, or virtual/physical servers, and so on. Imagine you’re wiring a large payment to a trusted supplier, but an outsider intercepts the transaction and subtly alters the bank details. You think the payment is secure, but it’s being diverted to a criminal’s account. This is one example of a MiTM attack in action.
What is a Man-in-the-Middle (MITM) Attack?
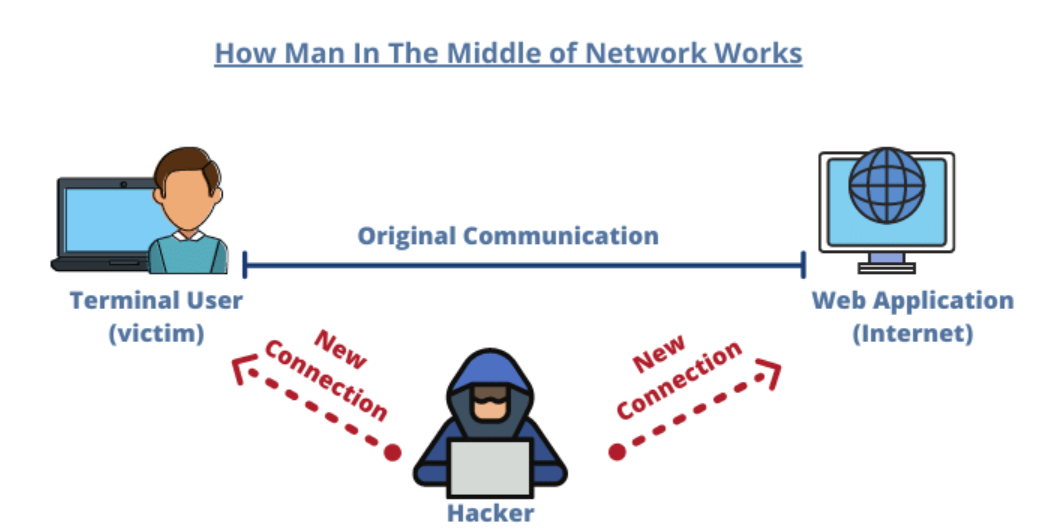
MiTM attacks accounted for 23% of identity-related cyber incidents in 2024. Their ghostly nature makes them easy to underestimate – but you shouldn’t. MiTM attacks can lead to several nefarious actions, from large-scale fraud to account takeovers (ATOs) and financial losses. Implementing effective strategies to prevent these attacks is crucial to protecting your business and customers.
For the bad actor, the critical part of the attack is finding a way to intercept communication. Attackers exploit network vulnerabilities, tricking people into connecting to compromised networks (e.g., by copying the name of nearby Wi-Fi networks) or redirecting a user to a fake website that mirrors a legitimate one (for example, by manipulating DNS traffic). Over time, attacks have grown in complexity, from eavesdropping via unencrypted Wi-Fi networks to exploiting network protocols and targeting APIs.
MitM attacks are not only about stealing sensitive information or manipulating messages; they can also involve injecting malicious content into communications, or impersonating individuals in digital interactions, like social platforms or dating apps, leading victims into potentially harmful situations.
As an example, a news story from April 2024 revealed how an Indian antivirus service delivering user updates via HTTP was targeted by a cybercrime gang that performed MiTM attacks. The hackers would hijack antivirus update files, manipulate them, and use them to install malware on user systems.
Several Types of Man-in-the-Middle Attacks
1. Email Hijacking
In the context of MitM attacks, email hijacking involves intercepting communications between two parties via email without accessing either party’s email account. Attackers employ various tactics, such as spoofing email addresses or leveraging vulnerabilities in email protocols, to manipulate email exchanges. Manipulation often enables attackers to redirect funds or alter payment details. They might also inject false information into email threads, leading to confusion or miscommunication, which can significantly affect businesses.
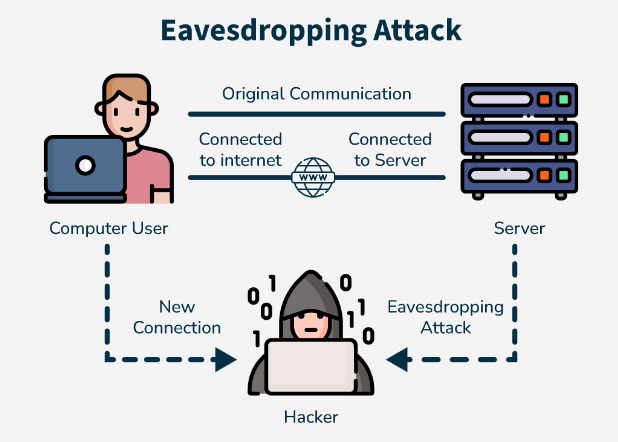
2. Wi-Fi Eavesdropping
Wi-Fi eavesdropping is when hackers intercept data sent over wireless networks. The man in the middle often sets up rogue access points known as “evil twins” that mimic legitimate networks. Unsuspecting users connect to these networks, which allows attackers to capture unencrypted traffic, including login credentials, credit card numbers, and personal messages.
Even if they don’t alter the data, attackers can gather intelligence by passively monitoring communications over rogue access points, which can be used in future targeted attacks. This attack is typical in public areas like cafes, libraries, and airports, where people often connect to open Wi-Fi networks without considering security.
3. Session Hijacking
Session hijacking is when an attacker takes control of an active user session with a web application, often by stealing session tokens or cookies. Attackers can execute session hijacking through cross-site scripting (XSS) or packet-sniffing techniques on unsecured networks. Once the attacker accesses a valid session, they can perform any action the legitimate user can, such as making purchases or transferring funds.
4. SSL Stripping
SSL stripping is a method that downgrades a secure HTTPS connection without the user’s awareness. The attacker intercepts the user’s request to access the target site and serves a non-secure impersonated version while relaying information to the legitimate site. This interception enables them to capture sensitive data, such as login credentials, while the victim believes they communicate securely. SSL stripping is especially effective against users who fail to notice the lack of HTTPS in their browser’s address bar.
5. DNS Spoofing/Poisoning
DNS spoofing involves manipulating DNS responses to redirect traffic from legitimate services to malicious ones. By corrupting the DNS cache of a resolver or server, an attacker intercepts and alters communications between systems. Attackers usually exploit vulnerabilities in the DNS protocol to inject false DNS responses into the resolver’s cache.
Understanding Man-in-the-Middle Attack Techniques
Threat actors are resourceful and versatile in their techniques to carry out MitM attacks. Here’s a number of tactics commonly used by attackers.
- Certificate authority compromise—This is a type of MiTM technique that compromises a certificate authority (CA), allows attackers to issue fraudulent SSL/TLS certificates, and makes a malicious website appear legitimate With a valid certificate, threat actors can intercept HTTPS traffic without raising suspicion, as browsers will trust the certificate just as they would with a legitimate site.
- Packet sniffing—Using tools to monitor and capture data packets across a network, packet sniffing is typically done with software like Wireshark or tcpdump which can capture real-time traffic. Once the attacker establishes a position on the network (often through methods like ARP spoofing or luring people into rogue access points), they can analyze the captured packets and extract sensitive information.
- Man in the browser—This technique injects malicious code into the victim’s web browser, for example by using a malicious browser extension that seems legit. The malware intercepts data transmitted between the user and web applications, allowing attackers to modify requests and responses without the user being aware.
- ARP spoofing—Involves sending false ARP messages over a local network. These messages allow attackers to associate their MAC address with the IP address of a legitimate device, enabling them to intercept and manipulate traffic directed to that device.
- API exploit—Attackers exploit unsecured APIs to intercept and manipulate requests. These security flaws include APIs that don’t use HTTPS for secure communication or publicly exposed APIs with no access controls. Exploiting APIs can lead to unauthorized access to sensitive data between different services.
6 Ways to Prevent Man-in-the-Middle Attacks
1. Strong Encryption Protocols
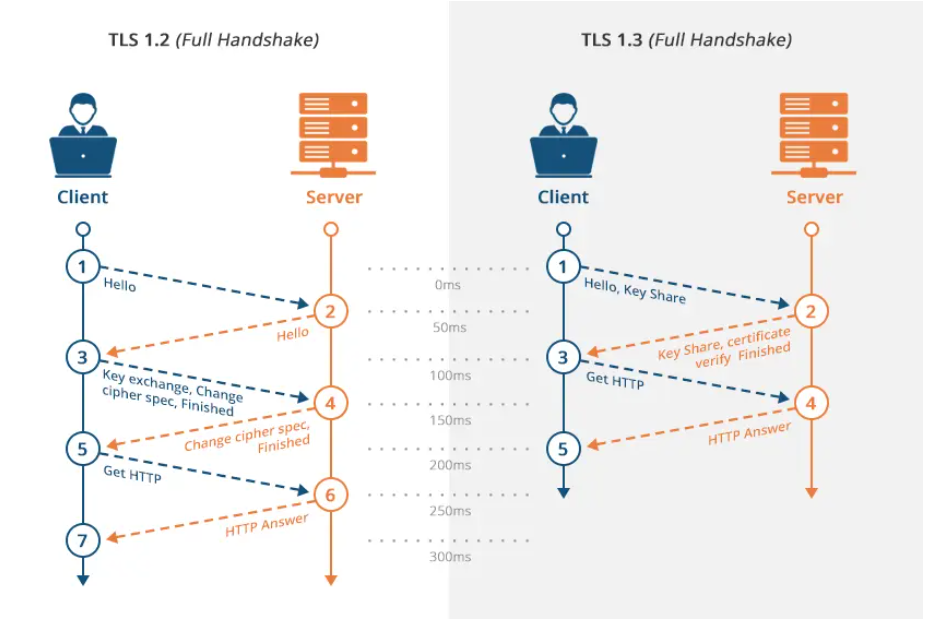
Robust encryption protocols such as HTTPS and TLS (Transport Layer Security) form the backbone of safeguarding data during transit. These protocols encrypt the data between clients and servers, rendering intercepted communications unintelligible to attackers.
Using the latest version of these protocols is vital here, especially with TLS. Worrying research from 2023 found that up to 79% of online servers use outdated TLS versions vulnerable to MiTM attacks. Conduct a thorough audit of your network to identify any services still running on older versions and disable them. Use tools like SSL Labs’ SSL Test to evaluate your server’s TLS version and configuration.
2. DNSSEC
DNSSEC adds an essential layer of security to DNS queries that prevent attackers from intercepting or spoofing DNS responses. By signing DNS records with cryptographic keys, DNSSEC allows resolvers to verify the authenticity of the responses they receive. If an attacker attempts to redirect a user to a malicious version of your site by altering DNS responses, the resolver can detect the tampering.
3. Dynamic ARP Inspection with DHCP Spoofing
Dynamic ARP Inspection (DAI) coupled with DHCP spoofing helps prevent ARP spoofing attacks, a common technique in MitM scenarios. DAI works by validating ARP packets on the network to ensure they are legitimate, effectively stopping attackers from associating their MAC address with a legitimate IP address. When used alongside DHCP snooping, which filters untrusted DHCP messages, you can prevent unauthorized devices from obtaining an IP address on the network.
4. Virtual Private Networks (VPNs)
A VPN encrypts all data transmitted between the user’s device and the VPN server, which makes it nearly impossible for attackers to intercept or decipher the information. This is particularly important for remote workers accessing sensitive company data or customers performing transactions over unsecured Wi-Fi connections. Though VPNs can be fundamental to your data governance plan, they aren’t immune to MitM attacks if not properly configured, especially when encryption, configuration, or the user’s device is compromised.
5. API Security
Take a look at the OWASP list of common API security weaknesses. Implement best practices like solid authentication and authorization mechanisms, such as OAuth 2.0, passwordless authentication, and API keys, to ensure that only trusted clients can access sensitive endpoints.
Regular security testing, including penetration tests and vulnerability assessments focused on API endpoints, can help identify and mitigate weaknesses before lurkers exploit them.
6. User Education and Awareness
As with many other areas of cybersecurity, addressing the human element with increased education and awareness can reap rewards. Communicate to employees and customers to check for the padlock icon when browsing online and understand the implications of insecure connections, like open public Wi-Fi (and how to use a VPN to mask information transmitted over those networks).
You can also communicate essential awareness tips and some of your security efforts during sales demos, assuring prospective customers that you take their data seriously. Highlight the importance of using strong, unique passwords and enabling extra authentication factors.
Outmaneuvering Man-in-the-Middle Threats
Foundational security practices like encryption and multi-factor authentication (MFA) remain essential for defending against various Man-in-the-Middle (MitM) techniques. But in some cases they do not suffice.
In quite a number of situations, MitM attacks involve impersonation or fake websites. Memcyco’s Digital Risk Protection (DRP) solutions excel at detecting impersonation attacks by monitoring suspicious activity and identifying when your website has been cloned in real-time. This helps prevent costly MitM threats tied to fake sites.
Some MitM attacks like Man-in-the-Browser (MitB) and session hijacking do not commonly resort to using cloned sites. Memcyco is now expanding its capabilities to address broader MitM sub-variants and related Account Takeover (ATO) fraud, in order to offer more comprehensive protection against these evolving threats.



















