Today, businesses don’t just rely on digital networks—they’re woven into them, with partners, third-party apps, and cloud platforms shaping their every move. Yet, every click, swipe, and connection opens a new door for attackers.
As of August 2024, a staggering 52,000 new common vulnerabilities and exposures (CVEs) were identified worldwide, with last year alone witnessing a record 29,000 CVEs. These numbers paint a clear picture: cyber threats are multiplying at an alarming rate.
As Bruce Schneier, a prominent voice in cybersecurity, puts it, “Security is not a product, but a process.” Integrating the principles of regulations like NIST 800-53 can be an effective way to adapt your security strategy to the complexities and growth of modern threats.
An Overview of NIST 800-53

NIST 800-53 is a set of security controls developed by the National Institute of Standards and Technology (NIST) to enhance the security of federal information systems. Originally published as part of the Federal Information Security Management Act (FISMA) in 2002, NIST 800-53 aims to protect sensitive government information from potential threats and vulnerabilities. The guidelines provide a structured approach to assessing cyber risks.
FISMA itself arose from a growing recognition that cybersecurity was becoming critical to the national security and economic interests of the United States. In the early 2000s, as digital technologies proliferated, government agencies faced increasing threats from cyber attacks. President George W. Bush signed FISMA into law in December 2002 as part of the E-Government Act.
Even if your business lacks a direct link to federal information systems that require mandatory compliance, voluntarily aligning with NIST 800-53 controls helps you securely handle sensitive or regulated data. Plus, you can tailor NIST’s guidelines to your specific operational needs.
For example, financial institutions deal with sensitive customer data like personally identifiable information (PII), credit card details, and transaction histories. E-commerce companies often manage vast amounts of customer data, including payment information and shipping addresses. This type of data needs rigorous security measures, potentially with the level of care that federal systems and data get, to prevent breaches and fraud.
Why NIST 800-53 Compliance Matters
NIST 800-53’s structured approach to cybersecurity can be quite helpful when organizations face mounting pressure to protect sensitive data and combat increasingly sophisticated threats. Here are some reasons why complying with NIST 800-53 can help:
1. Staying Ready with Continuous Monitoring – and a Response Plan
With NIST 800-53’s emphasis on continuous monitoring and a clearly defined incident response strategy, you’re always prepared to respond to potential threats quickly. Continuous monitoring gives your team the real-time insights they need to stay ahead of emerging risks, while streamlined incident response protocols reduce the impact of breaches. For companies where uptime is crucial, like financial institutions or e-commerce businesses, these capabilities help maintain all-important service continuity.
2. Reducing the Cost of Breaches
Data breaches come with significant costs that span multiple areas. These include penalties for non-compliance with regulations, recovery expenses for incident remediation, potential customer reimbursements, and the risk of prolonged operational downtime. Each of these factors contributes to the financial impact of a breach, affecting both short-term revenue and long-term business continuity.
3. Building Customer Trust
Today’s customers care about how you protect their data. In one study, 64% of consumers said they have opted not to work with a business because of concerns about whether they would keep their personal data secure. NIST 800-53 compliance allows you to demonstrate a commitment to high standards in security by building confidence and standing out as a trustworthy service provider. You’re not just meeting a standard—you’re using it as a competitive edge that lets customers/clients know their data is in secure hands.
4. Simplifying Compliance with Multiple Regulations
NIST’s privacy and security controls align with the strictest standards, which helps you tackle complex regulatory landscapes like GDPR, PCI DSS, and HIPAA with less duplicated effort. Imagine the time saved on audits and the confidence you’ll have knowing that NIST’s frameworks are widely recognized.
NIST Security Controls and Families
NIST 800-53 is a living document that has undergone multiple revisions. The most recent, Revision 5, marked a significant expansion and update to address modern cybersecurity threats and evolving tech infrastructures.
The document contains over 1,000 individual security and privacy controls, each designed to mitigate specific risks to information systems. The controls are organized under twenty distinct families, which allow you to apply relevant, risk-based measures tailored to your particular operational environment. The families are listed in the diagram below.
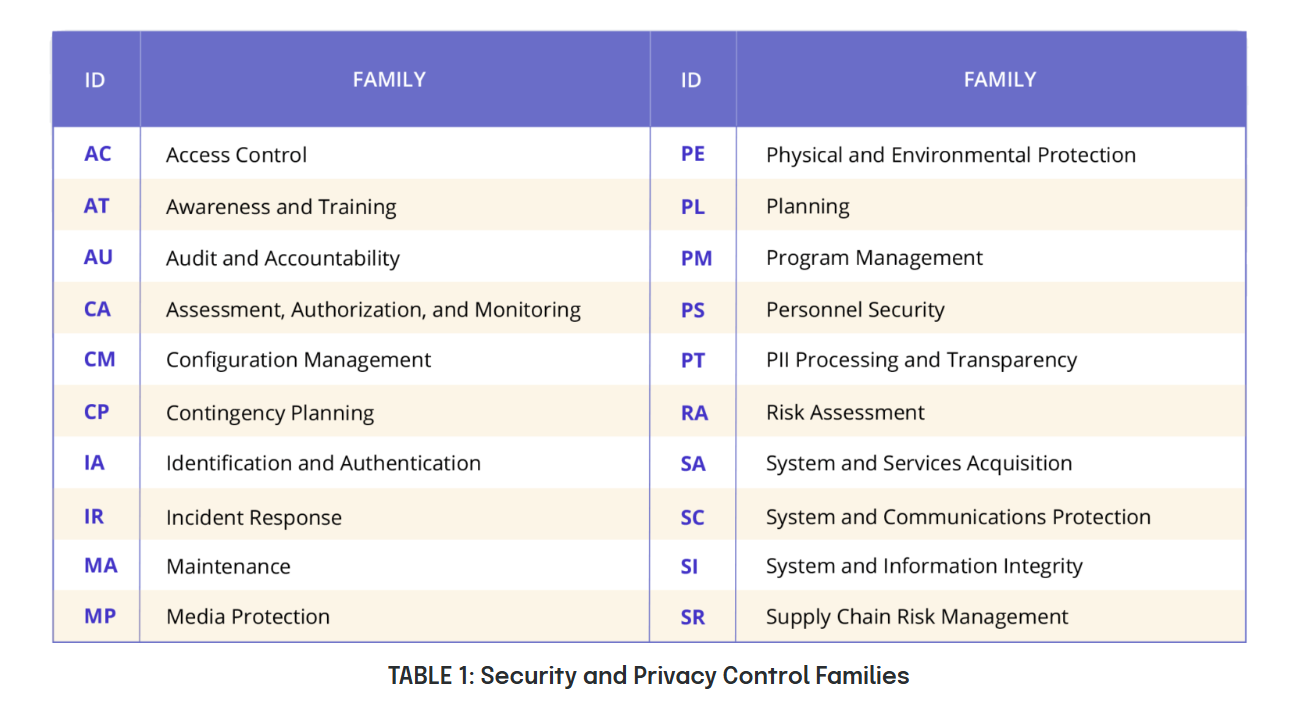
For example, within the Access Control family, specific controls might include limiting access to authorized users only (AC-2) or enforcing separation of duties (AC-5).
NIST 800-53 also uses a control baseline approach, dividing controls into three tiers: Low, Moderate, and High. These baseline layers help you implement levels of controls appropriate to your definition of risk and factor in other business priorities.
8 Steps to Compliance with NIST 800 53
1. Integrate Threat Intelligence into Security Operations
Incorporating threat intelligence feeds into daily operations helps your team gain real-time insights into emerging threats. NIST’s RA-5: Vulnerability Scanning and SI-4: Information System Monitoring controls support this by emphasizing the need for threat awareness and responsiveness.
Automated threat intelligence identifies attack indicators related to known threat actors, enabling your organization to block risks preemptively. Establish partnerships with trusted intelligence sources and customize feeds to suit industry-specific dangers if you want to refine your overall defense posture.
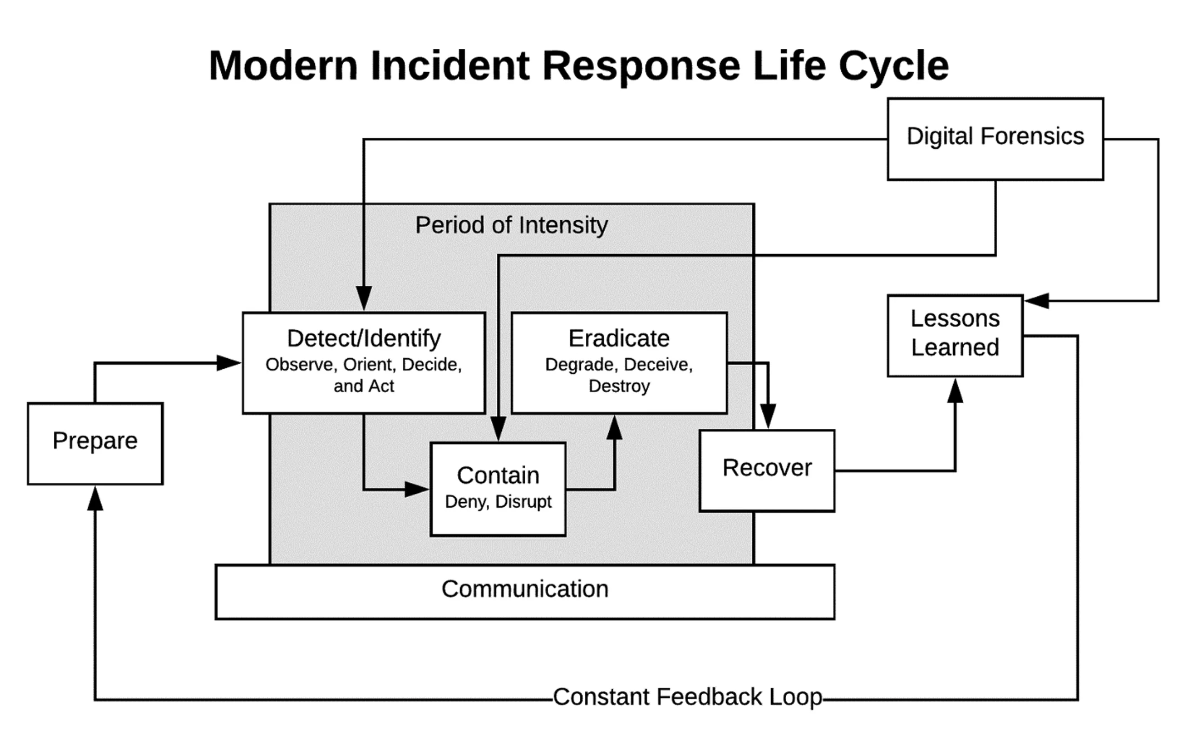
2. Automate Incident Response Workflows
Automated incident response workflows streamline the detection, analysis, and response processes for common threats, including malware and data exfiltration. This automation helps align with NIST’s IR-4: Incident Handling and CP-2: Contingency Planning.
Implementing automated incident response processes reduces human error, and speeds up response times for real-time threats, allowing your team to focus on advanced or targeted attacks. Automated workflows are invaluable for rapidly responding to incidents across customer data and financial transactions, whether in fintech or e-commerce.
3. Use a Secure Software Development Lifecycle (SSDLC)
Building security into your applications from the start can make it harder for attackers to impersonate or compromise your systems. SA-11: Developer Security Testing and Evaluation encourages security-focused design and testing. By incorporating secure design principles, you establish a foundation resistant to common vulnerabilities like SQL injection and cross-site scripting (XSS), key for SA-8: Security Engineering Principles. Also, peer reviews and code scans align with SI-10: Information Input Validation. These methods help you avoid costly post-deployment fixes and potential threats and enhance developer productivity, helping your team maintain a smoother workflow.
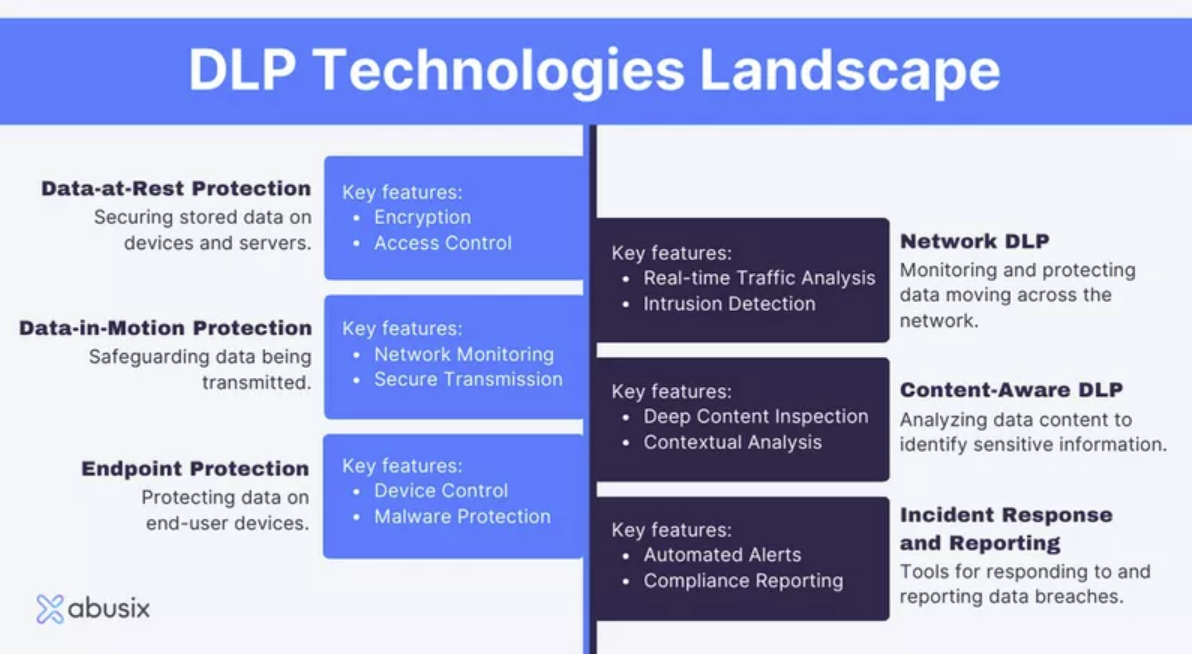
4. Implement Data Loss Prevention (DLP)
Don’t think of DLP as a type of solution; it’s more about a strategy for preventing data losses and leaks. A DLP program aligns well with SC-28: Protection of Information at Rest and AC-3: Access Enforcement by helping prevent unauthorized data transfers, particularly of regulated or sensitive data.
A DLP approach should include:
- Algorithms to inspect content across various data forms (e.g., documents, emails, and file transfers). These algorithms include keyword searches, pattern recognition (e.g., credit card or social security number formats), and data fingerprinting.
- Endpoint-based DLP tools to monitor and restrict activities on workstations, laptops, and mobile devices, especially when employees interact with sensitive information. These controls help prevent copy-pasting, USB transfers, screen captures, and printing of sensitive data.
- Network-based DLP tools to monitor the data flowing through network channels, particularly over email, web traffic, and cloud storage uploads. They can detect when sensitive data is about to leave your secure perimeter.
- Encryption and masking for data at rest and in transit. This step ensures that data remains protected even if it is intercepted or accidentally exposed.
5. Aim for Continuous Monitoring
To align with CA-7: Continuous Monitoring, you should leverage automated tools to track system changes, network traffic anomalies, and user behavior patterns. You can go beyond just monitoring what’s going on inside the network by continuously monitoring for signs of impending external threats – for example, by using advanced tools that detect attacks like phishing, ATO fraud, and brand impersonation.
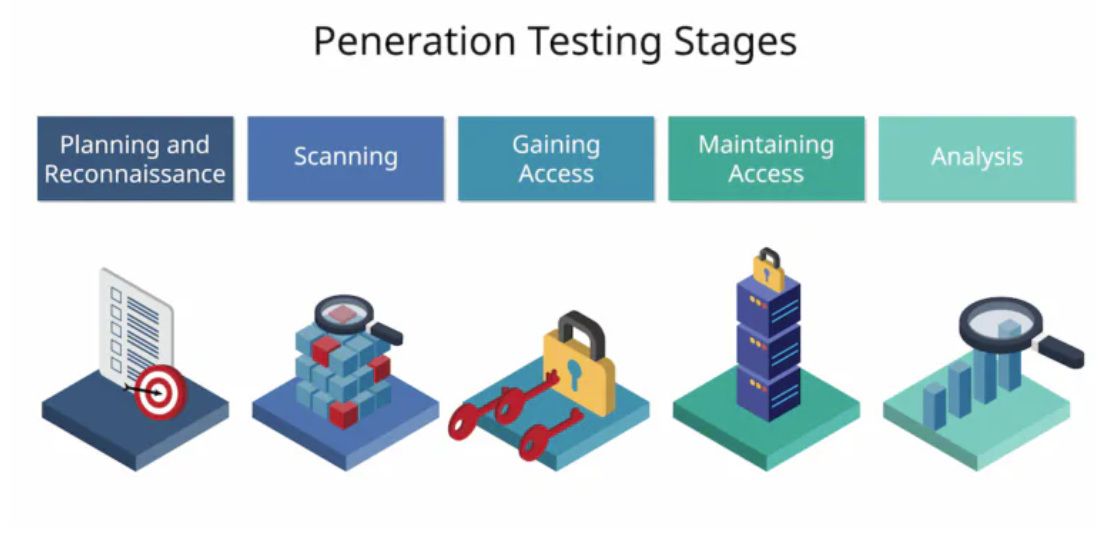
6. Conduct Regular Security Audits and Penetration Testing
Regular security audits and penetration testing help uncover vulnerabilities before hackers exploit them, and it’s this type of activity that the control CA-2: Security Assessments indicates you need to do. These assessments usually simulate various attack vectors to evaluate the effectiveness of existing controls. Collaborating with external security firms can provide an unbiased perspective of your security posture. Look for a mix of traditional penetration tests and other tests like blue vs red team exercises.
7. Regularly Update and Patch Software
Regular updates and patching are among the simplest yet most effective strategies for maintaining cybersecurity. NIST 800-53 emphasizes the importance of system maintenance through control CM-3: Configuration Change Control, which mandates that software and systems remain current.
Sectors such as automotive, consumer electronics, and pharmaceuticals can significantly benefit from this practice, as keeping all software updated mitigates security risks and optimizes manufacturing processes. A robust patch management strategy minimizes the attack surface and ensures that applications operate securely and efficiently, reducing the likelihood of production disruptions.
8. Develop an Advanced Persistent Threat (APT) Mitigation Strategy
Establishing a strategy to counter APTs includes identifying potential vulnerabilities that attackers could exploit. This aligns with NIST’s CA-9: Internal Systems Connection Control, which emphasizes the need for ongoing vulnerability assessments. A well-defined APT strategy enhances your ability to thwart sophisticated attacks and fortifies defenses against the most savvy hackers.
Elevate Your NIST 800-53 Compliance Commitment
Memcyco helps elevate your commitment to NIST 800-53’s high standards by providing real-time monitoring and protection against today’s nifty and nefarious phishing and fraud attempts. Its nano-defender technology enables real-time alerts if your website has been spoofed, so you can act swiftly and avoid breaches. You can protect your customers, too, as they get red alerts when entering a cloned site. In addition, Memcyco uses decoy data to prevent their data from ending up in the wrong hands.
With these capabilities, Memcyco can help you meet a series of NIST 800-53 controls, such as AC-22: Publicly Accessible Content (ensuring that publicly accessible content is legitimate and not impersonated), SC-23: Session Authenticity (protecting against session hijacking through fake websites), and IR-4: Incident Handling (responding to incidents promptly).
Ultimately, NIST 800-53 is an opportunity to bolster your organization’s security posture, win customer trust, and differentiate your company in a crowded marketplace (even if compliance isn’t mandatory for your specific sector and customer base).
Download the checklist to simplify your NIST 800-53 compliance path.
![8 Steps to Compliance with NIST 800 53 [XLS Checklist]](/wp-content/uploads/2024/11/Blog_8-Steps-to-Compliance-with-NIST-800-53-XLS-Checklist_1024x576.png)


















