Cybercriminals are notoriously adept at evolving their strategies and tactics to defraud individuals and businesses out of their hard-earned money. One perfect example of the evolution of effective and illusive financial fraud is card skimming.
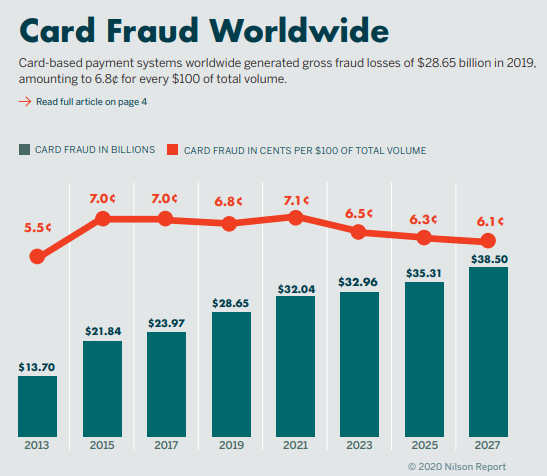
But is card skimming still a thing in 2024? Very much so. According to the FBI, card skimming fraud still costs financial institutions and American consumers more than $1 billion yearly—and it’s growing. In 2023, the FTC reported card compromise reports (CCRs) saw a 20% year-over-year increase.
Card skimming fraud in 2024 will not be limited to ATMs and gas stations and will have a direct and far-reaching impact on Infosec. The fallout of a successful web card skimming fraud can include financial consequences, legal and regulatory challenges, and damage to the hard-earned reputation of your brand.
How has card skimming evolved, and what methods do malefactors employ today to defraud your clients online tomorrow?
What is Card Skimming?
Card skimming is a category of credit card fraud involving illegally collecting a victim’s debit or credit card information. As the name suggests, it entails quickly reading payment details when the victims use them for legitimate activities like withdrawing cash at an ATM, filling gas, using self-service checkout, or making online purchases.
When the cardholder signals their approval of a transaction, the malefactor acts as a man-in-the-middle and captures the credit card information. The harvested payment card data can then be used to make additional purchases or payments unbeknownst to the victim.
What Makes Card Skimming a Challenge for Infosec Pros?
For digital merchants, online retailers, government agencies, and financial institutions, digital card skimming is a growing threat to data protection. Unlike traditional physical card skimming schemes, web card skimming campaigns do not require physical access to a card reader and are much harder to detect and prevent.
There are numerous reasons why digital card skimming is such a headache for digital businesses. Since most e-commerce businesses facilitate consumer payment through third parties and payment gateways, they believe the liability will fall on the payment service provider. However, that is not the case—and it’s up to retailers to invest in protecting their shops and shoppers, on and offline, with continuous security monitoring and other threat detection solutions.
Another issue with web card skimming attacks is that they are hard to detect and mitigate. Because these attacks often rely on JavaScript execution on the client side, there is no evidence in server logs of any redirection or tampering.
The 4 Steps of a Digital Card Skimming Attack
The process of executing a digital card skimming attack is usually made up of four steps:
1. Breach
Cybercriminals need access to the device or system that processes the credit card details in a way that enables them to collect and reuse the details.
2. Infect
Once they’ve gained access, the crooks conceal a card skimmer, which could be either a hardware device or software code that’s hidden on a legitimate-appearing checkout page or device.
3. Collect
The skimmer works quietly in the background, collecting the credentials that pass through it until it is shut down. The credit card details and PIIs may be collected locally and sent to the attacker in batches, or conspicuously transmitted immediately to the attack command and control server.
4. Monetize
Payment details and PIIs collected through card skimming methods are rarely used by the cybercriminal that harvests them. Typically, the data is sold in bulk on the dark web. The stolen payment information is often used to purchase cryptocurrency to make the stolen funds untraceable.
5 Card Skimming Methods Every Infosec Pro Needs to Know
1. Physical Card Skimming
This is the more traditional and familiar method of card skimming. It uses card skimmers or “shimmers,” small electronic devices that harvest credit card information from ATMs and gas station credit card scanners using hidden cameras and sensors. Malefactors with little knowledge of electronics can purchase card skimming devices and instructions on using them on the black market.

2. Digital Skimming
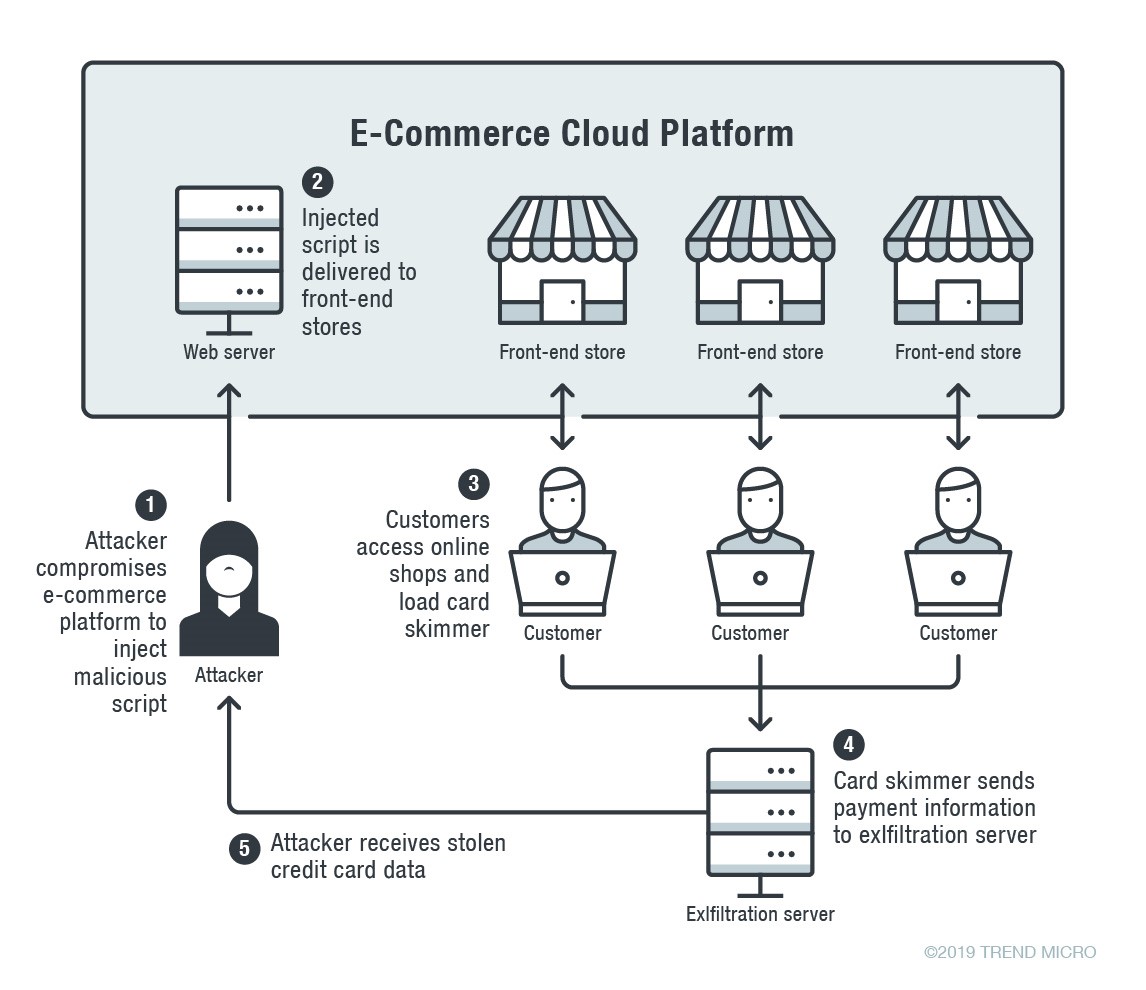
Web card skimming is also known as eSkimming and digital card skimming, and are often collectively referred to as Magecart campaigns (referring to a notorious cybergang that was the first to execute a web skimming attack successfully). These attacks allow malefactors to collect payment information from clients of an infected website.
The most famous web card skimming attack is the Magecart attack on British Airways, which exposed the personal information of 500,000 of the airline’s online users and cost the brand a hefty fine.
This method often involves the creation of spoofed websites that closely resemble the target website and appear entirely genuine to the average user. In other cases, it may involve using modal overlays to capture the credit card information.
To combat digital skimming and spoof-proof your e-commerce apps and websites, you can use Memcyco’s end-to-end website spoofing detection and prevention suite. It makes protecting your customers and digital assets easy with digital trust enablement and real-time brand fraud prevention.
3. Point-of-Sale (POS) and ATM Malware
Cybercriminals with enough skill and access to targeted financial systems can deploy malware onto ATM and POS systems to capture credit card information upon transaction. This type of malware often uses sophisticated methods to capture the data before it can be encrypted, such as RAM scraping malware. Attacks of this type can be tough to detect, and have been plaguing financial institutions and vendors since as early as 2008.
4. Wireless (Man-in-the-Middle) Interception Attack
In this method, attackers exploit unpatched vulnerabilities in payment systems or unsecured wireless communications, such as public wi-fi networks. This issue is easy to remedy by ensuring all PIIs and payment details are transmitted with strong encryption to protect them in transit.
5. Sideloading and Chain-loading Attacks
Users feel safe entering their payment information in a branded application on their mobile device, and malefactors know it. Cybercriminals create fake apps and plugins that introduce card skimming malware onto the device, usually along with keyloggers and other components to enable remote abuse of access to the compromised user device. For example, these attacks can send links to malicious websites to the users’ contact list without alerting the user.
Preventing and Mitigating Card Skimming with Memcyco
Digital card skimming attacks are the most challenging threats faced by e-commerce website administrators. Unlike physical card skimming, digital card skimming schemes can only be uncovered and mitigated using specialized tools and a robust website security posture. Card skimming threatens your business reputation and digital trust, while potentially violating PCI DSS compliance.
To protect your online clients and their credit cards, you need a suite that includes client-side JavaScript abuse prevention and granular context-based alerts on suspicious behavior detected in access to your digital assets. Memcyco’s solution offers industry-leading protection against impersonated websites used to harvest your customers’ payment information fraudulently.
Contact Memcyco today to discover how to protect your online shoppers from Magecart and other digital card skimming attacks.



















