You invest a wealth of resources in understanding your customers’ behaviors, predicting their needs, delivering products and services where they want them, and building strong relationships. But once they gain access to your ecosystem, how do you know they are who they say they are?
In 93% of attacks, cybercriminals can breach an organization’s network perimeter and successfully steal the credentials of 71% of companies they victimize. Compromised credentials are all they need to gain access to the portals, accounts, and services in your ecosystem and put you at further risk of a security breach. It’s a risk you cannot afford.
Trusting your customers—consumers, citizens, and partners, too—and protecting yourself from imposters starts with customer identity and access management (CIAM). CIAM ensures you give only verified customers access to your ecosystem and required data while ensuring a smooth user experience.
Read on to learn what CIAM is, why it’s a critical component of your cybersecurity stack, and how to go about finding the right solution to protect your assets and customers. Then explore our picks for the top five CIAM solutions for 2023.
What is Customer Identity and Access Management?
It’s easy to confuse CIAM with identity and access management (IAM), but each serves a specific purpose:
- IAM: Applies to how you control internal access to your organization’s networks, protecting them from outside intruders.
- CIAM: Refers to how you manage external identities for customers, partners, or contractors to access your organization’s ecosystem, including accounts, databases, products, and services.
Like IAM, CIAM ensures the external people who access your accounts and applications are:
- Authenticated: They are who they say they are.
- Authorized: They get access to only what they need based on their user profile.
- Managed: They get a streamlined, seamless digital experience across your ecosystem.
But unlike IAM, CIAM is scalable to authenticate large or peak loads—as many as a billion customers—in real time.
Why You Need a CIAM Solution
Even more so, CIAM is an extension of IAM that focuses specifically on managing external access you can’t get alone with IAM. Take a look at some essential advantages a CIAM solution provides:
- Secure sign-on: By securing each touchpoint between your brand and your customers, you establish your customers’ trust in you to provide safe and secure applications and services.
- Data privacy: When you protect your customer’s personal and account information, you boost their confidence by demonstrating your compliance with data privacy regulations.
- Smooth customer experience: When you provide your customers secure authentication to their accounts, you streamline their sign-in experience so they can more easily work with the applications and services in your digital ecosystem.
- Customer insights and personalization: By gathering information about each time a customer engages with your digital services, you gain insights into their unique behaviors to help you personalize offerings and provide more effective self-service.
A CIAM solution enables you to provide a smooth and custom user experience that keeps security at the forefront.
How to Select a CIAM Solution for Your Organization
When choosing a CIAM solution, keep in mind the following criteria:
- Seamless single sign-on and multifactor authentication (MFA) that works across applications, devices, and locations.
- Highly scalable cloud-based user management so you can oversee all users, groups, and devices; map user profiles; and get support for your ideal user migration approach.
- Rapid and autonomous user provisioning and deprovisioning across your technology infrastructure.
- Ability to integrate with existing, day-to-day IT systems, whether on-premises or in the cloud.
- Scalability to keep up with and support your organization’s customer growth.
- Reliability with consistent uptime to ensure a smooth customer experience and maintain your brand reputation.
- Security to protect you and your customers from today’s ever-evolving cyber threats.
Also, make sure the provider is accredited, meets data privacy and protection standards, and has proven customer success.
Top 5 CIAM solutions for 2023
As you plan to fortify your cybersecurity stack for 2023, be sure to include a CIAM solution in your budget. Take a look at our 5 picks of the top CIAM solutions for 2023.
1. auth0 by Okta
Auth0, a product unit of Okta, delivers convenience, privacy, and security to any user accessing any application. It’s a highly customizable identity platform is simple, yet flexible enough for development teams to protect billions of monthly logins.
Pros: Auth0 has diverse libraries, making it easy to integrate into any implementation or programming language. Also, its user interface makes it easy to search for, update, and manage user information.
Cons: Some users report the implementation isn’t as easy as it might seem, and it doesn’t provide enterprise-grade features. Others couldn’t access rule permissions.
Pricing: Free trial available. B2C – Essentials starts at $23/month, and B2B – Essentials starts at $130/month.
2. Frontegg
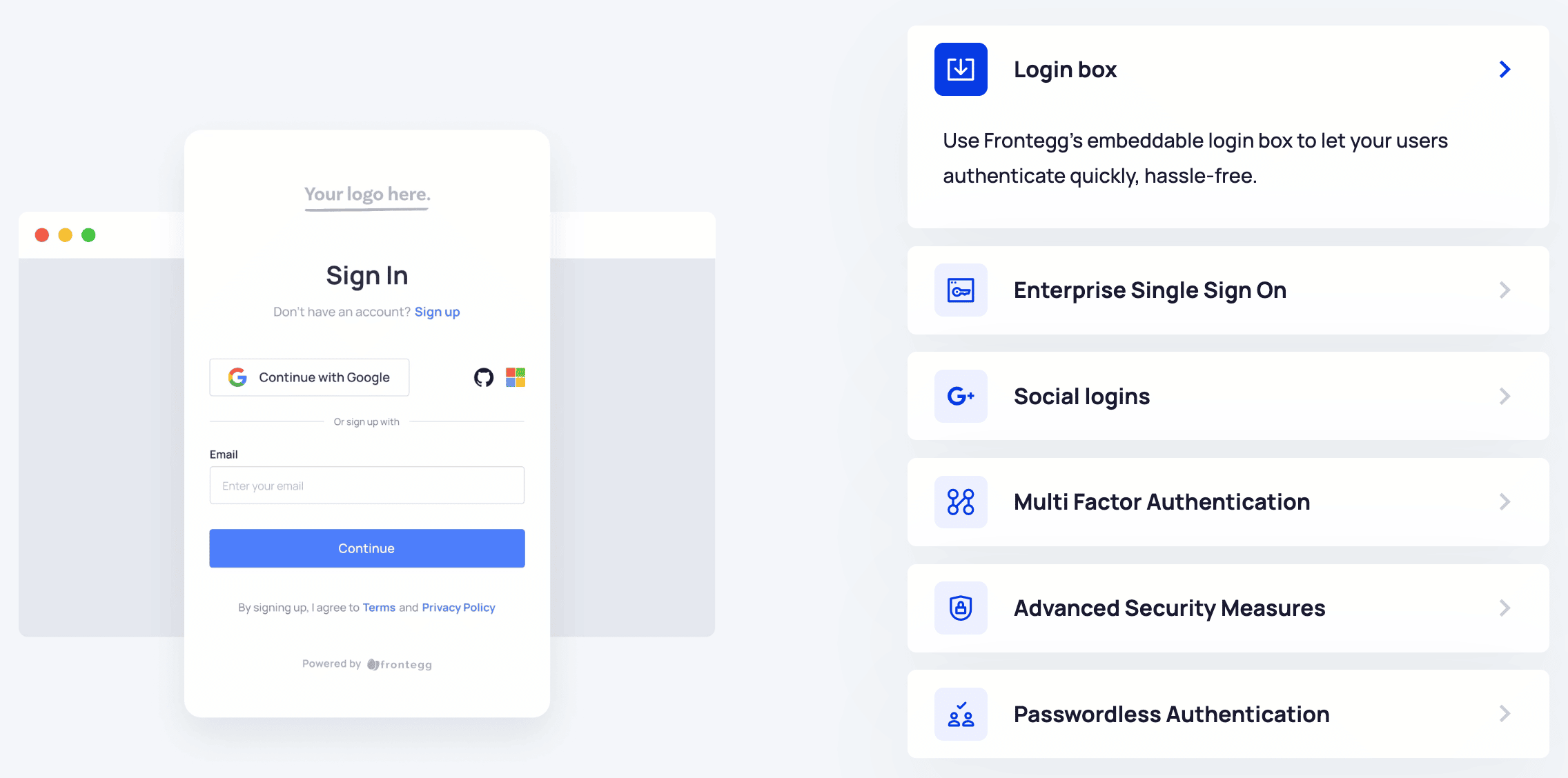
Made for developers, the Frontegg multi-tenant platform gives users full visibility and granular control over their personal and organizational settings through its self-serve Admin Portal. It supports application developers by managing base-level authentication flows, complex organizational structures, fine-grained authorization, API-token management, SSO, and much more.
Pros: Frontegg is easy to implement and use, saving developers work so they can focus on product development. Customers can freely configure their application on their own.
Cons: Users report the client customization features need improvement and that it lacks integration with other platforms, such as Terraform and NGINX, to ease deployment.
Pricing: Offers a basic free plan and three enterprise plans, with early-stage pricing starting at $249/month.
3. Memcyco
Although not exclusively a CIAM solution, Memcyco offers its Proof of Source Authenticity (PoSA) to protect your company and customers from imposters and scammers. The PoSA solution verifies and authenticates digital assets in real time at every touchpoint between brands and customers, partners and employees. It uses a watermark (see the following video)—or optionally a silent watermark—to certify an authentic website, email, or SMS message and block attempts to forge access.
It alerts end users about:
- Spoofing, cloning, or reverse-engineering attempts
- Sign-ins from a previously unknown device
- Repeated frequent login attempts
Pros: It installs in a single line of JavaScript code in your site’s HTML file and to configure email and SMS integration.
Cons: It isn’t a true CIAM solution because it doesn’t authenticate and verify individuals but rather verifies your company’s assets they come into contact with.
4. OneLogin
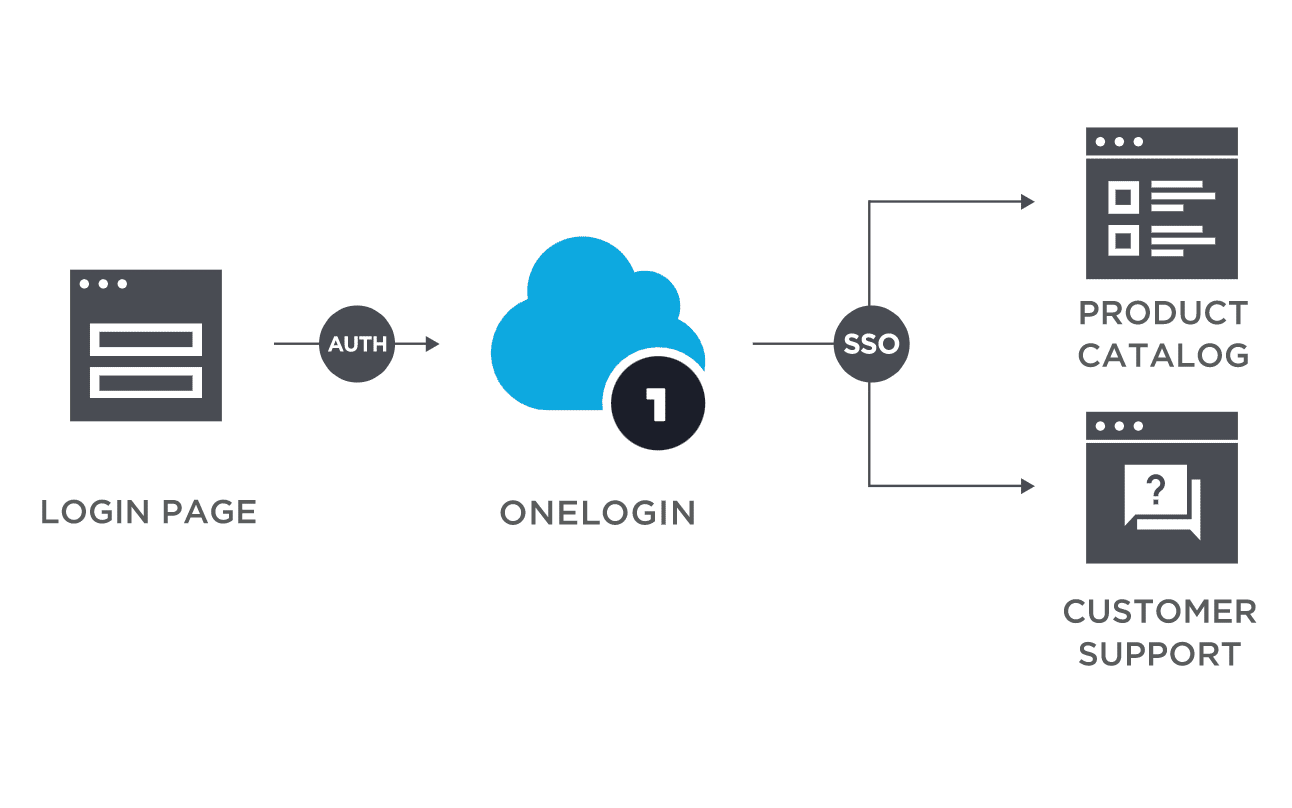
OneLogin offers employees, customers and partners secure, one-click access, for all devices, to all enterprise cloud and on-premises applications. It increases your security posture while ensuring a seamless customer experience. OneLogin provides robust security and authentication, easy migration and administration, and reliability at scale with zero downtime.
Pros: It keeps all applications and logins organized, making everything easy to find and manage. The session management architecture requires re-authentication after a period of inactivity, which insures the right person is accessing the resource.
Cons: Some users find the required password changes are too frequent. One user found OneLogin Protect unable to authenticate the login and had to resort to another authenticator.
Pricing: 30-day free trial. Contact sales for pricing.
5. Ping Identity
PingOne Identity offers the PingOne for Customers CIAM solution. It combines a no-code identity orchestration engine with SSO and MFA authentication and centralized API access management to build, test, and optimize digital customer experiences. This CIAM solution unifies customer profiles across disparate identity silos and datastores to create a single view of the customer.
Pros: It’s easy to set up, configure, and establish federation with other identity providers. It also seamlessly secures customer identities, making for an easy log-in experience.
Cons: One user reported that synchronization doesn’t seem to work at times. Other users reported difficulty with the user interface in navigating the application configuration process or accomplishing support tasks.
Pricing: 30-day free trial. Customer pricing plans start at $20k annually.
Use CIAM to Stand Out from the Crowd
To protect your organization and its assets, you need an IAM solution. But, to ensure your customers and partners also remain protected, you need a CIAM solution.
Going a step further, you need to ensure your customers and partners can trust your organization’s assets. That’s where Memcyco comes in with its Proof of Source Authenticity solution. The PoSA solution verifies your digital assets and differentiates them from fakes at every point of communication with your customers and partners—from your website landing pages to your ads, emails, and SMS messages.
This level of verification goes both ways, seamlessly ensuring your customers of the legitimacy of your organization and vice versa. This added security elevates the customer experience, creates greater trust in your brand, and boosts your competitive advantage. Amp up your CIAM solution with Memcyco. See how our Proof of Source Authenticity stops imposters in their tracks to keep your customers and digital assets safe. Read our whitepaper.



















