Imagine: You get an email from your bank alerting you to a suspicious login attempt. It looks identical to their usual security notices, down to the logo and phrasing. You click the link to review the activity, log into your account—and unwittingly hand your credentials over to a cybercriminal.
This is the reality of clone phishing. Unlike obvious scams riddled with typos and bizarre requests, clone phishing attacks are meticulously crafted copies of legitimate emails, websites, or even text messages designed to avoid raising suspicion, increasing the chances of successful attacks.
Verizon’s 2024 Data Breach Investigations Report found that human error factors into 68% of breaches—and that, on average, users click on a phishing simulation link in just 21 seconds, submitting sensitive data to a phishing website in only 28 seconds.
More importantly, how can you protect yourself and your organization? Understanding the various types of clone phishing—and how to protect your customers and employees against them—will help you mount your best defense in this high-stakes game of digital deception.
What is clone phishing?
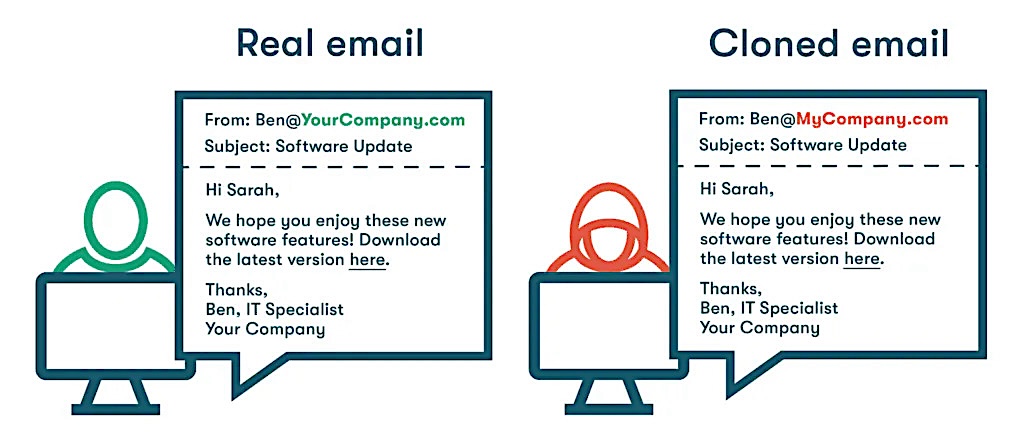
Clone phishing is a targeted social engineering attack in which threat actors create a near-identical copy (or “clone”) of a legitimate email, text message, or website. These clones often replicate branding elements, sender information, and even the stylistic conventions of the original communication, aiming to deceive even the most scam-aware recipients into believing the message is genuine.
The cloned messages are weaponized with malicious links or attachments that, when clicked or downloaded, can lead to consequences ranging from credentials theft and data exfiltration to unauthorized money transfers, malware, or ransomware.
Who are the targets of clone phishing?
Clone phishing attacks primarily target two distinct groups, each presenting unique mitigation challenges:
Internal Employees
When clone phishing scams target employees, the business impact can be significant. This can lead to data breaches, financial loss, fines, ransomware, and disruption of critical operations. While technical defenses such as advanced email security and endpoint protection can help, they are not foolproof.
Customers
Protecting customers from clone phishing attacks poses a more complex challenge than safeguarding employees, partly because organizations have minimal control over the security posture of their customers’ devices and cybersecurity awareness.
This underscores the importance of implementing proactive customer protection from phishing-related scams rather than relying solely on customer education, or waiting for customers to fall victim before gaining visibility of clone phishing attacks.
Clone phishing defense is even more critical in the face of the changing regulatory landscape in many countries, where businesses are held accountable for protecting and reimbursing customers who fall victim to APP fraud and other financial cybercrimes.
How does clone phishing work?
Clone phishing preys on the inherent trust individuals place in familiar communications. A typical attack unfolds in five stages:
1. Target Selection
The fraudster identifies a legitimate email or message to clone. This often involves selecting a communication that the recipient will likely recognize and trust, such as a recent transaction confirmation, a routine company update, or a recurring notification.
2. Message Cloning
Next, the fraudster creates a near-perfect replica of the chosen message. This process involves copying the email’s layout, subject line, sender information (often using spoofed email addresses or display names), and overall tone. The goal is to make the cloned message indistinguishable from the original.
3. Weaponization
The attacker modifies elements of the cloned message for malicious purposes, such as replacing legitimate links with URLs that lead to impersonated websites or swapping out benign attachments with files containing malware.
4. Delivery and Deception
The cloned message is sent to the intended recipient. Attackers often employ techniques like email spoofing to enhance the message’s apparent legitimacy further. The email’s recipient selection is based on prior reconnaissance, which may involve scanning company websites, social media profiles, or data breaches for potential targets.
5. Impact
The consequences can be severe if the recipient buys into the deception and interacts with the malicious content. They may include the compromise of sensitive data, financial losses, damage to the organization’s reputation, account takeover (ATO), and potential legal or regulatory repercussions and ransomware.
How to Recognize Clone Phishing
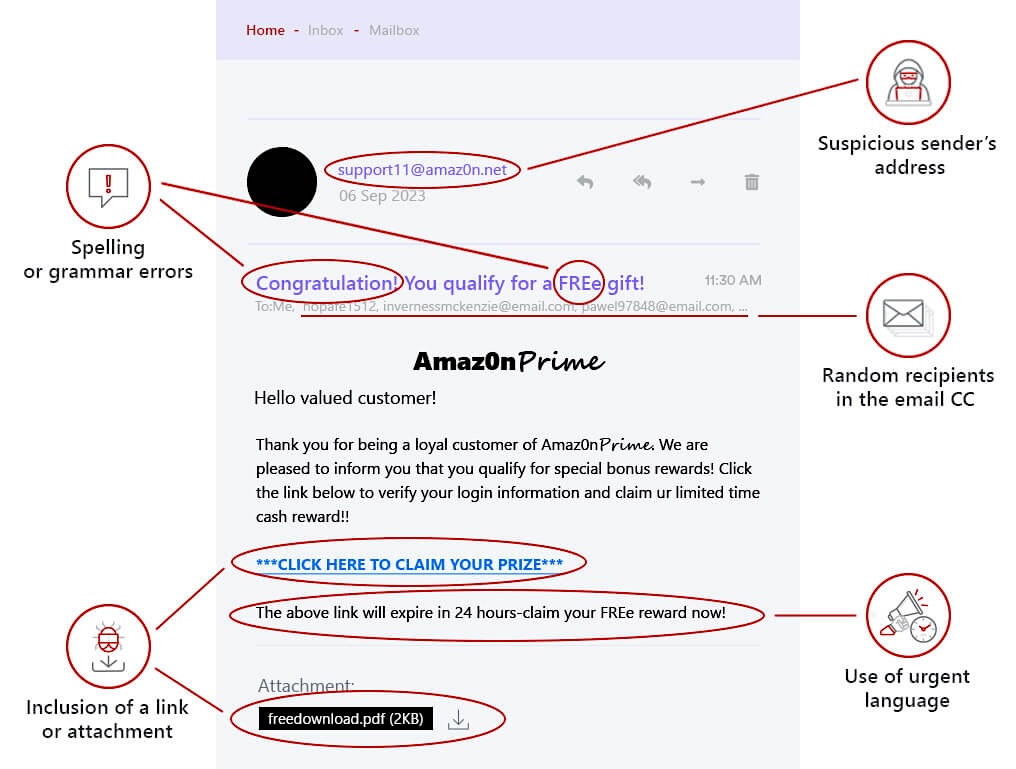
The deceptive nature of clone phishing makes it a particularly insidious threat. These attacks meticulously mirror legitimate communications, often lacking the telltale signs of more traditional phishing attempts like obvious grammatical errors or suspicious sender addresses.
Many available clone phishing detection tools are not software, but instead require human involvement—so vigilance and a keen eye for detail can help uncover these duplicitous attacks.
Here’s what to look for:
Sender Address Discrepancies
Scrutinize the sender’s email address for subtle variations or misspellings. Threat actors may use lookalike domains in a practice sometimes called cybersquatting. These impersonating websites have domains that closely resemble legitimate ones, such as ‘companny.com’ instead of ‘company.com.’
Urgent or Unusual Requests
Be suspicious of emails that demand immediate action or create a sense of urgency, especially those involving financial transactions, password resets, or personal information updates.
Template Inconsistencies
Compare the email’s layout, branding elements, and formatting to previous communications. Look for discrepancies in logos, colors, fonts, or overall design, as attackers may not have access to the most up-to-date templates.
Suspicious Links
Hover over links in an email (without clicking) to preview the URL. Avoid clicking if the destination doesn’t match the expected domain or appears suspicious. These links lead to malicious websites that steal credentials or payment information, often leading to ATO. The sites may also download malware or ransomware into the victim’s computer.
5 Types of Clone Phishing Attacks and Protection Strategies
Clone phishing attacks are diverse, each exploiting different avenues of trust. Here are five common types, along with potential mitigation strategies for the affected parties:
1. Replicated Content with Malicious Links
This attack involves fraudsters cloning legitimate emails, substituting genuine links with malicious ones that redirect to impersonated sites mimicking your authentic website. These fake sites are often designed to harvest payment information, login credentials, or other sensitive data.
Scenario Examples
- Password Reset Scams: An email that appears to be from a service you use claims there’s a need to reset your password due to a security issue. The link provided, however, leads to a fake login page designed to steal your credentials.
- Invoice/Payment Notifications: A seemingly legitimate invoice or payment request email includes a link to a phony payment portal where victims unwittingly enter their financial details.
Potential Damage
Identity theft, financial fraud, ransomware, unauthorized access to accounts, and significant damage to the company’s reputation.
Best Protection Strategies
- Employees: Robust email security tools with link analysis and threat intelligence, regular security awareness training on identifying suspicious links, and encouraging cautious clicking behaviors.
- Customers: In this case, the overwhelming majority of detect-protect-respond mechanisms are human-based—such as customer awareness training, which is often ineffective. Existing software solutions of the scan-and-takedown variety are non-real-time and lack protection and visibility.
However, advancements in real-time customer protection mean businesses no longer have to rely on customers to know when clone phishing attempts and similar attacks are scamming them. Only one company, Memcyco, offers a solution that helps protect customers against impersonated websites that clone phishing victims are sent to by malicious links.
2. Replicated Content with Malicious Attachments
In this case, fraudsters clone legitimate emails but replace safe attachments with malicious ones. These attachments often contain malware like ransomware, spyware, or keyloggers designed to compromise systems and steal data.
Scenario Examples
- ‘Updated’ Invoices: A vendor you regularly work with sends an ‘updated’ invoice with a slightly different file name or format. The attached file contains malware that infects your system when opened.
- Fake Shipping Notifications: An email that appears to be from a shipping company informs you of a package delivery and includes a malicious attachment disguised as a shipping label or tracking information.
Potential Damage
Ransomware infections, spyware monitoring, keystroke logging, theft of confidential data, and complete system takeover.
Best Protection Strategies
- Employees: Regular employee training on safe attachment practices, and content filtering to block suspicious file types.
- Customers: Customer awareness training from the company can help instill better cybersecurity practices, such as enabling multi-factor authentication (MFA) for online accounts, using strong and unique passwords, and taking a cautious approach to opening unexpected or unsolicited attachments.
3. Email Display Name Deception
During clone phishing attacks that use email display name deception, threat actors manipulate the display name in emails to impersonate trusted individuals (like CEOs or colleagues) or entities (like IT departments or familiar brands). This tricks victims into opening the email and clicking on malicious links or attachments.
Scenario Examples
- CEO Impersonation: An email appears to be from your company’s CEO, urgently requesting a wire transfer or the release of sensitive financial information.
- IT Department Updates: A message seemingly from your IT department instructs you to click a link to update your password or download a new software patch.
- Familiar Company Spoofing: An email that looks like it’s from a company you do business with (like your bank or a subscription service) asks you to verify personal information by clicking on a malicious link.
Potential Damage
Unauthorized financial transactions, disclosure of confidential company information, execution of fraudulent activities requested in the email
Best Protection Strategies
- Employees: Use email authentication protocols (DMARC, SPF, DKIM) to verify sender identity and undergo security awareness training to scrutinize the actual email address, not just the email display name.
- Customers: Consider using security awareness tools that simulate phishing attacks to train customers on how to identify and respond to them.
4. Seasonal or Event-based Clone Phishing
To exploit the heightened emotions and expectations around holidays, sales events, or major news cycles, attackers craft clone phishing emails that appear timely and relevant, often offering enticing deals or urgent information.
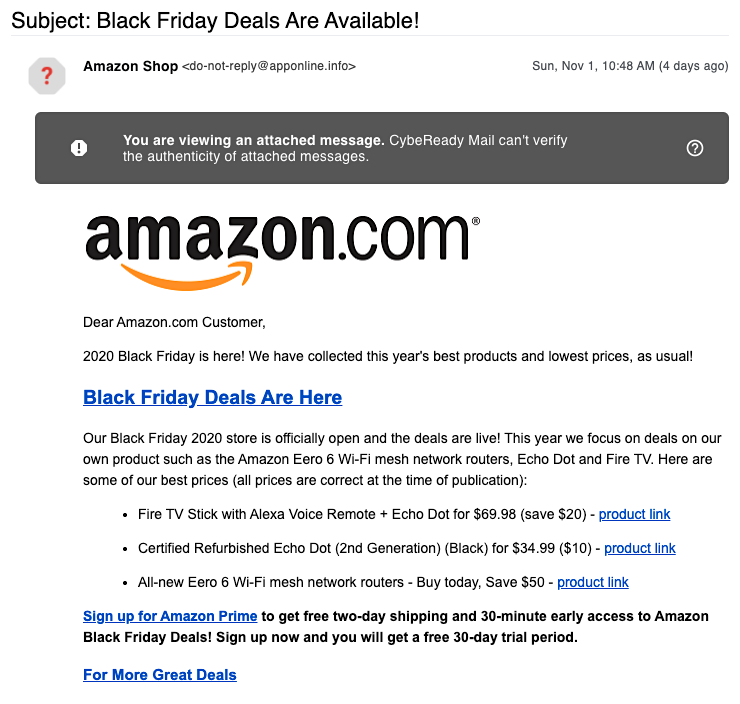
Scenario Examples
- Black Friday Bargains: An email advertising incredible deals on popular products leads to a fake website that steals credit card information.
- Last-Minute Getaway Deals: A tempting travel offer just before a holiday season pressures recipients to book quickly through a malicious website.
- Election-Related Emails: Messages impersonating political parties or election officials request personal information or donations through fraudulent links.
Potential Damage
Financial fraud through fake deals, identity theft through fake forms, spread of misinformation and political manipulation.
Best Protection Strategies
- Employees: Heightened vigilance during peak seasons or events, and always verifying deals or information directly with the official company channels.
- Customers: Proactive communication to customers about potential scams, with increased security measures and monitoring during high-risk periods.
5. Legal or Government Impersonation
Attackers impersonate government agencies (such as the IRS or law enforcement) or legal entities, using threats of legal action or promises of benefits to compel victims to follow their demands.
Scenario Examples
- Jury Duty Summons: An email that appears to be from a local court informs you that you’ve been selected for jury duty and must click a link to provide personal information or pay a “processing fee.”
- Tax Notices: A seemingly official email from the IRS claims you owe back taxes and threatens legal action if you don’t click a link and make an immediate payment.
Potential Damage
Financial loss due to fake fines or fees, identity theft through fraudulent forms, compliance issues due to misinformation.
Best Protection Strategies
- Employees: Verify any government or legal requests directly with the official agency through secure channels (like phone numbers listed on official websites, not in the email), and be skeptical of unsolicited communication.
- Customers: Public awareness campaigns educating citizens about common scams, secure online portals for official communication, and robust email authentication protocols.
Protect Customers from Clone Phishing Scams in Real-time, Before and as Attacks Happen, with Memcyco
Education campaigns and robust security protocols are the least businesses can and should deploy to protect customers from clone phishing attacks. However, such tactics are no longer enough, given the near-identical nature of impersonated clone phishing messages that dupe even the most scam-aware customers.
If clone phishing attacks lure your most aware customers, what hope do less aware customers have? Memcyco protects even your most vulnerable customers by giving them failsafe ways of knowing when they’re visiting your legitimate website, and when it’s a fake. If customers click suspicious links to fake sites, you’ll know about it, and they’ll know to avoid proceeding.
Memcyco even preemptively detects, in real-time, clone phishing attempts that leverage fake websites, before customers are even at risk of clicking suspicious links.
From website code reconnaissance attempts to fake URL registration and ‘fake site live’ events, Memcyco offers real-time coverage across the entire attack timeline—all while keeping customer credentials safe during attacks and after fake site takedown.
See how Memcyco can help protect your organization and customers from clone phishing by scheduling a demo today.



















