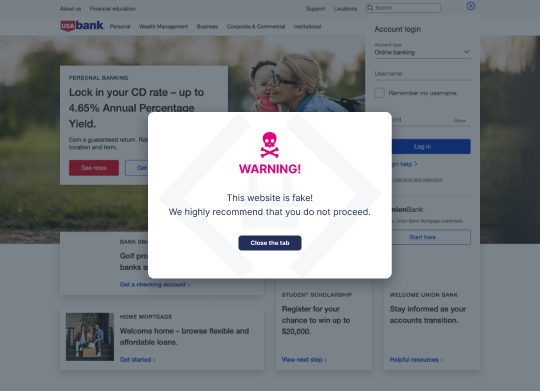
Imagine this scenario: An esteemed eCommerce player is facing a sophisticated cyberattack. The malefactors replicate their website to deceive customers into divulging sensitive data. If successful, the attack would be catastrophic for the business—and its customers. But there’s something the hackers weren’t counting on—a well-implemented cyber threat intelligence framework. With the ping of a rapid alert, the eCommerce organization identifies the counterfeit domain, mitigates the threat, and safeguards its customers’ data.
Recent data accentuates the severity of such threats. Cybersecurity Ventures predicts that cybercrime will inflict costs of $8 trillion annually in 2023, with the eCommerce, fintech, and online payment sectors particularly vulnerable. This enormous figure represents direct financial implications, business disruptions, and trust erosion.
This article explores the urgency of adopting a cyber threat intelligence framework, offering actionable steps and insights to fortify digital operations. We’ll also discuss how integrating solutions like Memcyco can bolster defenses against malicious entities.
Why Your Organization Needs a Cyber Threat Intelligence Framework
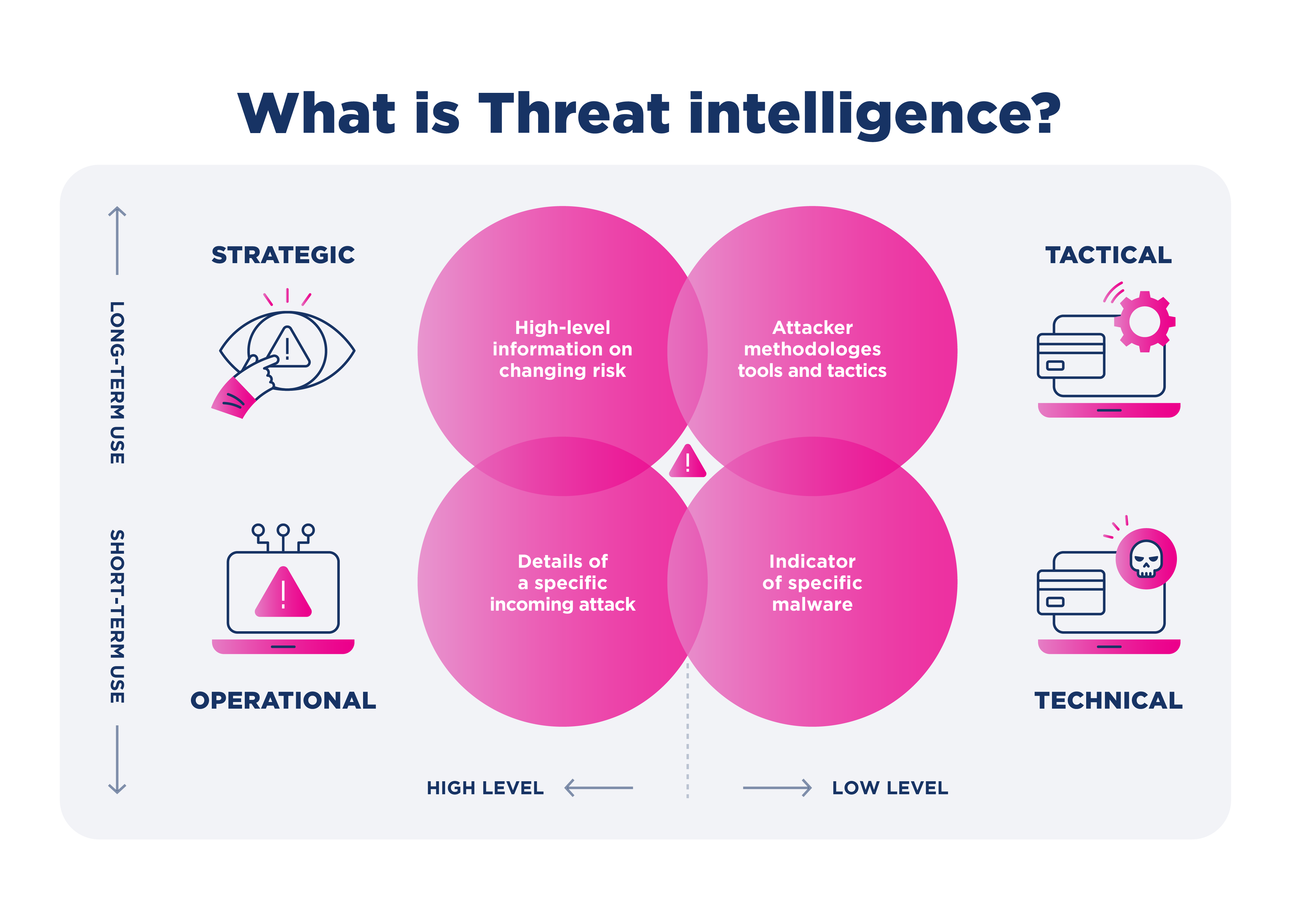
A cyber threat intelligence framework is a structured methodology that combines technology, processes, and human expertise to gather threat intelligence. Its goal is to proactively identify, analyze, and counteract cybersecurity threats. Organizations are armed with actionable insights by consistently gathering and interpreting data about potential cyber adversaries and their tactics, allowing them to anticipate and mitigate threats before they escalate.
The increasing frequency and sophistication of cyber attacks underscores the need for this framework. In a landscape where even minor vulnerabilities can lead to major data breaches, a proactive stance, provided by the intelligence framework, offers a significant advantage.
Without a robust cyber threat intelligence framework, organizations often find themselves in a reactive mode, perpetually addressing breaches and vulnerabilities. This leads to immediate tangible losses and can erode customer trust and tarnish the brand’s image. The repercussions of neglecting such a proactive approach can be profound and long-lasting, including damages to finances and reputation, lawsuits, fines from non-compliance with regulations, and even going out of business entirely.
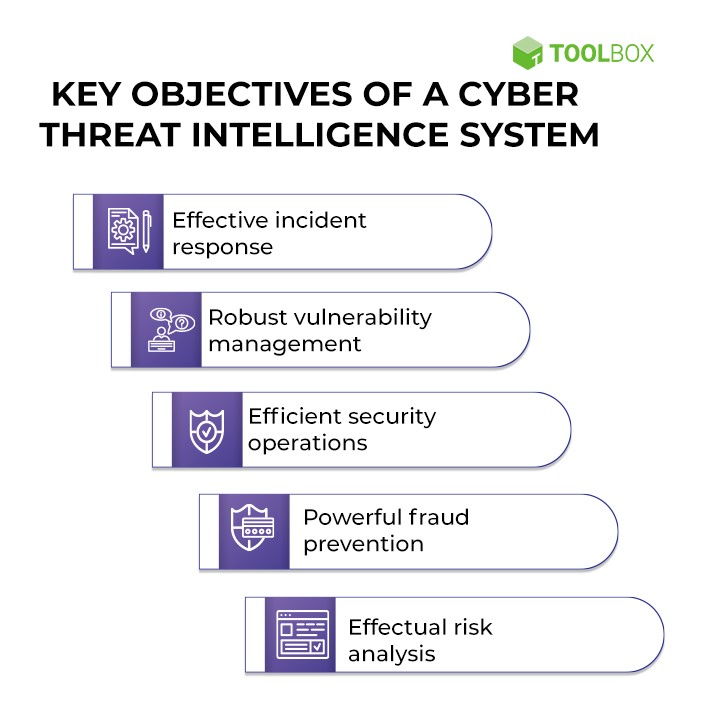
Various stakeholders within an organization can harness the power of a robust cyber threat intelligence framework:
- CISOs can utilize their insights to refine cybersecurity strategies.
- By recognizing patterns and anomalies, fraud teams can proactively detect and prevent fraudulent activities.
- Online business teams can ensure that security measures complement the user experience, balancing protection and usability.
A cyber threat intelligence framework isn’t a mere advantage—it’s essential for secure and sustainable business operations.
6 Steps to Building a Cyber Threat Intelligence Framework
If you’re ready to implement a cyber threat intelligence framework to protect your organization, here’s a simple guide showing the six steps you must take.
Step 1: Identification of Threat Vectors
Before you can defend against cyber threats, it’s vital to recognize where they might come from. Identifying potential threat vectors and actors helps businesses understand their digital vulnerabilities. To do this, liaise with your security teams and utilize cybersecurity platforms to spot patterns and trends that hint at possible attack vectors. Recognizing threats such as phishing campaigns, malware distribution sites, website spoofing, and even rogue insiders can significantly elevate your defense stature.
Step 2: Intelligence Gathering
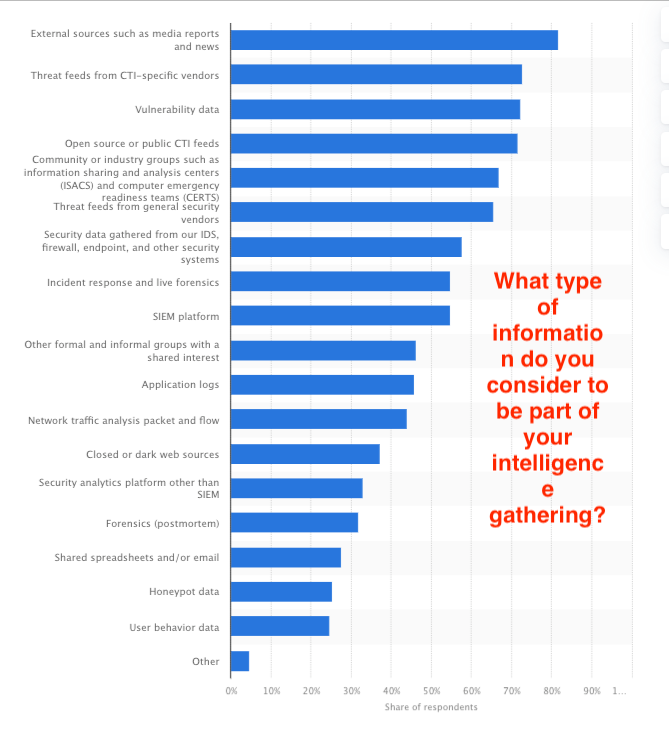
Once you’ve identified potential threats, you must gather actionable intelligence about them. Employ a mix of open-source intelligence (OSINT) tools, industry feeds, and proprietary platforms to collect comprehensive data. Your InfoSec team should have up-to-date insights to help this stage move forward with the latest intelligence.
Step 3: Data Analysis
After gathering intelligence, it’s pivotal to make sense of the data. Collaborate closely with fraud teams, as they can bring in a unique perspective on potential financial vulnerabilities and anomalies. Use advanced analytics tools to sift through the data and identify patterns or anomalies. This stage aims to convert raw data into actionable insights, ensuring threats are understood in context and magnitude.
Step 4: Strategy Formulation
Armed with insights, it’s time to formulate a cohesive security strategy. Central to an effective strategy is the creation of countermeasures for the identified threats. Whether it’s through enhanced authentication protocols, stricter access controls, or state-of-the-art encryption methods, the aim is to build a formidable first line of defense.
However, no defense is impervious. This is where incident response plans come into play. These contingency plans outline the step-by-step actions to be taken in the event of a breach, ensuring swift action and minimizing potential damage. From immediate threat neutralization to communication protocols informing stakeholders of the breach, every detail matters.
Given the fluid and dynamic nature of cyber threats, a static strategy won’t suffice. It’s essential that the security strategy remains adaptable, with provisions for periodic reviews and updates. To achieve this, regular consultations with security and IT teams are needed. Their on-the-ground experience and expertise can provide valuable feedback, ensuring the strategy remains comprehensive, current, and capable of withstanding the latest threat vectors.
Step 5: Implementation
A strategy is only as good as its execution. The next step involves implementing the devised plans. This could range from patching software vulnerabilities to deploying advanced intrusion detection systems. At this stage, seamless coordination between the digital business teams, fraud teams, and security personnel is critical to ensure strategies are implemented with precision, and that vulnerable systems are bolstered from potential attacks.
A unique solution to detect and mitigate website spoofing like Memcyco is an invaluable addition to your cyber threat intelligence tech stack. Providing real-time protection against website spoofing and brandjacking, Memcyco’s agentless solution issues real-time Red Alerts to users visiting spoofed websites, and provides organizations with complete visibility into the attack, allowing them to take remediating actions quickly.
It’s also the only solution addressing the critical “window of exposure” between when a fake site goes live and when it is taken down. Not covered by existing solutions, this time window can leave organizations vulnerable to data breaches, financial losses, and reputational damage, while their customers become targets for identity theft and financial harm.
Having real-time threat intelligence for a spoofed website creates a formidable proactive stance in your cyber threat intelligence framework.
Step 6: Continuous Monitoring and Improvement
The digital threat landscape is constantly evolving. What works today might be obsolete tomorrow. Therefore, it’s essential to implement a cyber threat intelligence framework and continuously monitor and improve upon it. Regular audits, system checks, and feedback loops can ensure your defenses remain impenetrable.
Comprehensive, structured responses become imperative as cyber threats grow in complexity. Incorporating these steps into developing your organization’s cyber threat intelligence framework will pave the way for a robust and dynamic defense system.
Integrate Memcyco into Your Cyber Threat Intelligence Framework
Navigating the complexities of cyber threats requires an effective and evolving strategy. As we’ve highlighted, crafting a comprehensive cyber threat intelligence framework is crucial for safeguarding digital assets, protecting customer interactions, and promoting business growth.
The dynamic landscape of cyber threats, however, demands innovative solutions. Addressing the menace of website spoofing remains critical for organizations aiming to build trust and ensure security. Integrating Memcyco’s solution into your cyber threat intelligence framework is not just a proactive measure; it’s a game-changer. By offering unparalleled real-time protection against the growing challenge of website spoofing and brandjacking, Memcyco redefines digital trust.
If fortifying your organization’s cybersecurity is a priority, it’s time to take the next step. Reach out to Memcyco to learn how its cutting-edge solution can be the linchpin in your cyber threat intelligence framework.