Fraud has moved from an IT issue to a boardroom topic across industries. The more complex the fraud, the bigger the financial, brand, and customer risk.
E-commerce fraud, for example, is expected to cost from $44.3 billion in 2024 (when it was last reported) to $107 billion in 2029, a 141% increase. And that’s just one industry. When the stakes are this high, you can’t blindly chase threats.
Instead, you need a holistic strategy like Enterprise Fraud Management (EFM) to detect, prevent, and respond to fraud in real-time.
What is Enterprise Fraud Management (EFM)?
Enterprise Fraud Management (EFM) is a unified, intelligence-driven approach to detecting, preventing, and mitigating fraud across a company’s entire system. It involves integrating and centralizing advanced tools, processes, and policies to speed up prevention and response workflows.
As fraud schemes get more sophisticated with AI-powered scams, Phishing-as-a-Service (PhaaS), and multichannel fraud attacks on the rise, traditional fraud prevention methods are no longer enough. Legacy systems that operate in silos can’t keep up with the scale and complexity of modern fraud, leaving organizations at risk of financial losses, regulatory fines, and reputational damage.
Unlike outdated methods that rely on isolated rules-based detection, modern EFM solutions use AI-powered analytics, behavioral monitoring, and real-time threat intelligence to identify fraudulent activity across all channels— even before damage occurs.
The Top Fraud Threats Enterprises Face Today
Phishing and Smishing
Phishing and smishing are two of the most common fraud methods, but AI has made them much more sophisticated. Instead of poorly written, easily recognizable scam emails, fraudsters use AI-powered large language models (LLMs) to generate personalized and contextually accurate phishing messages.
Memcyco works seamlessly with EFM platforms by adding real-time visibility into phishing attempts, attackers, and targeted victims, strengthening the fraud management strategy. Moreover, with its agentless, scalable deployment, Memcyco enhances an organization’s ability to prevent fraud without disrupting existing fraud detection systems or customer experiences.
Web Spoofing and Brand Impersonation
Fraudsters create near-perfect replicas of legitimate websites to trick customers into revealing sensitive information. But in 2025, AI is making these scams more convincing than ever. Machine learning models can now generate fake websites in real-time, mimicking legitimate UI designs and logos and adjusting content dynamically based on a victim’s browsing behavior.
These AI-powered tools allow fraudsters to create and scale brand impersonation attacks faster than ever. This makes it harder for customers to tell the difference between real and fraudulent sites and for brands to stop them before any damage is done.
Account Takeover (ATO) Fraud
ATO attacks are getting more dangerous as cybercriminals find new ways to bypass traditional security measures. Since the explosion of GenAI, fraudsters have been using session hijacking techniques to take control of active user sessions, potentially bypassing traditional login barriers.
Multifactor authentication (MFA), once considered a strong defense, is now being bypassed through real-time phishing proxies, SIM-swapping, and OTP interception. Man-in-the-middle (MitM) credential relay attacks (like those leveraging EvilProxy) have become a major enabler of MFA bypass, allowing attackers to intercept and relay authentication tokens in real-time. AI also plays a role here, enabling fraudsters to automate large-scale credential-stuffing attacks and even predict or manipulate authentication responses.
Essential Features of Enterprise Fraud Management (EFM) Tools
Implementing an effective EFM strategy requires selecting the right tools. While many tools address different aspects of fraud management, there are also comprehensive EFM platforms that cover various features within a single solution. Where are the key components your Enterprise Fraud Management (EFM) strategy should include:
Fraud Detection and Prevention
A good EFM platform should have real-time fraud detection, including spoofing and phishing detection systems that block fraudulent websites or communication attempts. AI-powered fraud systems monitor user behavior and transaction patterns to spot anomalies that indicate fraud so you can act fast.
However, most fraud prevention solutions focus on transactional fraud, analyzing and mitigating risks after fraud has already started. Leaving a critical gap, the pre-transaction stage, where phishing and impersonation attacks happen before any fraudulent activity has occurred.
That’s where Memcyco comes in. Unlike traditional tools that react after fraud attempts are made, Memcyco is a specialized fraud prevention layer that stops certain types of fraud before it reach the transaction stage. These include phishing, website spoofing, and digital impersonation scams. These AI-driven solutions uncover and disrupt phishing and impersonation attacks before they escalate into financial fraud.
Threat Intelligence
Identifying fraud effectively requires awareness of emerging threats. Threat intelligence platforms collect data from multiple sources and provide fraud feeds and cyber threat monitoring tools. These give organizations insight into new fraud tactics and attack vectors to stay ahead of the fraudsters. However, as threats become more complex and multi-faceted, these platforms should integrate with other fraud detection systems to share intelligence and create a single approach to threat response.
User Behavior Analytics
An often overlooked component of modern fraud management is user behavior analytics (UBA). UBA tools monitor and analyze user behavior to identify anomalies that may indicate fraud and speed up identity threat detection and response. Whether it’s an account takeover (ATO) attack or credential stuffing, UBA helps spot subtle, sophisticated fraud attempts that would otherwise go undetected. By analyzing real-time behavior patterns such as login locations, IP addresses, and transaction types, UBA tools add an extra layer of fraud detection so you can spot fraudsters who have already bypassed your initial security controls.
Identity Verification
Modern EFM platforms include Know Your Customer (KYC) tools and biometric authentication to prevent unauthorized access. These solutions ensure only legitimate users can interact with your services, adding an extra layer of security in identity access management. As account takeovers become more common, robust identity verification measures help reduce the risk of credential theft or misuse.
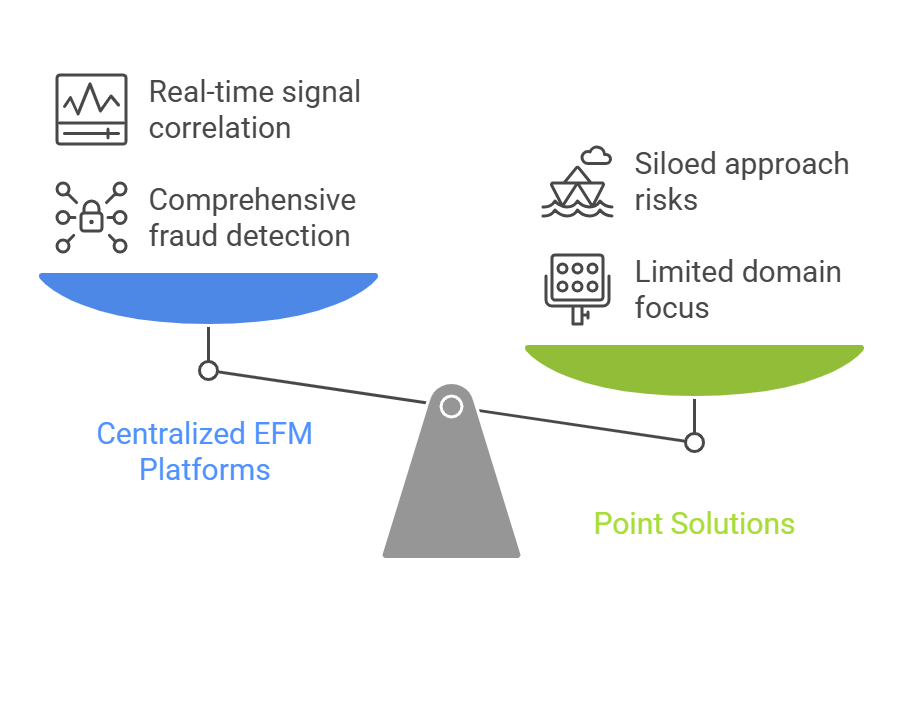
Centralized EFM Platforms vs. Point Solutions: The Key Differences
1. Siloed vs. Unified Insights
Point solutions are specialized tools designed to address a single type of fraud threat, such as phishing detection or transaction monitoring. They are excellent in their own domains. Still, they can’t connect the dots across different fraud signals. This siloed approach can lead to missed connections between seemingly unrelated fraudulent activities, resulting in delayed or ineffective responses.
On the other hand, centralized EFM platforms combine multiple fraud detection, prevention, and monitoring capabilities into one solution. These platforms enable you to correlate multiple fraud signals (from phishing to account takeover and credential stuffing) across different channels.
2. Attack Vectors
Modern fraud is rarely a single vector; it’s often a complex campaign combining different fraud techniques. For example, a phishing attack may be followed by account takeover (ATO) attempts using stolen credentials, which may be used for financial fraud.
While traditional point solutions focus on a single vector, centralized EFM platforms powered by AI-driven fraud detection can identify and respond to these multi-layered attacks. They correlate data across different touchpoints in real-time, giving you a single view of your fraud landscape.
3. Rules-based vs. Dynamic Systems
Point solutions rely on traditional rule-based systems that can no longer keep up with the scale and complexity of modern fraud tactics. On the other hand, AI-powered systems like those used in Memcyco’s real-time detection technology allow businesses to respond quickly and effectively to emerging threats.
AI allows real-time correlation of multiple fraud signals, spot patterns and anomalies across channels (web, mobile, call center), and provides faster, more accurate fraud detection. This holistic AI-driven approach ensures businesses are ready to counter fraud as it happens, safeguarding customer trust and financial assets.
Best Practices for Enterprise Fraud Management (EFM)
To effectively combat fraud, enterprises must prioritize automation and orchestration. AI-driven fraud detection systems can analyze behavior in real-time, reducing false positives and enabling teams to focus on real threats. By integrating fraud detection with case management and security orchestration tools, organizations can automate responses—such as blocking transactions or escalating cases—accelerating investigations and minimizing manual effort.
The threats against fraud detection and cybersecurity are increasingly interrelated. A strong defense against fraud now requires a unified approach where fraud and security teams share insights, data, and intelligence. By collaborating and breaking down silos, enterprises can improve their ability to discover fraud activity that may stem from a broader cybersecurity breach and vice versa. This joint effort ensures a more holistic response to complex fraud scenarios.
Protecting Your Brand and Customers
Fraud is no longer just a financial risk. It’s a risk to brand reputation and customer trust. As fraudsters become more sophisticated with web spoofing, phishing, and account takeovers, businesses must move beyond traditional fraud prevention.
Memcyco addresses a critical yet often under-protected layer of fraud prevention: the pre-transaction stage. While traditional fraud management solutions focus on monitoring and analyzing transactions, Memcyco safeguards organizations by stopping phishing and impersonation threats before they evolve into full-blown fraud incidents.
Rather than replacing broader Enterprise Fraud Management (EFM) tools, which primarily identify transactional fraud and analyze post-event data, Memcyco complements them by detecting and stopping digital impersonation-based fraud attempts before they result in credential theft and ATO.
With its seamless, agentless deployment, Memcyco scales effortlessly alongside your existing EFM solutions, ensuring immediate value without disrupting business continuity or customer experience.
















![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)

