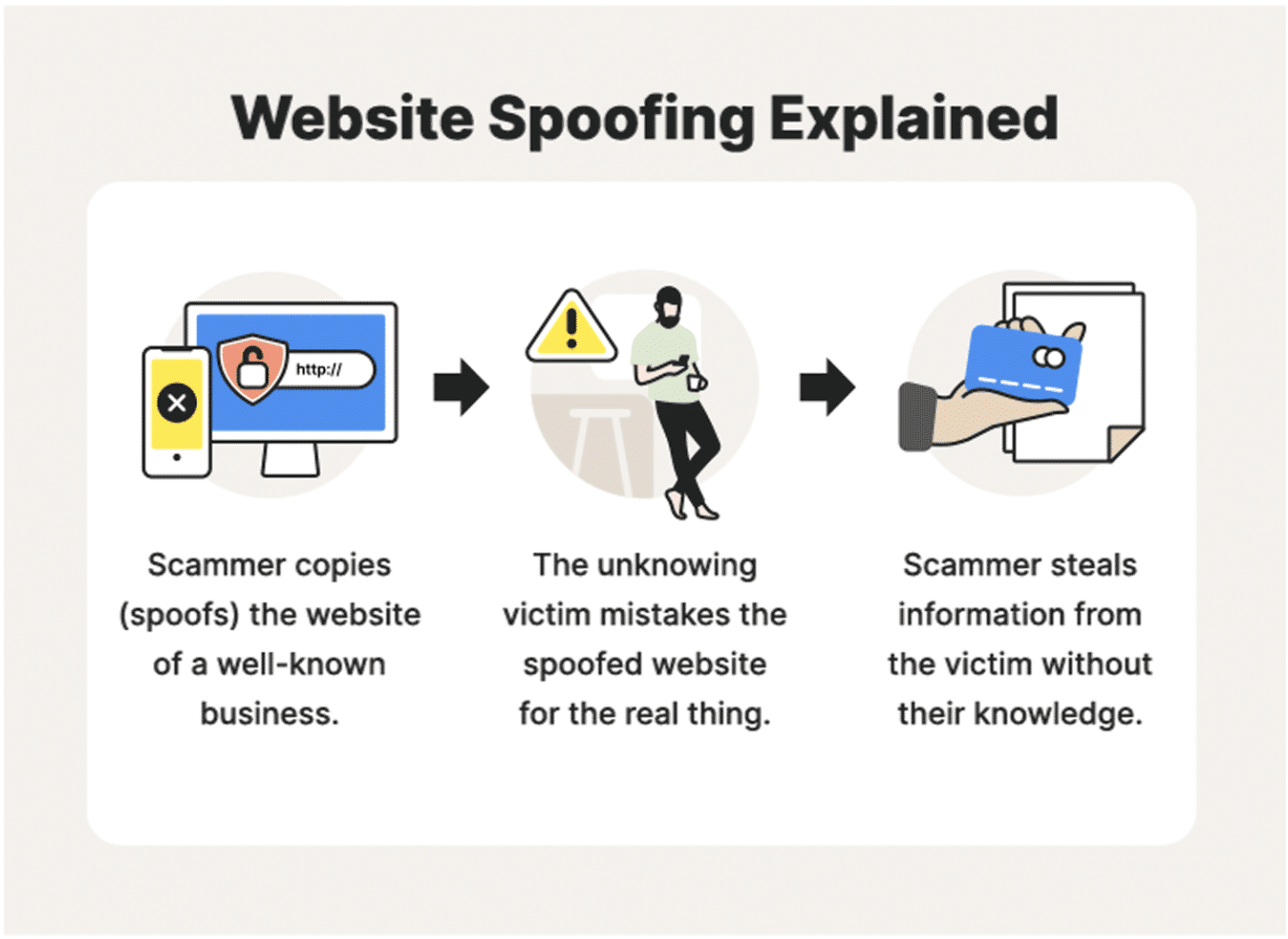
Chances are you’ve heard of spoofing, since it’s one of hackers’ most successful and frequently employed tactics today, constituting 50% of all cybercrime. Spoofing refers to deliberately falsifying contact information (phone number, email, and websites) to mislead victims into thinking hackers are legitimate sources, thus sharing their personal information with them, which leads to other crime types.
One reason this tactic is so popular is that the cost of entry for hackers is low while the potential for profit is high. Brand impersonation, for example, fits this category and cost businesses $4.35 million from fraud in 2022 alone.
The result? Fear of getting tricked into revealing sensitive personal and corporate information to impostors, which in turn results in loss of consumer trust. And that’s not all; while phishing fraud incidents continue to spiral, the resulting lack of engagement with legitimate brands due to cybersecurity fears impacts revenue by up to 20%.
The way forward is to regain consumer trust by stopping hackers upon any attempt to compromise your website or email domain name. But current security solutions that focus on securing infrastructure aren’t necessarily helping to prevent phishing spoofed websites and domains. Hackers stay under the radar by targeting end-user behavior, not technology.
This article gives you a quick overview of spoofing and how domain spoofing works. You’ll discover a new approach to help your security teams find impersonators that target your customers, prospects, employees, and partners in domain spoofing attacks.
Domain Spoofing In a Nutshell
Spoofing is a broad term describing hacker impersonation in cybersecurity.
- Hackers act like a person or computer system end users know online.
- Impersonating helps hackers to gain the trust of victims. End users believe they are interacting with a person or brand they know.
- Spoofing attacks may deploy malware in your system, direct users to a fake phishing page, and steal user data.
- The most common spoofing attacks are IP address attacks, email phishing attacks, and website domain attacks. They vary in volume, frequency, and method. IP spoofing attacks like DDoS or Man-in-the-Middle are high volume and attack tech vulnerabilities. Domain spoofing attacks are low volume and attack human nature.
Domain spoofing targets your brand and end users.
- Phishing attack campaigns use fake domains that look like your website and email to convince consumers and employees that the communication is coming from a legitimate source.
- Hackers use social engineering tricks to exploit the brand trust you’ve built. In other words, the hacker pretends to be your brand, taking advantage of your reputation and relationship with your users to gain their trust.
- End-users and visitors think that they’re talking to a trusted source, but they’re being sent to a fake site.
- Once in your network, it’s often too late. Your sensitive data is compromised, and your brand reputation is damaged.
Why Are Domain Spoofing Attacks On The Rise?
With security teams struggling to prevent fraudsters from using brand names, domain spoofing and phishing attacks were three times more common in 2021 than in the two previous years, according to the APWG. Here are a few reasons why phishing attacks are on the rise:
- Affordable domain names are widely available to hackers at low costs.
- SSL certification is easy to fake. 84% of phishing sites use SSL, so the SSL lock sign on the top left of sites doesn’t necessarily help users to distinguish safe websites from compromised websites.
- Advanced phishing attacks abuse trusted platforms like AWS, Google, SharePoint, Adobe, Backblaze B2, DigitalOceanSpaces, Weebly, and WeTransfer.
- Anti-spam tools can’t detect malware in fake attachments or links sent via impersonated emails and SMS.
- Hosts have a negligent attitude to phishing, leaving the burden on end users to identify them.
- End users have no good indication or tools to identify fakes and attempts of fraud. They tend to rely on ‘instinct’ and hesitate to click on links for fear of impostors.
Examples of famous phishing attacks
- Facebook and Google ($100 million). Hackers used fake invoices by Quanta (a Taiwan-based vendor) to trick both companies into sending them money between 2015 and 2018.
- Crelan Bank ($75.8 million). Hackers compromised the email account of a high-level Belgian bank executive and used it to convince employees to transfer money into their fake account until discovered by an internal audit.
- FACC ($47 million). Hackers posed as the head of an Austrian aerospace parts maker, using email to trick an employee in the accounting department into transferring money to their fake acquisition project account.
- Colonial Pipeline (>$4.4 million). The American fuel supplier was forced to halt operations after malware compromised its network and billing systems. It all started with a phishing email used to gain access to an employee’s password. The company paid $4.4 million in ransom to hackers to resume operations.
- Upsher-Smith Laboratories ($39 million). Hackers impersonated the CEO of this Minnesotan drug company via email to trick the Accounts Payable Coordinator into transferring $50 million to a fake lawyer’s account. Eight of the nine transfers requested were sent.
- Ubiquiti Networks ($46.7 million). This computer networking company was scammed to transfer funds to fake accounts in Russia, Hungary, China, and Poland. Hackers impersonated the company’s CEO and Lawyer to trick the company’s Chief Accounting Officer into making a series of transfers to close a secret acquisition.
How Domain Spoofing Works?
The most common ways that impersonation attacks happen are:
- Fake domains – Hackers send emails with fake domain names that seem real. They use brand visuals, logos, and designs that make the email look legitimate and impersonate individuals from your company to entice end users.
- Fake websites – Hackers create fake websites with imperceptible changes compared to the legitimate ones they are impersonating. If end users don’t notice, hackers attack by acting like your brand.
- URL substitution – Hackers alter characters in domain names, making spoofed domains hard to detect. Fraud can happen when end users are tricked into using the fake website or responding to a fake email.
- Cloaked URLs – Hackers use short or reader-friendly URLs for local redirects. Fraud can happen when end users don’t realize it’s a fake site, link, or person.
- Cross-domain embedding – Hackers use this in ad tech: They create two websites to overlay fake content on an ad exchange of premium publishers–one with low traffic, high-quality content, and the second with high traffic, low-quality content. Fraud can happen when advertisers click on fake premium URLs and enter data.
Recognizing Spoofed Websites to Prevent Phishing Attacks
Hackers are adept at spoofing websites. Visual cues like SSL locks are easy for them to copy, rendering them useless against impersonation. Let’s see what you can do instead to revert the phishing trends:
Current state:
Fake websites are found too late because:
- It’s easy for hackers to replicate a legitimate business’s logos, branding, and visual design today.
- Cyber tools aren’t detecting them. Hackers guide your users to enter financial details and other personal information. They intercept data and reap the benefits.
- Security teams don’t detect in time and just using secure connections doesn’t protect your business from fraud. Hackers work outside your perimeter to stay under the radar on all browsers.
- End users don’t have a reliable way to distinguish authentic from fakes.
What’s needed?
We propose a new way to give both security teams and end users the ability to recognize what’s authentic. With a proof of source authentication solution like Memcyco’s watermark, you can boost your end-user confidence and brand trust for more clicks on your links:
- Higher confidence – Make it easy to confirm that all sources are real, not fake.
- Pre-emptive protection – Notify upon any event that compromises your domain, alerting your security teams upon any attacker attempt to copy the site or phish users.
- Instant visual proof – Ensure visual cues aren’t forgeable by hackers by marking all your sites, landing pages, and campaigns with a unique, unforgeable watermark for visual proof of authenticity.
- End user trust – Reduce fear of fakes at every communication touchpoint and alert your end-users in real-time of any potential cybersecurity risks before hackers attack them.
Empower Your Customers to Interact Freely, Without Fear
Ultimately, we’re all striving for a free digital world where businesses and users can engage and transact in full confidence, without fear. But domain spoofing is hindering many businesses from bringing this vision to life, with long-lasting adverse effects for your brand. Attacks ruin your reputation, while user fear erodes your consumer trust, preventing them from interacting with you online. This impacts your revenue and bottom line with higher churn rates, lower campaign conversions, and higher compensation and recovery costs. Your security teams need help to protect your brand from losing business, costly attacks, and increasing frustration among your customers and staff.
Schedule a demo to see how Memcyco’s Proof of Source Authenticity (PoSA) solution transforms your customer experience to foster trust and prevent domain spoofing with a single line of code.