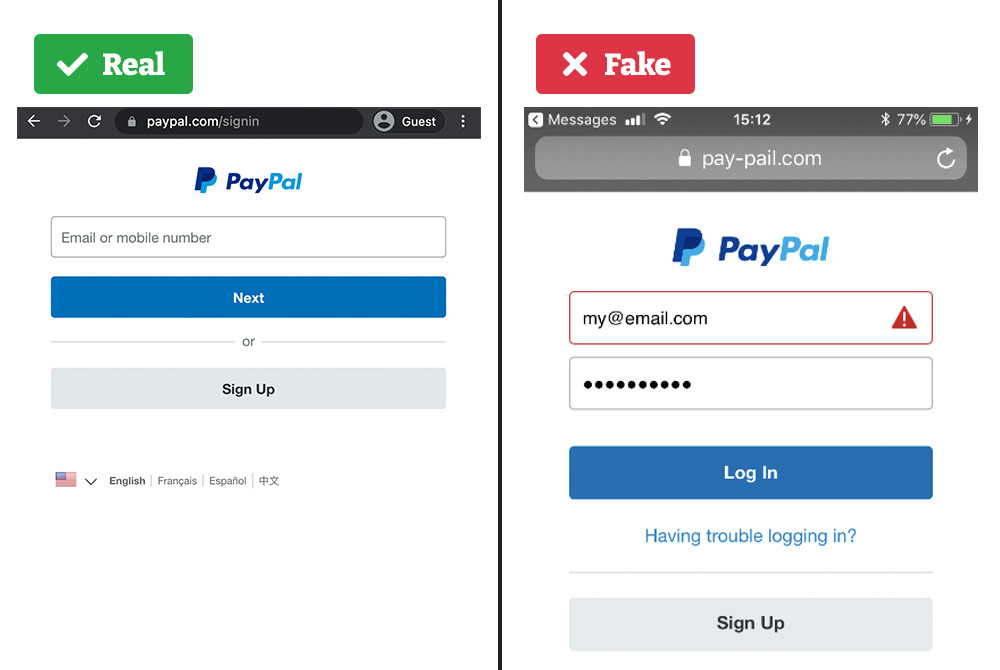
Some mornings start rougher than others. Imagine this: while still drinking your coffee, you get a message from a potential buyer on Facebook Marketplace or Craigslist about an item you posted for sale. They want you to pay before picking it up and offer to transfer the funds via PayPal. Not a bad start to the day, right?
The polite buyer sends you a link to (supposedly) PayPal so you can send them a payment request. You click through and see a login screen. It looks like the official PayPal website, with the logo, copyright information, and everything. You start typing in your email address.
Suddenly, the caffeine kicks in. You realize that you’ve just stepped into a potential scam, and the website you’re browsing is actually a spoofed one.
Website spoofing as part of online fraud campaigns is sadly common, costing online businesses millions each year—and consumers a whopping $8.8 billion in 2022 in the US alone. Not only do businesses suffer the direct financial costs of spoofed websites—such as lost sales, customers, and customer trust—but growing regulatory trends place liability on businesses to reimburse customers if their data and funds are stolen by a fake website.
In the UK, EU, and Singapore, regulatory authorities have set guidelines for banks and PSPs to implement, aiming to curb financial scams and related losses. A recent report from the Australian Competition & Consumer Commission detailed $3.1 billion lost to cyber scams in 2022, and called for a united front between law enforcement, government, and the private sector to more effectively combat threats like website spoofing. The US is soon to follow with similar regulations, making website spoofing prevention more critical than ever.
So, how can you tell if your website is a candidate for spoofing? And what can you do to protect your digital assets from unauthorized duplication? Let’s start at the beginning.
What is website spoofing?
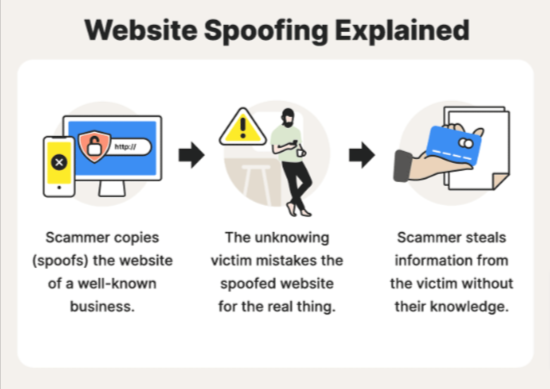
Website spoofing, also known as website cloning, is a malicious brand impersonation tactic often used in online fraud campaigns. It entails publishing a nearly identical copy (clone) of the original website frontend, aiming to mislead the users who land on it to assume it is the original and genuine brand website.
Malefactors usually create numerous fake websites hosted on shady cloud services and compromised servers. They then send unsuspecting users to these spoofed websites through phishing, smishing, social media brand impersonation, paid search ads, and even QR codes.
The danger of website spoofing to organizations is twofold:
- First, organizations are unaware of spoofing taking place until a customer reports it, or when they see it via analytics. Often they don’t see who or how much their customers were affected, or the damage to their brand reputation.
- Second, the “window of exposure” during a website spoofing attack is a significant security concern. It represents the duration between when a counterfeit website is likely detected by standard Threat Intelligence Solutions and its eventual takedown. During this critical period, unsuspecting customers can be easily lured to the fake site, leading to potential monetary losses, data breaches, and exposure of personal identities. Alarmingly, many companies currently lack the insight to determine how many of their customers have fallen prey during this vulnerable window.
A spoofed website may be possible to take down using dedicated website takedown services, but the pages are sometimes hosted on compromised web servers and even hacked endpoint devices.
Memcyco offers an out-of-box solution during the critical “window of exposure” – the time it takes to identify a fake website and until that site is taken down (if at all). It’s a unique service, alerting the customer in real-time with red alerts, and empowering the organization with instant insights of not only the potential attack, but the scope of damage and customer details of exposure.
Website Spoofing vs. Domain Spoofing
Though the terms are often used interchangeably, website spoofing and domain spoofing are different malicious tactics often employed concurrently in multi-pronged brand hijacking attacks.
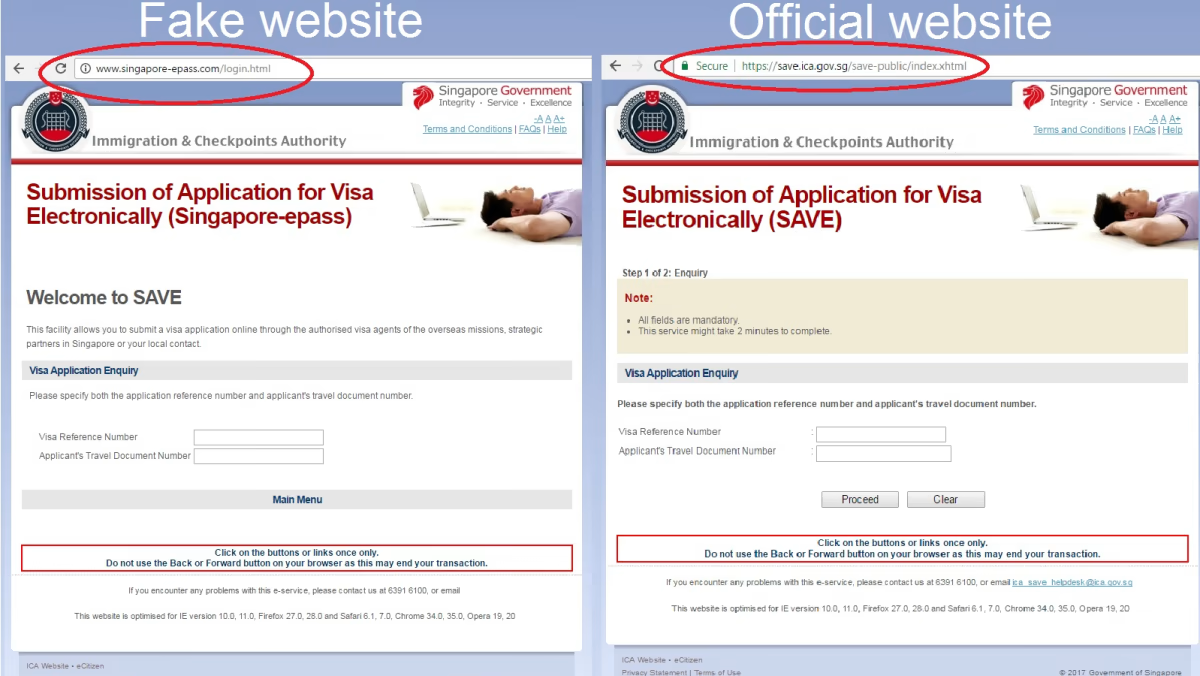
Domain spoofing pertains to typosquatting, URL hijacking, DNS record tampering, and other attack types related to the domain name of the impersonated brand. On the other hand, website spoofing refers to scraping or manufacturing a clone of the targeted brand website’s frontend content, including components such as the logo, social media links, and the fields where the victims may submit their credentials.
A spoofed version of a website such as the PayPal login page can be hosted on a misleading domain like paypai.biz. But it doesn’t have to be. It can instead be a subdomain or simply an IP address of a hijacked web server hosting the spoofed website. Hackers use this tactic to add “credibility” to their malicious act.
For example, hackers will conduct a website spoofing for a certain bank, and then will hack another credible organization website’s CMS (such as safe-baking-association.com), placing the spoofed website/login form on a subdomain/subpage of that site, so that the victim users will not suspect anything untowards—and even the hosting site will not have a clue.
A very important difference between website spoofing vs. domain spoofing is that all Threat Intelligence (TI) tools are essentially not protecting against website spoofing at all, but only protecting against Domain Spoofing.
This is because TI solutions are essentially Search Engines that crawl the web looking for partially identical or partially similar domain addresses, the kind that are used by hackers to fool victims so that they will not notice a slight change in letters, signs or numbers used to differentiate the address from the original spoofed brand website. But if the hacker chooses to use a completely different address, or at least one that the TI tool could not predict (such as in the previous example), then TI tools will fail to protect against Website Spoofing.
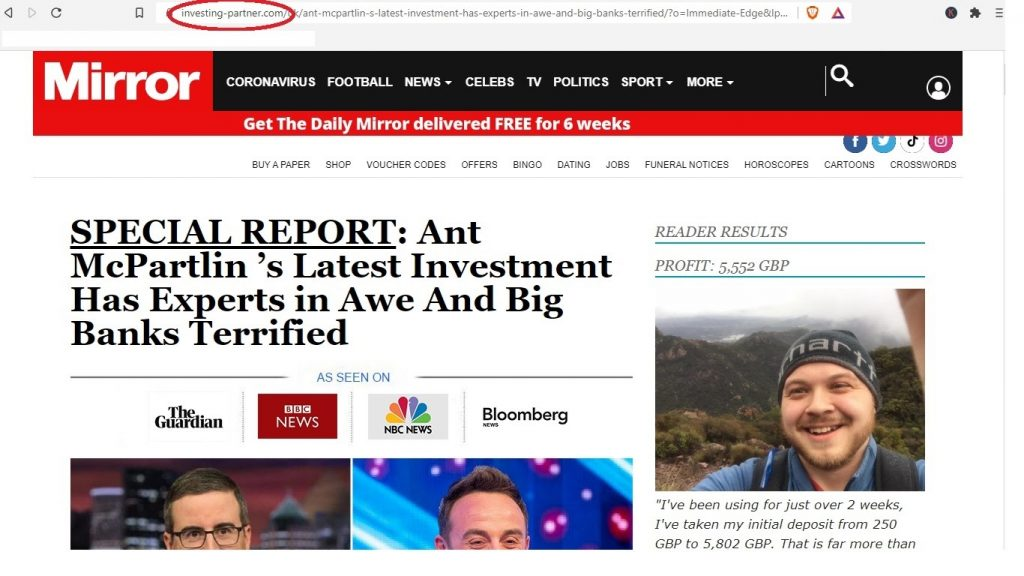
What are the risks of website spoofing?
Website spoofing is usually just one tactic malefactors employ in brand impersonation attacks. The spoofed website is the point of impact where the fraud is successful—users are fooled into believing it’s genuine and taking actions like signing in or downloading a file.
So when discussing the risks associated with website spoofing, we’re talking about the risk of brand impersonation attacks that conceal a malicious payload or harvest victim credentials using spoofed websites. Risks of website spoofing include:
- Legal expenses, regulatory fines, and associated costs kick in only when a spoofed website has been actively used to defraud users. By that juncture, the damage is not only monetary. First and foremost, the pain businesses feel is the theft of funds, particularly when it affects their customers. This infliction doubles; companies have to compensate for the stolen funds and grapple with the ensuing reputational damage. Such damage doesn’t merely exist in isolation. It ripples out, influencing customer engagement, altering purchasing habits, escalating customer churn, and more. These financial ramifications, coupled with the tarnished reputation, can deter potential customers from engaging with the company, fearing for their own security.
- Breach escalation is usually a risk for fraud victims whose identity may be stolen and whose personal information may become public. However, by thoroughly scraping your website, malefactors may gain insight and knowledge about your website security measures, and how they can be overcome to steal sensitive information or inject harmful code.
- Mitigation and remediation costs are another source of revenue losses and overhead. Removing the spoofed website using official channels is a painstaking game of whack-a-mole, as malefactors tend to create multiple clones of the same website. In addition, finding which customers were impacted and notifying them is costly and complex if you don’t have the right website security and brand protection tools implemented.
- Loss of customer trust due to a successful brand impersonation attack can tarnish the brand’s reputation, lower its value to stockholders, and hurt business relationships with partners, especially in highly regulated industries.
Three Proven Ways to Prevent Website Spoofing
Once malefactors have successfully duplicated your website’s front end, there’s very little you can do to stop the brand impersonation attack on your brand and the fraud campaign against your clients. However, you can take steps to deter potential attackers from spoofing your brand website, discover when your website may be targeted for spoofing, and protect your users from falling victim to brand fraud.
Once malefactors have successfully duplicated your website’s front end, it often feels like it’s too little too late to combat the brand impersonation attack on your brand and the fraud campaign against your clients. Even if the fake site is detected promptly, significant damage, encompassing both monetary and data theft, occurs during that window of exposure (WOE). Many companies currently lack the means to curb this threat effectively.
Tools like Memcyco significantly mitigate this risk, significantly reducing the attack damage and impact. It achieves this through real-time detection, immediate alerts to potentially affected customers, and zero-day notifications to SOC teams, not only about the spoofing breach but also pinpointing the exact customers who may have been victimized. This proactive approach ensures that at least 90% of the potential attack damage is thwarted.
While it’s crucial to deter potential attackers from spoofing your brand website and be vigilant about signs of targeting, it’s equally vital to have systems in place that protect your users from the vast implications of brand fraud.
You can take steps to deter or slow potential attackers who spoof your brand website, discover when your website may be targeted for spoofing, and protect your users from falling victim to brand fraud. These steps are:
1. Complicate It for Attackers
There are a myriad of tools available that let anyone download a website fully. Most static websites can be downloaded with just a few clicks using the “highly advanced hacking tool” Internet browser. It’s right there in the menu.
The developers of modern websites take some precautions to protect their digital IP and website content from scraping. Consequently, hackers develop new and innovative tools to circumvent those basic best practices and solutions for website security.
To help combate an attack once it takes place, you can employ Memcyco’s PoSA suite, which uses multiple layers of protection that effectively minimizes the attack’s impacts and potential damage. Among its features is a unique and tamper-proof user alert overlay displayed on spoofed versions of your website, wherever they may be hosted. This alert will notify users that they may be accessing a fraudulent website and prevent them from taking any action on it.
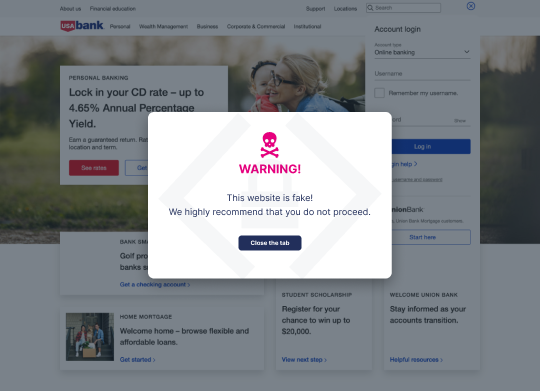
2. Detect Website Spoofing Threats
Scans, scrapes, and unauthorized access attempts to your website may get lost somewhere in server logs, never raising any red flags or alerts. Since website spoofing begins with malefactors probing and scraping your website, you need tools to alert you when this happens so you can take immediate action.
Moreover, to preempt the damage of a brand impersonation attack on your users, you need a solution that can alert you immediately of suspicious activity indicative of a compromised account.
With PoSA, you get complete real-time visibility into potential attempts to scrape your website and granular customer impact reports to investigate, prioritize and preempt potential damage.
3. Nurture Customer Trust in Your Genuine Website
You are not the only one hearing about the increasing cost of online brand fraud. Your customers are well aware of the dangers of the digital world, and many have developed a healthy sense of caution when clicking unfamiliar links or opting for offers that seem too good to be true.
A growing number of consumers, especially those who’ve previously fallen victim to online fraud, are now more hesitant to use digital services, including yours. Nurturing customer trust through customer education is challenging and expensive. The alternative is enabling your customers to immediately and quickly tell your genuine website from an imposter. Memcyco’s Watermark is an optional feature that customers can choose to enable as an add-on.This seal of authenticity is a unique, memorable, spoof-proof, and fully customizable watermark for your website—much like those that protect banknotes.
Spoof-proof Your Website with Memcyco PoSA
The main challenge with brand impersonation attacks that employ website spoofing tactics is that those spoofed websites are outside your security perimeter. By the time malefactors have created spoofed websites mimicking yours, it may be too late to take action.
Instead, you can take a proactive approach with Memcyco. Our solution provides real-time protection from website spoofing fraud to organizations and their customers by safeguarding the critical “window of exposure”; from when a fake site goes live until it is taken down. With agentless zero-day, AI-enhanced protection and real-time detection, Memcyco protects you and your customers against website spoofing threats.
To learn more, schedule a demo to see Memcyco in action.