The subscription model is a gift that keeps on giving. For customers, it offers convenience, flexibility, and continuous access to the services or products they love. For businesses, it creates a steady and predictable revenue stream, fosters long-term customer relationships, and provides valuable insights into user behavior.
But here’s a third player in the game that loves subscriptions just as much: fraudsters. Abuse of subscription policies is an increasingly concerning and costly business risk, with Netflix alone expected to lose over $12.5 billion by the end of 2024 due to password sharing.
Aside from sapping company revenue, subscription abuse requires an all-hands-on-deck approach to minimize damage, extending the workload of various departments. Most importantly, it impacts legitimate customers, who may lose trust in your brand completely. But what does that subscription abuse look like in practice? And what can you do to prevent it?
The Dark Side of Subscriptions: What to Watch Out For
Any subscription-based business (and its customers) can fall victim to subscription abuse, from digital streaming platforms to meal kit deliveries. Here are some of the most common types of subscription abuse to watch out for:
1. Account Sharing (aka Credential Abuse)
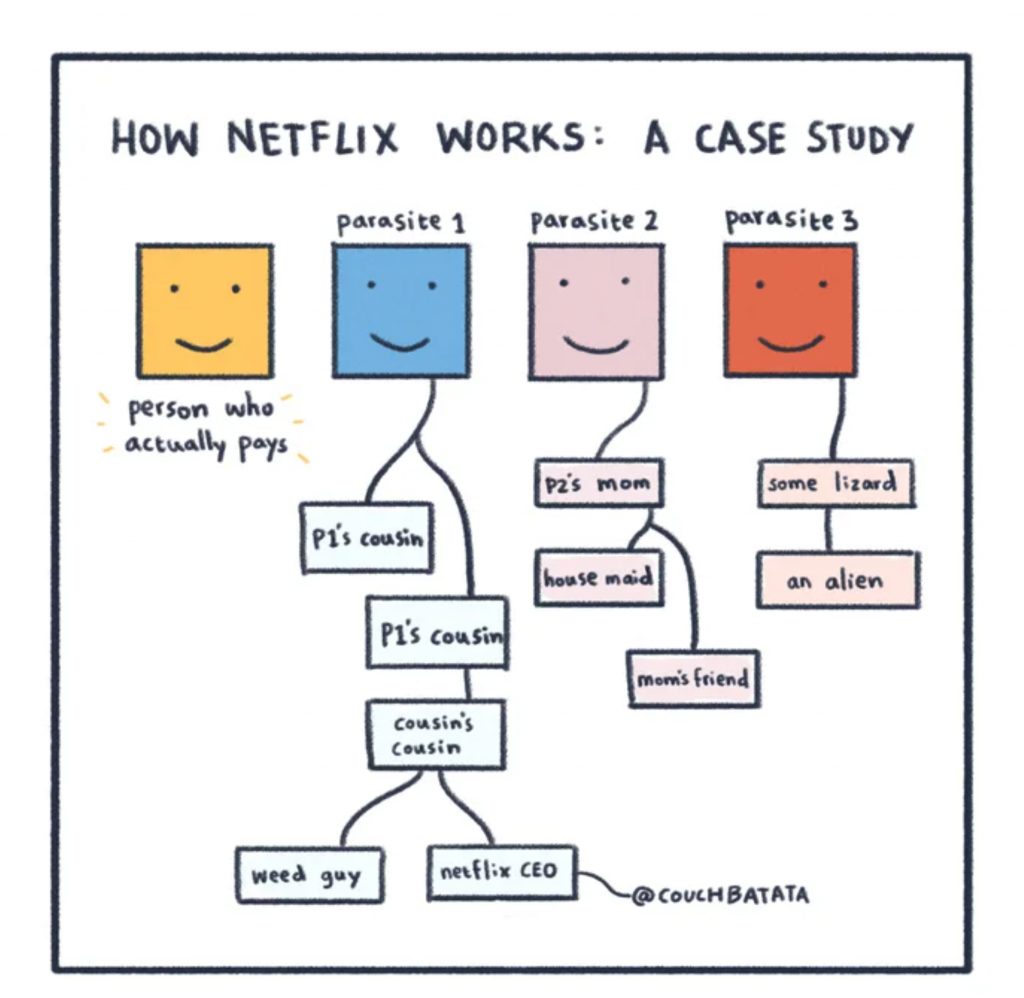
Perhaps the most well-known type of subscription abuse is when several people use a single subscription account, even though the account is meant for individual use only. Netflix, for example, estimates that more than 100 million households shared login credentials with friends and family outside their homes, even though this goes against the terms of service.
While a single shared account might not seem like a big deal to the people who choose to share their details, when multiplied across many users, it dramatically undermines your company’s revenue stream.
2. Family plan abuse
Family or group plans are designed to provide shared access at a discount to a service for a specific number of eligible users, usually part of the same household. However, this system can be exploited when individuals share their access with non-eligible users or even sell it to unrelated third parties, undermining the plan’s intended use and causing revenue loss for the service provider.
3. Free Trial Abuse (aka Trial Fraud) and Promotional Abuse
Many subscription services use free trials to entice prospective customers to try a service and (ideally) become paying customers. Free trial abuse is when the same person repeatedly signs up for your free trial using different email addresses or slight variations of their name to avoid paying for your service. This practice not only reduces revenue but also distorts your metrics.
A similar type of fraud is promotional abuse. It occurs when individuals create multiple accounts or use slight variations of their identity to exploit special offers and get discounts, special rates, or free times intended for other customers (such as first-time buyers). This type of abuse also leads to loss of revenue and skews marketing data, making it challenging to measure customer acquisition efforts.
4. Reselling subscriptions
Fraudsters exploit discounted subscriptions, including those acquired through promotions or free trials, by reselling access to third parties at a profit. This practice is often carried out on a large scale, resulting in significant revenue losses for subscription services and undermining the integrity of their pricing models.
5. Refund Fraud
Refund fraud is a type of scam in which customers falsely claim they didn’t receive your service or that it didn’t meet expectations. These customers request refunds while continuing to use your service. This problem is exacerbated by the growth of online communities that share tactics for exploiting refund policies, such as using multiple identities or exploiting loopholes.
6. Payment Fraud
Payment fraud is not specific to subscription abuse, but occurs frequently in this context as well. It happens in relation to subscription abuse when people use stolen credit cards or unauthorized payment methods to access subscription services. 80% of customers are concerned about having their credit card details stolen online, and for good reason. Buying lists of stolen credit card info on dark web marketplaces is relatively easy.
However, if the legitimate cardholder sees the fraudulent payment and requests a chargeback, your company will be left without payment and still having provided your service.
How dangerous can subscription abuse scams really be?
The most notable impact you’ll feel from subscription abuse is loss of revenue. But it’s not just about the direct financial hit—more profound effects can erode your company’s health over time.
For starters, subscription abuse also increases costs across various parts of your business. For example, supporting non-paying users and handling refunds and chargebacks consumes bandwidth, server capacity, and customer service resources. Over time, these costs add up, eat into your profit, and force you to allocate resources you could have used for revenue-growth activity. .
It also distorts user data, which is essential to inform business decisions. When your service is being abused, you might see, for example, inflated user numbers or engagement metrics that don’t translate into actual revenue. This distortion can lead to poor strategic decisions—investing in the wrong areas, misunderstanding your audience, or failing to identify real growth opportunities.
Lastly, it can erode customer trust. Legitimate, paying customers are the backbone of your business, and when they see others exploiting your service, it can create a sense of unfairness. They might wonder why they pay the total price when others get away with freebies. This perception can harm digital trust and lead to higher customer churn rates.
Cracking The Code: Why Subscription Abuse Remains An Unresolved Challenge
Companies face an ongoing battle to combat the problem of subscription abuse in digital services. Currently, user management systems for subscription-based services use IP addresses and assume that each IP address represents a unique user-device pairing. While this approach seems logical, it falls short in a few ways.
One significant weakness of IP-based solutions is their vulnerability to VPNs. Bad actors can easily use VPNs to mask their IP addresses and make it look like multiple users are accessing your service from the same virtual IP address. This allows them to share passwords and accounts across different places and hinders your ability to enforce fair usage policies.
Another problem with IP-based solutions is the customer friction they create in legitimate scenarios. When a customer’s IP address changes—perhaps because they are traveling or switching networks—your service might mistakenly flag this as suspicious activity. This flagging can lead to unnecessary account lockouts, forced re-authentication, or other barriers that frustrate legit users. This friction detracts from the user experience and can drive away paying customers who feel inconvenienced by overly rigid security measures.
5 Ways to Prevent Subscription Abuse
1. Using Dynamic Risk Scoring
Sometimes, the indicators of subscription abuse only become evident when observing user activities and transactions in real-time. Dynamic risk scoring leverages risk engines to track data points — user behavior, transaction history, device information, and geographical location—and calculate a risk score for each interaction.
This score evolves as new data becomes available to give you a real-time assessment of a particular user or transaction’s risk. If someone’s risk score reaches a certain threshold, the system can take appropriate action, like blocking the transaction or flagging the account for review (e.g., if free trial abuse is suspected). This approach can, however, generate false positives, leading to unnecessary interruptions for legitimate users and wasted time for fraud teams.
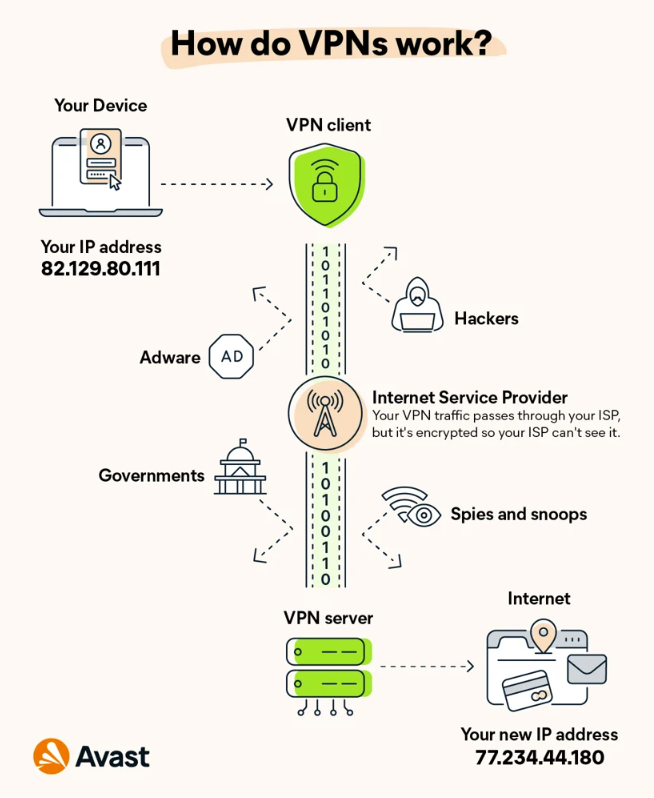
2. Implementing Adaptive Authentication
Adaptive authentication builds upon dynamic risk scoring by dynamically adjusting login and verification measures based on the risk level of each login attempt. It considers the user’s location, device, and behavior. A login attempt from an unusual location might trigger a request for additional verification, while a familiar login scenario would proceed smoothly. Solutions like passwordless authentication can also reduce the likelihood of abuse while tackling the issue of potential friction for legitimate users. However, additional authentication steps can lead to friction in the customer journey.
3. Integrate Fraud and Identity Intelligence Feeds
Look for data streams collected within dedicated identity and threat intelligence feeds that help you identify potential or current threats like compromised IP addresses, devices, credentials, stolen card details, or suspicious transactions. These artifacts can play a role in protecting against various types of subscription abuse.
By integrating these feeds into your security infrastructure, you can proactively block or monitor users associated with known fraudulent activity or require mandatory password resets for accounts at risk of abuse via credential stuffing. However, maintaining and updating these feeds to stay relevant is very time-consuming.
4. Impose Access Limits and Reward Subscription Policy Compliance
Introduce session-based timeouts that call for re-authentication after a certain period of inactivity or use. Consider also imposing limits on the number of times someone can access your service within a specific period to prevent excessive access beyond what even the most hardcore user might do on their own (which might indicate account sharing). Challenges with this approach include the risk of inconveniencing legitimate users who may experience disruptions due to session timeouts or access limits, potentially leading to dissatisfaction.
Conversely, you can find ways to reward users for not abusing your subscription policy, such as premium content or discounts. Rewarding compliance could help reduce instances where people violate subscription policies while under the impression that they’re not causing much harm.
5. Tighten Payment Verification and Free Trial Access
Have robust payment verification processes to combat the prevalent use of stolen card information to access online services. Implement systems like 3D Secure, which requires additional authentication during the payment process. This extra authentication usually calls for a PIN code or approval in a mobile app to verify payments, making it far more challenging for fraudsters to successfully use stolen credit card information to subscribe to your service (even though some clever social engineering techniques may still allow them to bypass that).
Similarly, implement tighter security controls such as requiring a valid payment method to sign up for a trial or limiting free trials to one per name/address. While these systems support a more secure payment and authentication process, they may incur additional costs. Plus, extra steps in the customer journey lead to unnecessary friction and customer dissatisfaction.
How Memcyco Combats Subscription Abuse
Memcyco’s AI-powered digital impersonation solution reduces subscription abuse risk for your business in several ways. Our unique device fingerprinting and user-device mapping capabilities accurately identify fraudulent activities, providing deep insights into attackers while maintaining user privacy.
These technologies can identify several users operating on the same device, typically the setup for promotion and trial abuse. They can also spot a single user operating from multiple devices, which is used for account sharing. By alerting you of these fraudulent activities in real-time, Memcyco can help you mitigate these types of subscription abuse and avoid significant revenue losses, compliance issues, and growing client mistrust.
Memcyco’s protection against payment fraud, in the context of subscription abuse as well as in other contexts, is based on our unique set of nano-defenders, code snippets that act like our eyes and ears in regards to impersonating sites.