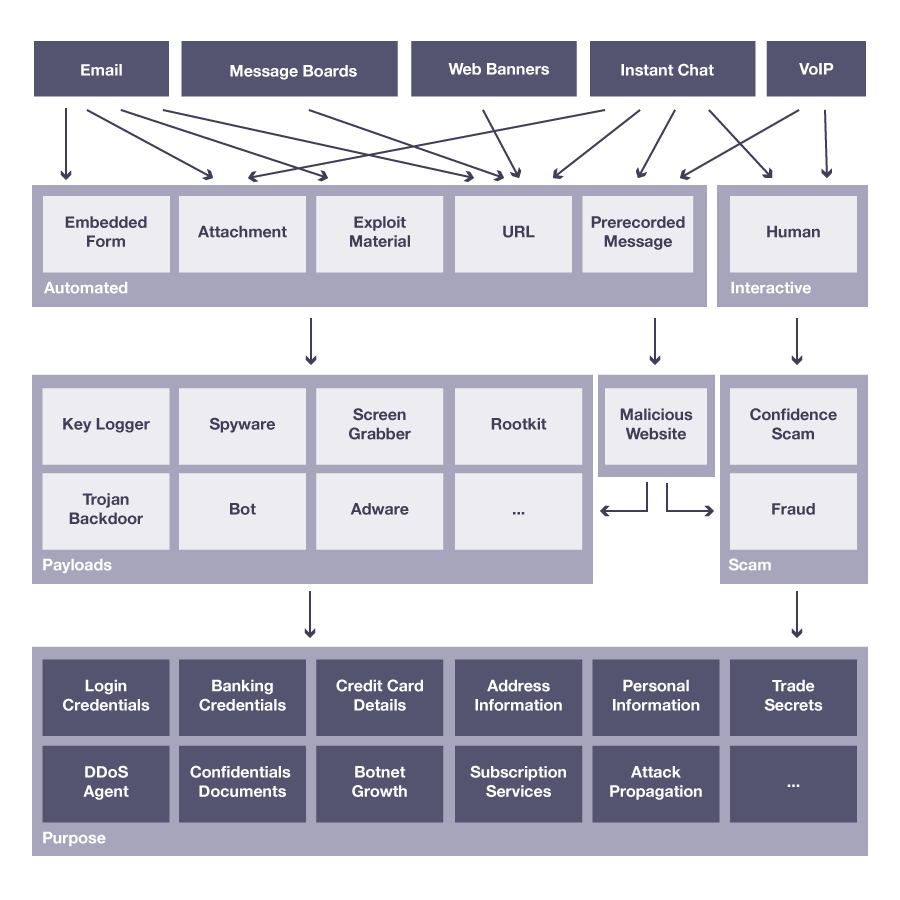
Trust is one of the most basic building blocks of business. It is also the one most frequently abused by cybercriminals. In the digital realm, the exploitation of the digital trust between providers, clients, and business partners is at the heart of most social engineering schemes designed to defraud the users of digital services.
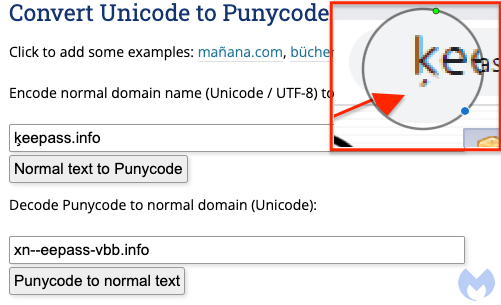
In early October 2023, security researchers discovered that threat actors were impersonating popular free software brands and employing search engine ads to trick users into browsing a fake website to download malware. In the case of KeePass, a popular open-source password manager, the malefactors cloned the original website and published it (with some alterations) on a spoofed domain. Another recent case uncovered cybercriminals spoofing the websites of at least thirteen national postal services.
A new spoofed website is created every eleven seconds. Considering that the time to take down a spoofed domain averages twenty-one days, it’s clear this problem isn’t going away anytime soon. To understand what exactly is happening, it’s essential to get under the hood and dissect the process of web spoofing attacks from an attacker’s perspective. But first, let’s clarify why website spoofing is a major threat to digital trust.
Why website spoofing?
When discussing online fraud, most people think of phishing attacks delivered via email or text messages. Many technologies can stop at least some types of phishing messages and malicious attachments. Businesses and service providers employ email scanners, and most mobile service providers also offer some SMS filtering.
Unfortunately, malefactors are familiar with these defenses. They are turning to alternative channels to spread links to malicious websites to bypass them. Among these are paid search ads, social media platforms, messaging apps (like Signal and Telegram), and even QR codes placed in public spaces.
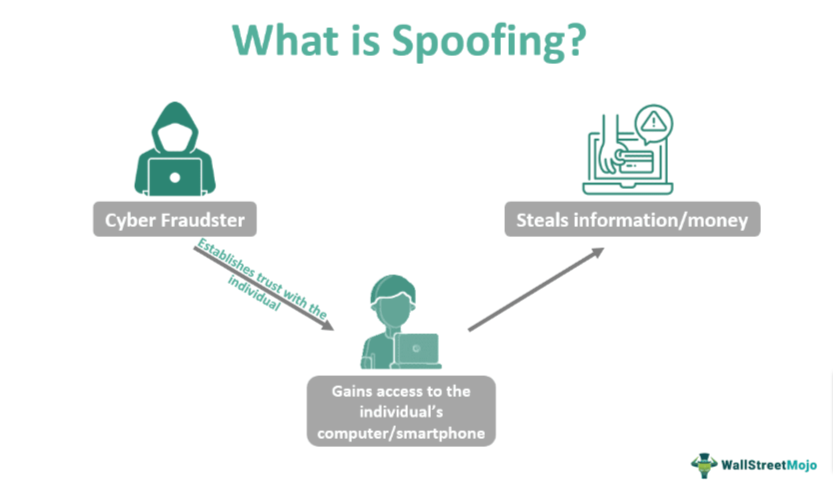
In most cases, malefactors aim to get users to click through to a spoofed website the criminals own and control. Once there, unaware users can be misled into downloading malware or handing over sensitive access credentials or payment information.
This fake website, cloned from one that the users know and use, will attempt to exploit their trust in the familiar website branding and interface to defraud them. That spoofed website is the point of impact and the place where the exploitation of digital trust turns into costly online fraud.
The Anatomy of a Website Spoofing Attack
Creating and publishing a spoofed website requires no special skills or lengthy training. Basic familiarity with website frameworks and architectures, as well as access to Google and a good technical sense, are all one needs to spoof most legitimate websites successfully.
The process consists of a few steps and can differ according to the attack’s scope and the criminal’s proficiency and experience. Here’s how it works:
Research and Intelligence
First, attackers choose their target. It may be a digital bank, a postal service, or even a government agency.
The choice of website to spoof depends on several factors:
- Goal of the Attack – Are they looking to disseminate malware or collect sensitive information for sale on the dark web?
- Ability to Reach Potential Victims – Do they have a list of valid email addresses or mobile numbers you can target with the link to your spoofed website? Or perhaps they’ll need a valid search engine advertising account to trick people into downloading malware.
- Attack ROI – Are the cost of hosting, various phishing tools, and the risk worth the predicted gains?
For seasoned cybercriminals, this step may also entail accessing the Dark Web or specialized Telegram and Signal groups to purchase datasets and tools to automate, conceal, and scale the spoofing fraud scheme.
Domain Spoofing
Web spoofing and domain spoofing are two terms that are frequently used interchangeably. However, domain spoofing is limited to creating a URL that can be mistaken for the genuine domain name of a brand. It does not address the content of the page displayed.
The techniques fraudsters usually employ include:
- Homograph Replacement – One or more letters in a genuine domain name are replaced with letters from different languages and Unicode characters that appear identical to their ASCII counterparts. One such example is the brand impersonation attack on KeePass.
- Subdomain Spoofing – With access to a compromised server or even a random domain name, malefactors can create long subdomains that spoof genuine URLs. For example, www.paypalcomsecurelogin[.]xyz[.]com is a close approximation of a legitimate-looking URL that can go unnoticed, especially on a small mobile screen.
- Typosquatting – A less popular technique for spoofing domains is registering a typo version of the genuine domain name. For example, paypak[.]com or amazom[.]com are likely typos to enter when using a keyboard on a PC. Since most significant brands are aware of typosquatting attacks, they usually purchase these domain names in advance. In addition, most browsers today include built-in protection against typosquatting.
- URL Masking – Especially common with SMS and social media-based scams, URL masking entails using URL shortening to conceal the actual address of the spoofed website. Since legitimate brands often employ URL shortening in their text messages and social media posts, it makes it easier for malefactors to create addresses like lnk[.]to/paytaxesatdiscount or bit[.]ly/freecouponsoctober2023.
Website Cloning
Cloning most websites is surprisingly easy with just a browser. If Chrome doesn’t get the job done, there are specialized tools for downloading websites like HTTrack Website Copier or SiteSucker. Once the website is downloaded, malefactors reverse engineer it to send data to their servers instead of those of the original website.
Usually, the genuine website servers will not log any suspicious activity when the website files download. To ensure they’re not detected, fraudsters often employ a VPN service with rotating IPs, delay page requests, and employ specialized tools to cover your tracks.
Alternatively, criminals might purchase a phishing toolkit with templates for many popular websites and save themselves some of the technical work. Yes, it’s all that easy—and very frightening.
Publishing the Spoofed Website
Malefactors will set up multiple sites to host spoofed pages to launch an effective phishing attack. They also automate user redirection as victims of the attack (including the brand targeted) will begin to take steps to have the spoofed domains taken down, and pages removed from hosting servers.
Depending on the scope of the attack, cybercriminals can leverage compromised hosts, stolen cloud platform credentials (that can be acquired on the Dark Web), and free hosting services like Google Sites that include the bonus of a valid SSL certificate.
Safeguarding Digital Trust at the Point of Impact
Website spoofing attacks are at the heart of malware payload delivery and credential theft. They cause massive financial harm to businesses and customers, and the reputational damage results in lower customer engagement and digital trust. Considering just how easy it is to spoof websites, businesses must take a proactive approach to prevent and mitigate the risks.
Takedown services, domain registration scanners, and threat intelligence solutions can be part of the protective envelope businesses extend to their clients, but more is needed. Organizations today need complete visibility into potential attempts to spoof their website, and sophisticated tools to spoof-proof their digital assets and safeguard the digital trust of their clients.
For brands looking to proactively tackle website spoofing risks, Memcyco offers an end-to-end solution that ensures immediate attack detection, in-depth forensics, and innovative mitigation measures. With additional guardrails built into its agentless system, Memcyco enables quick identification of spoofed sites and attack victims, regardless of the attack technique used.
To stop the exploitation of digital trust, it’s time to stop cybercriminals spoofing websites at the point of impact—and Memcyco does that better than anyone.