2022 surveys suggest that organizations have accelerated digital transformation by 59% compared to pre-COVID-19. This rush to go digital doesn’t go unnoticed by cybercrime gangs. Whether you’re a social media platform like Reddit, a state hospital, a media company like Vice, a password security service like LastPass, or a telco like T-Mobile, data breaches are costing businesses millions of dollars in recovery, fines and remediation costs. But another consequence of data breaches rarely discussed is: their impact on customer trust in digital services.
You don’t need to fall victim to hackers to develop a healthy fear of executing online transactions; Cybersecurity headlines are often enough to make users doubt the reliability and trustworthiness of digital services. To safeguard your organization’s reputation, stay ahead of crime, and comply with regulations, you can employ attack surface management (ASM) in your cybersecurity strategy. This blog shares what you need to know to get started.
What is attack surface management?
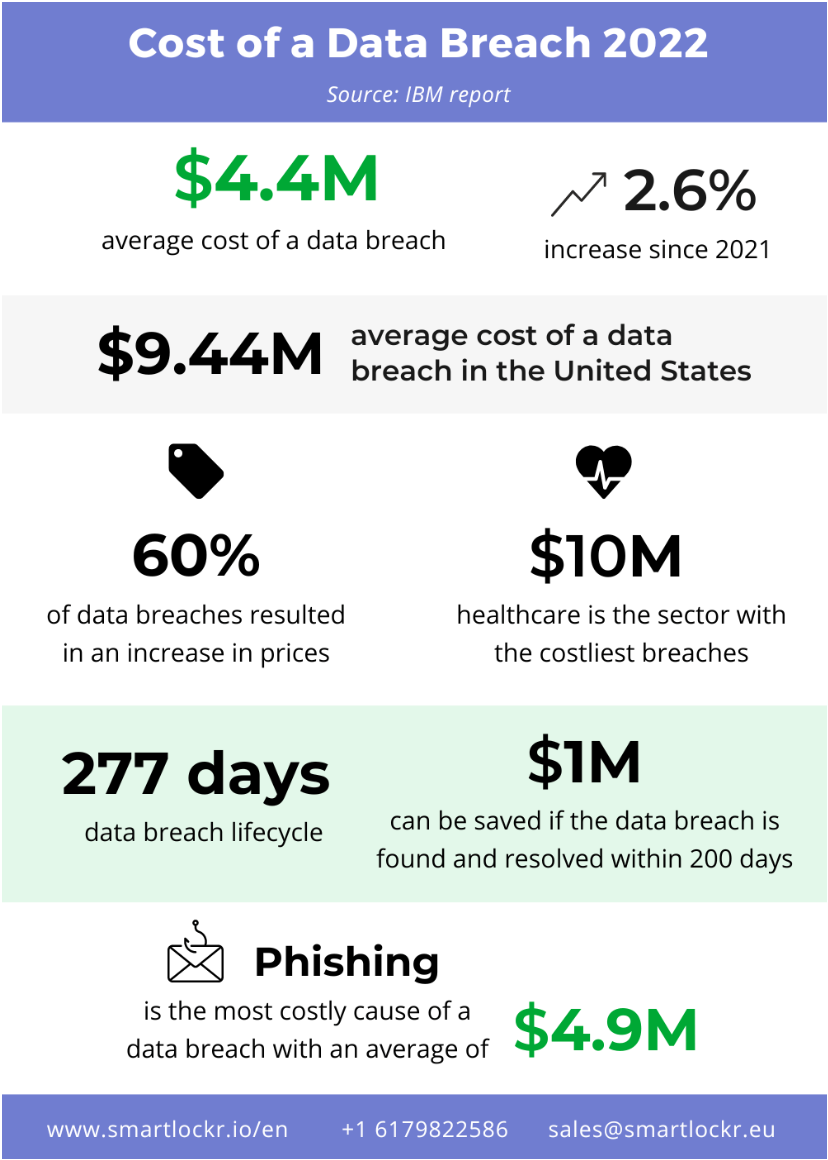
Attack Surface Management (ASM) is the continuous process of identifying, assessing, and mitigating potential attack vectors of a system, network, or application. The goal is to minimize the number of possible entry points for attackers to gain access to an organization’s digital assets by finding and “plugging” those holes.
Unlike other cybersecurity disciplines (like vulnerability management), ASM is conducted from an attacker’s perspective rather than the defender’s. It is a proactive approach to identifying potential targets and evaluating risks based on the opportunities they present to malefactors.
Holistic ASM entails mapping out the entire system (including infrastructure, applications, devices, and users) to identify security gaps and evaluate their potential risks before taking action to prevent them from becoming threats.
What are attack surface management tools, and why you need them in 2023
The attack surface of organizations today is vast, complex, and rapidly evolving. It encompasses everything from web applications to cloud infrastructure, mobile devices, and end users. The right set of ASM tools and resources can help CISOs understand the attack surface and continuously identify risks for timely resolution.
Employing a proactive defense against cybercrime has a positive, albeit incalculable, impact on overall digital risk reduction. By managing and reducing the attack surface, businesses can minimize the risk of breaches and their costs regarding remediation, reputation damage, and lost business.
Last but not least is the issue of regulatory compliance. Complying with laws and regulations demands a toolset that provides a comprehensive view of the attack surface. This is necessary to prove that you’re taking all possible actions to minimize the risk of a data breach. ASM tools can help you achieve just that.
What to look for in an ASM solution
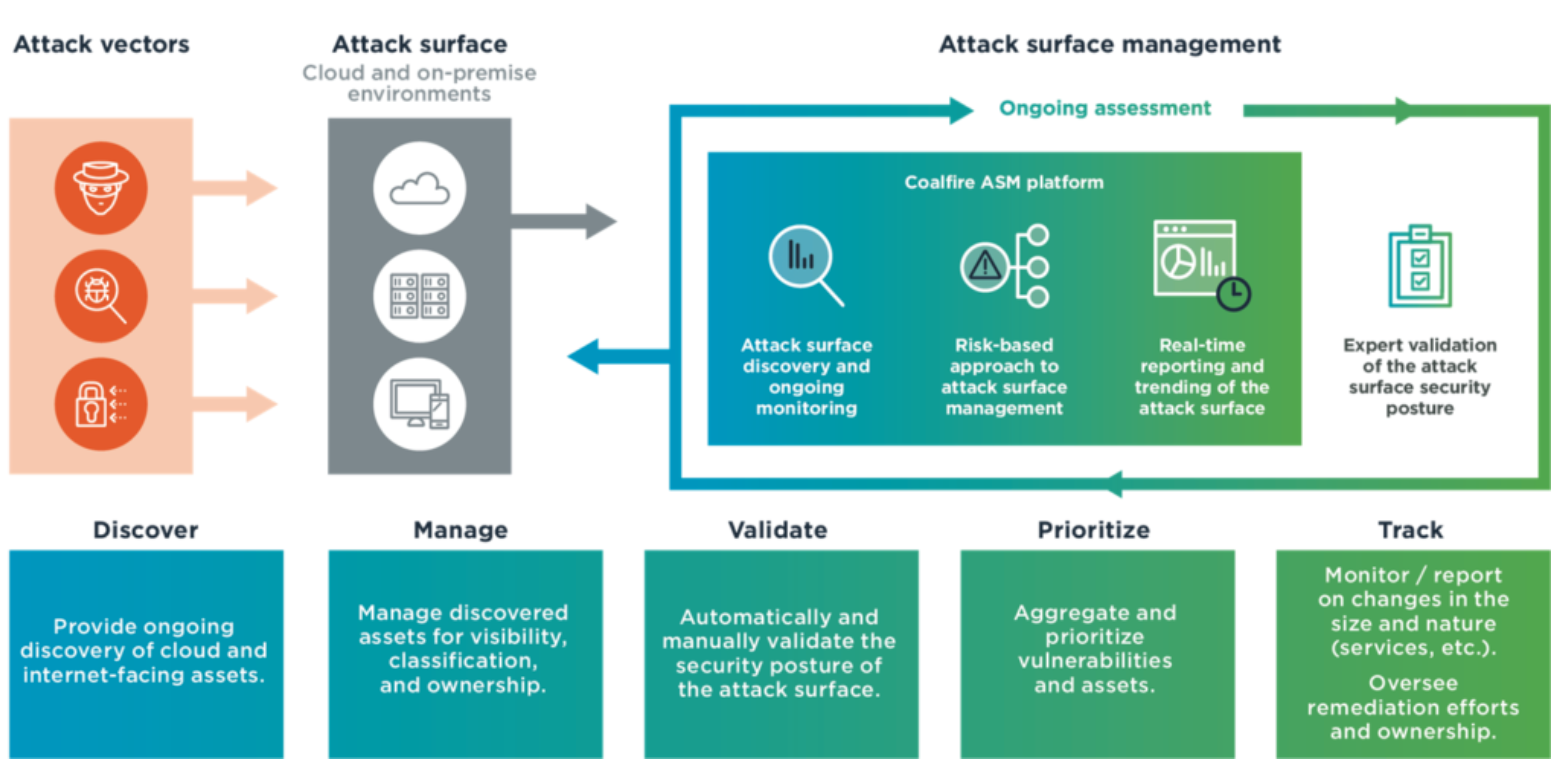
Attack surface management is a practice rather than a single product. Regardless of what cybersecurity vendors may want you to believe, there’s no such thing as an all-in-one ASM tool for all businesses. Instead, surface attack management entails employing solutions and tools to discover and resolve potential weaknesses across all your systems and processes.
Consider your organization’s specific needs and risk profile when evaluating ASM solutions. Remember that rather than layering solutions over obvious vulnerabilities, you should aim to gain visibility over your entire security perimeter to outsmart and deter malefactors.
Though there is no one-size-fits-all solution, there are features that you should consider:
Asset Discovery & Inventory Management
The more digital assets your organization owns, the bigger your attack surface. The first step to protecting these assets is understanding and mapping them out, from codebases and infrastructure to endpoint devices and users.
Vulnerability Assessment & Threat Intelligence
Knowing what to protect is step one. The next step is understanding what you need to protect from. Your ASM solution should be able to identify potential attack vectors in your systems, prioritize them based on severity and risk, and integrate with existing resources for real-time information about new and evolving threats.
Continuous Security Monitoring
When should you be managing your attack surface? The answer is all the time. Manual scans do little to protect your assets from 0-day exploits, but a good ASM tool provides passive and active continuous monitoring of your assets to detect potential threats.
Reporting, Analytics & Ease of Use
Your infosec teams are busy, and the last thing you want to do is give them yet another complex tool. Seek out ASM tools that provide clear, actionable reports and solutions that enable easy integration and automation of tasks.
Scalability
As your business evolves, so do the cyber threats it faces. A scalable ASM solution will grow with your business without introducing unnecessary features, management overhead, or costs.
Top 8 attack surface management solutions for 2023
Because no single tool can provide a complete ASM solution, you’re likely to benefit from multiple categories of ASM tools. Some may not brand themselves as ASM tools but offer access to attack surface monitoring and proactive threat assessment features.
Web-based attack surface management solutions
1. Detectify
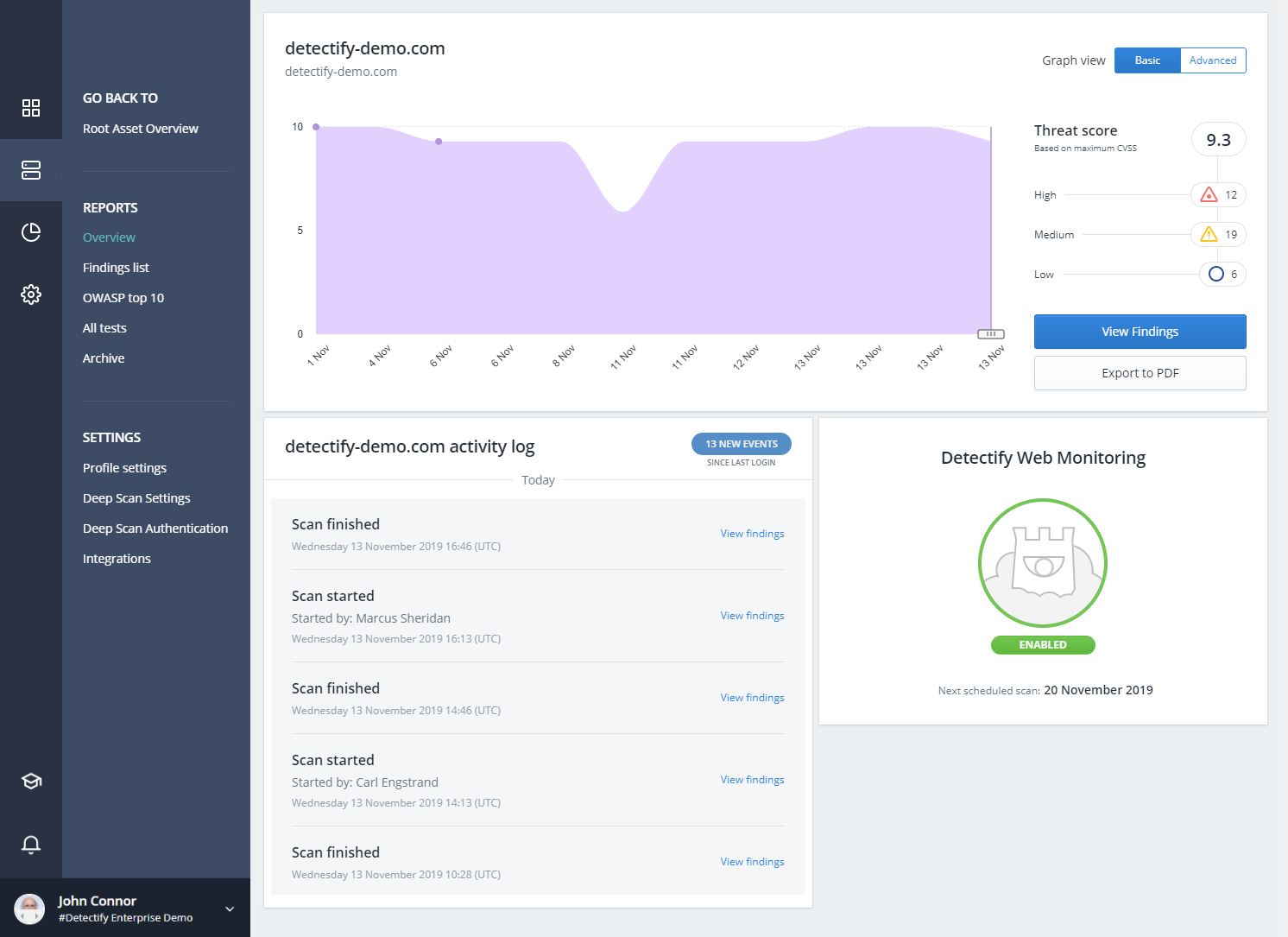
positions itself as an EASM (external attack surface management) solution, focusing on attack surface monitoring, application scanning, and subdomain takeover prevention. Aimed at growing businesses and brands, Detectify boasts scalability options and an ethical hacking initiative, Detectify Crowdsource.
You can test the system for two weeks without entering a credit card number, which helps test multiple ASM solutions before purchasing and integrating them. Detectify is best for application and product security teams at technology companies and consumer packaged goods (CPG) brands.
2. Memcyco
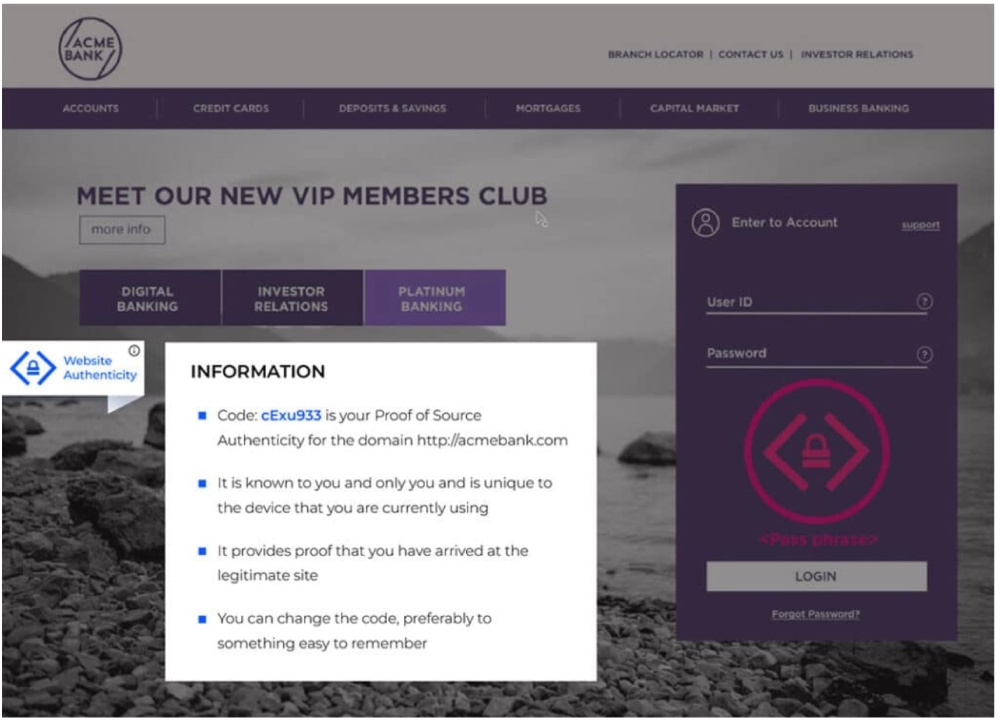
As noted earlier, CISOs often think of cybersecurity in terms of protecting an organization’s digital assets within clear boundaries. These boundaries rarely include customers–perhaps the most valuable of business assets. Memcyco takes a different approach by prioritizing the digital trust of clients and the convenience of Infosec pros.
A turnkey solution for brand security, Memcyco enables unprecedented visibility into a previously obscure area of your attack surface: fraud attacks on your clients through brand abuse and fraud. In addition to zero-day monitoring and detailed real time impact reports on actual impersonation attacks, Memcyco’s unique authenticity watermark protects end users from fraud at the point of impact. The solution best suits medium to large enterprises with a transactional digital presence (e.g. finance, e-commerce, shipping, government and education).
Cloud infrastructure attack surface management solutions
3. Skyhawk Security
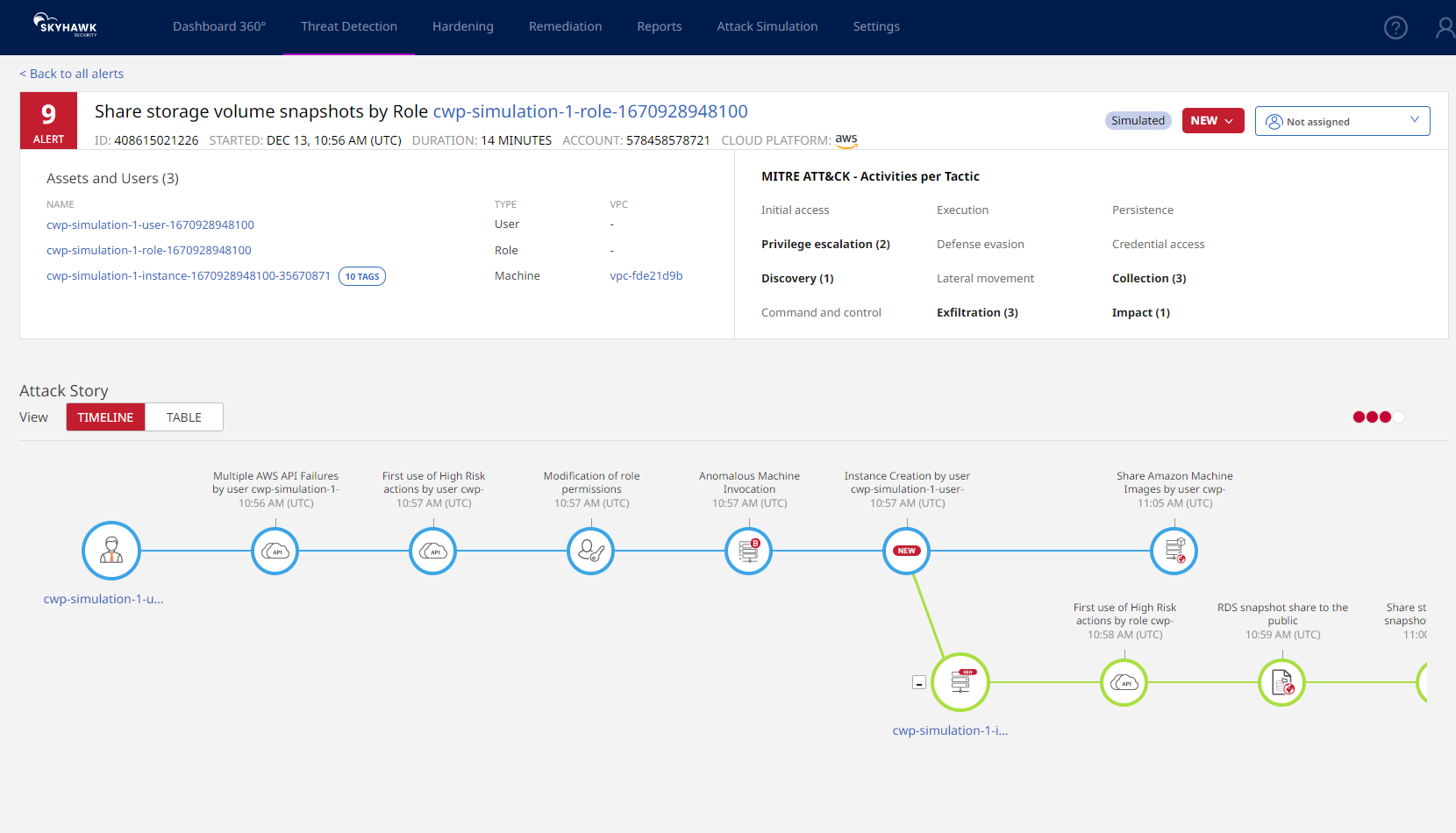
Alert fatigue troubles security teams frequently exposed to an overwhelming number of notifications. Skyhawk security aims to remedy this with what it calls “REALerts”: actionable notifications only when there is an actual threat to remediate.
Skyhawk’s platform correlates logs and activities across your cloud assets for a complete view of the runtime. By employing AI/ML, the solution can learn relevant behavior in ‘peacetime’ and show a full attack-kill chain in ‘wartime.’ Skyhawk is best for security teams managing the attack surface of complex cloud environments.
4. Wiz
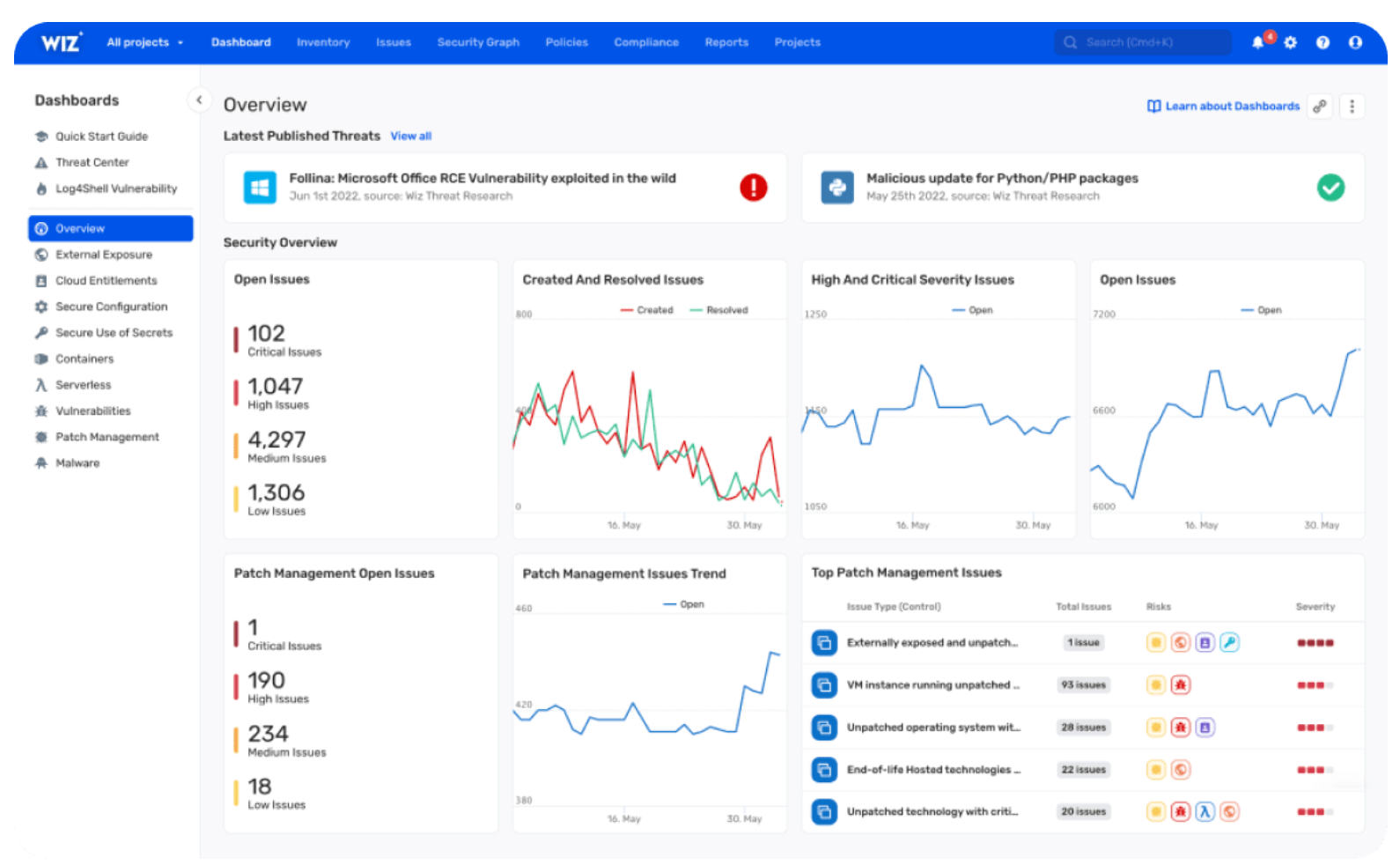
According to Wiz, context is king–which makes sense considering the alert fatigue problem discussed above. Wiz aims to offer comprehensive visibility and context into your cloud attack surface so you can proactively identify, prioritize, remediate, and prevent risks to your business.
Wiz’s modular and scalable approach to ASM serves organizations at any stage of their cloud journeys.
Application code attack surface management solutions
5. SpectralOps

If your organization develops internal or customer-facing applications, you must employ code security and DevSecOps practices. SpectralOps, recently purchased by Check Point, is a lightweight developer-first solution that monitors your application code for exposed secrets and misconfigurations.
Aimed at DevOps and DevSecOps teams at technology companies, SpectralOps scans for code-based vulnerabilities so developers can continue to work at speed without the risk of making costly mistakes.
6. Jit
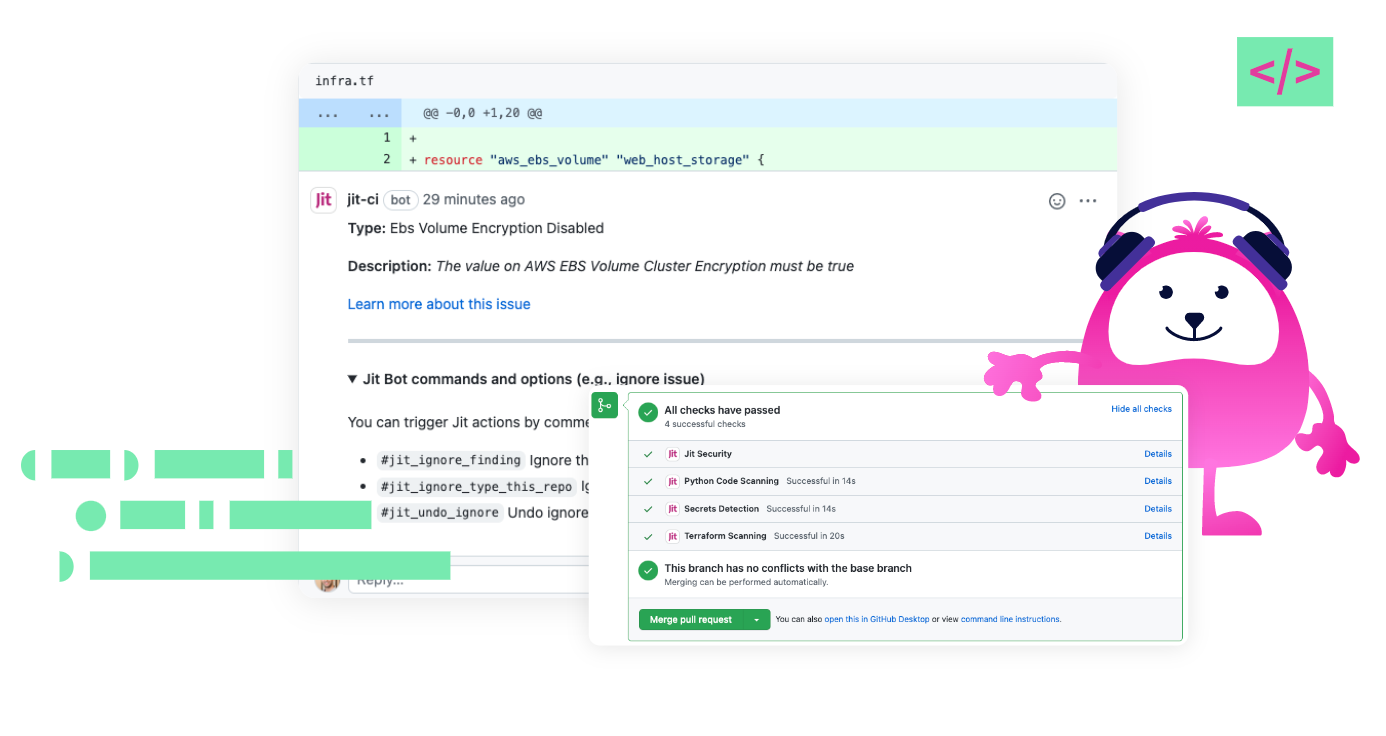
Although Jit is not your typical ASM solution, it provides cybersecurity teams the ability to orchestrate security solutions and attain a holistic overview of the attack surface under one roof.
Jit is recommended for rapidly-growing software development companies looking for a modular, lightweight, scalable code ASM solution that helps to maintain development velocity.
Enterprise network attack surface management solutions
7. Check Point
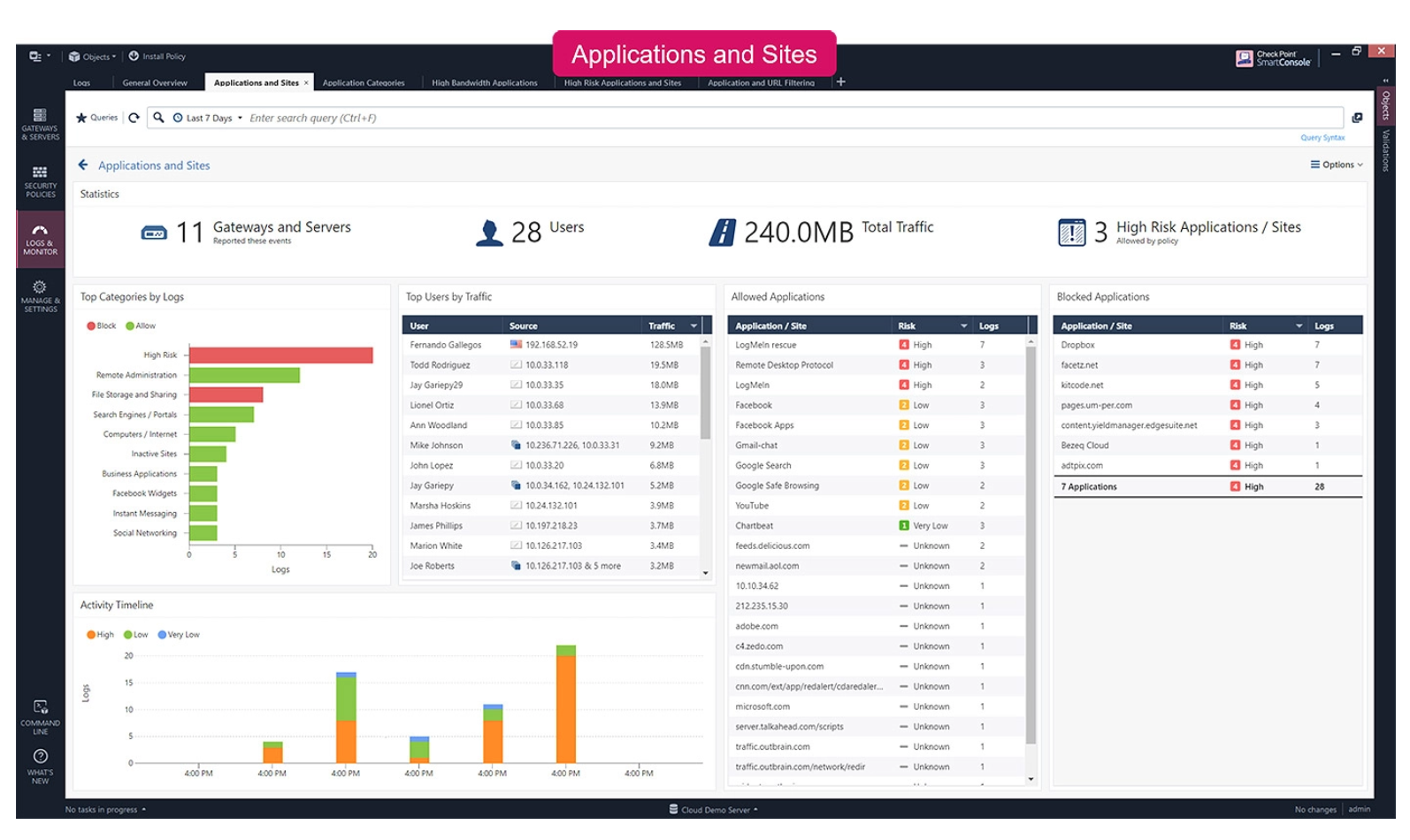 Check Point is known for excellent network security and attack surface management. With a broad selection of products for network security, cloud security, endpoint protection (including IoT devices), and corporate user security, Check Point aims to provide a comprehensive ASM toolset for IT and InfoSec teams at large enterprises and corporations.
Check Point is known for excellent network security and attack surface management. With a broad selection of products for network security, cloud security, endpoint protection (including IoT devices), and corporate user security, Check Point aims to provide a comprehensive ASM toolset for IT and InfoSec teams at large enterprises and corporations.
8. IBM Security Randori Recon
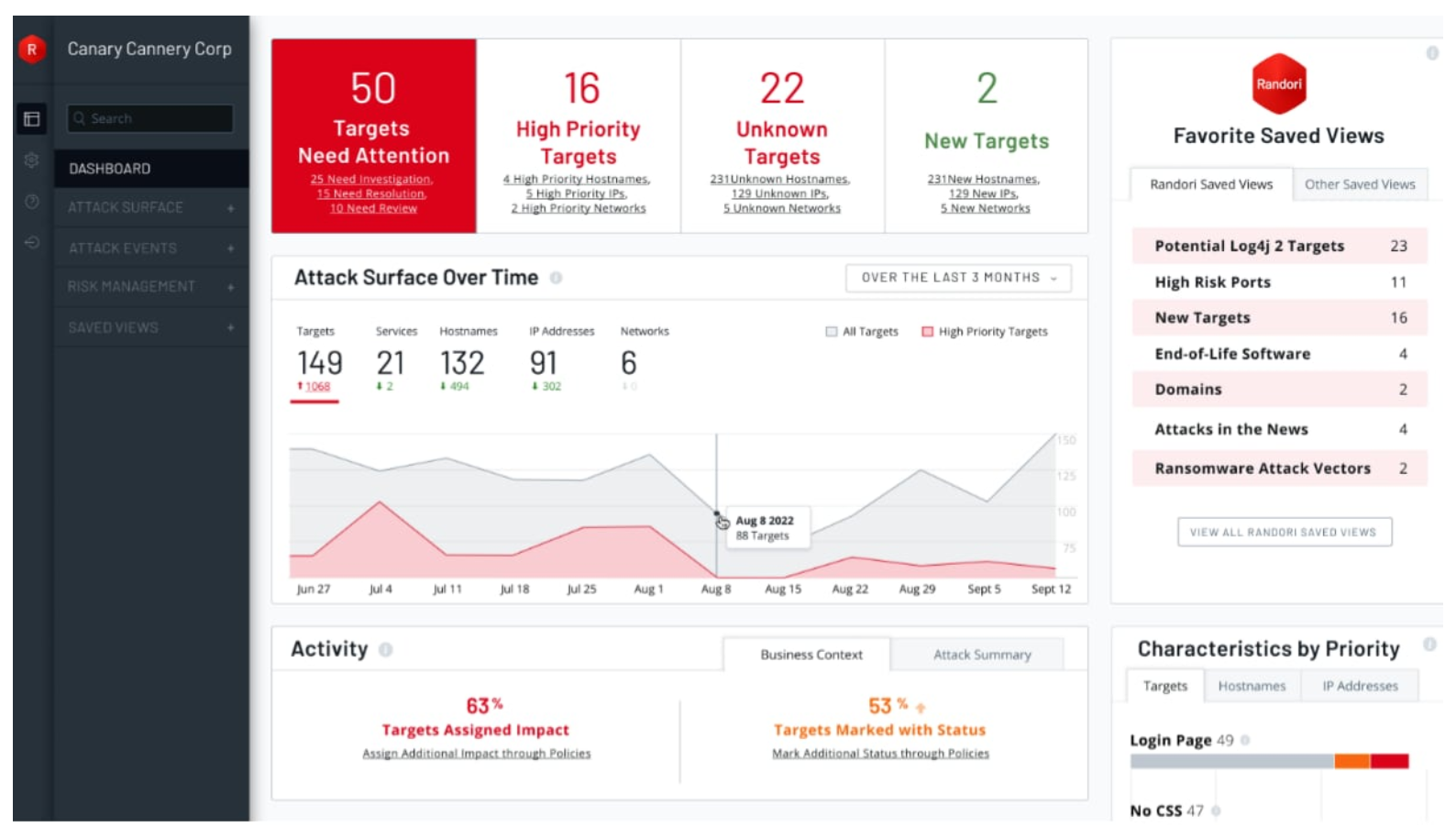
Another old kid on the block is IBM, with an ASM solution named Randori Recon. Aimed at enterprises engaged in cloud migration and digital transformation, Randori Recon employs a continuous discovery process to uncover shadow IT assets and arm you with correlated findings based on adversarial temptation.
In addition to shadow IT discovery (integral to asset mapping), Randori Recon helps enterprise infosec teams detect attack patterns and techniques most likely to be exploited by malefactors.
Your growing attack surface and you in 2023
The cybersecurity perimeter of your organization is different from what it was a year ago–or even yesterday! You needn’t introduce new cloud services or employ clumsy junior developers (who leave credentials in code) to watch your attack surface spread beyond the boundaries of your organization.
As commerce, banking, communications, and trade go digital, organizations must think beyond the security of assets within their perimeter. As they also become more reliant on online services, customers must trust brands with their data. Living up to that expectation by protecting customers from cybercriminals may set your business apart. Learn more here.


















![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)