Email owners are no strangers to email scams. Unsurprisingly, phishing was the most often reported cyber crime in 2021, jumping by 182% compared to the previous two years. And although some scams are visibly scams, evident in their malintent, attackers are determined to get your private information online by using increasingly elaborate ploys, believably-spoofed websites, brand impersonation, and various other impostor tactics. That’s why these attacks aren’t just fooling your grandparents; even giant corporations with massive cybersecurity budgets have fallen victim. Take Facebook and Google, for example, who combined lost $100 million to a phishing scam in 2019.
Clone phishing is one well-known form of such attacks, infamous for often going undiscovered for a considerable time and taking a long time to resolve. In their 2022 Cost of Data Breach, IBM found that phishing-based data breaches took 213 days to be identified and another 80 days to be contained. To fight them off as attack methods evolve and become more sophisticated, you must be proactive in protecting your organization. But how? We explore the answer in this blog.
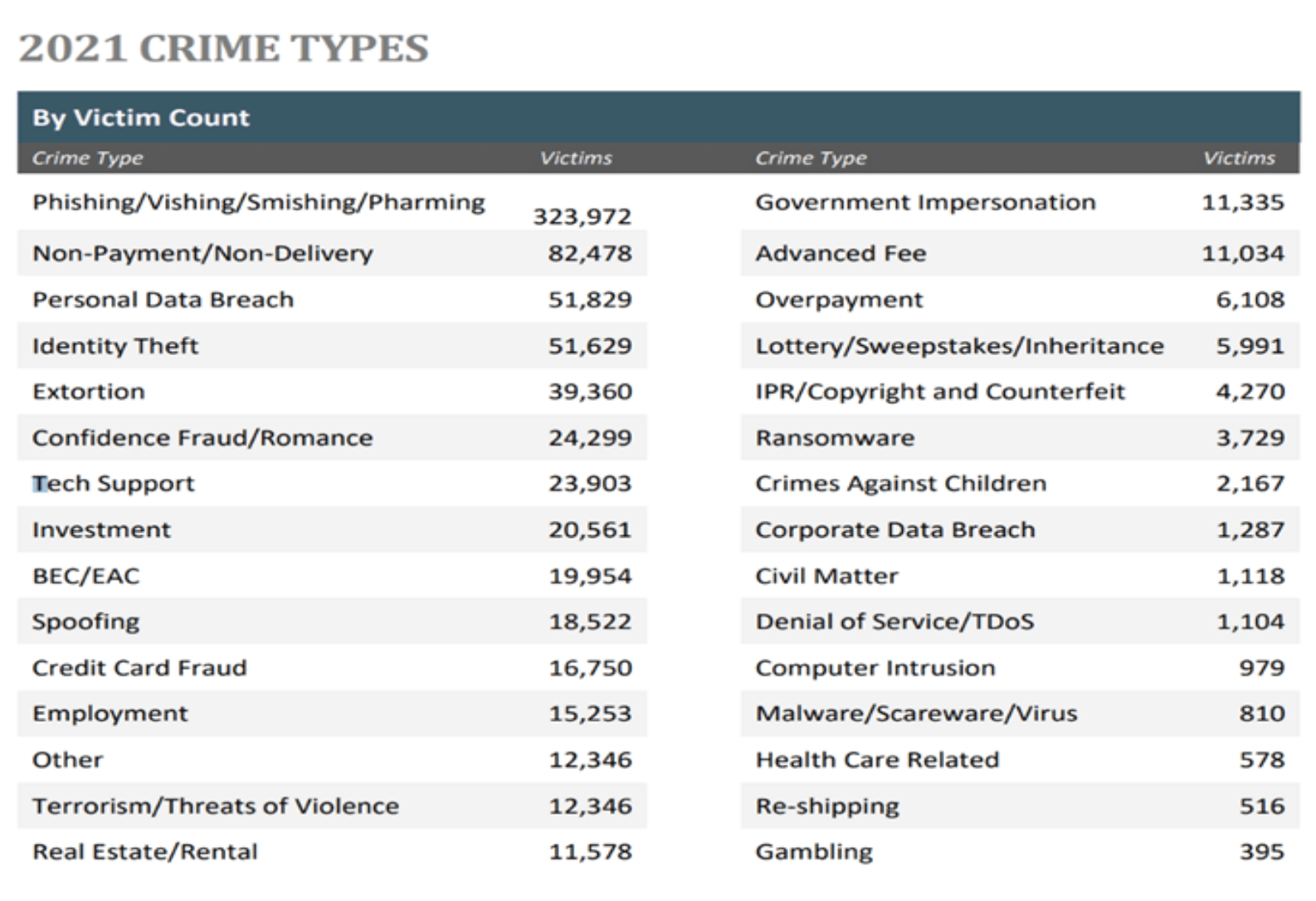
Figure 1. Breakdown of Cybercrimes by type. From “Internet Crime Report 2021,” by Federal Bureau of Investigation 2021 Copyright 2021 by Federal Bureau of Investigation
What Is Clone Phishing?
There is a typical pattern and approach to clone phishing attacks.
- Scammers impersonate a well-known company by using similar web addresses or creating fake websites.
- The scammer then sends a fake email to a long list of potential victims while impersonating that brand. The messages tend to be impersonal in hopes that as many people as possible open the scam links, leading to websites where they are prompted to enter their login credentials.
- The login credentials are copied by the scammer, who can then access the victim’s account on the legitimate website.
Other types of phishing scams you should be on the lookout for include:
Spear Phishing
While clone phishing relies on copying branded messages sent to masses of recipients, spear phishing is when scammers send customized messages targeting a single person or organization. They use familiarities like mentioning your name, referencing a coworker, your company name, or other trust manipulation tactics to convince you to click on malicious links.
Whaling
Whaling targets high-profile employees like CEOs or CFOs. These attacks aim to steal sensitive information from the company or even trick the victim into initiating large wire transfers to the attacker.
Despite the sophistication behind these attacks, there are a few ways to check if a communication is legitimate from the receiving end:
- Check the sender’s address for inconsistencies, such as typos, grammar errors, or a different domain name. Attackers may use email addresses that appear similar to the brand’s but vary in minor ways, or the website they direct you to could be a .net domain when the brand itself has a website ending in .com. Most large organizations have a communications team tasked with checking emails and other communications for errors, so spelling or grammatical errors can be a good tip-off that an email is malicious.
- Check for suspicious links by previewing their URL before opening. If you have already clicked on a suspicious link, you can do two things: check the URL to see if it’s different than the official brand’s domain page, and see if the URL includes HTTPS. Secure URL addresses are typically preceded by HTTPS:// so if that prefix is absent, chances are this is not a secure connection, and your information could be at risk. If you’re still unsure, contact the brand’s official support line and ask to verify the email address. If the email seems legitimate but you don’t want to take the risk, log into your account by entering the brand’s URL yourself in your browser instead of clicking the link.
- Use a password manager. Password managers securely store your login credentials and automatically enter them when you log in to your account. If the site is not authentic, the password manager will not automatically enter your password.
- Be wary of alarmist language. Scammers try to create a sense of urgency to get you to act before you can think, so you’re more likely to expose your personal information to them. If you feel rushed and pressured to respond, it can be challenging to have the clarity of mind to take a step back. But this is when you should avoid clicking on any links.
How to Protect Your Organization from Clone Phishing Attacks
As a brand, you may be wondering what else you can do to protect not just yourself and your employees from falling victim to scammers but also your customers. Clone phishing is notorious for taking advantage of a brand’s reputation to reach its customers, damaging their trust in your legitimate communication efforts. Here are a few actionable suggestions for preventing this:
1. Make it difficult for attackers to reach your users
Memcyco’s Proof of Source Authority (PoSA) works to detect and warn companies of real-time brand identity theft attempts, such as website spoofing, cloning, and account takeovers. By alerting your security team that someone is trying to compromise your brand’s name, even if outside of your security perimeters, you can warn users and report the fakes to stop attackers in their tracks. This PoSA feature also automatically informs end-users of any attempts to impersonate your brand so your customers can stay alert for suspicious activities without compromising their trust in you.
2. Help your customers identify and report suspected phishing emails
As we’ve seen in previous blogs, simply alerting customers that there are fraudsters out there isn’t necessarily helpful. It makes them feel like the onus is on them to prevent attacks, making them hesitant to engage with you online. Memcyco’s solution instead provides an authentication watermark to be featured on a brand’s website, so customers have the means to immediately identify whether the brand they’re engaging with is legitimate.
The watermark is user-specific, so it cannot be forged. It is customizable and adaptable to branding specifications–instead of a big, red warning sign on your page, you can have something functional that also aligns with your identity. Our solution is scalable for any company or marketing operations and can be integrated with websites, email, and text messaging platforms. It can be installed in minutes with a single line of code, and no user registration or installation is needed.
3. Prevent the effects of undetected phishing emails
With so many evolving approaches, protecting your company from the numerous phishing emails that go undetected is vital. Because many phishing emails look and feel legitimate, don’t directly include malicious links or malware attachments, and don’t arrive in high volumes, they are often missed by anti-spam tools. With 45% of employees likely to open suspicious emails that could be trying to install malware into the organization or steal sensitive data, you need a better layer of protection.
You can prevent malware from being installed by properly configuring devices and having endpoint defenses, even if an email was opened. Be sure to only use supported software and devices that are up to date with the latest patches to prevent attackers from knowing your vulnerabilities. You can also prevent malware from being accidentally installed by limiting administrator accounts and ensuring those administrators do not use said accounts to check email or browse the internet.
Strong passwords can also help protect you from malware, but it is imperative to use authentication and authorization effectively to prevent login credentials from being breached. For example, set up multi-factor authentication (MFA) and use password managers or alternative login mechanisms such as biometrics or smartcards. Be thorough in removing or suspending accounts that are no longer in use.
Employee education is also necessary to protect your company–after all, impostor attacks target people, not technology. Employees must be educated and empowered to create a line of defense for your company. Create a culture of awareness and spread information on what phishing attacks can look like, ways to detect suspicious links and emails, what to do if they accidentally open a scam email or link, and what strong password policies entail.
Choosing the Right Network Protection Solution
It can be daunting to keep track of information and the appropriate steps to take when clone phishing is continually evolving. Employee education takes time and money, and even with that training, employees are still prone to opening suspicious emails because, well, humans are only humans. The reality is unfair: It takes a lot of energy to always be on alert for attacks, but it takes only one successful attack to create damage.
We aim to simplify all of this for you while enabling constant vigilance. Our solution protects from attacks on every touchpoint between your brand and its customers, partners, and employees. We alert your team to any impersonation attempts in real time, and help your customers feel confident that you care about their security and that their personal information is safe. To learn more, book a demo here.


















