It’s easy to think that securing the systems and data of an organization is primarily a technological undertaking. The human element of your cybersecurity strategy is usually seen as a weakness—and not without reason.
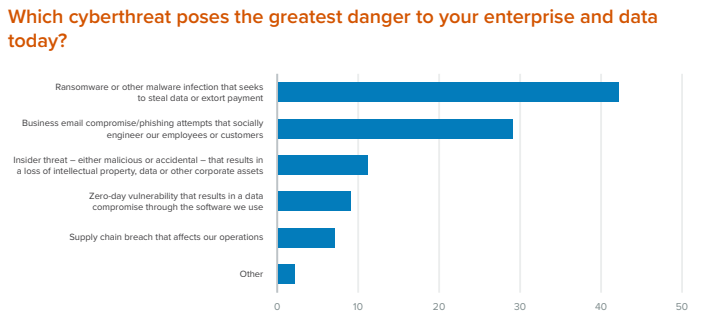
According to estimates, up to 95% of breaches involve a human element. There’s only so much that technology can do to safeguard against human error and neglect of cybersecurity principles.
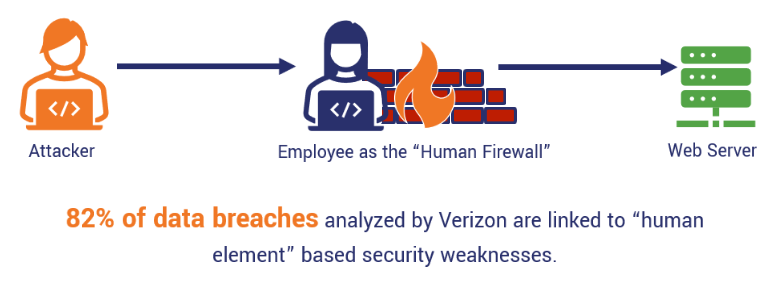
Examining cyber and data security from a human-first perspective reveals an important insight: The individuals who develop and use your corporate applications and services can play a crucial role in enhancing your overall security posture and cyber-defensive capabilities. How? By acting as a Human Firewall.
What is a human firewall?
You’d be forgiven if you thought “The Human Firewall” was the latest Marvel hero coming soon to a theater near you. While the reality is much more mundane, the heroism level might be comparable.
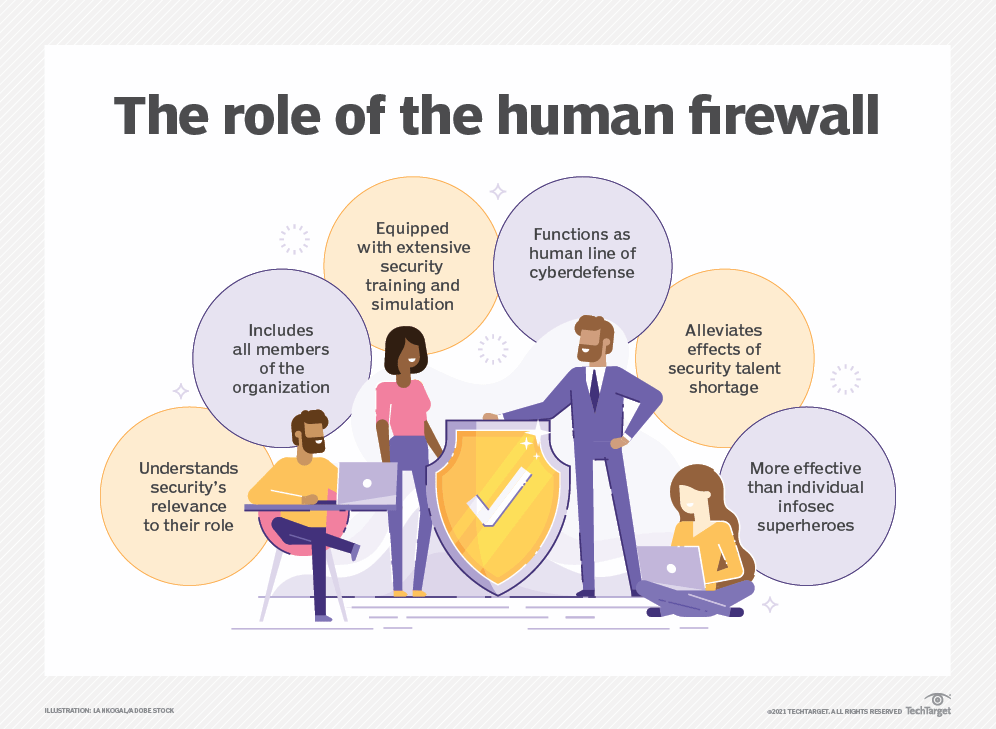
In cybersecurity, many are familiar with the term “firewall”—the software that protects networks or applications from attempts to breach the organization’s virtual perimeter. A Human Firewall is a term that describes the collective ability of an organization’s employees to prevent cyber attacks, data breaches, and lower the organization’s exposure to cybersecurity risk.
The idea behind the human firewall is to provide the workforce with the mindset, skillset, and toolset to maintain cyber hygiene and detect suspicious activities. Much like a network firewall that monitors the traffic between public and private networks for malicious activity, the human firewall is on the lookout for social engineering scams, suspicious access attempts, or other signs of malicious activity in the organizational digital environment.
What are the benefits of a human firewall?
Transforming your workforce into an additional, non-technological cybersecurity layer has numerous advantages, including:
Keeping Up with Developing Threats
Malefactors aren’t scared of employing new technologies and tools to breach corporate cyber defenses. AI, malicious QR codes, innocent-looking USB drives, and cleverly spoofed websites or emails can slip by application firewalls, email filters, and malware detectors. However, it’s much harder for them to pass by the watchful eye of a security-minded employee.
Protecting Data (and the Bottom Line)
A robust human firewall lowers your organization’s overall cyber risk and contributes to your efforts to protect the business from costly data breaches. Moreover, your human firewall can protect intellectual property and proprietary information from leaving your organization’s security perimeter through non-digital means (like printed information). An effective human firewall also boosts organizational regulatory compliance, especially for data protection standards.
Promotes Trust through Good Stewardship of Sensitive Data
Data breaches are costly, and not only because of regulatory fines or downtime. The untold cost of data breaches is in the damage delivered to digital trust in your organization and brand. A human firewall ensures your employees, partners, and customers can trust your organization to safeguard the sensitive information they entrust you with.
Three Steps to Building a Robust Human Firewall
Building a human firewall entails transforming every employee into a watchful guardian of your organization’s digital assets. To develop a resilient and sustainable cybersecurity strategy, you should train your employees to be aware, mindful, and capable of telling apart potential threats from genuine and safe actions and content.
One of the best approaches to implementing a human firewall throughout the organization is through the “Mindset – Skillset – Toolset” triad. Let’s take a closer look at what each involves.
1. Mindset – How to Cultivate a Security Culture
People often assume that IT policies and software security tools are enough to protect them from making errors or falling for scams. Although tools can be helpful, they are no replacement for human mindful attention.
Therefore, the first step to cultivating a security culture is getting people to care about data security. You can do this with:
- Leadership Buy-in – Leading by example is essential to engaging employees on any topic. It’s vital that a culture of cybersecurity culture starts at the top, and is communicated transparently.
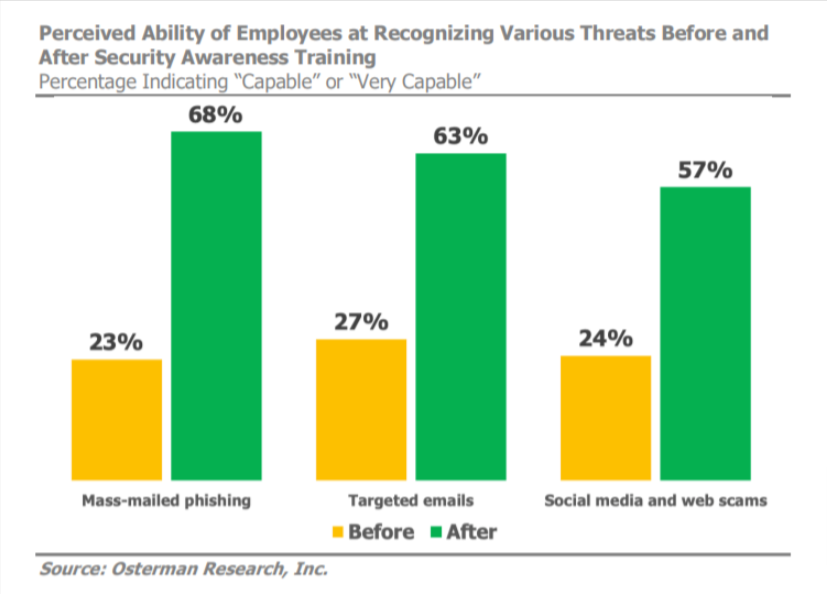
- Relevant Initial Training – Initial information security awareness training should be mandatory, with customized training and content provided to different departments depending on their function and interaction with systems and data. The basic training should include education on handling sensitive data; recognizing phishing attacks, malicious links, and spoofed websites; reporting security issues; password hygiene; and other relevant information.
- Open Communication – Remind employees that data security is everyone’s responsibility. Encourage employees to report potential security policy violations, suspicious emails, and other issues that may impact the cyber-resilience of the business.
- Vigilance Rewards – Identify, praise, and reward employees that report security issues and potential cyber threats to the organization and its systems.
2. Skillset – How to Keep Your Human Firewall Up-to-Date
Relevant initial training and leading by example are just a starting point. To ensure your human firewall is always on and ready to thwart the next attack against your information systems, you can’t just “set it and forget it.”
Here’s how to keep your Human Firewall current:
- Ongoing Training – Since thorough cybersecurity training can be time-consuming and difficult to plan, it is often best to provide regular training in frequent, interactive bits of information to keep up with the latest threats and relevant best practices. It’s essential to consider the roles and responsibilities of each employee. For example, the cybersecurity training necessary for software development teams differs greatly from the best practices for data security of warehouse employees.
- Reminders – Ensure employees are frequently reminded of the importance of data security. Put up posters in work areas, use IT-defined wallpapers on workstations, and find other creative ways to communicate security tips and list relevant risk indicators.
- Attack Simulations – Test the vigilance of your human firewall and the effectiveness of your training by checking their reactions to fake phishing emails, dubious tech support calls, suspicious USB drives, and other scenarios.
- Continuous Assessment and Optimization – The results of attack simulations against your human firewall, audits, and security tool logs can help you assess your human firewall’s resilience. You will also uncover any weaknesses or areas needing improvement. Repeat assessments regularly and adjust as necessary.
3. Toolset – Empowering the Human Firewall with Tech
The core of a security culture is in human behavior and personal attention to potential security threats. However, technology and security tools have a role in empowering your human firewall, encouraging cyber-vigilance, and collaboratively enforcing security policies.
Empower your human firewall with tech by:
- Involving Your Employees – Make sure you understand the needs, preferences, and limitations of your employees and relevant stakeholders when selecting the security and data protection tools and services you will employ. To create and maintain a company-wide human firewall, cybersecurity must become second nature to everyone in the organization without becoming a hurdle or obstacle to productivity.
- Employing Tech for Effective Training – Interactive and gamified experiences are much more engaging and memorable than boring textbooks and lists of guidelines and policies. Experiment and collect feedback from your human firewall and the infosec teams planning the training exercises and cyber attack simulations.
- Make Use of Automation – Make your human firewall’s life easier by automating repetitive tasks and providing always-on monitoring of systems. Also, automate software patches, network scans, and password expiration notifications to fit seamlessly into your human firewall’s day-to-day operations.
Strengthen Your Human Firewall with Memcyco
A Human Firewall is the synergic combination of mindful cyber-vigilance, awareness of relevant threats and risk indicators, and intelligent tech implementation that serves the human element in the cybersecurity equation. Those three pillars – mindset, skillset, and toolset – can make the difference between asset and cybersecurity liability.
One of the most visible and prominent assets a business has is its corporate website. Having it copied and spoofed by malefactors can devastate your business’s reputation, especially if your employees and clients are scammed due to a website spoofing attack.
Today, you can protect your website and brand from spoofing and cloning with a single line of code that enables Memcyco’s agentless end-to-end website spoofing protection. Harness human-first cyber security with intelligent granular incident analysis at the point of impact to deter, detect, and address website spoofing attacks on your brand.
Contact Memcyco for a free demo of the most innovative brandjacking detection and prevention solution to discover how it protects your digital assets.