Phishers are in the business of deception. They trick unsuspecting individuals into compromising sensitive data, potentially bringing an entire organization to its knees.
Awareness training for employees is one of the most important tools a company can use in its anti-phishing strategy. However, it also has its downsides. Some of these flaws can, and should be fixed. Others leave no choice but to complement training with additional anti-phishing tools.
What is Phishing?
Phishing is a cybercrime where attackers impersonate legitimate entities to deceive individuals into divulging sensitive information or taking actions that compromise security. These attacks exploit multiple channels, including email, SMS (smishing), voice calls (vishing), and social media platforms. Attackers often tailor their messages to specific individuals or organizations (spear phishing) or target high-profile executives (whaling).
Typically, phishers employ social engineering techniques to entice victims to click on malicious links, resulting in redirection to fraudulent websites. In many cases, those are fake websites that resemble legitimate ones, aiming to deceive users into entering sensitive information or downloading malware. These websites often exploit users’ trust in established brands, and distinguishing between genuine and malicious sites can be quite difficult. Successful phishing attacks can be devastating, leading to cybercrimes such as account takeover (ATO), ransomware, and PII breaches. These attacks can result in significant financial losses, downtime, regulatory fines, and irreparable damage to an organization’s reputation.
Recent high-profile incidents, such as the $20 million loss suffered by a Hong Kong company due to a phishing scam, highlight the evolving nature of phishing attacks. This, combined with their potential for significant personal and organizational damage, makes phishing a persistent challenge in cybersecurity, and underlines the need for robust security measures.
Why is Phishing Awareness Important?
Individuals are often considered the weakest link in an organization’s cybersecurity defenses, but they can also be a first line of defense against phishing attacks. Well-informed individuals can identify and report suspicious emails, messages, or websites, particularly fraudulent websites designed to steal sensitive information, effectively thwarting phishing attacks before they cause damage.
The threat landscape constantly evolves, with attackers becoming increasingly sophisticated in their methods. Ongoing phishing awareness is therefore crucial. Clearly, businesses and individuals serious about protecting their digital assets must stay updated on the latest phishing techniques.
Phishing attacks take many shapes and forms, with fraudulent websites being a particularly dangerous component of phishing, due to their ability to deceive users into entering sensitive information. Comprehensive phishing awareness training programs must empower individuals to recognize and respond to all kinds of phishing-related threats, emphasizing identifying and avoiding fake websites. However, more than training and education are needed to combat the increasingly sophisticated techniques used in these attacks.
Why Phishing Awareness Training Isn’t Enough
Many organizations remain vulnerable to phishing attacks even with robust phishing awareness training programs. The situation can be even worse if training programs are less robust than we think they are.
Let’s delve into the reasons why your training might fall short. These fall into two categories:
- the inherent limitations of any awareness training program, and
- common shortcomings specific to the training programs themselves.
The Top 5 Unavoidable: Training Can’t Cover Everything
Even the most well-designed and comprehensive training programs will face challenges due to these inherent limitations.
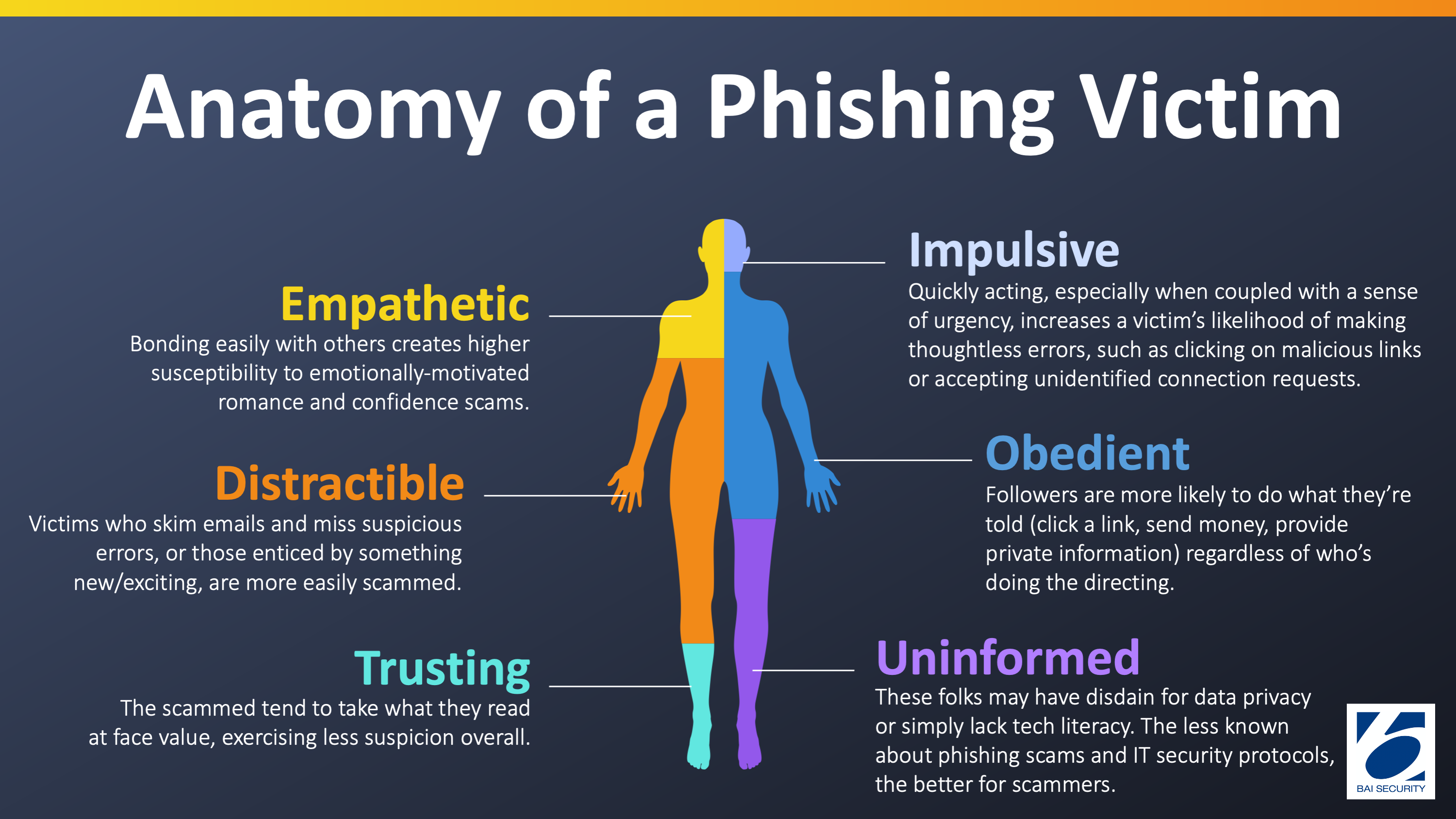
1. The Limits of Human Judgment
Even with the best training, it’s challenging to eliminate human error. People are prone to cognitive biases that attackers exploit, such as:
- Urgency bias: The tendency to act impulsively under pressure, leading to clicking on malicious links without careful consideration.
- Authority bias: The inclination to trust messages from seemingly important figures, even if they contain suspicious requests.
- Confirmation bias: The tendency to favor information that confirms existing beliefs, making individuals more likely to fall for scams that align with their preconceived notions.
- Scarcity bias: The tendency to value things perceived as rare or limited, making individuals more likely to click on urgent or exclusive offers.
These biases, combined with information overload and occasional human error, make relying solely on training to prevent phishing attacks challenging.
2. Evolving Tactics and Technologies
Phishing attacks constantly evolve, with attackers leveraging new technologies and tactics to deceive their targets. Attackers increasingly use artificial intelligence (AI) to generate highly personalized messages tailored to individual recipients, making them more likely to be opened and clicked. The constant evolution of tactics and technologies makes it difficult for training programs to keep pace with the latest threats, as attackers always find new ways to circumvent security measures and exploit human vulnerabilities.
3. The Complexity of Modern Phishing Attacks
Modern phishing attacks have become increasingly sophisticated, often incorporating multiple techniques to bypass traditional security measures and exploit human vulnerabilities. Attackers may combine social engineering tactics with technical exploits, such as zero-day vulnerabilities, to create highly targeted and convincing attacks that are difficult to detect and prevent. For example, an attacker might use a combination of spear phishing (targeted emails with personalized information) and website spoofing (creating fake websites that mimic legitimate ones) to trick a victim into divulging sensitive information. The complexity makes it challenging for training programs to cover all possible scenarios and equip employees with the knowledge and skills to identify and respond to every attack.
4. The Overreliance on Individual Vigilance
Phishing awareness training often places the burden of detection and prevention on individual employees, expecting them to be constantly vigilant and able to identify every potential threat. However, the approach can be unrealistic and unsustainable, as it ignores that humans are fallible and can make mistakes, especially when faced with a barrage of information and distractions. Employees may be tired, stressed, or simply not paying full attention, leading to lapses in judgment that attackers can exploit. Overreliance on individual vigilance can also lead to burnout and complacency, as employees may become desensitized to the constant warnings and reminders about phishing threats.
5. The Lack of a Holistic Security Approach
Phishing awareness training is just one component of a comprehensive anti-phishing strategy. Other security measures should clearly complement it. However, many organizations focus solely on training, neglecting other critical security aspects. The lack of a holistic approach can leave organizations vulnerable to phishing attacks, even if their employees are well-trained. For instance, an organization might invest heavily in phishing awareness training but fail to implement adequate email security measures, leaving a significant vulnerability that attackers can exploit. A holistic security approach recognizes that phishing attacks are a multifaceted problem that requires a multi-layered defense strategy.
The Top 5 Avoidable: Where Most Training Programs Fall Short
In addition to the inherent limitations above, the effectiveness of phishing awareness training can be further hampered by common shortcomings in designing and implementing these programs.
1. Limitations of Simulated Phishing Attacks
While simulated phishing attacks can be a helpful training tool, they often need more realism and sophistication than real-world attacks. Basic simulations may not adequately prepare individuals for diverse phishing techniques, such as impersonating trusted figures or using emotional manipulation. The lack of realism can lead to a false sense of security among employees, who may believe they are better prepared than they are. To be effective, simulated phishing attacks should be tailored to the organization’s specific threats and regularly updated to reflect the latest phishing trends.
2. Lack of Personalized and Adaptive Training
Many phishing awareness training programs take a one-size-fits-all approach, failing to consider an organization’s diverse roles and responsibilities. Employees in different departments may face varying levels of phishing risk and require tailored training content. For instance, employees in finance or accounting may be more susceptible to attacks targeting financial information, while those in HR may be targeted with scams related to payroll or benefits. A more personalized approach can help employees better understand the specific risks they face and how to mitigate them. It can be achieved through targeted training modules, role-specific simulations, and personalized feedback.
3. Failure to Implement Proactive, Real-Time Solutions
The constantly evolving tactics of attackers highlight the need for continuous improvement in phishing awareness training and the adoption of advanced security technologies to stay ahead of the evolving threat landscape. It includes investing in advanced security solutions that can detect and mitigate phishing threats in real time, such as those that employ artificial intelligence and machine learning algorithms to identify and block suspicious activity. Real-time detection and response are crucial for minimizing the damage caused by phishing attacks, as they can prevent attackers from accessing sensitive information or causing further harm.
4. Neglecting the Importance of Continuous Reinforcement
Infrequent or one-time training sessions are not enough to maintain phishing awareness. Employees need continuous reinforcement of key concepts and reminders of the latest threats to stay vigilant. It can be achieved through regular refresher training, ongoing communication campaigns, and gamification techniques to make learning more engaging and interactive. By making phishing awareness an ongoing priority, organizations can create a culture of security that empowers employees to identify and report potential threats.
5. Underestimating the Power of Social Engineering
Training programs often focus on the technical aspects of phishing, such as identifying suspicious links or attachments. However, they often neglect the psychological manipulation techniques used in social engineering attacks. Attackers prey on human emotions like fear, greed, and curiosity to trick victims into clicking on malicious links or divulging sensitive information. Training programs should address these social engineering tactics and teach employees to recognize and resist them. This can involve role-playing exercises, case studies, and discussions about the psychology of persuasion.
The Need for a Multi-Layered Defense Strategy
While phishing awareness training remains a crucial element in the fight against cybercrime, it’s clear that it’s not enough on its own. Attackers’ evolving tactics and the inherent limitations of human judgment necessitate a more comprehensive approach to security.
Organizations and individuals must adopt proactive, real-time solutions to detect and mitigate phishing threats, particularly those involving fraudulent websites and social engineering tactics. Combining robust training with cutting-edge security technologies can create a more secure digital landscape for everyone.



















