Some cybersecurity commentators say that network perimeters no longer exist, but this is not true. What is true is that perimeters are more fluid and dynamic than ever in light of cloud adoption, digital transformation, and hybrid workforces.
Securing your network perimeter means building barriers and fortifications that keep intruders out. To achieve this level of security in modernized, virtualized, and complex network architectures, you need to know exactly what’s happening as it happens inside and outside of the perimeter – wherever attacks can originate. In other words, you need comprehensive real-time security monitoring.
With 84% of tested companies having high-risk vulnerabilities on their perimeters, current approaches are clearly not sufficient. This article highlights the importance of real-time security monitoring and points out some key features of real-time security monitoring solutions. When you finish reading, you’ll be well-versed in the missing piece of the modern perimeter security puzzle.
The importance of real-time security monitoring

The harsh reality of the current cyber attack landscape is that your network constantly faces new and emerging threats. The more widespread accessibility of diverse hacking tools and the emergence of dark web underground services have lowered the barriers to entry for conducting cyber attacks.
Couple that with the lucrative nature of the cybercrime market—expected to top $20 trillion by 2026—and you have a situation where you need constant visibility into traffic and other network events. This constant visibility comes in the form of real-time security monitoring tools that track information and alerts about events in your network as they happen (as opposed to periodic data collection, which does not suffice for dealing with ever-present threats in complex environments).
Some of the benefits you get from real-time security monitoring include:
- Improved threat detection and response times: An offshoot of today’s more complex, virtualized, and cloud-based networks is that it becomes harder to spot and respond to genuine threats. Real-time security monitoring cuts down the lag between when a suspicious event occurs and the time taken to analyze, verify, and respond to that threat.
- Reduced data breach risks: The prospect of a severe data breach is what probably keeps most CISOs awake at night. This fear is understandable, given the high costs and reputational damage from data breaches. Sophisticated attacks like ransomware often see threat actors lurking for days or weeks with the intent to steal data, but real-time security monitoring makes it easier to spot anomalies and protect your most valuable information assets.
- Better visibility into network activity: another benefit of real-time security monitoring is getting better total visibility into network activity. This visibility enables you to establish baselines of what’s normal to quickly pinpoint deviations. You also get reduced cybersecurity risks when you have a centralized view of what’s happening, whether it’s in the cloud or the communications between endpoints and data centers.
Types of real-time security monitoring
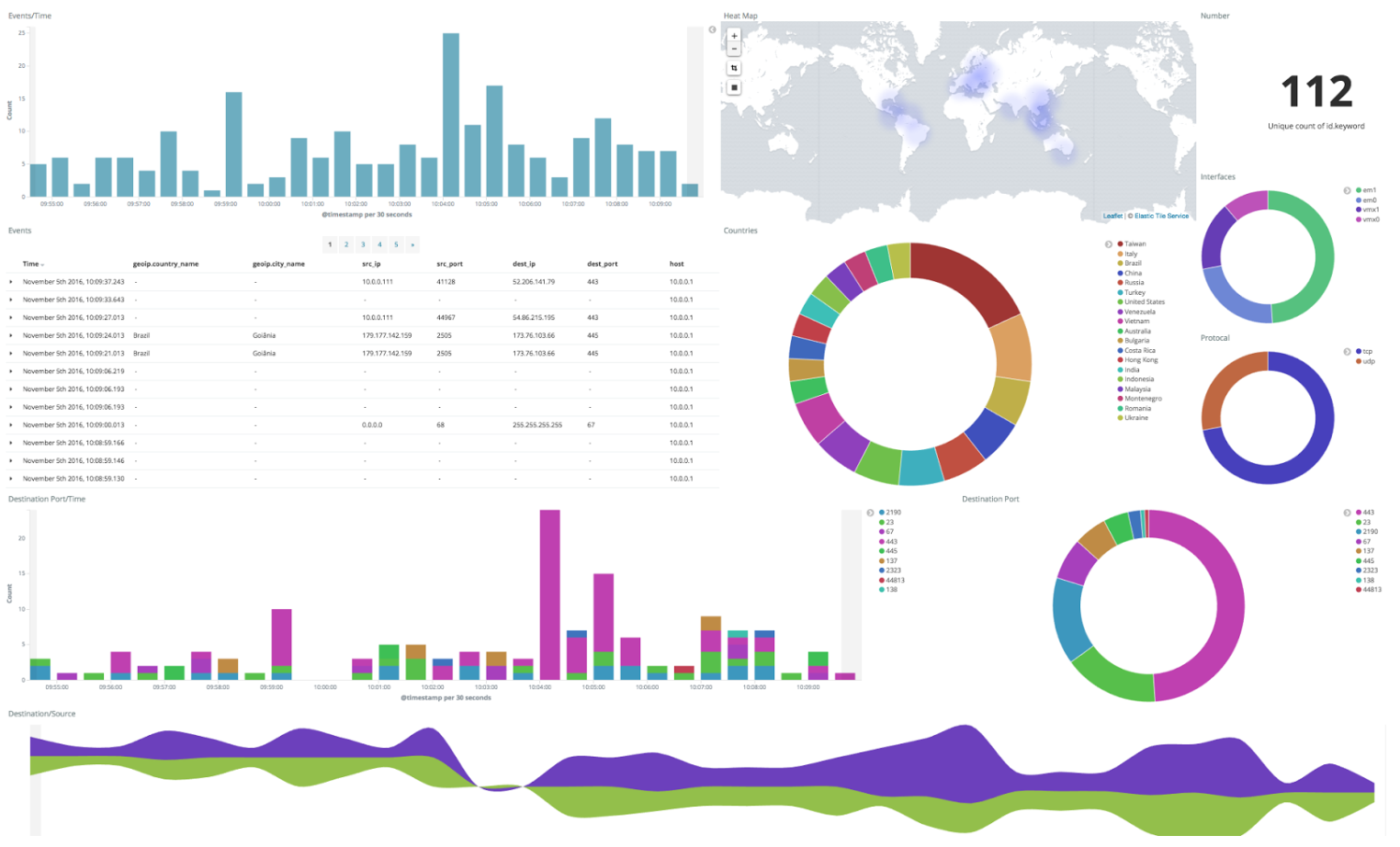
Real-time security monitoring is an umbrella term that captures a range of specific solutions capable of collecting and analyzing information as it’s generated. Here are some of the main types of real-time security monitoring tools you can opt for on your network:
- Security information and event management (SIEM) tools collect log data and traffic data from devices, monitor in real-time for events, and correlate the data to identify anomalies and attack patterns. SIEM tools often come with intuitive dashboards that help maintain simple visibility over what’s happening on your network, although some require a lot of fine-tuning to get right.
- Endpoint detection and response (EDR) tools that gather and analyze information from your desktop workstations, registered user devices, smart IoT devices, and other endpoints. The benefit of these tools is their visibility into perhaps the most vulnerable area of cybersecurity; the end users (specifically, employees) that interact with your apps and data.
- Intrusion detection and prevention systems (IDPS) tools can operate in two modes: detection and prevention. They monitor network and system activity for suspicious behavior, such as attempts to breach firewalls or exploit vulnerabilities, and can alert security teams in real-time or take immediate action to prevent an intrusion, such as blocking traffic from a suspicious IP address.
- Web Application Firewalls (WAFs) inspect incoming web traffic and apply rules to detect and block malicious requests, such as SQL injection and XSS attacks. WAFs protect web applications from vulnerabilities and security exploits that could compromise sensitive data, damage reputation, or disrupt business operations.
- Data Loss Prevention (DLP) solutions use various technologies, such as content filtering, encryption, and access controls, to identify and protect sensitive data. DLP solutions monitor and control data in motion, data at rest, and data in use, to help organizations comply with regulations and standards and reduce the risk of reputational damage, legal penalties, and financial losses resulting from data breaches.
- User and Entity Behavior Analytics (UEBA) tools use ML and data analytics to identify user and entity behavior anomalies within a network. UEBA tools establish a baseline of normal behavior and monitor network activity for deviations from that baseline, indicating potentially suspicious or malicious behavior. They can detect insider threats, compromised accounts, and other security incidents that traditional security solutions may miss. This way, UEBA tools can enable early detection of threats, reduce response times, and provide actionable intelligence for incident response and forensic investigations.
- Threat intelligence platforms collect, analyze, and disseminate threat intelligence from various sources, including public and private sources, social media, and dark web forums. They can provide valuable context about threat actors, their tactics, techniques, and procedures (TTPs), and indicators of compromise (IOCs), which can help organizations identify and prevent potential security incidents. These platforms can also integrate with other cybersecurity solutions, such as the previously-mentioned SIEM and EDR, to provide a more comprehensive and automated approach to threat detection and response.
- Cloud Security Posture Management (CSPM) solutions automate the assessment of cloud configurations against industry best practices and compliance standards and identify potential misconfigurations, security risks, and compliance violations. CSPMs provide a unified view of the organization’s cloud environment, allowing security teams to quickly identify and remediate security issues. They can also integrate with cloud security solutions such as Cloud Access Security Brokers (CASBs) and Identity and Access Management (IAM) tools to provide a more comprehensive and automated approach to cloud security.
Key features of real-time security monitoring solutions
With many different tools available and many marketing teams listing real-time security monitoring as a feature of their company’s solutions, what are some key capabilities to watch out for as a CISO and ensure you get the most value from a potential investment?
✔ Monitoring privileged user account activity: with these accounts holding the keys to the kingdom of your most valuable systems and assets, solutions that monitor their activity in real-time can prove indispensable in preventing breaches.
✔ Machine learning: look for tools that use machine learning to progressively improve their performance over time, ideally using training data from your own network.
✔ Actionable, real-time alerting: tools that watch out for suspicious activity aren’t much use if they don’t notify you immediately. Ideally, you want contextualized, high-fidelity, real-time alerts, which means you can trust and act on the information in those alerts without wasting time figuring out the best course of action or chasing down false positives. Additionally, single-event alerts are less useful than stringing events together into a meaningful play-by-play account of a suspected attack. A good solution should provide event aggregation to generate meaningful attack narratives.
✔ Automated threat response: it’s worth looking for tools emphasizing automation. Of particular value is automated response that uses rule-driven logic to initiate proactive responses to security incidents.
Challenges and considerations for implementing real-time monitoring
Of course, implementing real-time security monitoring is not as simple as plugging in and playing whatever tools you procure. Aside from the sheer complexity and fluid nature of today’s networks, there are other challenges and considerations worth thinking about. Some challenges include:
- Alert overload: implementing new tools that give you visibility into all that’s happening in real-time can be a blessing or a curse, depending on how those alerts are managed and contextualized. The truth is, many security teams faced with a large (and increasing) volume of security alerts find that many of those are false positives, leading to alert fatigue and decreased effectiveness of incident response.
- Budget: your available budget dictates the kinds of solutions you can invest in. You may need to make some hard choices, such as opting for a cheaper tool with a more complicated user interface that takes longer for users to adapt to.
- Staffing: bear in mind that implementing real-time security monitoring comes with staffing headaches, such as being able to use different/new types of tools or being able to respond effectively under pressure to alerts.
- Tracking endpoint activity: endpoints in modern networks are notoriously slippery to keep track of. With endpoints like printers, smartphones, and connected personal devices popping up and connecting to your network constantly, it can feel daunting to keep track of new and existing endpoints in real-time.
- Conflicting data: When using several tools, sensors, or software agents to monitor different activities on your perimeter, there are always risks from conflicting data that can add to the confusion rather than flag suspicious incidents.
- Restricted visibility: It’s also worth pointing out that traditional security tools focus inside the corporate perimeter–while that’s a good start and may help protect corporate data and employees from some cyber threats, it’s not enough to protect customers or to stop threats that harm your brand’s integrity despite originating outside the organization’s cybersecurity perimeter.
Some general pointers for implementing real-time monitoring are:
- Ensure you train staff on how to use any new tool, regardless of how simple it promises its user interface to be.
- Don’t neglect to monitor user activity because their behavior is often the first indicator of an in-progress attack.
- Favor solutions that use artificial intelligence, machine learning, and automation, as these three capabilities can save much of the grunt work.
- Pick your targets carefully and consider a phased implementation where you get continuous monitoring of the most important systems, users, and infrastructure first.
- Ensure potential solutions integrate well with your existing tool stack to avoid gaps in visibility.
Mitigating attacks with the missing piece in a secure perimeter
To exemplify how real-time security monitoring is the missing piece in a secure perimeter, let’s examine its potential use in a common type of cyber attack: account takeover attacks. In these attacks, threat actors gain control of a legitimate user’s account (e.g., by phishing) and use this to further their goals, whether exfiltrating data, installing ransomware, or committing fraud. Real-time monitoring can help flag these attacks by:
- Analyzing traffic and identifying suspicious patterns of activity associated with certain users or devices (e.g., strange login times).
- Detecting when attackers attempt to use stolen accounts to perform activities that aren’t normally associated with that account.
- Providing behavioral insights that act as a form of threat intelligence so security teams can better anticipate adversaries’ next moves and tactics.
- Identifying users who were lured into fake sites and had their credentials stolen.
Maintain the trust of your customers and partners
While traditional real-time security monitoring solutions can help bolster perimeter security and fill in the gaps that older solutions leave exposed, it’s important to think outside the box as threat actors do.
Cyber attacks such as brand impersonation regularly occur outside your perimeter, where imposters create fake websites and communications to lure in unsuspecting customers. These attacks are hard to detect even with the latest perimeter-focused real-time solutions. Besides, while they start outside the perimeter, they often end up inside the perimeter when stolen credentials are used to breach your walls.
Broaden the scope of your real-time monitoring strategy to combat these trickier threats like impersonation attacks that standard real-time monitoring tools fail to detect. Memcyco has created a Proof of Source Authenticity (PoSA™) suite of tools that provide real-time detection of impersonation attacks for both end users and your brand.
Your security teams get instant alerts on spoofing, cloning, and other impostor attempts, while also end users get effective protection against the damaging impacts of these attacks. Memcyco integrates with your SIEM solution for comprehensive real-time security monitoring both in and outside your perimeter. Book your demo here.


















