Two deceptive tactics—spoofing and phishing—are at the core of many cyberattacks. Understanding these threats is essential for protecting your digital assets.
What is spoofing?
Spoofing is a deceptive practice where an attacker disguises their identity or the identity of a malicious resource to appear as a trusted or legitimate entity. The attacker aims to gain unauthorized access to systems, steal sensitive information, or spread malware.
Types of spoofing
Website spoofing:
Attackers create fake websites that look like real ones. They mimic design and content, and use similar domain names, with the aim of stealing information or spreading malware. Even careful individuals can fall for these tricks. For example, a fake banking website may capture login credentials and use them to access customer accounts (Account Takeover, or ATO).
Email spoofing:
Attackers make an email look like it’s coming from someone you know, by using techniques such as altering the “From” field, which is possible since some email systems don’t verify the sender’s identity. In addition, attackers will tamper with the email’s look-and-feel and with the language used, to make sure it is hard to tell apart the fake email from real ones sent by that person.
Caller ID spoofing:
Attackers alter the caller ID to make it look like the call comes from a trusted source, such as a bank or a government agency. The goal is to trick the recipient into providing personal information. An example would be a scam call pretending to be from tech support asking for remote access to a computer.
The Dangers of Spoofing
Spoofing can have serious consequences. For individuals, it can mean losing money, exposing personal information, and compromising online accounts. Businesses can suffer from reputational damage, loss of customer trust, financial losses, data breaches, disrupted operations, higher security costs, and losing their competitive edge.
Tools and Solutions for Spoofing Prevention:
- Email Authentication Protocols: Implement SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) to authenticate emails and reduce the risk of email spoofing.
- Secure Browsing: Use web filters and trusted browsing tools to block access to malicious websites.
- Caller Verification: Verify the caller’s identity by calling back the organization’s official number.
Technical Defenses Against Spoofing
Traditional defenses, like the ones described above, are valuable tools in the fight against spoofing attacks. However, these solutions often rely on detecting known threats and patterns.
Real-time detection and response are crucial for addressing the limitations of traditional defenses. As an example, Memcyco helps detect and prevent website spoofing attacks by providing real-time protection and visibility to attacked companies and their customers. In other words, Memcyco can tell you in real time when someone uses a fake version of your website – for example in order to steal user credentials. By continuously monitoring for fraud and other suspicious activities, businesses can identify and neutralize spoofing attacks before they cause significant harm. This proactive approach protects customers and brand reputation and provides valuable insights into attacker tactics and targeted vulnerabilities.
What is Phishing?
Phishing involves sending fake communications (like emails, texts, and social media messages) that look like they come from legitimate sources. The goal is to trick people into giving up sensitive information, visiting harmful websites, or opening dangerous attachments.
Types of phishing
Email phishing:
Attackers send emails that appear to be from legitimate sources, such as banks or online services, asking recipients to click on a link or download an attachment. The link often leads to a fake website that steals login credentials or personal information. For example, an email that appears to be from a bank might ask you to verify your account details.
Spear phishing:
This targeted attack is aimed at a specific individual. The attacker gathers information about the target to create a more personalized and convincing message. For instance, an email might reference specific projects or colleagues to appear more legitimate.
Smishing (SMS phishing):
Attackers send text messages that appear to be from trusted sources, prompting recipients to click on a link or call a phone number. These messages might pretend there’s a problem with your account, that you have won a prize, etc. An example would be a text message which looks as if it’s from a well-known package delivery service, asking you to key in your credit card info in order to pay a small amount of money for faster delivery.
Vishing (Voice phishing):
Attackers use phone calls to trick victims into providing personal information. They might pose as a bank representative or tech support. An example would be a call from someone pretending to be from your credit card company, asking for your account details to resolve an issue.
Angler phishing:
This type of phishing takes place on social media platforms. Attackers create fake customer service accounts to lure victims into providing personal information. For example, you might tweet about a problem with a service, and a fake customer service account responds, asking you to provide your account details.
The Impact of Phishing
Phishing can lead to fraudulent transactions, stolen funds, and high business recovery costs. It can cause downtime, lost productivity, and legal liabilities. Phishing harms a company’s reputation, affecting customer trust, brand loyalty, and revenue.
Tools and Solutions for Phishing Prevention:
- Email Filtering: Use email filtering tools to detect and block phishing emails.
- Two-Factor Authentication (2FA): Enable 2FA to add an extra layer of security to your accounts.
- Security Awareness Training: Educate employees and individuals about the risks of phishing and how to recognize phishing attempts.
- Real-Time Threat Detection: Implement real-time threat detection systems to identify and block phishing attempts before they reach users.
Anti-Phishing Strategies
Similar to spoofing, traditional anti-phishing strategies like email filtering, link analysis, and behavioral analysis have limitations. These methods often struggle to keep pace with cybercriminals’ constantly evolving tactics.
Real-time detection and response are essential for combating phishing attacks. Businesses can quickly identify and block phishing attempts by analyzing user behavior, network traffic, and other indicators in real time, preventing them from reaching their intended targets. This proactive approach minimizes the risk of compromised credentials, data breaches, and financial losses. Additionally, real-time response allows immediate action, such as blocking malicious links, quarantining suspicious emails, and alerting users of potential threats.
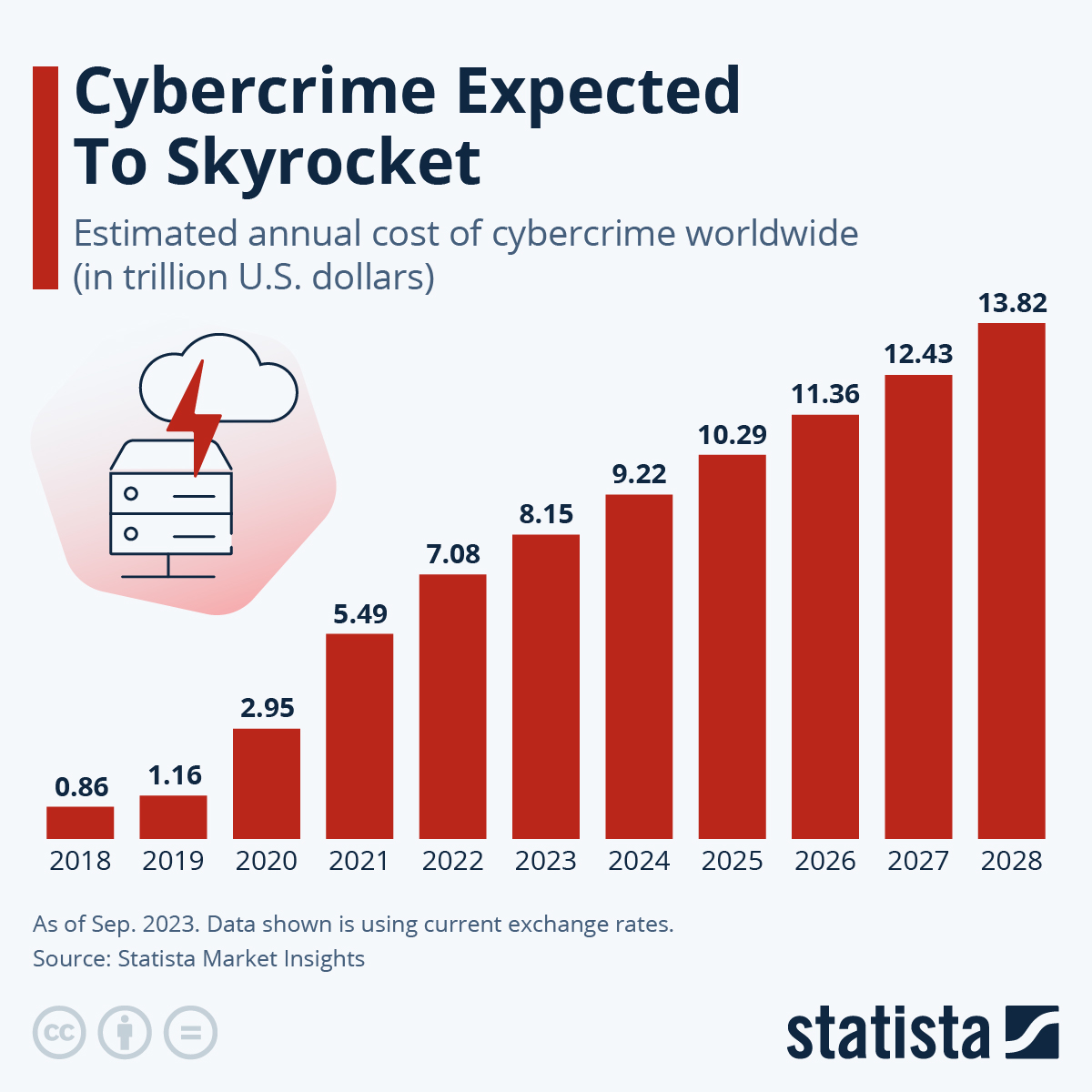
Spoofing vs. Phishing: A Head-to-Head Comparison
Spoofing involves manipulating identifiers like email addresses, websites, or phone numbers to impersonate a trusted entity. The goal is to deceive the victim into believing they are interacting with a legitimate source.
Phishing relies on communications to manipulate victims. Attackers craft deceptive messages, often using urgent or enticing language, to trick individuals into clicking on malicious links, downloading harmful attachments, or revealing sensitive information.
Both methods rely heavily on social engineering. Here are some examples of social engineering tactics used:
- Impersonation: Attackers pose as someone the victim knows or trusts, such as a colleague, boss, or company representative. For example, an email from your company’s IT department might appear to ask you to reset your password.
- Urgency: Messages often create a sense of urgency to prompt immediate action. For example, an email might claim that your account will be locked unless you verify your information right away.
- Fear: Attackers use fear to coerce victims into compliance. For example, an email might warn that your bank account has been compromised and that you need to click a link to secure it.
- Greed: Offers of rewards or financial gain are common. For example, an email might promise a gift card in exchange for filling out a survey.
- Curiosity: Intriguing or sensational subject lines entice victims to open emails. For example, a subject line might read “Important update on your recent purchase” to get you to click.
Spoofing and phishing are distinct techniques but are often used in conjunction. For example, a phishing email might contain a link that directs the recipient to a spoofed website designed to steal login credentials.
The combination of tactics makes these attacks more convincing and challenging to detect. It also makes it harder to stop them, because the spoofed elements lend an air of legitimacy to the phishing attempt, increasing the likelihood that victims will fall for the scam. Attackers often use spoofing to bypass security measures and create a sense of urgency or authenticity, manipulating the victim into taking actions they otherwise wouldn’t, such as clicking on a malicious link or providing sensitive information.
| Spoofing | Phishing | |
| Definition | The act of impersonating a trusted person or entity. | The fraudulent practice of sending communications that appear to be from reputable sources. |
| Goal | Gain unauthorized access to systems, steal sensitive information, or spread malware. | Trick victims into revealing personal information, clicking on malicious links, or downloading harmful attachments. |
| Focus | Technical manipulation of digital assets (e.g., email headers, websites, phone numbers). | Manipulating communication channels |
| Varieties | Website spoofing, email spoofing, caller ID spoofing, etc. | Deceptive emails, text messages, phone calls, social media messages, etc. |
| Examples | A fake website that looks like a bank’s login page; a spoofed email from a trusted colleague; a phone call from a fake tech support agent. | An email claiming to be from a bank asking for login credentials; a text message offering a gift card; a phone call from a fake IRS agent. |
| Relationship | Spoofing can be used in phishing attacks (e.g., a phishing email may contain a link to a spoofed website). | Phishing attacks often rely on spoofed assets to appear more legitimate. |
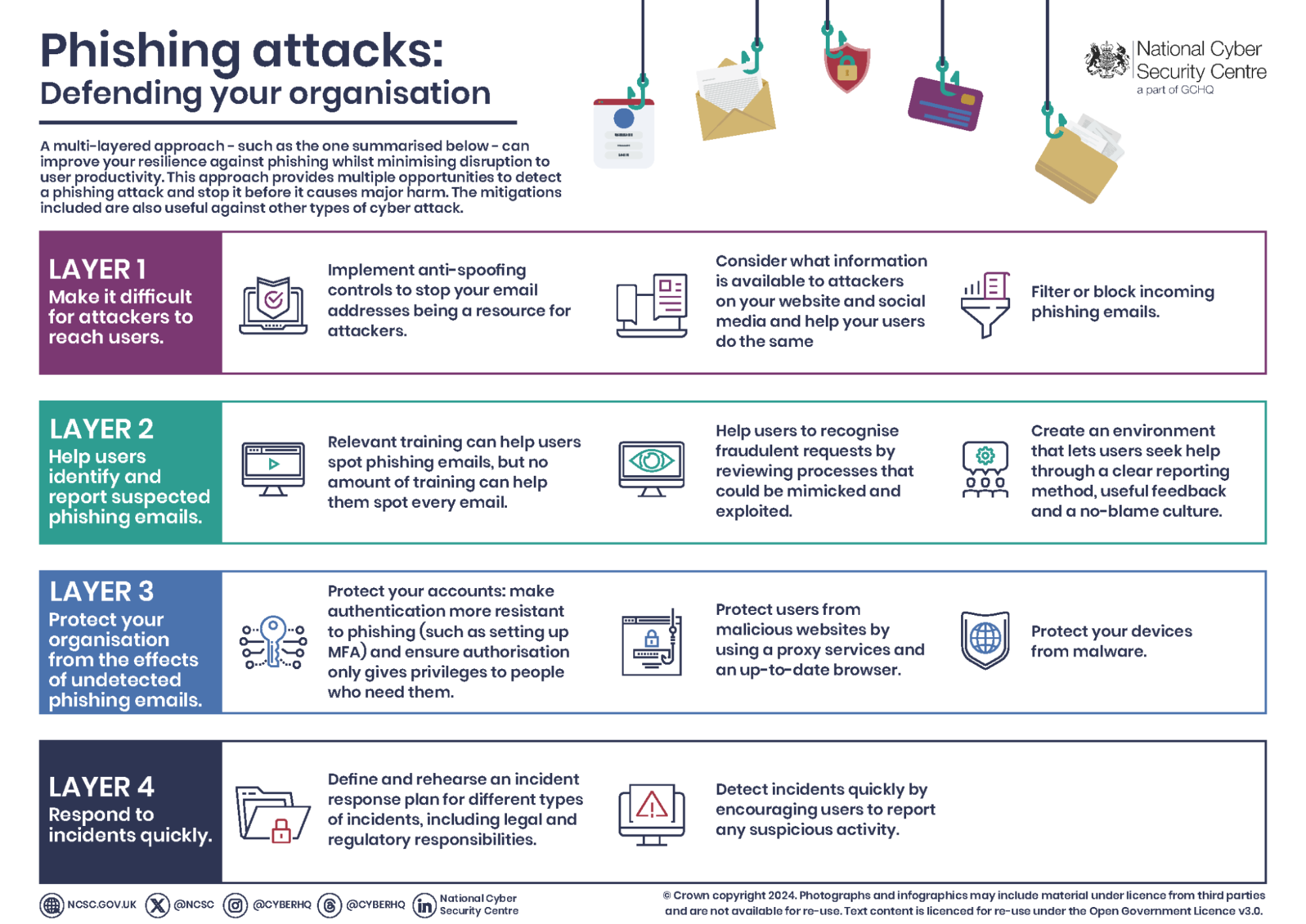
Defending Against Digital Deception: Advanced Strategies
Defending against spoofing and phishing attacks necessitates a multi-faceted strategy encompassing user education, robust technical safeguards, and proactive, real-time threat detection.
For Businesses:
- Implement robust email security protocols: Use SPF, DKIM, and DMARC to authenticate emails and prevent spoofing.
- Deploy web filtering and anti-phishing solutions. These tools can block access to known malicious websites and detect phishing attempts.
- Educate employees about security risks: Conduct regular security awareness training, a staple component in cyber risk management, to teach employees how to identify and report suspicious activity.
- Monitor for suspicious activity. Use intrusion detection and prevention systems to detect and block unauthorized access attempts.
- Implement real-time threat detection: Use solutions that can identify and stop spoofing and phishing attacks in real-time before they reach users.
- Embrace passwordless authentication: Transitioning to passwordless authentication methods, such as biometrics or security keys, can significantly reduce the risk of phishing attacks that target user credentials.
For Individuals:
- Be wary of unsolicited communications. Exercise caution when receiving unexpected emails, text messages, or phone calls, especially those requesting personal information or urging immediate action.
- Verify the sender’s identity. Double-check the sender’s email address or phone number, and be wary of slight variations or misspellings.
- Avoid clicking on suspicious links or attachments. Hover over links to preview the URL, and be cautious of attachments from unknown senders.
- Use strong, unique passwords: Create complex passwords and avoid reusing them across different accounts.
- Enable two-factor authentication (2FA): Add an extra layer of security by requiring a code from your phone or another device to log in.
- Stay informed about the latest scams: Keep up-to-date on current phishing and spoofing techniques to recognize and avoid them.
General Best Practices
Embracing a zero-trust security model is paramount. This model operates on the principle of “never trust, always verify,” implementing stringent access controls, continuous authentication, and micro-segmentation to minimize the potential impact of a security breach.
Multi-factor authentication (MFA) is a critical digital asset protection method. MFA significantly bolsters security by mandating multiple verification factors, such as one-time codes, even if an attacker compromises a password.
Regular security awareness training is indispensable. It educates employees about evolving threats, empowers them to identify and report suspicious activity, and effectively serves as the first line of defense against spoofing and phishing attacks.
Don’t Get Spoofed or Phished: Take Control of Your Digital Security
The threat of spoofing and phishing attacks is not just a looming possibility. It’s a daily reality for businesses and individuals alike. These attacks have the potential to cause devastating financial and reputational harm.
But you don’t have to be a passive victim.
Don’t let cybercriminals dictate your security. Book a demo with Memcyco and discover how our cutting-edge technology can protect your business and customers from the ever-present threats of spoofing- and phishing-based digital impersonation.



















