Every day, new headlines emerge about another major corporation falling victim to a cyberattack, leaving businesses everywhere questioning their vulnerabilities. These breaches underscore the critical need for thorough risk assessments to identify and mitigate potential weaknesses. Proactively managing risks enables organizations to better defend against the relentless wave of cyber threats.
According to the World Economic Forum, 45% of leaders said operational disruption is their most significant concern regarding cyber incidents. This concern underscores the vital importance of a robust risk assessment framework, as unanticipated disruptions can cripple an organization’s operations and erode stakeholder confidence.
Imagine transforming this challenge into an opportunity. What if you could have a straightforward, structured method to uncover every potential risk, ensuring no threat goes unnoticed? A comprehensive risk assessment template could be the game-changer your organization needs, transforming how you approach cybersecurity.
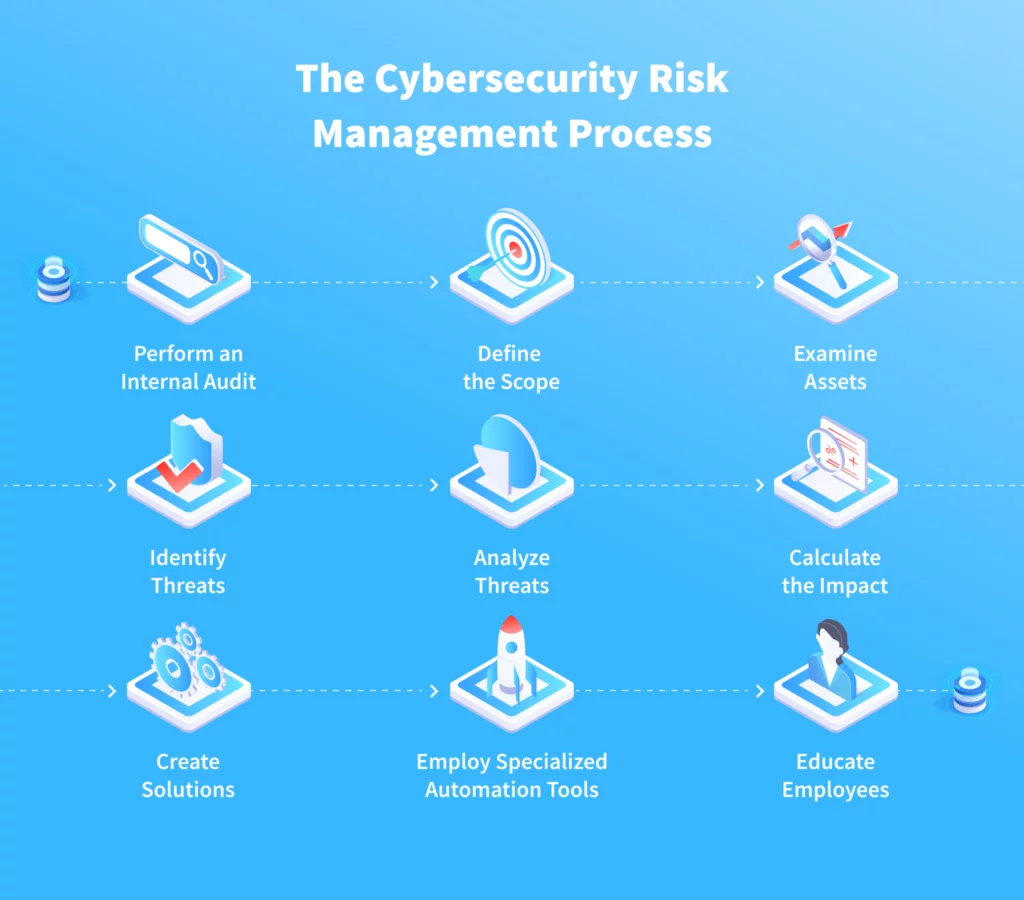
Understanding Cybersecurity Risk Assessment (What and Why)
Cybersecurity risk assessments involve identifying, analyzing, and evaluating risks associated with digital assets, including hardware, software, data, and network infrastructure. It requires understanding the potential threats, vulnerabilities, and impacts on your organization. There are three main types of risk assessments:
- Qualitative: This approach focuses on risk nature and severity. For example, it might call for conducting workshops with stakeholders to identify, say, phishing as a top concern and suggest employee training as a mitigation strategy.
- Quantitative: Uses numerical data to estimate the probability and impact of risks. For instance, analyzing past security breaches to determine a 20% chance of a data breach within the next year, with an estimated financial impact of $500,000.
- Hybrid: This method combines both qualitative and quantitative methods. For example, it starts with interviews to list potential cybersecurity threats and then uses statistical analysis to measure their likelihood and impact.
Regular risk assessments improve your security posture, reduce the attack surface, and ensure compliance with regulatory requirements.
The Importance of Regular Risk Assessments
Conducting regular risk assessments is crucial for several reasons:
- Improving Security Posture: Regular assessments help identify new vulnerabilities, enabling organizations to proactively adapt their cybersecurity strategy.
- Reducing Attack Surface: By continuously monitoring and addressing risks, organizations can minimize the points of vulnerability that attackers could exploit.
- Ensuring Regulatory Compliance: Industries such as healthcare (HIPAA), finance (GLBA, PCI DSS), and critical infrastructure (NERC CIP) require regular risk assessments and documentation of security measures. Compliance with these regulations helps avoid legal penalties and enhances trust with customers and partners.
5 Key Components of a Risk Assessment Template
A comprehensive risk assessment template should include the following sections:
- Asset Identification: List all critical assets, including hardware, software, data, and personnel. For example, identify all servers, workstations, databases, and key employees in maintaining cybersecurity.
- Threat and Vulnerability Assessment: Identify potential threats and vulnerabilities using sources such as past incident reports, threat intelligence feeds, vulnerability scanners, and penetration testing results. For instance, assess vulnerabilities in software applications and potential threats like malware or insider attacks. Utilizing diverse risk assessment methods can streamline this process, making it more effective.
- Risk Analysis: Analyze the likelihood and impact of each identified risk using qualitative or quantitative methods. For example, evaluate the potential impact of a data breach on customer trust and financial losses.
- Risk Prioritization: Rank risks using a risk matrix based on their severity and likelihood, ensuring high-priority risks are addressed first. Use a risk matrix to visualize and prioritize risks.
- Mitigation Strategies: Develop strategies to mitigate identified risks. This could include implementing security controls, updating software, or conducting regular employee training sessions. For instance, introducing multi-factor authentication to reduce the risk of unauthorized access can be a crucial mitigation strategy, as highlighted in various best practice guides.
To effectively use each section, gather accurate and relevant data, involve key stakeholders, and ensure regular updates to the assessment.
How to Use the Downloadable Risk Assessment Template
You can quickly adapt the risk assessment template to suit various organizations and industries. You can tailor it in the following way:
- Large Enterprises: Incorporate advanced security measures like intrusion detection systems and incident response plans. Large enterprises must perform detailed risk analysis for complex IT infrastructures and ensure compliance with various regulations.
- Healthcare Providers: Review and address specific regulations, such as HIPAA and the HITECH Act. Healthcare providers should prioritize asset visibility for their medical assets, including electronic health records (EHRs) and physical medical devices.
- Financial Institutions: Emphasize fraud detection and prevention mechanisms and compliance with financial regulations. Financial institutions must focus on risks like account takeover fraud and ensure robust security measures to protect financial transactions.
When tailoring the template, consider industry-specific risks and regulations such as GDPR for data privacy, SOX for financial reporting, and CCPA for consumer privacy. For example, healthcare providers should prioritize patient data protection, while financial institutions should focus on fraud detection and prevention.

6 Benefits of Using a Risk Assessment Template
A risk assessment template is valuable for organizations planning their cybersecurity risks systematically. Here are the key benefits, elaborated with insights and details:
1. Streamlined Process
A risk assessment template simplifies and accelerates the risk assessment process, making it accessible even for organizations with limited resources. A standardized template ensures that all necessary steps are covered and no critical details are overlooked. In most cases, small and medium-sized businesses don’t have large cybersecurity teams. These organizations can efficiently identify and mitigate risks by following a structured template without requiring extensive manual effort.
Example: Instead of starting from scratch, an organization can use the template to quickly list assets, identify potential threats, and document vulnerabilities. This saves time and ensures a comprehensive approach.
2. Consistency
Using a template ensures a standardized approach to risk assessment, improving the results’ reliability. Consistency is critical for comparing assessments over time and identifying trends or recurring issues. Organizations can maintain uniformity across different departments with a template and ensure all risk assessments are conducted using the same criteria and methodology.
Example: A multinational corporation can ensure that its branches in different regions follow the same risk assessment process, making it easier to compare and analyze results globally.
3. Improved Quality
A detailed template enhances the overall quality of risk assessments by providing a structured and comprehensive framework. It ensures that all aspects of risk management are considered, from identifying assets to developing mitigation strategies. This comprehensive approach reduces the likelihood of overlooking critical vulnerabilities or threats.
Example: The template guides the assessor through questions and checklists covering various risk factors, ensuring everything is covered.
4. Enhanced Stakeholder Involvement
Involving key stakeholders in the risk assessment ensures diverse perspectives and comprehensive risk identification. Regularly reviewing and updating the risk assessment helps keep pace with the evolving threat landscape. For instance, involving IT, legal, and business departments can provide a holistic view of the risks and ensure that all potential impacts are considered.
Example: During the assessment, input from the IT department might highlight technical vulnerabilities, while the legal department could identify compliance risks, leading to a more robust risk management strategy. Insights from digital risk protection tools can provide additional layers of security.
5. Proactive Risk Management
Organizations can adopt a proactive approach to risk management by utilizing a risk assessment template. One must continuously monitor and update the risk assessment to accurately reflect changes in the threat landscape and organizational environment. Proactive risk management enables organizations to anticipate potential threats and implement preventive measures before they escalate into significant issues.
Example: Regular updates to the risk assessment template can incorporate new threat intelligence, ensuring the organization stays prepared for the latest cybersecurity challenges.
6. Regulatory Compliance
A structured risk assessment template helps ensure compliance with various regulatory requirements. Different industries have specific regulations that mandate regular risk assessments and adequate security measures. Using a template helps organizations meet these regulatory requirements systematically and consistently.
Example: Healthcare providers can use the template to ensure they comply with HIPAA regulations by systematically documenting risks to patient data and implementing appropriate safeguards.
Memcyco’s Expertise and Role in Risk Assessment
Memcyco brings extensive experience and expertise to help organizations assess and mitigate cybersecurity risks. We proactively design solutions to protect against website impersonation attacks, a crucial aspect of any risk assessment. Here’s how Memcyco’s solutions align with the critical components of a risk assessment:
- Asset Identification: Memcyco’s technology monitors your digital assets in real-time, ensuring that all critical assets, such as your website and customer data, are protected against impersonation attacks.
- Threat and Vulnerability Assessment: Memcyco’s solutions include advanced threat intelligence that identifies potential threats and vulnerabilities related to website impersonation.
- Risk Analysis: Our real-time monitoring and analytics provide detailed insights into fraud attempts, giving you full visibility of attack devices, timing, and victim identities. For instance, Memcyco can instantly detect when a phishing site mimics your legitimate website, allowing you to understand the potential impact and take action immediately.
- Risk Prioritization: Memcyco helps prioritize risks for identified threats, enabling organizations to focus on the most critical vulnerabilities first.
- Mitigation Strategies: Memcyco offers proactive mitigation methods, such as blocking attackers from using stolen data. These methods protect customers from falling victim to fraud, losing money, or having their identity stolen for other criminal activities.
Next Steps for Your Cybersecurity Journey
Our downloadable risk assessment template provides a practical tool for organizations of all sizes to manage their cybersecurity risks proactively. By utilizing this template and leveraging Memcyco’s advanced solutions, you can streamline the risk assessment process, ensure consistency, and improve the overall quality of your cybersecurity posture. Download the risk assessment template here and begin identifying and mitigating risks that could threaten your organization’s digital assets.
If you want to gain complete visibility over your digital threats and prevent attacks swiftly, book a demo with Memcyco’s team. Our real-time digital risk protection solutions help you detect and combat attacks as they unfold, so you can effectively secure your customers’ accounts and protect your brand online.



















