As mobile technology becomes integral to day-to-day life, fraudsters are refining phishing techniques to exploit vulnerabilities in mobile browsing. According to Zimperium’s 2024 zLabs Global Mobile Threat report, 82% of phishing sites specifically targeted mobile devices in 2023.
To protect customer data, enterprises need to counter-adapt. How fast that happens depends on their appetite for pivoting to proactive, and even disruptive, real-time approaches that don’t leave scam detection to the user.
Before we unpack such approaches, let’s cover the basics.
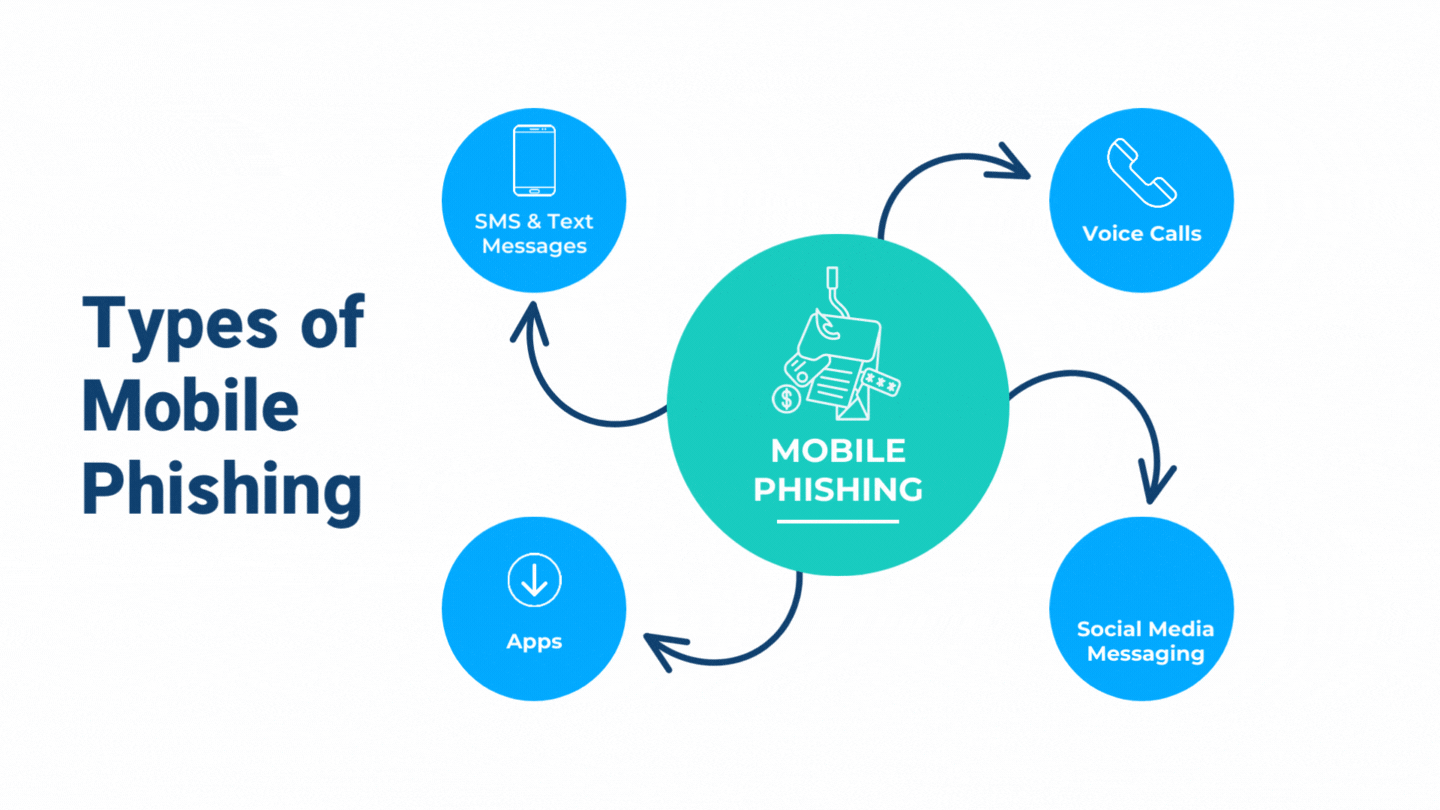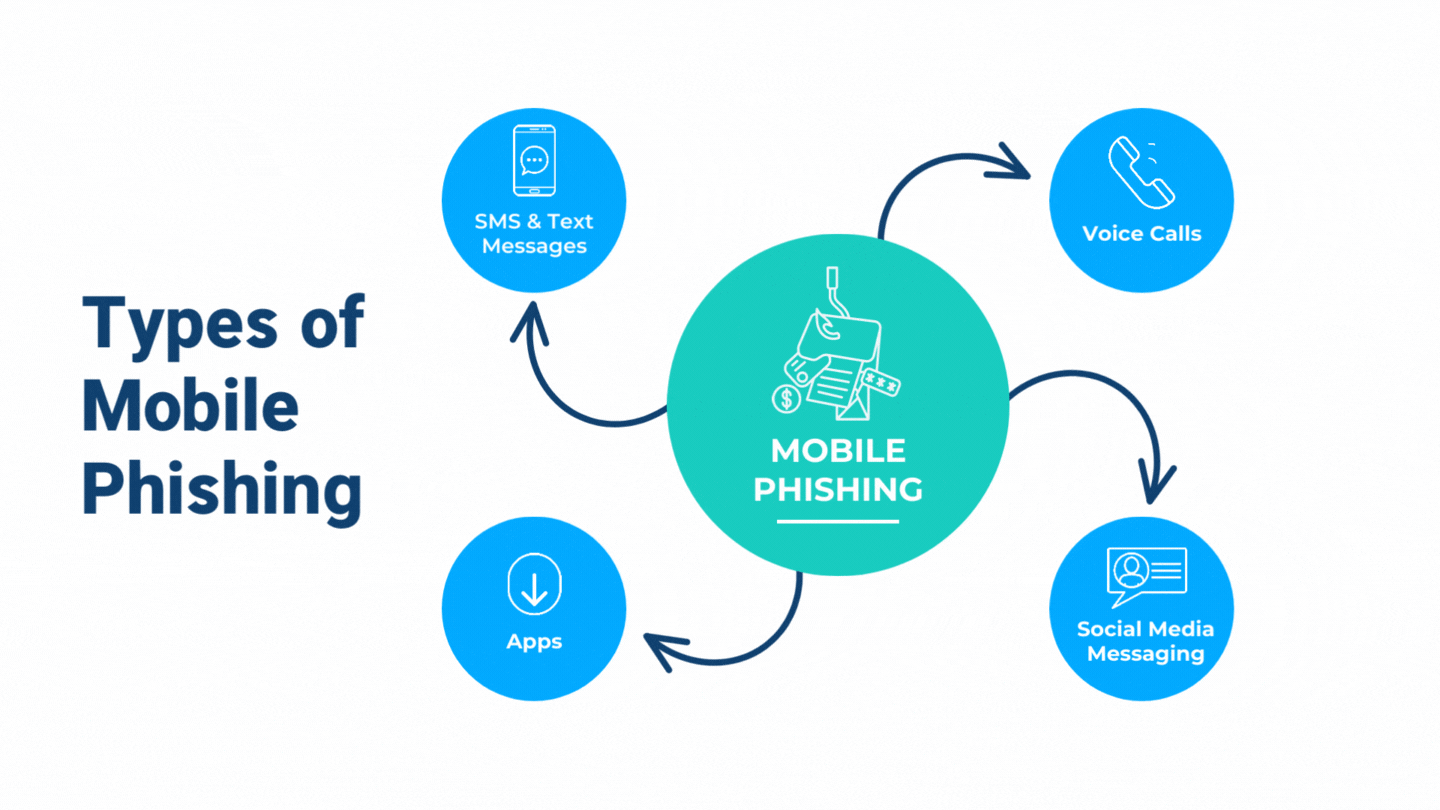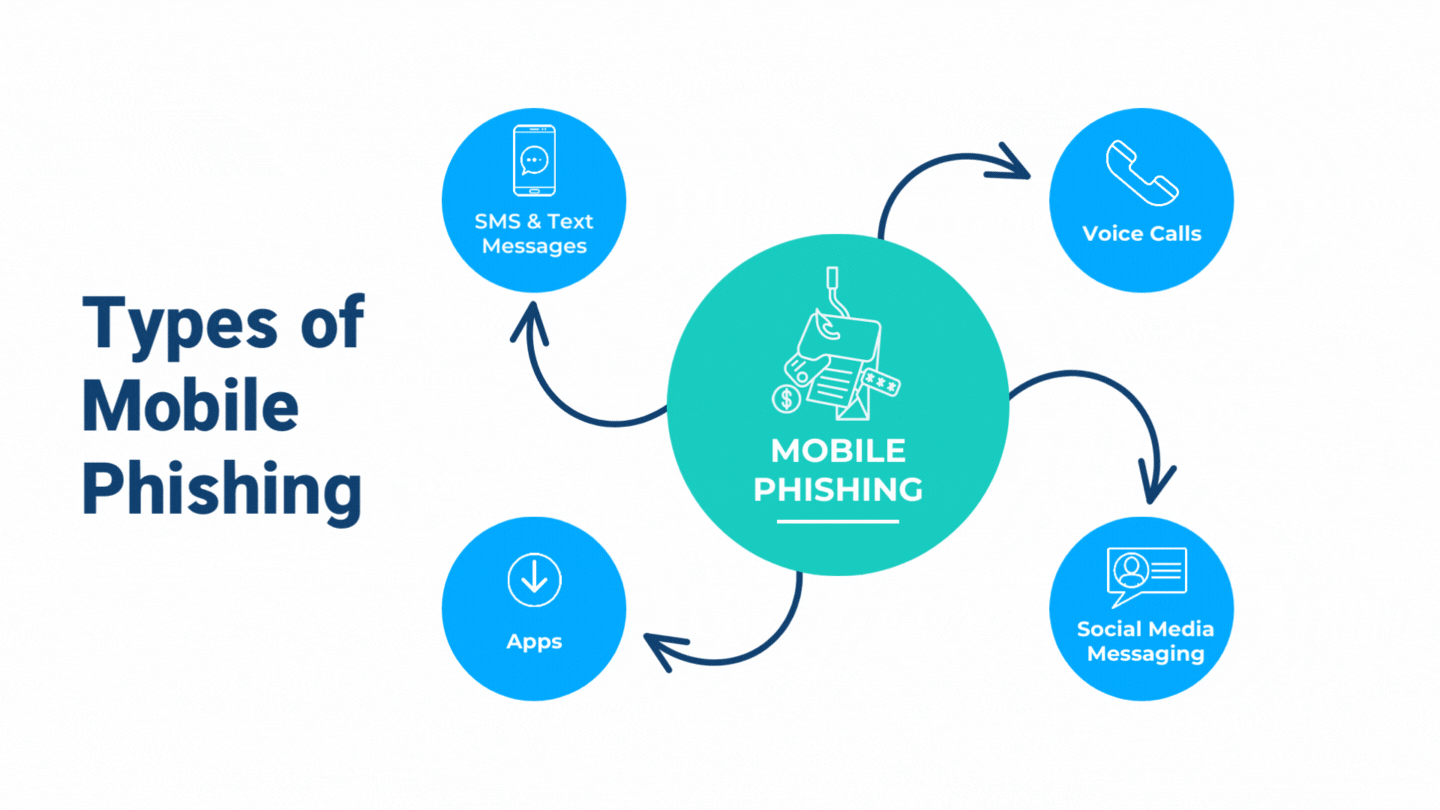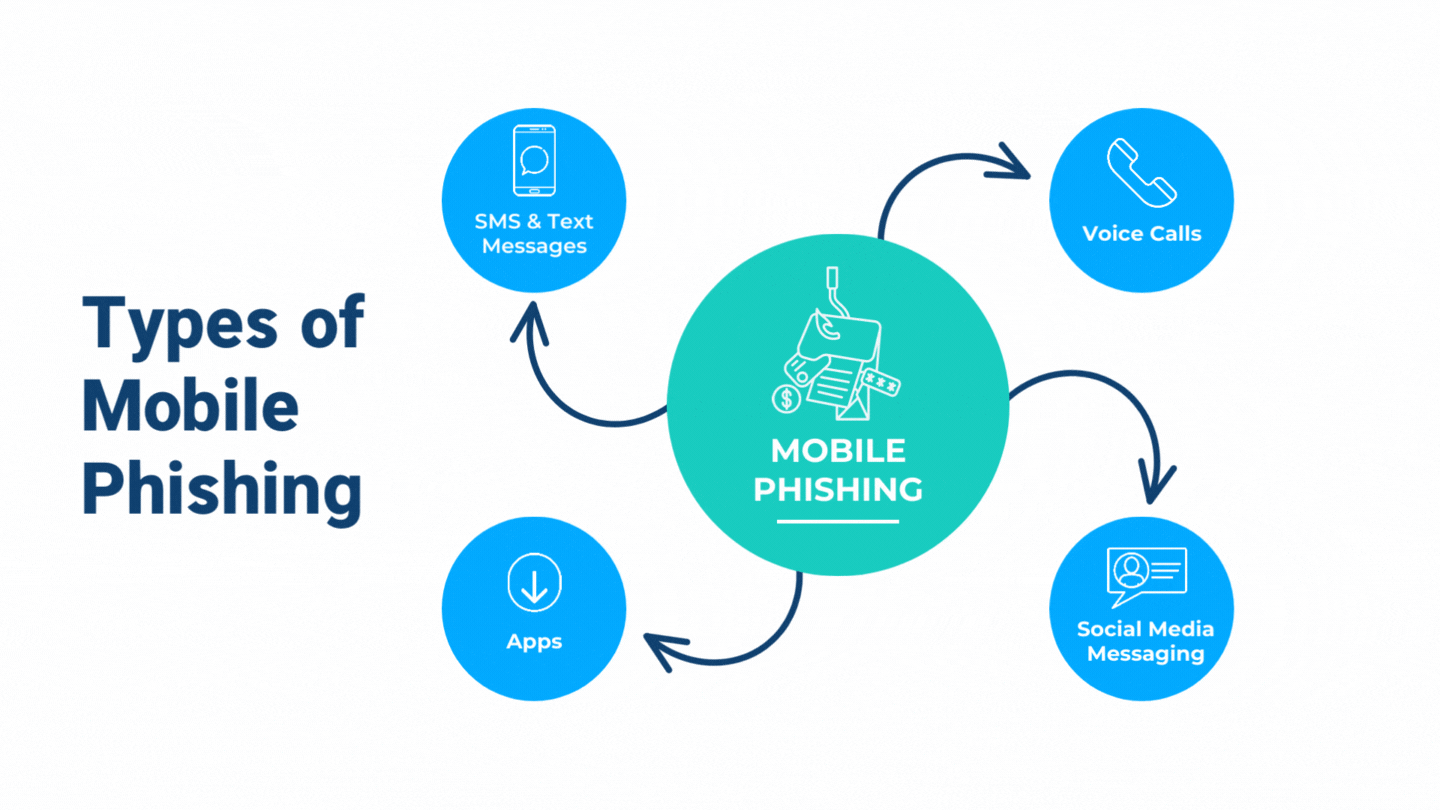
What is mobile phishing?
Mobile phishing refers to phishing attacks that are crafted specifically for mobile users. These attacks exploit mobile-specific traits, such as truncated URLs, multitasking behavior, and reduced screen space, which limit a user’s ability to verify the legitimacy of a website or link. Attack vectors include smishing (phishing via SMS), fraudulent apps, and deceptive websites designed to steal credentials, leading to financial loss, identity theft, or even full account compromise.
Industries at High Risk from Mobile Phishing Attacks
Enterprises in the following industries are particularly vulnerable to mobile phishing, given the nature of their interactions with sensitive data and frequent use of mobile platforms. These sectors face heightened exposure due to the valuable information they handle:
- Financial Institutions: Banks and fintech companies remain prime targets due to the high-value data they handle. Mobile banking applications are a lucrative target for attackers. In one example, the Bank of Ireland fell victim to a phishing campaign where mobile users were tricked into providing their login credentials via a fake mobile login page.
- Healthcare: With the digitization of healthcare, mobile devices have become critical for accessing patient data. According to Zimperium, a leading mobile security provider, 39% of mobile threats are directed at healthcare professionals, often through cloned hospital login pages that capture sensitive information.
- E-commerce and Retail: The widespread use of mobile shopping apps has made e-commerce a frequent target for phishing scams. Attackers mimic login pages for popular shopping platforms, such as the Target mobile app, to steal payment details and user credentials.
- Government and Education: Digital services in the public and education sectors have expanded, creating new opportunities for attackers. Phishing campaigns during tax season, for example, have successfully cloned IRS portals, tricking mobile users into submitting sensitive personal and financial data.
Each of these industries relies heavily on mobile platforms to handle critical transactions and data, making them attractive targets for mobile phishing attackers.
Which regions are most affected by mobile phishing Attacks?
According to Statista, in the second quarter of 2023, North America topped the list for the highest number of mobile phishing attempts, with almost half-a-million mobile phishing attempts. Europe came in a close second, with 462 thousand.
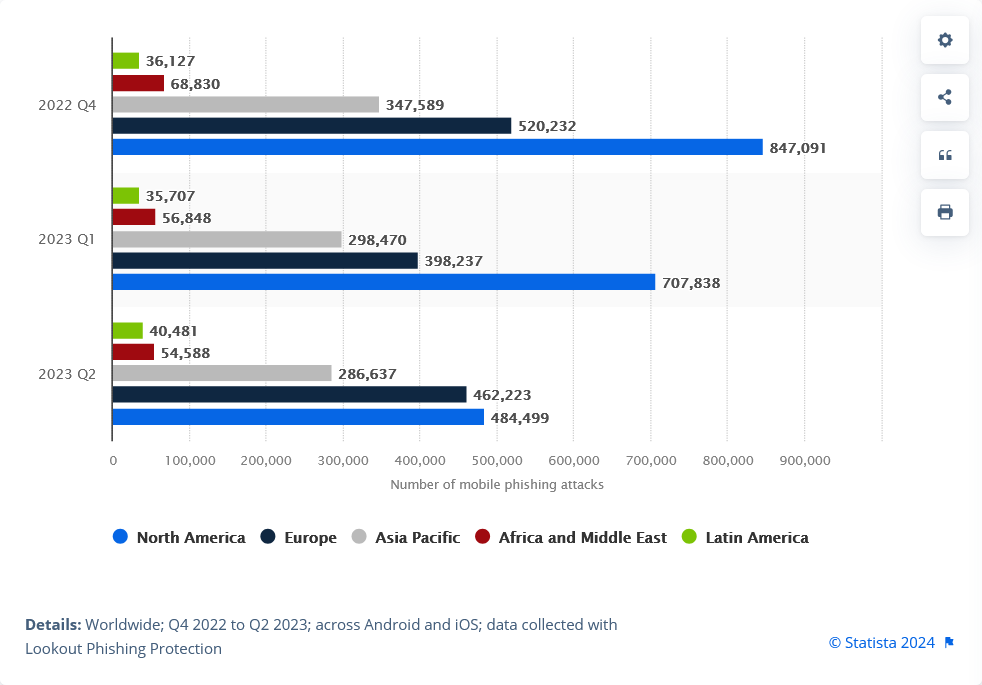
Rather than showing a significant downward trend, Statista’s data likely reflects a plateauing of mobile phishing attacks, as the spike in mobile traffic during the COVID-19 crisis tapers off.
Despite the apparent downward trend, mobile phishing attempts remain higher than the pre-COVID era. And the threat is being amplified as fraudsters leverage ‘Phishing-as-a-Service’, Generative AI and phish kits to increase the number of successful attacks.
The lesson here is that mobile is now the go-to medium for threat actors. To keep pace, enterprises should invest in new, proactive approaches for intercepting attacks preemptively, earlier in the attack lifecycle – and that means going ‘real time’.
Common Mobile Phishing Techniques
Mobile phishing tactics continue to evolve, exploiting the specific vulnerabilities of mobile devices. Some of the most common techniques include:
- Website Cloning for Mobile: Attackers create near-perfect replicas of legitimate websites, optimized for mobile devices. These cloned sites are often indistinguishable from the real ones, fooling even the most cautious users into entering their credentials.
- Shortened or Hidden URLs: On mobile devices, URLs are frequently shortened or truncated, making it difficult for users to spot a fraudulent link. Attackers take advantage of this by deploying shortened URLs that lead users to malicious websites.
These tactics demonstrate the increasingly complex and deceptive nature of mobile phishing, which cannot be fully countered by user vigilance alone.
Real-Time Mobile Phishing Attack Detection, Protection and Disruption Throughout the Attack Timeline
Memcyco’s real-time capabilities cover every stage of a phishing attack, offering real-time protection and response.
By adopting the following mobile-first security advantages, businesses can protect themselves and customer data from the growing wave of mobile phishing attacks.
Protection from Fake Progressive Web Apps
Memcyco provides real-time, enterprise-grade protection for businesses leveraging Progressive Web Applications (PWAs), detecting impersonated applications and websites at the moment of launch. By addressing the unique security risks associated with PWAs—such as their distribution outside of official app stores and their susceptibility to cloning—Memcyco’s solution offers proactive defense against mobile phishing campaigns that target these vulnerabilities, ensuring robust security for both users and businesses.
Live Monitoring
Once a phishing site is active, Memcyco tracks suspicious behavior, detecting cloned or impersonated websites in real-time. Memcyco flags phishing attempts as they unfold, triggering immediate alerts for businesses and their customers.
Red Alerts
Memcyco’s fake site Red Alerts are an immediate, actionable defense mechanism, triggered the moment a user encounters a malicious site. By intercepting interactions with fake sites in real-time, Red Alerts eliminate the reliance on customer intuition, providing an automated safety net that directly counters the phishing lifecycle.
Real-time Credentials and Card Data Protection
If users disregard Red Alerts and inadvertently input credentials or card data into impersonated sites, Memcyco auto-swaps them for marked decoy data that’s traceable, like marked money stolen during bank robberies. Thinking the data’s real, fraudsters will try to use them, locking themselves out while revealing investigable data.
Automated Takedown
Memcyco automates takedown requests for phishing sites and malicious domains, reducing the window of opportunity for attackers to cause harm. The intelligence gathered from each event feeds back into SIEM systems, enhancing the organization’s future detection capabilities.
Protect Customer Data from Mobile Phishing Attacks in Real Time, with Memcyco
Don’t leave mobile phishing attack detection to customers. Protect their data with proactive mobile phishing and prevention capabilities deployed throughout the attack timeline. Schedule a demo to learn about Memcyco’s unique, real-time mobile phishing detection and automated defense.