Whenever anything of value is transferred between parties online, there will be crooks lurking in the shadows, looking to defraud the participants. As consumers, we almost expect them to be there. As businesses, it’s often our responsibility to protect our customers and prospects from being defrauded by bad actors masquerading as our representatives.
Airline-related fraud accounts for an estimated 46% of all fraudulent online transactions. From a business perspective, this translates into approximately 1.2% of airlines’ mobile and website revenues being lost to fraud yearly. To put it in perspective, that’s over $1 billion yearly. What does airline impersonation fraud look like? And what can airlines do to rise above it?
What does impersonation fraud look like in the airline industry?
Impersonation fraud in the airline industry entails misusing passengers’ trust in the airline brand and its representation online. By creating malicious websites, impersonating social media accounts, and even spreading fake call center numbers, bad actors pretend to represent your airline to obtain data they can profit from.
Here are a few examples of common types of impersonation fraud:
Social media customer service impersonation
Especially easy to do on X (formally Twitter); bad actors create bogus social media accounts with the names and logos of airlines. Then, they use these accounts to reach out to passengers complaining about delays or cancellations, or just showing off their flight tickets on social media.
This fraud type is so popular that all UK airlines were impersonated on X this summer. Even though X’s policy states: “You may not misappropriate the identity of individuals, groups, or organizations or use a fake identity to deceive others,” reporting and having the fraudulent account removed is often slow and ineffective.
Moreover, sophisticated bad actors employ numerous accounts to continue conversations with the victims even when one account is inactive. They can simply claim to be a different CS representative using a different account.
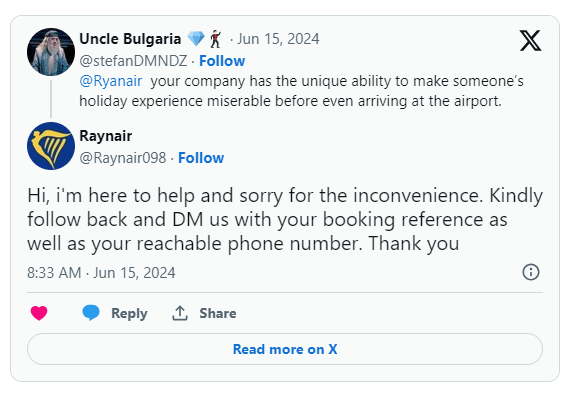
When disgruntled passengers turn to social media to complain about issues with their booking or flight, they are immediately contacted by bogus customer service representatives asking for personal information. The information potential victims hand over to those they believe are representatives of the airline can be used to perform a variety of cybercrimes – from credential compromise which can lead to theft of frequent flier miles, to complete identity theft. Note that airlines have more data on you than even banks do (e.g., your passport number).
Here’s a real-life example: when one researcher turned to X with a fabricated complaint against Ryanair, the first response he received was from a fake account, which immediately started asking him for PII:

Search ad poisoning
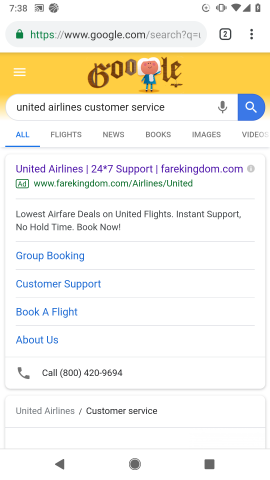
Another threat vector for airline customer service impersonation is search ads – an attack similar to SEO poisoning. Bad actors invest in search engine ads that include fake call center numbers where the crooks, pretending to be airline representatives, extract as much PII as possible from their victims. A victim of such fraud detailed their story in a post on X:
“My Delta flight got canceled from JFK. The customer service line was huge, so I Googled a Delta JFK phone number. The number was 1888-571-4869. Thinking I had reached Delta, I started telling them about getting me on a new flight.”
He did not fall for the scam but quickly discovered that the number he had dialed was part of a scamming network with similar numbers for American Airlines and Southwest.
Employee account phishing
Some ambitious scammers aim higher than airline passengers and target employees with access to the Global Distribution System (GDS). In these systems, they can book and issue tickets to resell before the compromised account is locked.
In one prominent example of an employee phishing attack on airline companies, a single fraudster spear-phished employees in several different airlines and travel companies in the U.S. with fake emails requesting their GDS login credentials. This attack resulted in over 2 million dollars of flight tickets fraudulently booked using stolen credentials.
While this hacker was eventually caught when trying to board an international flight, other, more sophisticated cybercrime groups continue to target airline employees to gain access to booking, ticketing, and CMS systems in order to steal payment details and PII.
Fake reservation sites
Website impersonation scams plague many industries, including banking, e-commerce, shipping, and travel. Bad actors can create nearly perfect copies of airline online assets with AI tools. These bogus websites and apps often offer significant discounts on travel packages and flights and even send a confirmation email to the victims. None of these are delivered to the victims, while their stolen credit card data and other PII are sold on the darknet.
One of the many recent examples is Air Vietnam, whose website was spoofed under a lookalike domain (https://vietnam-airline\.org). The stolen passport and credit card details of the defrauded victims quickly showed up for sale on the so-called underground market.
Loyalty mile theft and ATO
Airlines’ frequent fliers and loyalty programs are an incredibly lucrative attack target in online airline fraud. Like the case of fraudulent reservation sites, they require the scammers to create a clone of the airline website.
Unlike credit card loyalty programs, frequent flier miles are poorly secured and much easier to abuse. When ordering with loyalty miles, the user (or thief) may not even be directed to a payment gateway for user authentication or risk assessment while booking accommodations and flights. For scammers, this is a highly sought-after resource for reselling on the underground market, where stolen loyalty miles and compromised accounts are constantly offered for sale.
The untold costs of airline website impersonation fraud
Airlines’ direct losses to impersonation fraud schemes are already sky-high, affecting operational costs and therefore profit. This industry is also pressured by a growing number of challenges, including unstable equipment and fuel costs, high competition, and increasing legal and regulatory pressure to comply with customer data protection standards.
Until now, regulators have focused mainly on protecting banks and other financial institutions – and their customers – from brand abuse and website impersonation. Considering the overall impact of airline fraud on the economy and the volume of airline fraud worldwide, experts expect to see similar legislation in the airline industry.
Another critical concern rarely addressed is the relationship between international crime and airline fraud. Since airline fraud is often used by professional criminals to travel around the world and commit serious crimes (like human trafficking, terrorism, and transporting dangerous drugs), airlines that don’t want to find themselves part of an investigation should seek out ways to protect themselves and their clients.
Speaking of clients, it’s needless to say that brand impersonation fraud is devastating to the reputation of any brand or business. Meanwhile, 1 in 3 people in the US admit they were scammed when booking or taking trips, and over a third (34%) of those lost over $1,000.
The sky’s the limit: Effectively solving impersonation fraud in airlines’ websites
Airlines are slow to move at the moment, even though they were leaders in digital sales innovation in the 1990s. However, cybercriminals excel at hit-and-run attacks that are over before anyone at the airline is even aware of them. SOC and fraud teams are then left scrambling for information with little to no visibility into the scope of a website impersonation attack.
While many e-commerce sectors are plagued by impersonation fraud, airlines seem to be one of the slowest to respond and transform their cybersecurity strategies to take a proactive approach. So, what should airlines invest in to prevent fraud and protect their customers and their bottom lines?
Enhance authentication and authorization protocols
Multi-factor authentication (MFA), risk-based authentication and authorization, and additional authentication solutions make it much harder for cybercrooks to take over accounts. They are vital in curbing loyalty mile fraud and credential compromise.
In addition, you should inform and educate your employees and customers on what to do and who to contact when they receive an MFA-related email or SMS from a suspicious entity after attempting to log in. But that’s not the only thing your customers and employees need to know.
Educate customers and employees
Most people are familiar with phishing and airline scams, but bad actors are constantly evolving their scams. Simply posting an alert on the official airline’s social media channels about an ongoing fraud campaign is not enough.
Memcyco’s real-time website impersonation protection suite can embed a warning alert in spoofed websites, warning your customers when they attempt to click on them.
Develop a fraud incident response management plan
How you respond to detected impersonation fraud against your clients is critical. You need to invest in a well-planned incident response and management process, with a team of first responders trained to manage complex fraud and cybersecurity incidents and a set of tools to enable swift response. It also helps to partner with global airline fraud prevention organizations, governmental agencies, and partner airlines.
Employ advanced impersonation detection, prevention, and response tools
You can employ AI-powered real-time solutions to safeguard your brand and digital assets against spoofing and impersonation. Memcyco addresses website impersonation attacks in real-time before a single customer has fallen for the scam, by detecting fake websites and alerting you on the spot. Your customers also receive alerts if they visit a fake website, so they are protected, and prevented from submitting any sensitive information. If you don’t want any potential customer friction related to such alerts, Memcyco also allows you to replace PII by decoy data “behind the scenes” and unbeknownst to the potential victim, before it reaches the bad actor.
If and when customer information is in danger of being compromised through a spoofed website, Memcyco’s solution automatically provides fraud and infosec teams with granular visibility into every fraud event, victim, and action. Book a demo to learn more.



















