CISOs have a lot on their hands and won’t get a break anytime soon. By 2025, 45% of organizations will be impacted in some way by cyber threats. The good news is that in an ever-evolving threat landscape, threat modeling can help CISOs understand how attackers might target their systems and the potential vulnerabilities they might exploit. This makes it easier to prioritize efforts and resources when creating a more secure system. Let’s have a closer look at how threat modeling works.
What is threat modeling?
6 steps in the threat modeling process
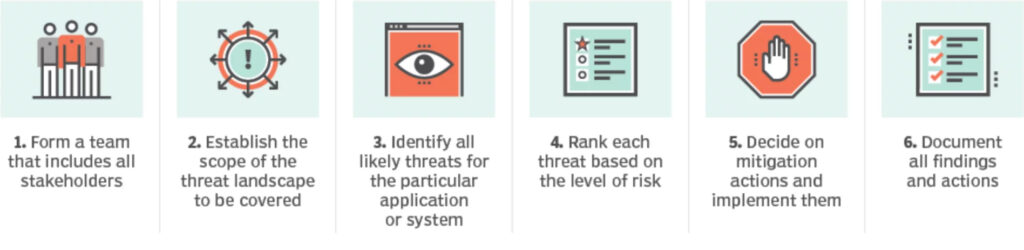
Threat modeling typically involves identifying assets, such as sensitive data or critical systems, and then considering potential threats against these assets to prevent them from succeeding. This can be done through a variety of approaches.
For example, asset-centric threat modeling focuses on identifying all assets that must be protected within a system, while attacker-centric threat modeling identifies the most likely methods attackers use to compromise a system so security teams can prevent attacks. On the other hand, software-centric threat modeling focuses on analyzing the software itself, looking for potential security flaws and vulnerabilities to patch before problems arise.
Regardless of the approach, the desired outcome of a successful threat modeling process is a set of secure design patterns used to build or modify a system to minimize potential vulnerabilities.
How to design secure patterns
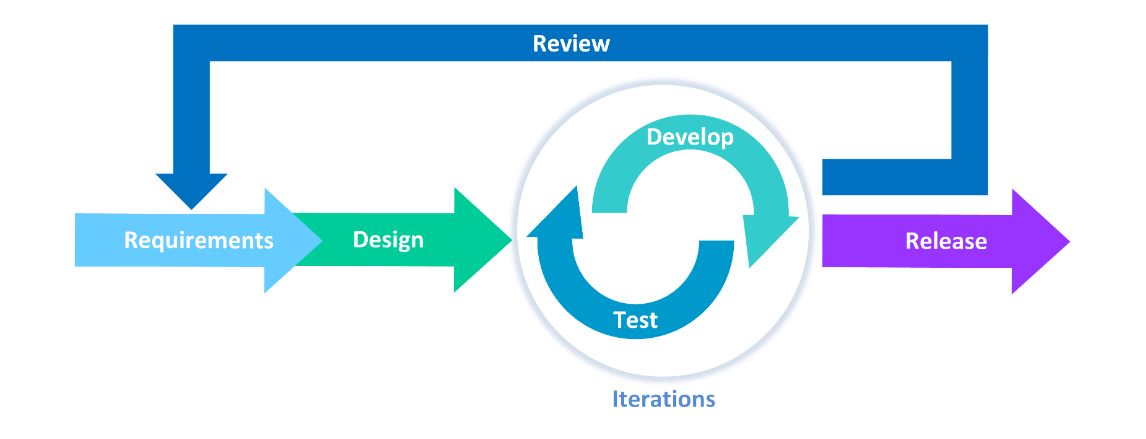
Designing secure patterns means that security is considered from the start of development rather than being tacked on at the end. Threat modeling is crucial for this security-by-design approach to DevOps because it identifies potential threats and vulnerabilities early in development, resulting in more resilient products.
You can also think of a security pattern as a reusable guide to a common security problem. In this sense, security patterns differ from security frameworks–the latter is a more comprehensive set of tools, protocols, and best practices for creating a secure system.
Threat modeling can be relevant in various use cases when designing secure patterns. For example, if a team is developing an outdated application, they may use threat modeling to identify an encryption algorithm used to store user passwords that is no longer secure. Or, when developing a new payment processing system, threat modeling can help identify potential vulnerabilities such as unauthorized access to payment data. The team can then create a security pattern featuring multi-factor authentication and encryption to mitigate these risks.
7 threat modeling examples for secure design patterns
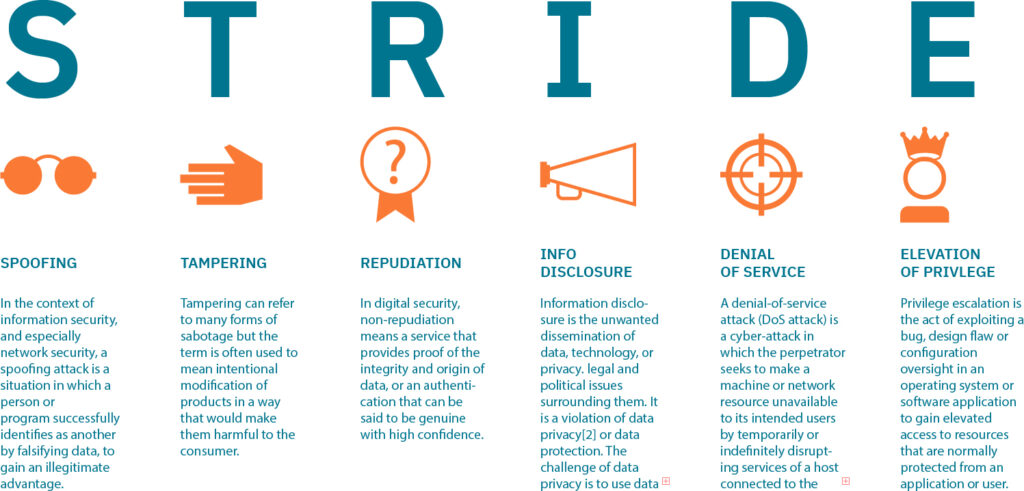
STRIDE is an acronym for the six types of threats it identifies: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. This threat modeling methodology is easy to understand (therefore helpful for development-focused organizations new to threat modeling) and provides a structured approach to identifying threats and vulnerabilities in a software system.
Aside from identifying potential security weaknesses, STRIDE suggests mitigation strategies to help organizations proactively secure their systems against those risks. This way, CISOs and security teams can better understand their systems’ security posture and make informed decisions about prioritizing their security efforts and resources.
2. Trike Methodology
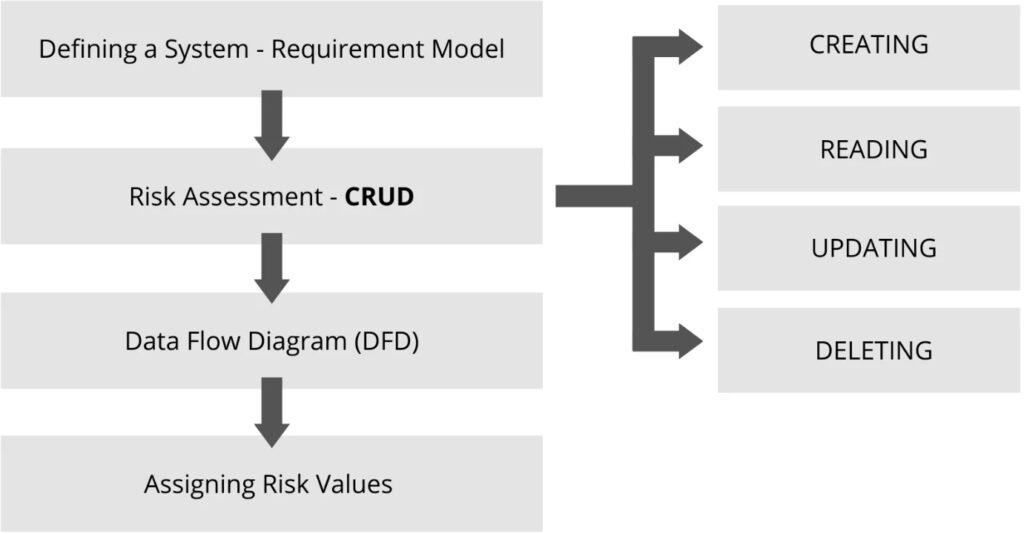
Trike was primarily designed for organizations that must comply with security audit requirements and regulations, such as the PCI DSS or HIPAA, because it provides a clear and systematic way to document the results of the threat modeling process.
Trike is a comprehensive and methodical approach to threat modeling. It emphasizes the importance of stakeholder engagement and communication throughout the threat modeling process to identify and address all potential vulnerabilities. This methodology is based on core concepts and principles, including using threat trees, attack trees, and risk matrices to analyze and prioritize potential threats. Despite using various techniques and tools to identify and analyze risks, Trike is repeatable and scalable, making it suitable for teams of all sizes.
3. Visual, Agile, and Simple Threat (VAST)
Vast Threat Modeling Methodology
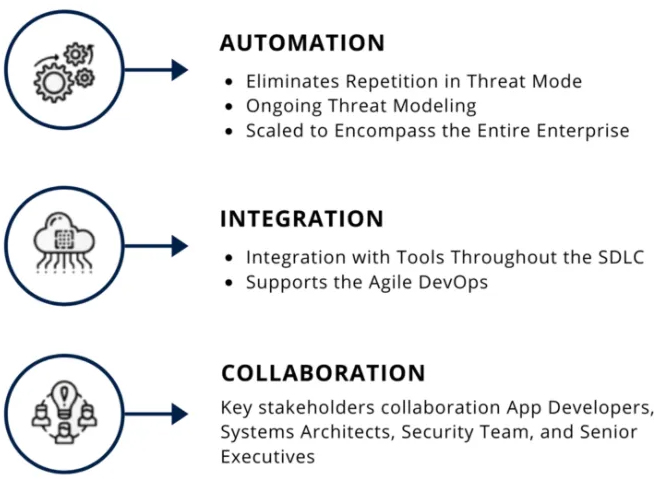
Visual, Agile, and Simple Threat (VAST) creates a streamlined and efficient approach to identifying and mitigating potential security risks. It emphasizes the use of diagrams, flowcharts, and other visual representations to simplify the process of identifying and understanding potential vulnerabilities. This facilitates communication and collaboration across different teams, making this threat modeling methodology particularly useful for large organizations.
At the same time, VAST focuses on agility, making it optimal for organizations that need flexibility to adapt to changing circumstances. This approach allows organizations to respond quickly to emerging security threats or changing business requirements by skipping the time-consuming process of redesigning their entire threat model.
4. Attack trees
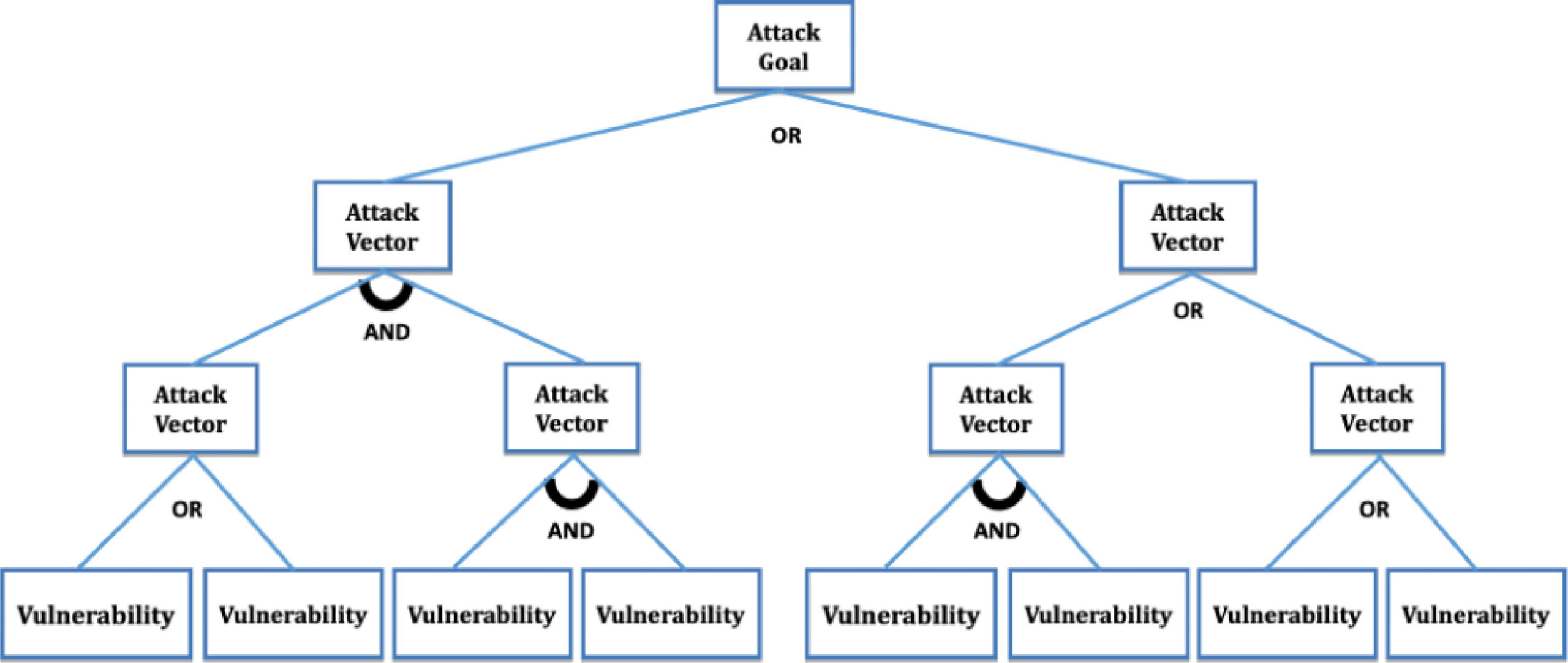
An evaluation of potential attack surfaces based on attack tree modeling and risk matrix applied to self-sovereign identity. Source
Attack trees are graphical and analytical conceptual diagrams. They are particularly useful for threat modeling in complex systems with multiple components and attack vectors, as it allows organizations to break down the system’s attack surface into smaller, more manageable components to assess potential risks.
Attack trees are great support for an attacker-centric approach to threat modeling. They can be used to evaluate the effectiveness of existing security controls and identify gaps or weaknesses in the security posture, highlighting vectors where attacks are highly likely to happen.
5. Common Vulnerability Scoring System (CVSS)
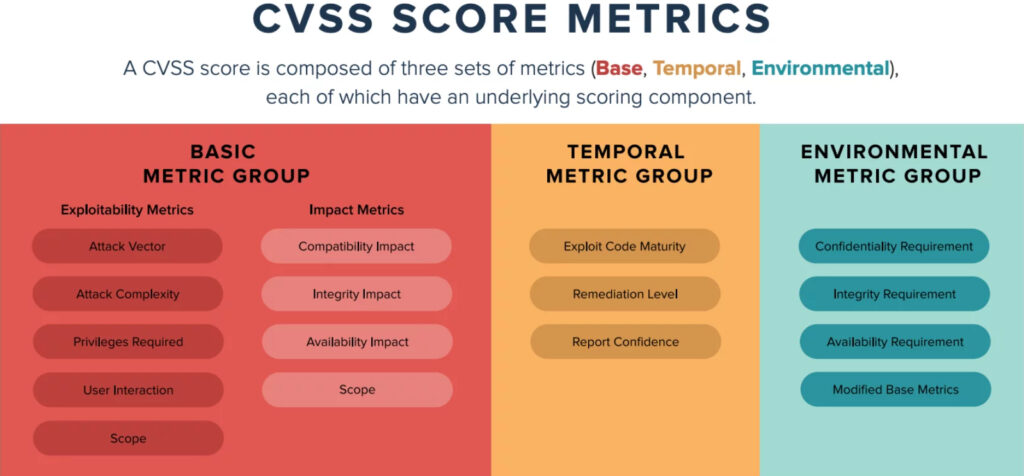
The Common Vulnerability Scoring System (CVSS) is an open framework currently at its third major version (v3.1) and maintained by the Forum of Incident Response and Security Teams. It provides a common language and a standardized approach to scoring the risk and likelihood of vulnerabilities, helping organizations to prioritize their security efforts.
The CVSS metrics fall under three main groups: base, temporal, and environmental. The base score represents the vulnerability’s inherent risk, while the temporal score considers factors that may change over time, such as the availability of patches or the development of exploitable code. The environmental score considers factors specific to an organization’s environment, such as the availability of compensating controls or the value of vulnerable assets.
6. Process for Attack Simulation and Threat Analysis (PASTA)
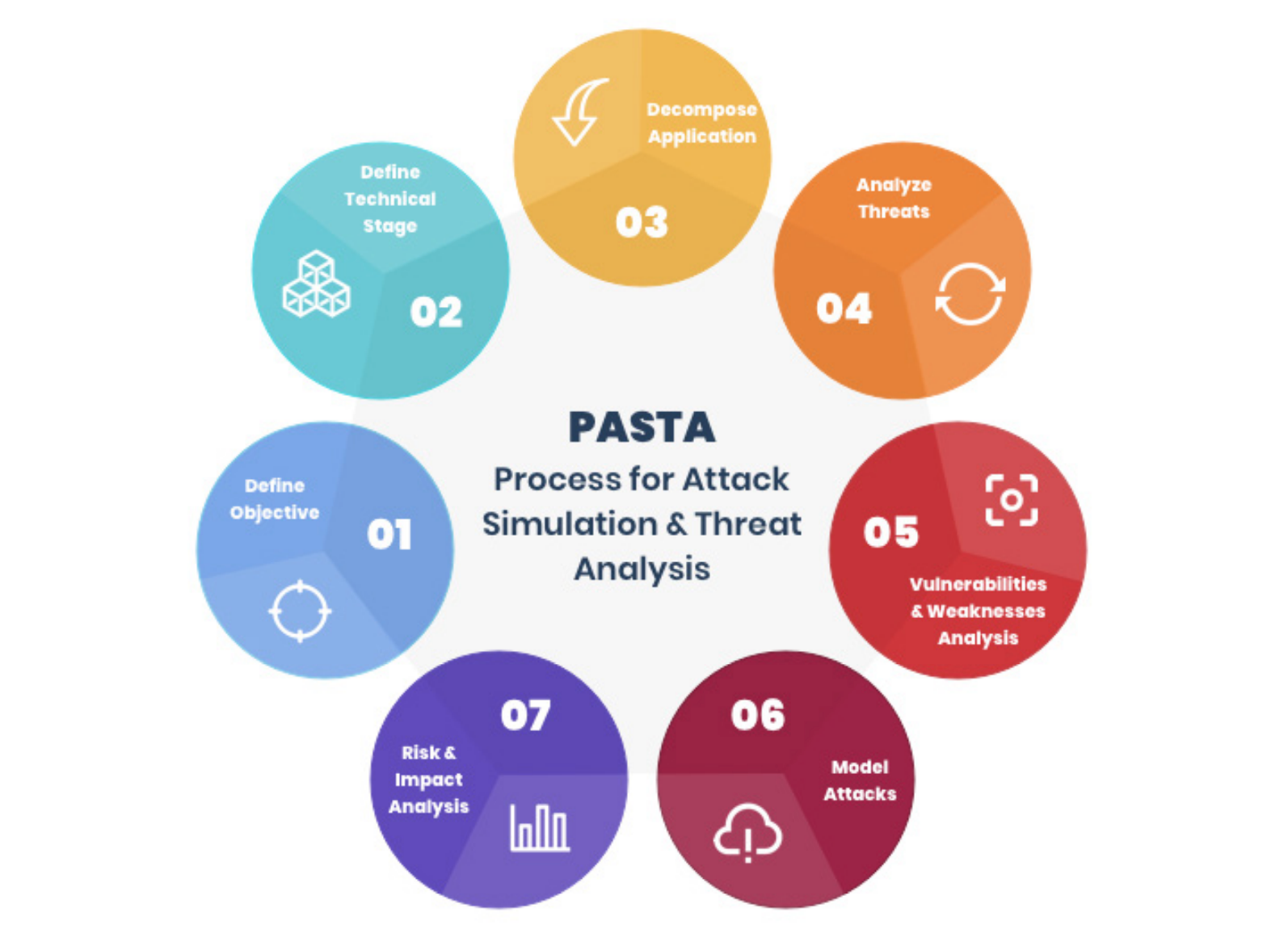
The Process for Attack Simulation and Threat Analysis (PASTA) takes a risk-centric approach to threat modeling. It is a comprehensive framework that provides a structured way of aligning business strategies with product security. PASTA provides a step-by-step process to inject risk analysis and context into an organization’s security strategy. It can be tailored to fit your organization’s needs because it is based on the idea that it is necessary to understand business priorities and risk appetite when designing security measures.
The approach emphasizes collaboration and team communication, making it ideal for organizations of all sizes. PASTA helps stakeholders to acknowledge shared security concerns, focus on the probability of each attack, and create appropriate countermeasures.
7. NIST
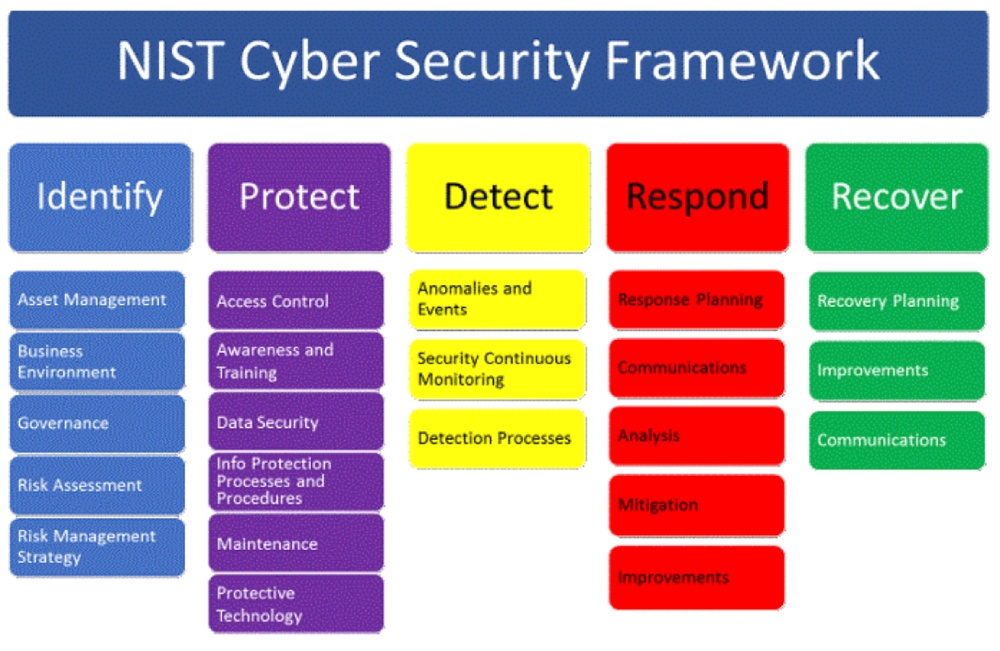
IN 2016, The National Institute of Standards and Technology (NIST) published a guide to data-centric systems threat modeling (referenced SP 800-154)–a risk assessment methodology that models aspects of the attack and defense sides for selected data within a system.
In 2021, NIST gave prominence to threat modeling by ranking it first among other recommended minimums for verification of code by developers. This is impactful because the Institute’s recommendations typically become part of government procurement. “Threat modeling can identify design-level security issues and help focus verification,” explains NIST of the recommendation. NIST’s guidelines are regularly updated, ensuring they remain relevant and effective in an ever-changing threat landscape.
Are you considering every point of impact?
By using threat modeling to support a security-by-design approach, organizations can create more robust and secure systems, which will ultimately help protect sensitive data and reduce the risk of attacks. As we’ve seen, the market has invested much effort into developing tools and methodologies to support end-users within a corporate environment.
At Memcyco, we believe the next generation of security solutions should look beyond the corporate perimeter to protect customers, not just employees, from cyber risks. That’s why we developed PoSA, covering every point of impact between organizations and their customers to proactively prevent cyber crime. Learn more here.



















