Estimating the potential impact of a successful cyber attack may seem impossible, especially given the rapid expansion of organizations’ digital footprint (and, consequently, their attack surface).
One example are attacks which pertain to the contact points between businesses and clients, such as websites and mobile apps. In particular, these assets can be cloned and used for phishing attacks. Armed with GenAI tools and commercialized on-demand fraud kits, bad actors are getting better at launching these scams. And an organization needs to be able to assess the potential risk brought about by such attacks.
So – how do you measure this risk, and that of other attacks? What tools should you use for cyber risk assessment?
What is a Cyber Risk Assessment, and Why is it Important?
A cyber risk assessment is the systematic process of identifying, analyzing, and prioritizing an organization’s risks to its security and operations. These risks can arise from how information systems and assets are used within the organization, or from the broader ecosystem in which the company operates. Some popular cyber risk assessment frameworks include NIST SP 800-53 and the ISO 27001:2013 standard.
Cyber risk assessments help communicate cyber risk to stakeholders inside and outside the organization, enabling them to make informed decisions about resource allocation. In addition, they support your risk management strategy, compliance audit readiness, and incident response planning. Ultimately, they help you improve your security posture, meet regulatory requirements, and avoid financial or reputational damage.
Key Types of Risk Assessments and the Tools that Help
Cyber risk assessments typically address various risks relevant to the organization, as well as other risk types, such as human cyber risk and geopolitical cyber risk. No single tool can cover every potential risk.
The tools used for cyber risk assessment can be split into a handful of categories according to different criteria. With many cyber security vendors aiming to deliver risk assessments as part of a cyber risk monitoring and prevention service platform, some solutions overlap in their coverage and feature offerings. So, what types of cyber risks should you assess, and what tools can you employ to streamline and automate this process?
Identity-Based Risk Assessment Tools
Identity-based risk assessment, also known as Digital Identity Risk Assessment (DIRA) by NIST, is a process in which cyber risk to an organization is measured from an identity-centric perspective. It accounts for human and machine identities interacting with organizational information systems.
This assessment typically entails identifying and characterizing users, transaction information, and the roles and permissions of each active account within a specific application. Then, you can identify the threats, estimate their impacts, and actively monitor for fraud.
The tools used to perform identity-based risk assessments vary greatly, depending on the type of business they aim to serve. While some tools and services aim to assess the risks associated with corporate identities, others help fight online brand impersonation and account fraud by actively monitoring and analyzing user interactions to determine a risk score and profile.
Here are two examples of identity-based risk assessment tools:
1. Suridata
Suridata focuses on discovering and protecting SaaS identities throughout the enterprise. It scans your entire system for SaaS vulnerabilities, helping your risk and SOC teams to have a holistic view of Shadow SaaS and misconfiguration vulnerabilities across their apps. It also offers automated vulnerability mitigation and real-time alerts, enabling SOC teams to resolve any security issue promptly. Suridata’s focus on SaaS environment cyber risk also makes it a good fit for vulnerability and compliance assessment categories.
Customer Review
“One of the things we liked most about Suridata was its ease of deployment. It had API integrations for many common business apps and easy-to-follow documentation for each one. Setup rarely took more than 5-10 minutes per app.”
2. Memcyco
Memcyco is an operational cybersecurity tool that provides real-time detection, protection, and response features to disarm website impersonation attacks. One of Memcyco’s key capabilities is feeding risk engines with data about impersonation attacks, attackers, and individual victims. This enables your organization to understand your identity-based threat surface and detect fraudulent activity in real-time.
Customer Review
“We are very satisfied with MEMCYCO and thoroughly recommend it. It has finally provided us with a solution to fill a significant gap in our cybersecurity needs. Our students and professors can now browse, upload, and share on our sites with complete assurance that they are in their desired place on the web.”
Vulnerability Assessment Tools
Vulnerability assessments are systematic reviews of weaknesses in information systems. They evaluate the system and assign risk values to known vulnerabilities. This evaluation enables fraud and risk teams to prioritize their tasks better and address the most dangerous vulnerabilities first.
A vulnerability assessment can detect risks leading to code injection attacks, privilege escalation, or ransomware attacks. Traditionally, these assessments addressed the application, the host, the network, and the data as separate assets. Today, with more organizations going cloud-native, they must also include cloud risk.
One example of an open-source tool that does this well is Trivy.
3. Jit with Trivy
Trivy is a comprehensive and versatile application and infrastructure security scanner. Aqua Security’s free software can scan file systems, repositories, container images, and virtual machines for known vulnerabilities (CVEs), IaC misconfigurations, sensitive information and code secrets, and invalid software licenses.
To streamline the management of Trivy’s scans within your CI/CD pipeline, you can use Jit with Trivy. Jit orchestrates powerful security tools like Trivy, helping you manage security testing in a single developer-first environment. If you consider all the features offered by the platform, Jit can also be categorized as a code-based risk assessment tool.
Customer Review
“Jit’s blend of automated security scans, gamified team monitoring, and the flexibility to integrate tailored security tools has seamlessly woven security into our development lifecycle.”
Code-Based Risk Assessment Tools
One of the main challenges of security teams and developers today is prioritizing what to fix first. Code-based risk assessment tools are a subset of vulnerability assessment tools. They can contextualize vulnerabilities in application security against potential business impact. They can also help determine the likelihood of exploitability of each vulnerability very early in the software development process, ensuring prompt mitigation.
4. Spectral
Spectral has an AI-powered scanning engine with over 2000 detectors to uncover blindspots in your code. It protects against secrets sprawl, exposed API keys, and security misconfigurations, helping developers understand the risks associated with their code. This visibility, in turn, enables security teams to perform thorough code risk assessments and fix vulnerabilities before deployment. The features of the platform as a whole also make it a vulnerability risk assessment tool and (depending on which detectors you use) a compliance risk assessment tool.
Customer Review
“We’ve solved the issue of having zero visibility into our ADO environment with SpectralOps. It integrates easily into ADO, allowing us to track previously unknown exposures.”
Endpoint Risk Assessment Tools
Endpoint devices are multiplying. Endpoint security risk assessments, which fit within the vulnerability assessment category, are vital in helping identify and prioritize the dangers that threaten the growing number of endpoint devices.
Two prominent endpoint risk assessment providers that take a different approach to assessing endpoint risk are Watchguard and Bitdefender.
5. BitDefender
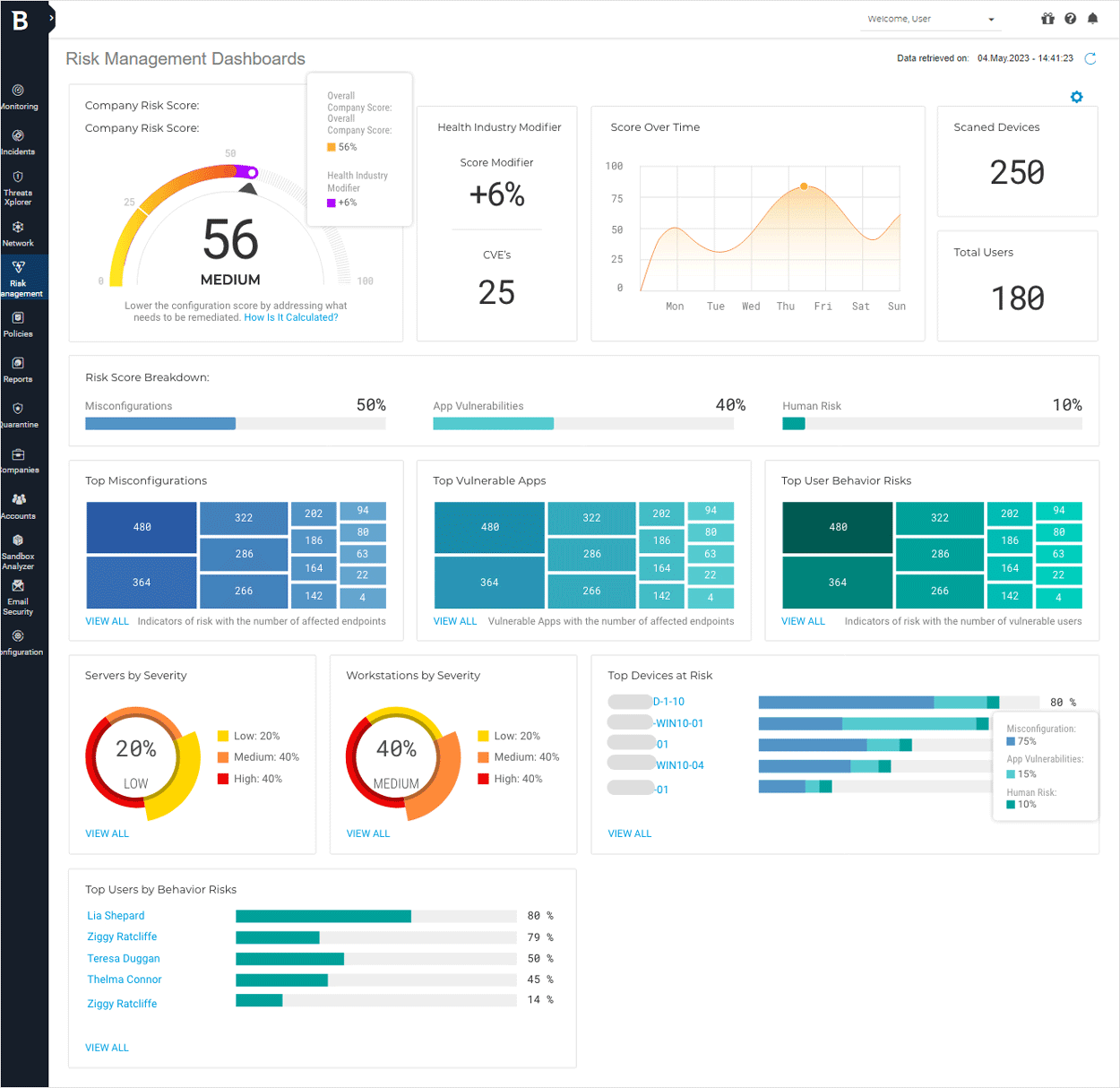
A feature in its extensive cybersecurity product offering, BitDefender’s Endpoint Risk Analytics (ERA) is an agent-based solution that helps identify, assess, and remediate endpoint security risks. With a centralized management platform, GravityZoneControl Center, BitDefender enables businesses to run scheduled risk assessments with policies, view insights, and automatically mitigate endpoint vulnerabilities.
Customer Review
“Since signing up for Bitdefender Mobile Security, I know my devices are completely protected. They give you more control over the tools and features that most security apps don’t offer.”
6. WatchGuard
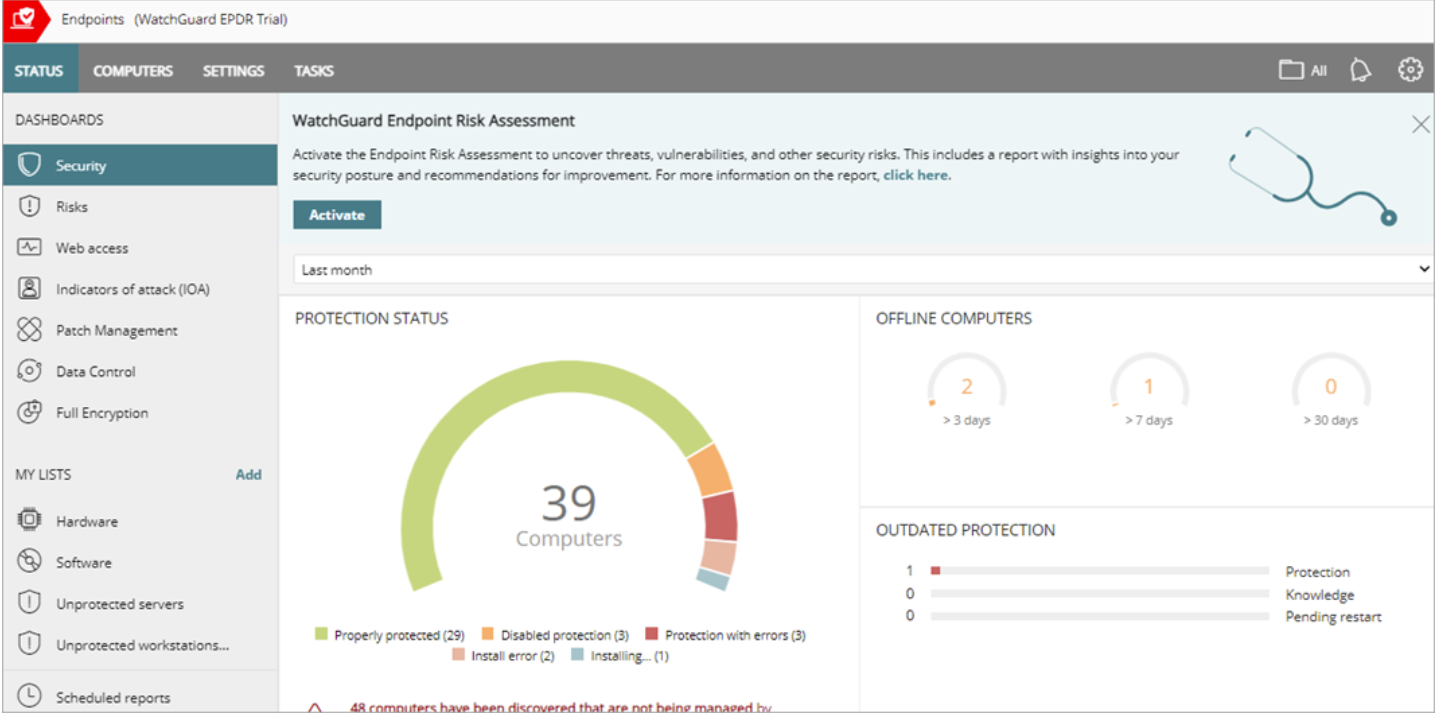
WatchGuard targets managed security service providers (MSSPs), helping them improve their cybersecurity offerings. It enables them to assess the risk introduced by the endpoint devices used by their managed accounts.
Customer Review
“I’ve been using WatchGuard Network Security solutions for our organization’s cybersecurity needs, and I’m thoroughly impressed with their features and usability.”
Supply Chain Risk Assessment Tools
A supply chain risk assessment quantifies the cyber risk associated with integrating with third-party service providers and code components (like libraries and packages). These tools assess risks in access controls, data governance, and incident history, among others. They analyze existing and upcoming vendors based on pre-defined criteria and the organization’s priorities.
7. BitSight
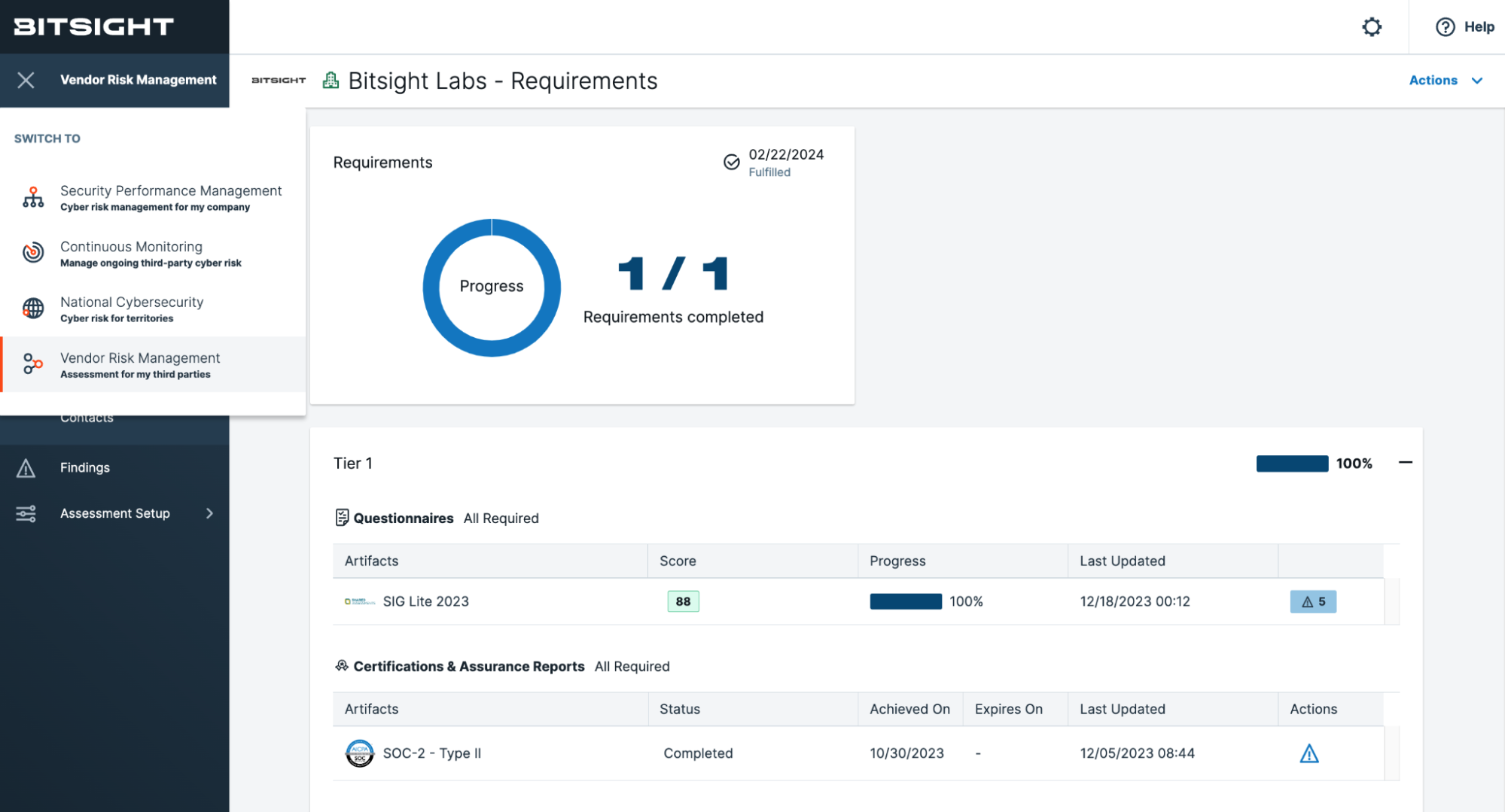
Bitsight offers a data-driven and dynamic measurement of an organization’s cybersecurity performance based on the widely adopted Bitsight Security Ratings. The tool derives the ratings from verifiable feeds and benchmarks in vendor-related risk categories such as open ports, spam propagation, and patching cadence.
Customer Review
“When I first started doing security assessments on third parties, it would take several hours to do the initial research. BitSight summarizes my initial work into an overall risk score.”
Data Risk Assessment Tools
A data risk assessment is a process in which potential risks to sensitive data assets are identified and categorized, with particular attention to where assets are stored and who has access to them. A data risk assessment tool aims to quantify these risks and the potential impact of sensitive data being compromised, stolen, or lost.
8. IBM Security Guardium Data Risk Manager
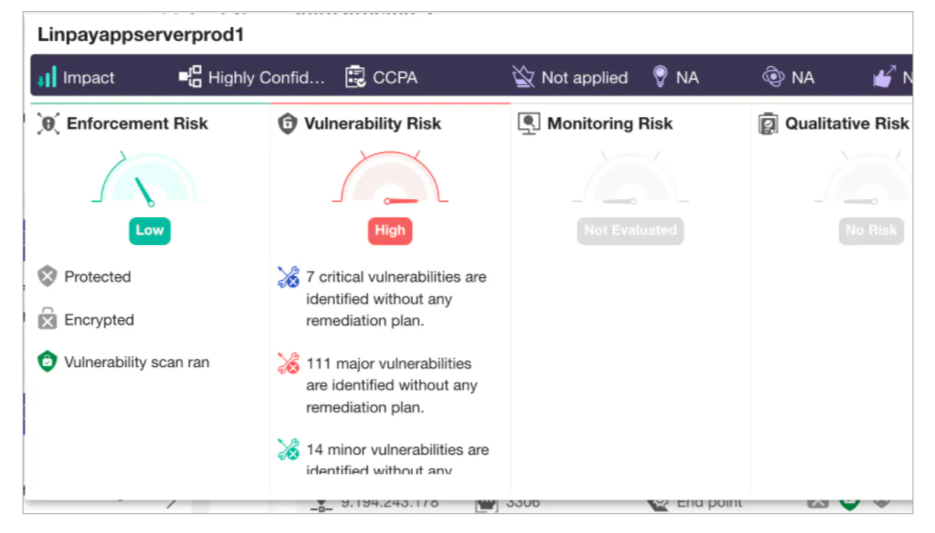
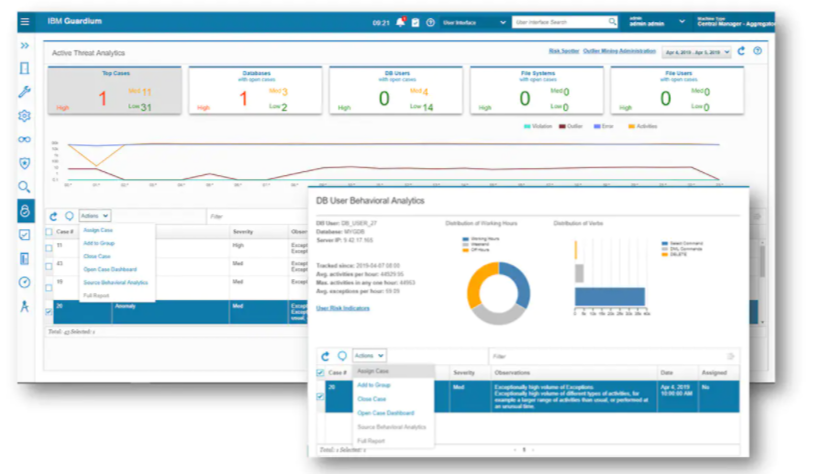
One of the oldest computing brands, IBM offers a unified dashboard for IBM Guardium, Symantec DLP, and IBM Information Governance Catalog. This dashboard provides workflows enabling the discovery, classification, and reporting of sensitive data and associated risks across the organization. Aimed at large enterprises, IBM’s Security Guardium Data Risk Manager correlates vulnerabilities, threats, controls, and organizational attributes to the monetary value of every sensitive data asset to calculate a risk score.
Since this tool does much more than assess the risk associated with data assets, IBM Security Guardium also fits the vulnerability and compliance risk assessment categories.
Customer Review
“Guardium is a complex tool that requires thoughtful planning and strong execution. That said, it is very effective and comprehensive! We implemented IBM’s Guardium appliances. We performed data discovery and classification, which allowed us to monitor database activity and perform vulnerability assessments against our most critical data assets.”
Compliance Risk Assessment Tools
Compliance standards and applicable laws ensure your business operates under data protection and cybersecurity standards. A compliance risk assessment is a comprehensive review of all relevant industry standards and regulations to which an organization may be subject. These include standards like GDPR, HIPAA, and PCI-DSS.
Compliance risk assessment tools help streamline and automate this process, quantifying the risks of compliance violations throughout the organization’s systems.
9. LogicGate
LogicGate’s Risk Cloud®’s Cyber Risk & Controls Compliance Solution helps organizations contextualize cyber threats to business impacts and express it in monetary terms. It specializes in compliance risk assessment and management. It enables you to align your audit assessments with common control frameworks like HIPAA, ISO 27000, NIST CSF, SOC 2®, FFIEC CAT, and PCI DSS.
Customer Review
“Brilliant—my experience so far has been a very positive one! As time passes, I am getting more involved in different areas of the system, both as a user and as a power user. I like the ease of use, the functionality, and the ability of the system. One thing I like most about Risk Cloud is the customer support from our TAM.”
10. MetricStream
MetricStream CyberGRC is a cyber governance, risk, and compliance (GRC) tool that can allow your teams to accelerate compliance risk assessments by offering pre-packaged support for industry frameworks such as ISO 27001, NIST, HIPAA, CSF, and NIST SP800-53. In addition, this tool enables autonomous testing and monitoring of cloud security controls to proactively identify risks and weaknesses in your organization’s cloud environment.
Customer Review
“MetricStream has a better UI, and the platform supports multiple small and large devices. The security provided by MetricStream is great, and it provides multiple user source configurations and user authentication and authorization from multiple protocols.”
AI-enabled Behavioral Risk Assessment with Memcyco
To gain a comprehensive understanding of prominent cyber threats and the weaknesses of your systems, you will require a set of tools to address the relevant attack vectors and risks unique to your organization.
When it comes to website impersonation risk, Memcyco’s AI-based solution provides real-time insights into identity-based risks, offering granular visibility into every attack, bad actor, and individual victim. Using nano defenders, Memcyco can instantly detect any attack originating from your website. Real-time alerts enable your team to proactively address attack attempts and prevent ATO fraud and other costly attacks.
Book a demo to discover how Memcyco’s user-first approach to identity risk management can help strengthen your cybersecurity posture.



















