Hackers don’t always need malware or harvested credentials to break into systems and accounts. Why bother with technical hacks when bad actors can trick people into getting what they want? From deepfake video calls impersonating friends or relatives to perfectly cloned login portals that steal credentials in real-time, social engineering scams are more convincing than ever.
In fact, social engineering now accounts for 70 to 90% of cyber attacks. These scams don’t just target individuals: companies face a rising wave of digital impersonation attacks and social engineering schemes designed to exploit employees.
Stopping today’s social engineering takes more than just training; you must deploy the right technologies and strategies to outsmart the psychology behind these scams.
Social Engineering Scams: What Are They and Where Are They Now?
Unlike traditional cyberattacks that rely on technical exploits, social engineering targets human psychology by using deception, urgency, and impersonation to help threat actors achieve goals. Whether a fake email from “your mom” requesting an urgent wire transfer or a deepfake voice call impersonating a close friend, these scams weaponize familiarity and authority to make their deception almost indistinguishable from legitimate communication.
Kevin Mitnick, one of the world’s most famous hackers, spawned social engineering tactics as far back as 1979. Mitnick hacked into the computer systems of Digital Equipment Corporation (DEC) by pretending to be a lead developer over the phone and saying he forgot his password. For a couple of decades after Mitnick kicked it off, social engineering mostly meant cold calls, fake ID badges, and email scams riddled with apparent typos.
Fast-forward to today, attackers have diversified their social engineering tactics. AI-generated deepfakes, perfectly written fake emails, and sophisticated multi-channel fraud schemes have made social engineering more advanced, scalable, and convincing than ever. The rise of automation and AI means fraudsters can generate highly personalized phishing messages at scale to target customers (and employees) with shocking accuracy.
The impact of social engineering scams extends beyond immediate financial loss. A successful attack can undermine customer trust, damage brand reputation, and expose businesses to fines. More importantly, recent regulations state that companies are responsible for protecting their users from deception. That could mean preventing customers from falling for fake websites or stopping employees from approving fraudulent wire transfers.

5 Types of Social Engineering Scams to Watch Out For
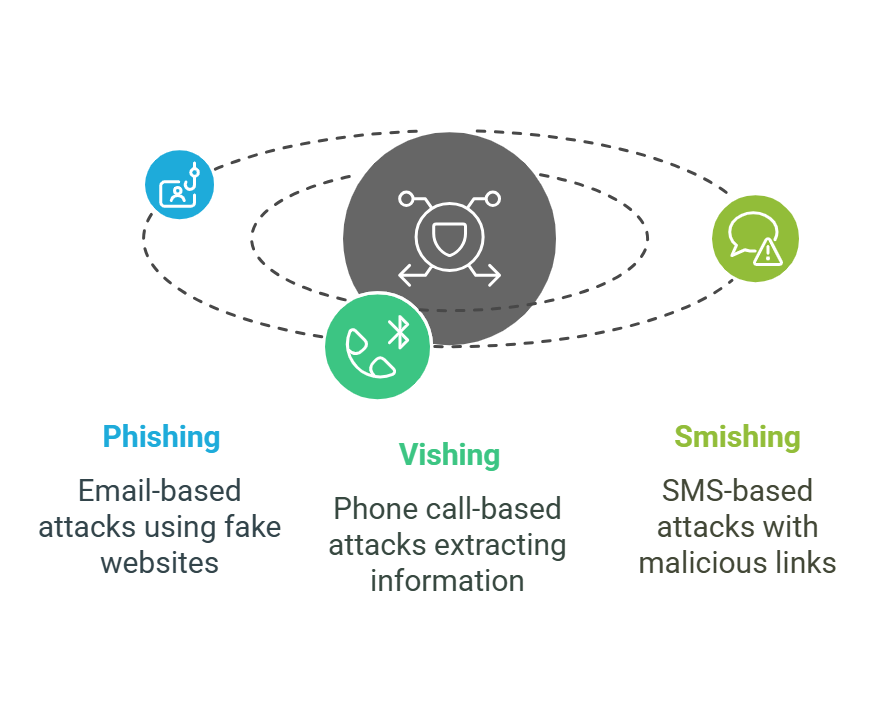
1. Phishing, Vishing, and Smishing
Phishing is the umbrella term for scams that trick users into revealing sensitive information by impersonating trusted entities. These attacks usually cast a wide net and try to dupe many people at once. While email phishing remains common, attackers also use voice phishing like Kevin Mitnick did (vishing) and SMS phishing (smishing) to increase their chances of success.
Attackers now impersonate trusted brands—banks, e-commerce sites, airlines, and delivery services—to steal credentials and financial data. They don’t stop at emails, either. They follow up with texts, WhatsApp messages, and even phone calls to make their scams seem more legitimate.
Smishing is one of the most effective tactics against customers. Attackers send fraudulent text messages pretending to be a customer’s bank, PayPal, or a delivery service like DHL, claiming their account has been locked, or a package requires urgent verification. The message contains a fake but convincing-looking login link, leading to a cloned website to steal banking credentials or credit card details.
2. Website Spoofing
Attackers know many people don’t inspect URLs before logging in or browsing your site. Website spoofing creates nearly identical copies of banking sites, corporate portals, and e-commerce platforms—right down to the logos, fonts, and login flows. Victims land on these spoofed sites through phishing emails, SMS scams, or even ads placed in search results. Tactics in these specific scams include:
- Attackers registering domains with subtle typos (e.g., amaz0n[.]com or microsoft-suport[.]net) and launch fake login pages.
- Intercepting login credentials in real-time from the fake site and relaying them to your actual website in an effort by fraudsters to bypass MFA.
- Fake checkout pages that steal credit card details.
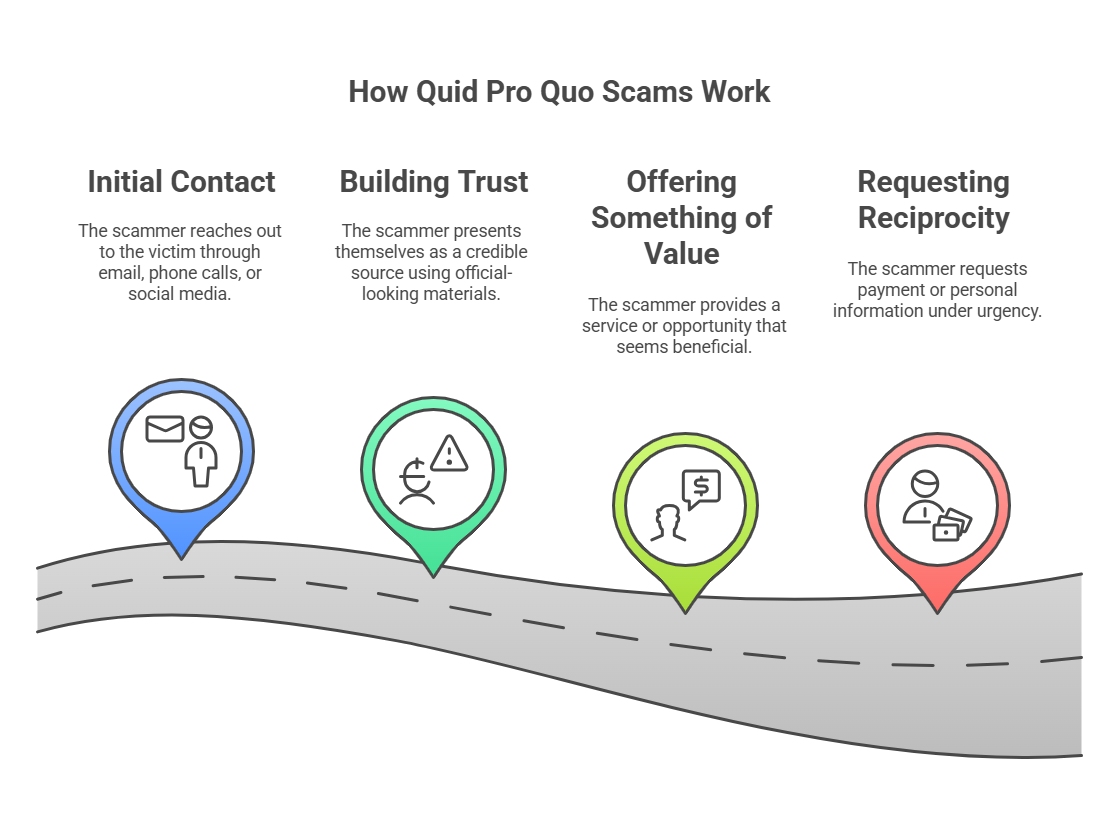
3. Quid Pro Quo Scams
Some social engineering scams work because victims think they’re getting something valuable in return. This is the essence of quid pro quo: attackers offer benefits like help, insider knowledge, and free software in exchange for access, security credentials, or sensitive data. At its core, quid pro quo scams tap into a social norm of reciprocity: when someone does something for us, we feel obligated to return the favor.
A clear example of incentive-based manipulation is attackers posing as suppliers or logistics partners, saying, “We’re offering priority shipping discounts to key partners this quarter. Just log in to confirm your eligibility.”
In financial businesses, an attacker might pose as a ‘research analyst’ offering exclusive financial insights or early investor reports in exchange for access to internal trading desks or deal-flow data. Employees who think they’re getting privileged information end up handing over credentials that attackers use for insider trading or corporate espionage.
4. Deepfake-Assisted Social Engineering
A few years ago, deepfakes were a novelty. Now, they’re powerful tools for fraudsters. Attackers use AI-generated voices and videos to impersonate relatives, employees, or vendors and trick people into making payments or approving access.
Exemplifying this risk was a news story from September 2024 in which two Houston women were scammed out of hundreds of dollars after receiving AI-generated deepfake videos of a friend. The videos showed the friend selling various items she owned, which her friends then sent money to the creator of the fake videos,
By replicating familiar faces and voices, deepfakes can more powerfully manipulate victims’ emotions. Because they can convincingly mimic trusted individuals, these scams erode the reliability of traditional verification methods.
5. Quishing (QR Code Phishing)
Fraudsters are taking phishing offline with social engineering schemes that exploit the growing popularity of QR codes. Known as ‘quishing,’ this technique replaces legitimate QR codes with malicious codes, tricking users into visiting fake sites
What’s so pernicious about quishing is its ability to circumvent user vigilance. For example, QR codes placed on parking meters, event posters, and restaurant tables won’t be subject to the same user suspicion as unsolicited emails and SMS messages containing links.
When scanned, the QR codes redirect victims to cloned websites that steal login credentials or credit card details. For instance, a fraudulent QR code on a payment terminal may lead users to a fake checkout page, where their financial data is captured and misused.
Defending against quishing requires tools to detect malicious sites in real-time and protect users from interacting with fraudulent pages. Organizations can safeguard their customers and maintain trust by disrupting these attacks at their source.
How to Protect Against Social Engineering Scams
Stopping social engineering requires far more than basic security awareness. Fraud teams, CISOs, SOC analysts, and your wider Cyber Fusion Centre need deeper visibility into user interactions, which users are visiting which fake sites, contextual authentication, and real-time fraud detection to halt threat actors.
1. Use AI to Detect Phishing Across Multiple Channels
Savvy social engineers impersonate executives, vendors, and IT support across channels. Traditional phishing filters struggle to keep up because scammers spin up new domains, tweak message content, and use AI-generated text to evade detection.
Leverage AI-powered detection that goes beyond basic signature-based filtering, analyzing writing patterns, domain metadata, and even the psychological triggers used in phishing attacks. For example, AI models might flag subtle inconsistencies in a phishing email pretending to be your bank or a trusted online retailer—like an unusual tone, missing contextual details, or an email header mismatch.
Deploying cross-channel phishing detection is essential so you can monitor email, smishing, fake social media profiles, and malicious messaging links to catch scams before employees or users fall for them.
2. Move Towards Adaptive Authentication
Adaptive authentication is a model that evaluates real-time risk signals instead of unquestioningly accepting a password + OTP combination. This model includes:
- Device fingerprinting to detect login attempts from unfamiliar hardware configurations;
- Session anomalies such as rapid credential stuffing attempts from the same device;
- Behavioral biometrics to flag inconsistencies in typing speed, mouse movements, and user habits.
For example, if an attacker logs in with valid credentials but suddenly changes account settings, adaptive authentication should detect the anomaly and require additional verification. Risk-based models dynamically escalate authentication challenges rather than relying on rigid MFA enforcement.
3. Apply Zero Trust Principles to Communications
Many social engineering scams don’t come from obvious external threats—they happen within the platforms and brands your customers trust. Attackers impersonate banks, e-commerce sites, and service providers to manipulate customers into sharing credentials, approving fraudulent transactions, or handing over sensitive information. That’s why a zero-trust architecture isn’t just about network security—it’s about verifying every high-risk action, no matter who requests it.
Zero trust enforces continuous verification, blocking fraudulent actions before they happen. Even if a user logs in successfully, risky actions (like adding new payment recipients or accessing critical data) trigger extra authentication checks.
4. Real-time Fraud Detection
Social engineers clone entire websites, intercept login attempts, and trick users into thinking they’re in the right place. If your security controls and tools aren’t detecting these threats in real-time, you’re giving fraudsters an open window.
Fraudsters commonly impersonate your brand to steal from your customers. Fake banking sites, cloned e-commerce checkout pages, and bogus airline ticketing platforms steal credentials and financial details from your users—these customer-facing incidents damage trust and reputation.
The ability to monitor for unauthorized clones of your login portals and brand pages is invaluable. Implement real-time fraud detection like Memcyco, which actively scans for spoofed websites, impersonation attempts, and unauthorized brand usage.
Effectively mitigating social engineering scams requires advanced tooling. Risk-based approaches, like adaptive authentication and zero-trust principles, ensure that sensitive actions are always verified, making it harder for attackers to gain unauthorized access to your systems. However, attackers can still clone your website and impersonate your brand, even without accessing your systems, so you need real-time fraud detection tools to identify these attempts.
How to Stop Social Engineering Attacks at the Source and Identify Scam Victims
Memcyco is the only solution in its class that ‘accompanies’ in real-time digital impersonation attacks that use social engineering, flagging each attack stage while deploying defensive and proactive measures. In this way, Memcyco enables enterprises to neutralize phishing-related scams at their source in ways other solutions can’t.
Even if fake sites go live, Memcyco’s real-time protection ensures that user credentials and credit card data are secured from the moment an attack is detected.
This capability uses overt and covert methods:
- Covert protection: Memcyco sends marked decoy data to bad actors. This traceable data renders stolen credentials useless while identifying attackers for immediate lockout.
- Overt protection [optional]: Red Alerts notify users of fake websites, warning them not to enter sensitive information. Simultaneously, the organization is alerted to the incident.
Memcyco customers also gain deep insights into attackers, the devices they use, and each individual victim; this intel can help you identify threats, disrupt fraud networks, and tighten security where it matters most. Agentless deployment means you can start protecting users immediately without complex integrations or delays. Book a product tour.



















