Fraud is built on deception, and third-party fraud is no exception. In this type of fraud, attackers use stolen or synthetic identities to impersonate legitimate customers and gain unauthorized access to accounts, services, or funds. By exploiting the trust between businesses and their customers, fraudsters bypass traditional security measures, making third-party fraud a growing threat in an era of automated attacks and large-scale data breaches.
42% of companies either don’t have a third-party risk management program or don’t include any form of risk scoring in their program. This visibility gap leaves businesses vulnerable, especially as sophisticated fraud rings and organized crime groups continue refining their tactics.
To effectively combat third-party fraud, companies need dedicated fraud prevention strategies that address the evolving nature of impersonation-based scams – starting with a deeper understanding of the threats and how to stop them.
Understanding Third-Party Fraud
Third-party fraud occurs when fraudsters exploit a person’s identity or credentials without their knowledge or consent, typically to gain unauthorized access to accounts, conduct financial fraud, or manipulate transactions. These attacks often bypass traditional fraud detection methods by operating outside the company’s security perimeter. They are complex because they work on both psychological and technical levels, exploiting human trust and security shortfalls.
Many third-party fraud scams operate outside the scope of traditional monitoring or enterprise fraud management solutions, which makes them even more challenging to detect and stop. Fraud teams often rely on transaction monitoring, login activity analysis, and standard fraud detection algorithms designed to flag anomalies within the company’s environment.
The problem is that third-party fraud often happens entirely outside of that environment. For example, fraudsters use fake websites or phishing attacks that steal credentials before a fraudulent login occurs.
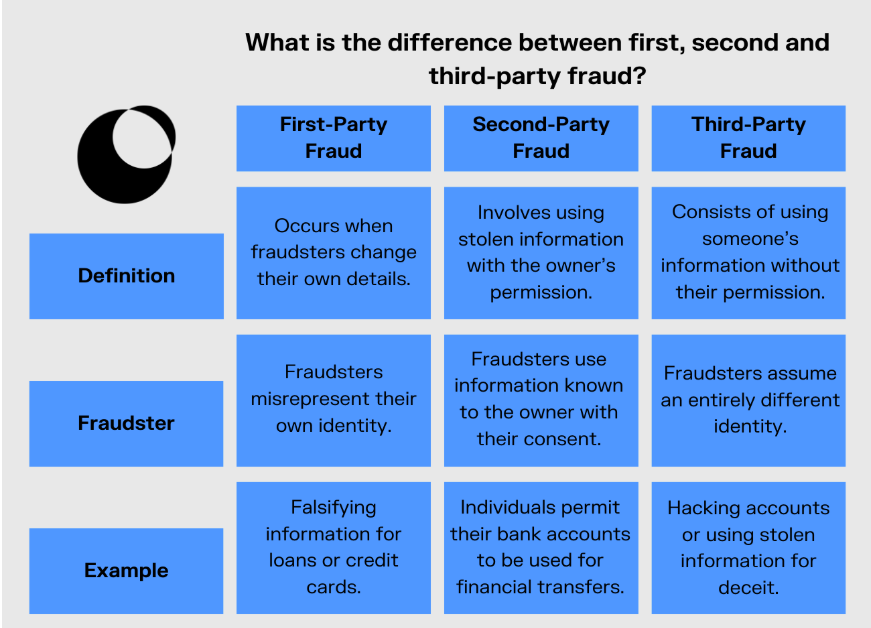
Third-Party vs First and Second-Party Fraud: Key Differences
The differences between these types of fraud come down to both knowledge and the perpetrator’s identity.
Perpetrator
- In first-party fraud, the perpetrator is a customer who knowingly misrepresents who they are or otherwise gives false info for financial gain. For example, someone applying for a credit card inflates their income to receive a higher credit limit than they would otherwise be granted.
- In second-party fraud, the perpetrator uses a customer’s identity or account to commit fraud with that customer’s permission. Money mules are a good example.
- In third-party fraud, fraudsters steal customer identities, credentials, or financial data through deception – often via phishing, impersonation, or fake sites – without the victim’s awareness. Unlike second-party fraud, where the victim knowingly participates, third-party fraud occurs entirely without their consent.
Knowledge
- The person committing first-party fraud knows what they are doing because they are trying to deceive others.
- The individual knows their details are being used in second-party fraud scams, but they allow it to happen, often under the guise of a reward but sometimes because of a threat. These scams disproportionately target those under 30 who might be more naive or in dire financial circumstances.
- Third-party fraudsters are the only ones “in the know” in these scams. The customer doesn’t know their info has been stolen and used often until it’s too late.
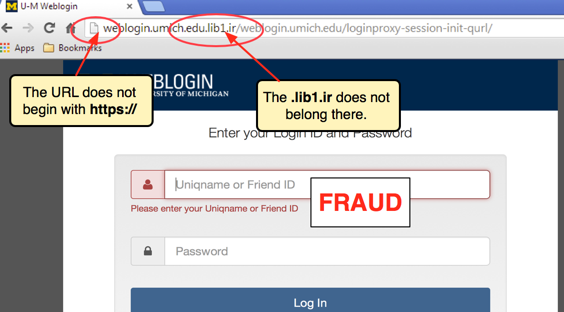
Third-party fraud is uniquely dangerous because of the high level of deception involved. Fraudsters often impersonate banks, government agencies, or well-known companies to gain access to victims’ personal and financial information.
They might create fake websites that look identical to those of your company, send phishing emails that mimic official communications, or pose as customer service agents to extract sensitive data directly from individuals. The sophisticated nature of these scams makes them highly effective and tricky to combat. In cases like website impersonation, fraud occurs entirely outside your company’s systems, meaning traditional fraud monitoring won’t catch it.
Common Examples of Third-Party Fraud and Its Prevention Methods
1. Account Takeover
Fraudsters use tactics like compromised credentials (billions of them circulating on the dark web), session hijacking, and social engineering to take over someone’s account and pose as that person. Once inside an account, they’ll typically transfer funds or make purchases.
Prevention Methods
- Consider moving beyond traditional passwords and MFA by adopting passwordless solutions that rely on digital certificates or biometric data. This reduces the risk of credential theft, a common ATO entry point. Although, it’s worth noting that passwordless solutions are not entirely foolproof.
- Implement real-time ATO detection that identifies compromised user credentials before login attempts occur. Solutions like Memcyco provide instant alerts when stolen credentials are used, replacing them with decoy data to disrupt attacks.
- Ensure customers know who to contact and what steps to take if they believe their account could be compromised or might soon be.
2. Invoicing fraud
Fraudulent invoicing is a type of third-party fraud in which scammers pose as your business and send fake invoices to unsuspecting customers. This kind of scam is more direct, as instead of getting customers to reveal credentials first, it tries to get the money straight away.
Scammers create invoices that closely resemble those from a legitimate business, with forged logos, fake contact details, and plausible charges. These invoices might claim to be for standard services or products or renewal fees.
Prevention Methods
- Provide customers specific details on how legitimate invoices are sent, what information they include, and who to contact for confirmation.
- Encourage customers to use service portals or direct contact channels to verify invoices before paying them.
- Ensure that all invoices clearly state the payment policies, including the exact names and bank account details to which legitimate payments should be sent.
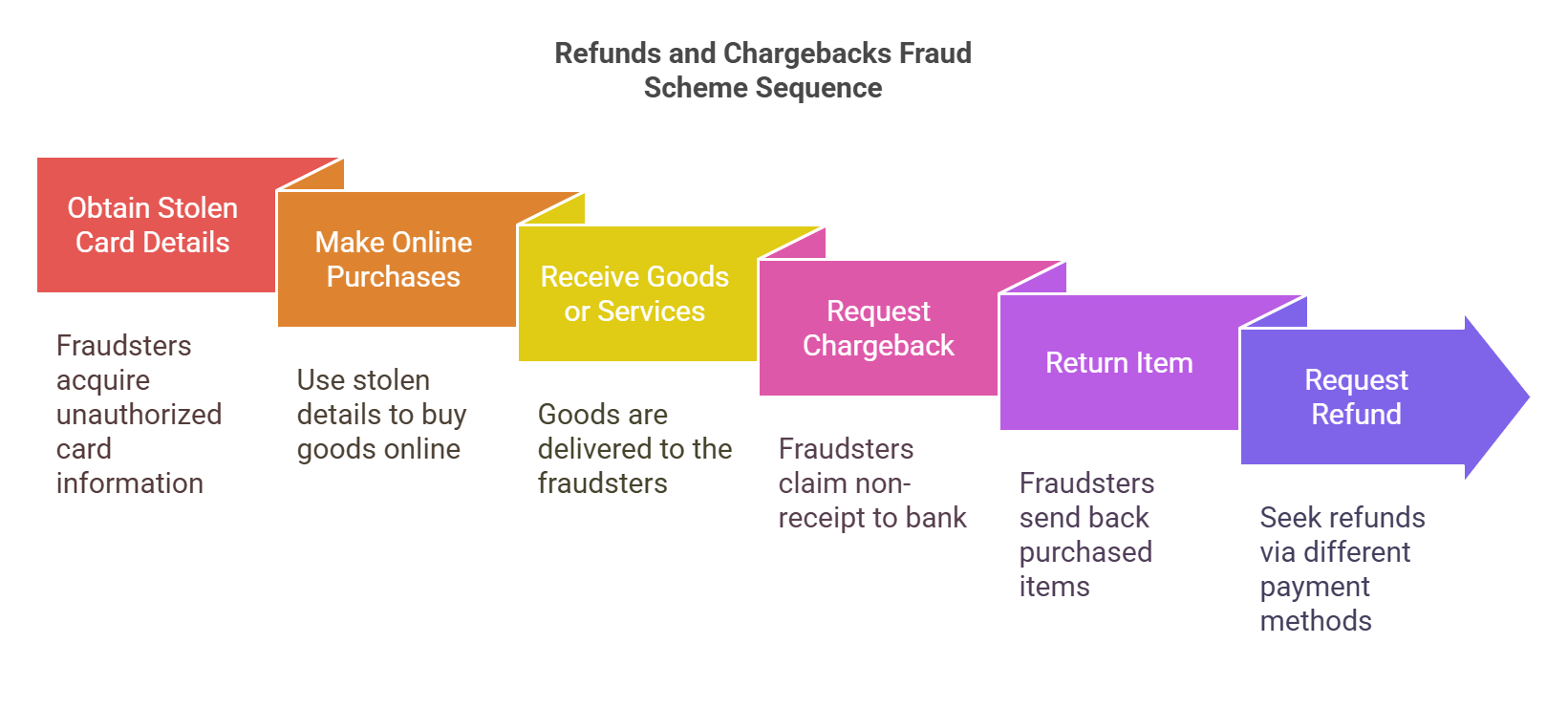
3. Refunds and Chargebacks
Armed with stolen credit card details, fraudsters make purchases online. After receiving the goods or services, they request a chargeback from the issuing bank, falsely claiming they never authorized the purchase or received the goods. Alternatively, they might return a purchased item and request refunds using a different payment method, such as another credit card or a bank account under their control.
Prevention Methods
- For physical goods, use reliable delivery services that provide detailed tracking information to dispute non-receipt claims.
- Look for systems where refunds must be processed through a dynamic payment link, which ensures that refunds are automatically rerouted to the original payment method.
- Develop or adopt fraud scoring models that quantify the risk associated with each transaction or refund request. These models can use various data points, such as customer purchase history, device ID, or location data, to score transactions according to their likelihood of being fraudulent.
4. Website Impersonation
Website impersonation happens when a third party creates a fake website that closely resembles your company’s site. This type of fraud deceives customers into believing they are interacting with a real company’s site. It leads them to input sensitive information, such as login credentials and credit card details, that the fraudsters can use.
The scammers clone your website’s design, including logo layout, and even use security certificates to make it appear authentic. They’ll lure customers to these fake sites using phishing or other forms of social engineering.
Prevention Methods
- Look for solutions that monitor the web for domain registrations and impersonated sites or portals that mimic your brand. Real-time detection is vital here because customers are at risk when sites go live.
- Encourage customers to manually type your website URL into their browsers instead of clicking on links from emails or other sources.
- Deploy real-time website cloning detection to identify and neutralize fake domains before they go live. Memcyco proactively detects impersonating sites, notifies organizations instantly, and provides customers with Red Alerts when they visit fraudulent pages. It goes one step further by providing bad actors with decoy data, so if customers are tricked into adding their details on this site, the data is automatically replaced with fake data that is useless to fraudsters.
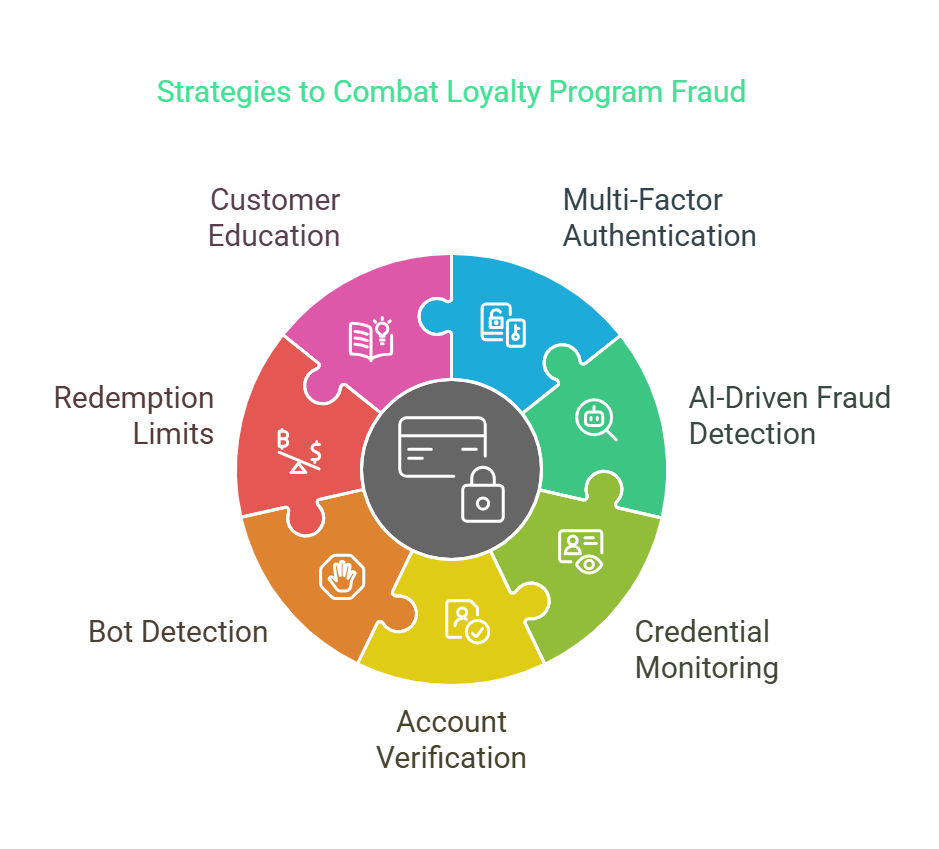
5. Loyalty Program Fraud
Loyalty program fraud involves unauthorized access to customer loyalty accounts to steal points or benefits, which fraudsters can use or sell on the black market. While the premise sounds similar to account takeover, access methods sometimes differ.
Many loyalty programs are interconnected with various partners, such as airlines, rental services, and retailers. Fraudsters often exploit weaker security in partner systems to access linked loyalty accounts without directly compromising the primary account credentials. Instead of directly hacking customer accounts, fraudsters could use social engineering to manipulate your customer service representatives into accessing and making changes to loyalty accounts. This method could involve pretexting as the customer or a partner company.
Prevention Methods
- Use IAM tools to detect unusual patterns within loyalty program activities, such as unexpected point redemptions or transfers, especially in large volumes.
- Introduce extra verification steps before approving high-value point redemptions.
- Encourage customers to treat these points as valuable assets and give tips for secure management and red flags for potential fraud.
Best Practices to Manage Third-Party Fraud
1. Deployment of Decoys to Gather Intelligence
Create decoy accounts and transactions within your system to attract and engage fraudsters. You can closely monitor these controlled environments to observe fraudster behaviors once inside and tactics for gaining access to the accounts. By understanding the tactics fraudsters use, you can preemptively adjust your security measures to block similar attempts in the future.
2. Interactive Customer Education
Develop interactive and engaging online education programs for customers that simulate third-party fraud scenarios they’re likely to encounter. This training could include gamified learning experiences that teach them to recognize phishing attempts and securely manage their personal information. By actively involving customers in the learning process, you can improve fraud awareness and reduce the chances of customers falling for these scams.
3. Geofencing
Use geofencing technology to set up virtual boundaries around digital assets. When a device attempts to access these assets outside the predetermined geographic area, additional authentication steps are triggered, or access is blocked.
Because fraudsters often try to access accounts from different parts of the world, this can prevent unauthorized access from atypical locations. Automate this process with cloud-based workflows so that suspicious login attempts trigger predefined security actions without requiring manual review.
Strengthen Your Defense Against Third-Party Fraud
Third-party fraud takes many forms, from fake invoices and account takeovers to deceptive websites. This kind of fraud can hit hard—not just your company’s finances and your customers’ wallets but also the trust you’ve built with them. Recognizing these risks is key to protecting your business. A strong prevention strategy needs good internal controls plus intelligent, real-time monitoring. Using up-to-date technology like Memcyco can make a big difference.
Memcyco is a leading provider of protection for real-time phishing and account takeover (ATO). It helps customers stop third-party fraud as it happens, to minimize damage. The agentless tool spots digital impersonation in real-time, giving you key information about the attack, attacker and each individual victim. It also notifies customers when they visit a fake version of your site, and comes with a decoy data feature to protect your customers’ sensitive info when they fall victim to these scams. Visit Memcyco today.




![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1-300x169.png)





![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)