In 2024’s State of Digital Impersonation Resilience report there was one key finding that neatly frames the digital impersonation fraud challenge. Of the businesses surveyed, 72% use a digital impersonation protection solution, but only 6% could confirm its efficacy. In other words, scam-targeted industries are investing in finding solutions, but those solutions aren’t delivering.
In 2025 Memcyco’s latest digital impersonation protection innovations aim to fill this clear capability gap. The goal? To equip scam-targeted enterprises with the ability to shield revenue, reputation and customer accounts in an era of AI-assisted scams.
This latest release broadens and optimizes our core offering, building on two flagship pillars; real-time visibility and real-time protection. First, let’s start with what sets Memcyo apart from incumbent solutions.
What Sets Memcyco’s Digital Impersonation Solution Apart
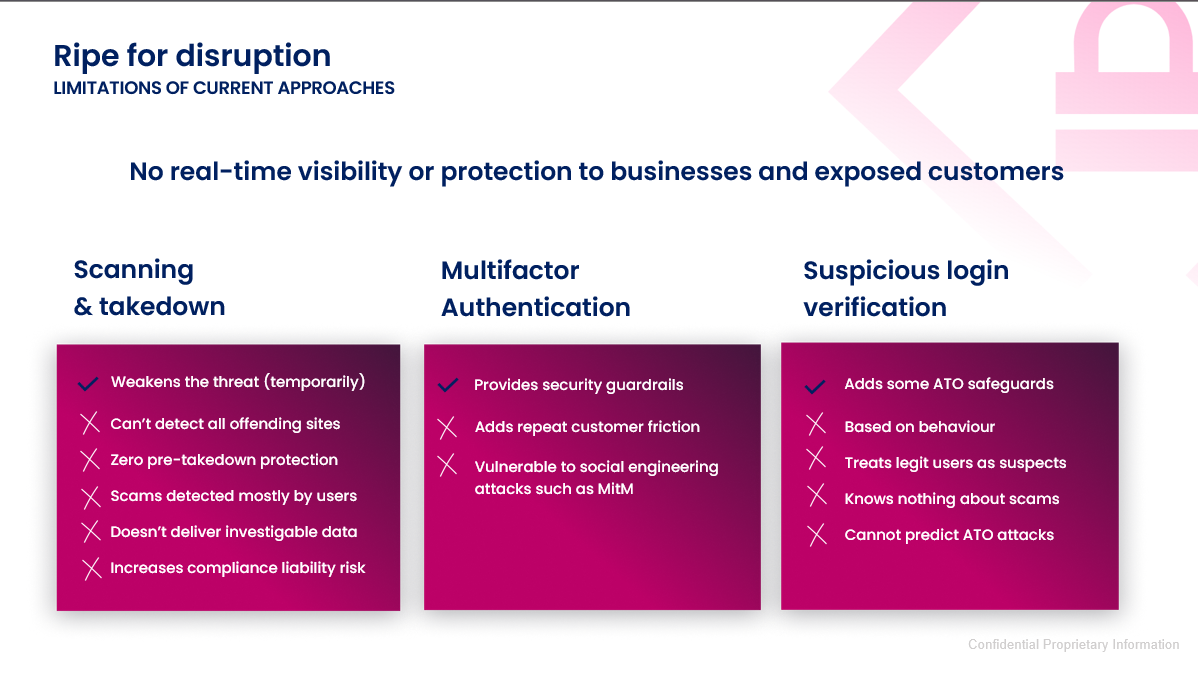
Traditional solutions like scanning and takedown typically arrive after the damage is done, detached from the attack lifecycle. At best, they identify impersonating sites and request their removal, often without knowing if the site was ever part of an attack.
MFA and suspicious login verification, though effective in providing some safeguards, increase user friction, lack attack insight and remain vulnerable to Man-in-the-Middle attacks.
Even modern solutions that use predictive analytics aren’t present when attacks start, and offer zero visibility of which customers fell victim.
Memcyco Matches the Attack Pace, Revealing Granular Detail in Real-time
Memcyco’s technology goes beyond these suboptimal approaches, ‘accompanying’ attacks in real-time, identifying each phase, each individual victim, the attack device and which ‘application’ (URL clusters) was targeted by digital impersonators.
In short, better identification of attack stages, victims and phishing targets enables greater visibility, protection and proactive disruption of attacks in real-time.
By adopting this insight-rich, proactive approach, Memcyco customers can reveal attacker intent, understand patterns, and counter digital impersonation attacks from their inception in ways no other solution offers.
Tracking Attack Incidents from Inception in Real Time
At the core of the latest release is the new Incidents capability that represents how, uniquely, Memcyco stays alongside the attack throughout its timeline. By tracking the attack moment by moment, Memcyco is able to deliver the real-time visibility, protection and disruption that define its solution coverage.
Memcyco ‘Incidents’ leverage advanced correlation to analyze events tied to attackers’ devices, phishing hosts, and historical data. In this way Memcyco unlocks an integrated view of suspicious events leading up to digital impersonation and phishing attacks, and as they unfold.
Rather than relying on sporadic data, security teams gain an itemized, chronological breakdown of incidents depicting attack lifecycles. This unified and summarized data / insights optimizes risk-based prioritization, facilitating swift action.
Key advantages
- Seamless detection of patterns across multiple incidents.
- Threat consolidation of all related activity into a single timeline, for optimized evaluation, understanding and response.
- Enhanced prioritization by dynamically assessing risks based on historical and real-time signals.
Protecting Enterprises and their Customers in Real-time
If and when scams go live, Memcyco’s real-time protection ensures credentials and payment data remain secure from the moment an attack is detected. This capability integrates both overt and covert mechanisms to protect customers and organizations:
- Covert protection: Memcyco sends marked decoy data to bad actors. This traceable data renders stolen credentials useless while identifying attackers for immediate lockout.
- Overt protection [optional]: Red Alerts notify users on fake websites, warning them not to enter sensitive information. Simultaneously, the organization is alerted to the incident.
Real-Time, Proactive Attack Disruption
In addition to Memcyco’s real-time detection and protection capabilities, Memcyco customers also gain the ability to proactively disrupt attacks.
Key proactive and disruptive measures include:
- Deception Campaigns: Confound attackers by feeding false data into their operations.
- Automated takedowns: Quickly remove phishing sites, minimizing the duration of threats.
- SEO poisoning defense: De-rank fake sites using organic search engine optimization and fake paid ads to outrank your legitimate site and steal customers.
By engaging with attacks proactively, Memcyco reduces their effectiveness and deters future attempts. For instance, businesses can mitigate damage from malicious campaigns while gathering critical data to prevent similar attacks.
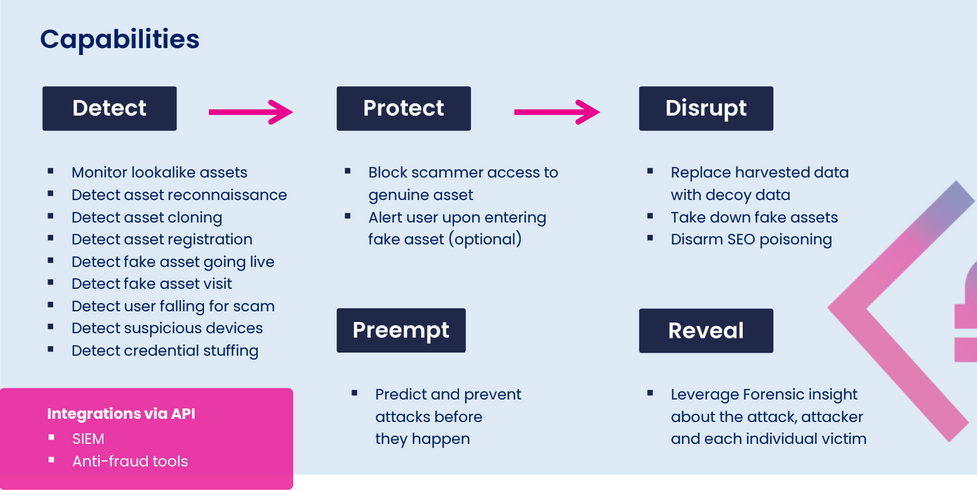
Memcyco’s Full Platform Capabilities
Following quick installation into the original website code, or via WAF, all of Memcyco’s real-time platform capabilities are activated, delivering value from day one without operational disruption.
‘Secret Sauce’ Technologies Driving Memcyco’s Next-Gen Solution
Underpinning Memcyco’s paradigm–shifting capabilities are two proprietary technologies that combine to confer the key advantages so far discussed.
What’s striking about these technologies is the level of protection offered to end users while remaining completely agentless. Following quick installation within the client website code, all capabilities become active with zero end-user apps or involvement. In this way, Memcyco’s next-gen solution generates immediate business value from day-one, with minimal setup time and investment.
‘Nano Defenders’
Easily embedded directly into the legitimate site, these lightweight, tamper-resistent code snippets monitor for suspicious activity such as cloning attempts, unauthorized code injections, or phishing setups. They also help actively disrupt impersonation attempts by detecting anomalies as soon as they occur, preventing attackers from replicating proprietary assets.
Advanced Device Analytics
Memcyco’s device analytics work in tandem with its Nano Defenders, leveraging advanced fingerprinting techniques to differentiate between legitimate users and malicious actors based on objectively unique device attributes. Unlike many device fingerprinting offerings prone to device ID overlaps, Memcyco maps unique user-device relationships, optimizing accuracy and efficacy in key areas.
Memcyco customers can expect a plethora of advantages from advanced device analytics – fewer false positives and negatives, frictionless account access for scammed customers during investigations, identification of non-authenticated users that aren’t logged in, and more.
Key Benefits: Protecting Revenue and Reputation
Memcyco’s real-time digital impersonation and phishing protection delivers measurable benefits:
- Reduce OPEX and by reducing the number and severity of incidents, the need for customer reimbursement, and customer attrition. Memcyco customers typically achieve x10 ROI from the first year.
- Boost operational efficiency by moving from a reactive, to proactive digital impersonation protection posture that leads to fewer successful digital impersonation attacks, requiring fewer and less complex investigations.
- Shield reputation and boost retention by avoiding scam-related PR meltdowns, strengthening digital trust and reducing brand shaming from scammed customers.
- Strengthen compliance posture by quickly and easily optimizing and evidencing your Internal Controls to auditors, while preparing for tightening regulation related to customer protection from scams.
Typical Savings to Expect

 What Memcyco Users Are Saying
What Memcyco Users Are Saying
Memcyco gives us pre-emptive foresight of ATOs in the making, with real-time visibility into phishing attacks and brand scams before they hit our customers.
Even if customers fall for scams, Memcyco dismantles card data and credential theft attempts at the moment of impact.
– Oren K, CEO
Mid-Market Organization (1,000-5,000 emp.)
Get a Product Tour: Discover Next-generation Digital Impersonation and Phishing Protection
During your product tour, you’ll tell us what solution, if any, you’re currently using to tackle digital impersonation fraud and what kind of attack scenarios you’re facing. We’ll explain in detail how Memcyco outperforms your current solution, and what outcomes to expect in those specific scenarios.
We can also discuss specific client case studies, and how Memcyco is helping enterprises in scam-prone industries save millions annually on digital impersonation and phishing scam expenses.
Check back for future content on how Memcyco’s real-time technology pre-empts and accurately predicts customer account takeovers (ATO).



















