When your customers entrust you with their information, they expect you to protect it from prying eyes. Customers, business partners, and employees are not the only ones with that expectation. Lawmakers and data protection agencies worldwide demand that businesses and organizations comply with regulations for protecting citizens’ data.
For CISOs, navigating the world of regulatory compliance can often be challenging as it entails understanding the ever-changing definitions and nuances of data privacy. Since most discussions around data privacy protection tend to be written in legalese rather than in common English, this process can get overwhelming.
To help out, this blog looks at two of the most commonly confused three-letter acronyms (TLAs) in the world of data privacy laws and regulations: Personally Identifiable Information (PII) and Protected Health Information (PHI). While both fall under personal information (PI), it’s important to understand their differences to protect customer data appropriately.
What is Personally Identifiable Information (PII)?

(Source: prweb)
As the name suggests, Personally Identifiable Information (PII) is any data that can directly point to a person’s identity.
Types of PII records
- Direct identifiers are unique and personal identifiers like passport or driver’s license numbers and biometric data.
- Indirect identifiers are sets of interconnected data fields that enable identification. For example, the combination of gender, ZIP code, and date of birth can allow you to pinpoint the identity of as many as 87% of U.S. citizens.
Sensitive vs. non-sensitive PII
Sensitive PII is information that directly identifies an individual and that, if compromised, could potentially cause significant harm. Examples of sensitive PII include direct identifiers such as government-issued identification numbers, biometric data (like fingerprints and DNA), and financial information (including bank account login details and credit card numbers). Non-sensitive PII are those you can scrape off public online databases, including email addresses, phone numbers, and demographic information.
That said, it is possible to weaponize sets on non-sensitive PII to gain access to sensitive PII by defrauding the intended target through brand impersonation. So if a malefactor has a list of names, emails, and mobile phone numbers of the clients of a specific company, they can easily target those clients across multiple channels while pretending to represent said company.
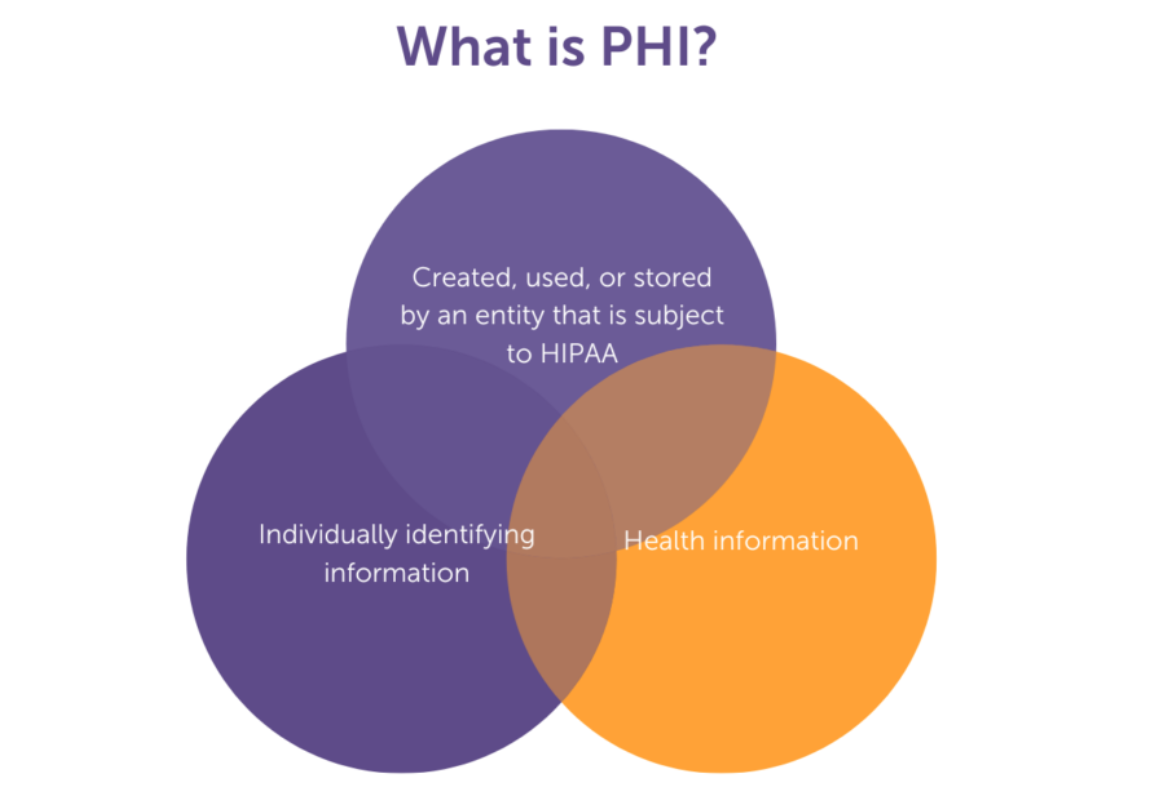
What is Protected Health Information (PHI)?
According to the Department of Health and Human Services, protected health information (PHI) is “a type of personally identifiable information that includes information about a person’s past, present, or future health status, payment for healthcare, or medical treatment.”
(Source: Health Information Management: How It Helps Prevent PII and PHI Breaches)
While PHI can be considered a subset of PII, data is considered protected health information (PHI) when regulated under the Health Insurance Portability and Accountability Act (HIPAA). This means it must be personally identifiable to the patient and used or disclosed to a covered entity during medical care.
HIPAA regulations specify 18 identifiers for what types of information are considered PHI:
- Patient names
- Geographical elements (such as a street address, city, county, or zip code)
- Dates related to the health or identity of individuals
- Telephone numbers
- Fax numbers
- Email addresses
- Social security numbers
- Medical record numbers
- Health insurance beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers
- Device attributes or serial numbers
- Digital identifiers, such as website URLs
- IP addresses
- Biometric elements (including finger, retinal, and voice prints)
- Full-face photographic images
- Other identifying numbers or codes
PHI records are much more valuable to identity thieves and blackmailers than PII records. While a Social Security number sells for about 1 USD and a valid credit card number can reach 100 USD, a full set of medical records can bank as much as 1,000 USD each into the pockets of malefactors who sell them on the Dark Web.
3 Key differences between PII and PHI
Depending on who you ask, there are many differences and similarities between PII and PHI. For CISOs, three key differences contextualize the legal-speak of laws and technical actions you should take:
1. Regulation & Government
The protection of PII and PHI is governed by different agencies in the US (as well as the EU and other regions).
PII is generally covered under laws like the General Data Protection Regulation (GDPR) in the European Union and the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada. PHI protection and security, conversely, is governed by the Health Insurance Portability and Accountability Act (HIPAA) in the United States.
It’s worth noting that regardless of where your business is based or where it operates, investing in protecting your clients’ data makes business sense, even if you’re not obligated by law to implement security measures or report major breaches.
2. Purpose
PII is often collected and used for various purposes. From marketing, customer service, personalization, optimization of data-driven services, and even fraud prevention. We share PII records with brands to get better service all the time.
PHI, by contrast, is primarily collected and used for physical and mental healthcare purposes. These include providing treatment, conducting medical research, and processing medical insurance claims.
3. Cost
As noted earlier, there are different price ranges for different types of personal information traded among cybercriminals, with PHI records ranking between 10 and 1000 times as much as credit card numbers or email credentials. The difference in cost also pertains to the price tag of an average data breach.
While the average cost of a data breach involving PII records in the US was $9.44M in 2022, the cost of breaches involving PHI in the healthcare sector averaged $10.10M. For CISOs, this means shifting operations toward regulatory compliance and employing tools that enable technical teams to easily apply regulatory policies across data storage, processing, and communication.
Protecting users from fraudulent PII and PHI disclosure
Overall, while PII and PHI may have some similarities, they are distinct types of potentially sensitive information that are governed by different regulations and employed for different purposes. Organizations must understand the differences before bridging the gap between privacy and security to comply with regulations.
When protecting PII and PHI records, the discussion often focuses on compliance with regulations and the safety of sensitive information on corporate cloud servers and inside applications. One angle rarely mentioned or discussed in the context of PII and PHI protection is customer fraud and brand impersonation.
Fraudulent methods to extract customer information exploit their trust in your brand–Trust that you’ve worked hard to earn. For example, phishing emails promising a lower premium on health insurance can lead to scammer sites where customers may enter their payment details, believing that they are entering them on the legitimate website of their insurer.
You can employ PoSA, our unique customer-centric brand protection platform to safeguard your customers from such brand impersonation fraud. With PoSA, you can actively prevent users from clicking through on fraudulent websites and display a unique and memorable code to assure them they’ve reached your genuine website and not a fraud.
Contact us now to learn more about how PoSA can help you protect your customers’ PII and PHI beyond the security envelope of your organization, enabling hassle-free logging and monitoring for website security and data compliance.






![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1-300x169.png)








![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)