Phishing Is Now a Real-world Threat:
Here’s How to Protect Customer Data
Imagine scanning a QR code to pay for parking or to buy a new jacket, only to realize you handed over credentials or card data to fraudsters.
Yes – phishing is now also an offline phenomena, expanding its reach into real-world spaces via QR codes. Known as ‘QRishing’, this increasingly common attack exploits growing reliance on QR codes in both online and everyday physical environments, exploiting users’ lack of vigilance.
Online, QR codes increasingly replace links in emails – even traditional banks are using QR codes to provide quick access to account information, allow users to pay bills or make mobile deposits.
The good news? Whether QRishing codes are digital or physical, there are now effective techniques and technologies for proactively pre-empting and preventing QRishing fraud.
If you’re already familiar with QRishing, and you’re here for solutions, feel free to skip the basics that follow.
What is QRishing?
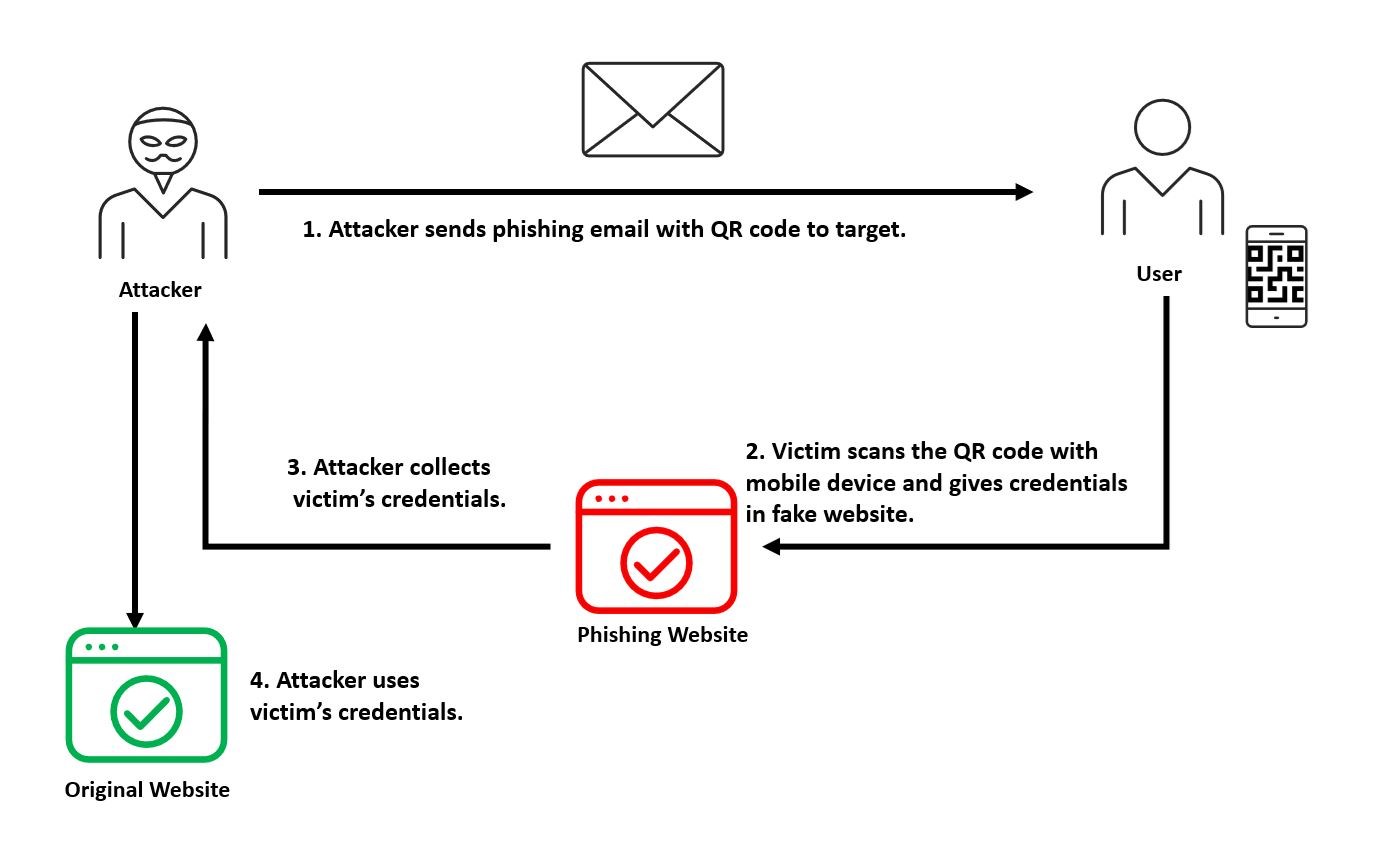
QRishing, a combination of “QR” (Quick Response) and “phishing,” refers to a type of cyberattack where malicious actors use QR codes to direct unsuspecting users to fraudulent websites designed to steal sensitive information, such as login credentials or financial data. Just as traditional phishing uses fake links in emails or messages, QRishing exploits the trust people place in QR codes to mask malicious URLs.
Attackers can place fake QR codes in both digital (emails, social media) and physical spaces (posters, restaurant tables, parking meters), tricking users into scanning them. Once scanned, the user is redirected to a website that looks legitimate but is actually a phishing site designed to capture their personal information or initiate unauthorized transactions.
The rise in QRishing is closely tied to the growing use of QR codes in everyday life, particularly in the wake of the COVID-19 pandemic, when contactless interactions became more common.
What makes QRishing so effective?
QRishing can happen digitally, via suspicious emails. However, unlike traditional phishing emails or text messages that can be flagged or filtered, QRishing attacks bypass common detection via physical placement in real-world environments. QR codes are often plastered on posters, tables, or notices, and their immediate function is to provide useful information, leading people to scan without hesitation.
QRishing works so effectively offline because:
- People trust QR codes implicitly, especially in familiar environments like restaurants, stores, or public services, where they’re accustomed to using them for contactless interactions. Who would suspect? Nobody, that’s who.
- QR codes obscure the destination URL, so users don’t see where they’re being directed until they actually arrive there after scanning. This provides an easy way for scammers to cloak malicious websites.
QRishing thrives in physical environments where malicious codes can be placed in spots where people wouldn’t normally question their legitimacy, such as on restaurant tables or official-looking posters.
Emerging QRishing Trends affecting Global Enterprises
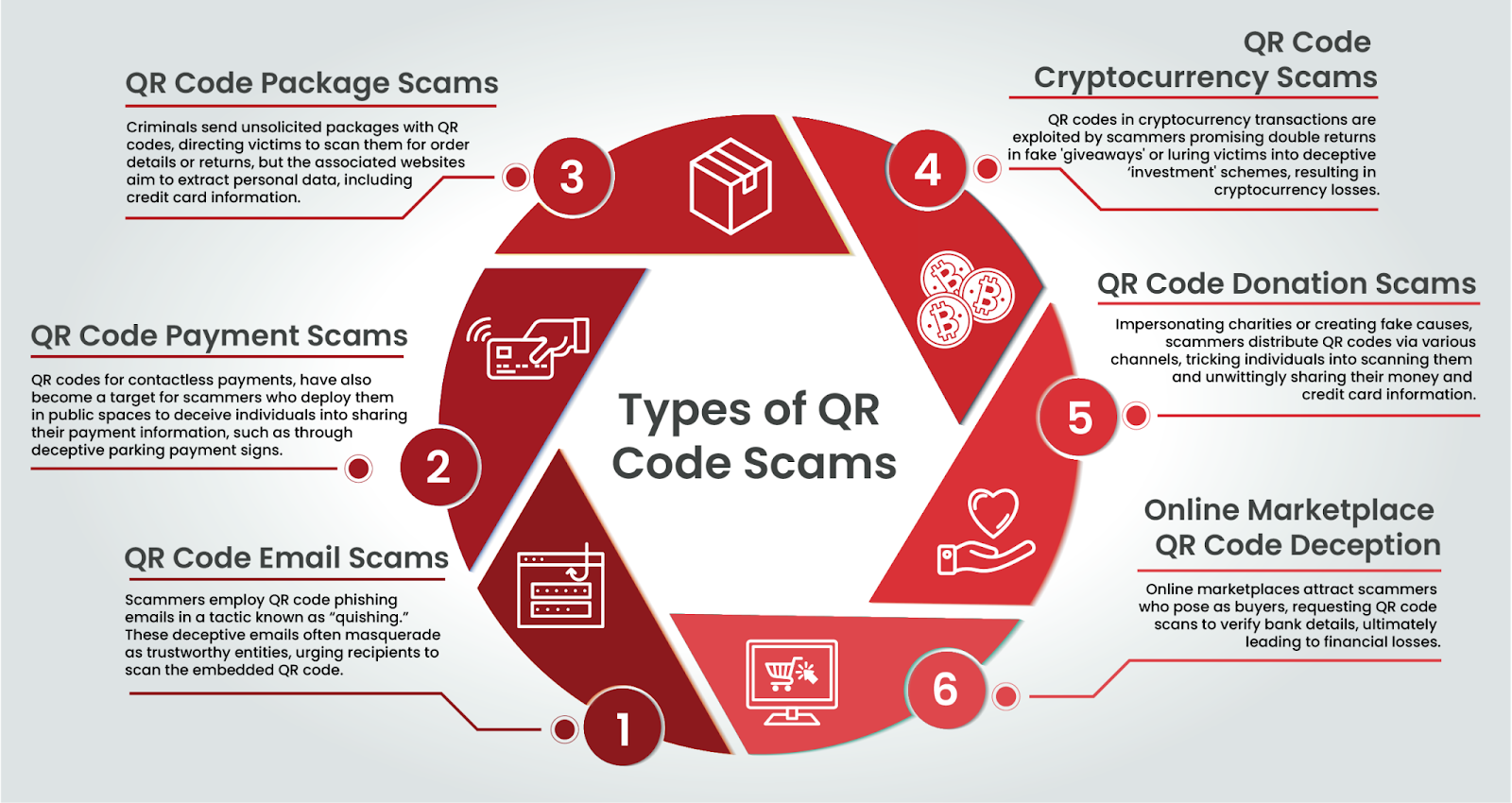
QRishing is one of the fastest-growing attack types. How fast, exactly? According to some reports, there was a 270% monthly increase in QRishing attacks from early 2023 through to May, with an increase of more than 2,400% from May through to August.
Here are a few reasons why:
Physical Placement of Malicious QR Codes
Attackers are taking advantage of high-traffic public spaces such as restaurants, malls, and airports to place fake QR codes in areas where people expect legitimate codes. Whether for menus, payment processing, or Wi-Fi access, these codes appear innocuous but lead to phishing sites or malware downloads.
QR Code Tampering in Trusted Environments
QR scams can also involve tampering with legitimate QR codes by covering them with counterfeit stickers or swapping them out altogether. This trend is especially dangerous in places where customers trust the environment—such as cafes or stores. Users often don’t question the authenticity of these codes, increasing the risk of falling victim to phishing attempts.
Offline Phishing Through Digital QR Code Campaigns
Some phishing campaigns now use QR codes as the delivery mechanism in email or print media (flyers, posters). These campaigns create a false sense of urgency, such as limited-time offers or exclusive promotions, driving users to scan the codes without properly vetting them. Once scanned, victims are directed to phishing sites where their personal data is stolen.
Industries at High Risk from QRishing
Several industries are particularly vulnerable to QRishing attacks because they frequently use QR codes for customer interactions:
- Retail and Hospitality: It’s common to see QR codes in stores offering discounts or coupons. Scammers can easily create fake QR codes advertising these promotions, only to redirect users to phishing sites designed to steal personal information or payment credentials. Similarly, counterfeit QR payment codes might be placed over legitimate ones in restaurants or retail outlets, tricking customers into sending money to the attackers.
- Public Services: QR codes used for parking meters, fines, or official government notices can be replaced with fraudulent ones. For instance, fake QR codes are sometimes placed on traffic fines or parking tickets, claiming to facilitate payment but instead leading users to phishing sites that harvest personal and banking information.
Financial Services: Banks and fintech companies increasingly use QR codes for mobile payments and authentication processes. In some cases, email phishing campaigns use QR codes to prompt users to reactivate multi-factor authentication (MFA) or verify account details, redirecting them to phishing pages that look like legitimate financial services.
3 Ways Memcyco Helps Enterprises Fight QRishing in Real Time Using AI
Before covering how Memcyco uses AI to prevent QRishing attacks, it’s worth touching on Memcyco’s flagship real-time capabilities that include both overt and covert protection methods.
Overt: fake site Red Alerts discourage customers from entering impersonating websites
Covert: If customers disregard the Red Alert, marked decoy data replaces פחcard data and credentials imputed by customers who visit impersonating. Think of it like traceable, marked money used to pay bank thieves, but with one key difference. If fraudsters try to use Memcyco’s decoy card data or credentials, they’ll lock themselves out.
Those are just two of Memyco’s protective mechanisms. Here’s how Memcyco uses AI to combat QRrishing.
1. Phishing Referral Detection Using AI
Memcyco’s AI-driven phishing referral detection can analyze the signals around website referrals, such as where the traffic is coming from and the behavior patterns of users arriving at these sites. When users are redirected after scanning a QR code, the AI system evaluates the site’s referral pathway, analyzing website reputation, user behavior, and contextual factors to determine if the destination is malicious.
- How this helps tackle QRishing: If a user scans a fraudulent QR code, Memcyco’s AI will analyze the referral behavior and immediately flag any suspicious redirect patterns, blocking the user from engaging with a phishing site.
2. ATO (Account Takeover) Prediction Using AI
Memcyco’s AI-models analyze user-device behavior, device DNA, and phishing campaign intelligence to predict account takeovers before they occur. It tracks unusual login patterns, device changes, and phishing indicators to stop attackers from exploiting data captured via QRishing attempts.
- How this helps tackle QRishing: If a QRishing victim unknowingly enters login credentials into a phishing site, Memcyco’s AI can flag anomalous bad actor login attempts, letting businesses trigger protective measures.
3. Phishing Site Detection via Semantic Analysis
Memcyco’s AI techniques also leverage semantic analysis to identify phishing sites that are set up as part of QRishing campaigns. By using large language models (LLMs) to evaluate the similarity between phishing sites and legitimate websites, the AI system can flag new phishing sites even before they become widespread. This is especially useful in QRishing, where attackers frequently create clone websites that resemble legitimate services.
- How this helps tackle QRishing: When a user scans a QR code leading to a cloned phishing site, This method allows Memcyco to flag phishing sites, even if they aren’t yet in threat databases, providing an additional layer of security against evolving threats.
Discover Why Global Enterprises Replace their Current Digital Impersonation Protection Solution with Memcyco
Schedule a demo to learn how Memcyco’s pioneering capabilities prevent and disrupt QRishing-related digital impersonation attacks throughout the attack timeline, protecting customer data indefinitely after takedown.



















