In social engineering attacks like smishing and phishing, the mind is the real target. How often do we quickly glance at a text or email and click without a second thought about its origins? Scammers know this, so they prey on the urgency conveyed in the convincing messages sent to your valued customers and unprepared coworkers.
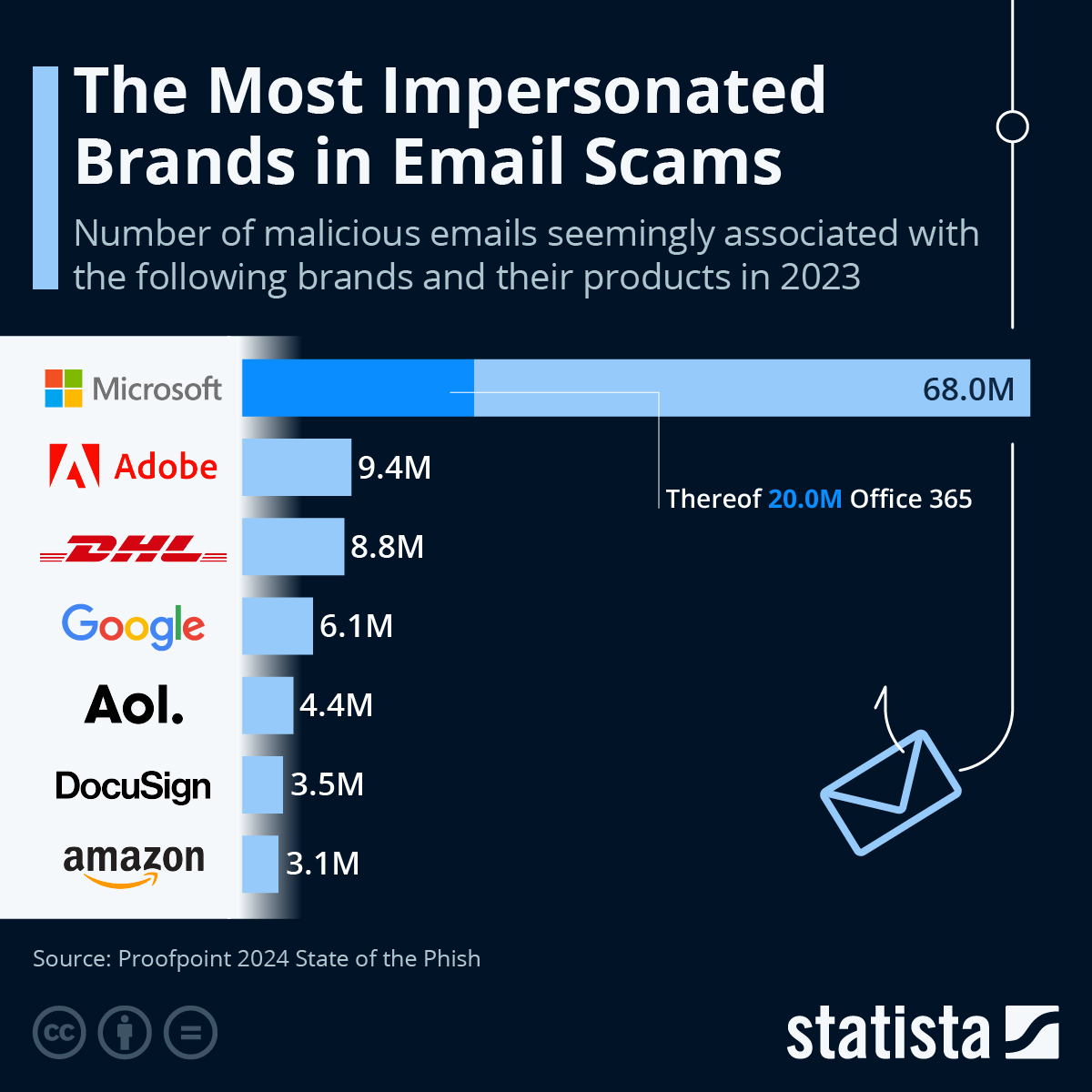
Opportunistic scammers send 3.4 billion spam emails daily. Low technical barriers to entry and the help of generative AI technology will likely increase these figures in the coming months and years. But how do these attacks differ, and how can you protect your employees and customers?
Smishing vs Phishing: What Are the Differences?
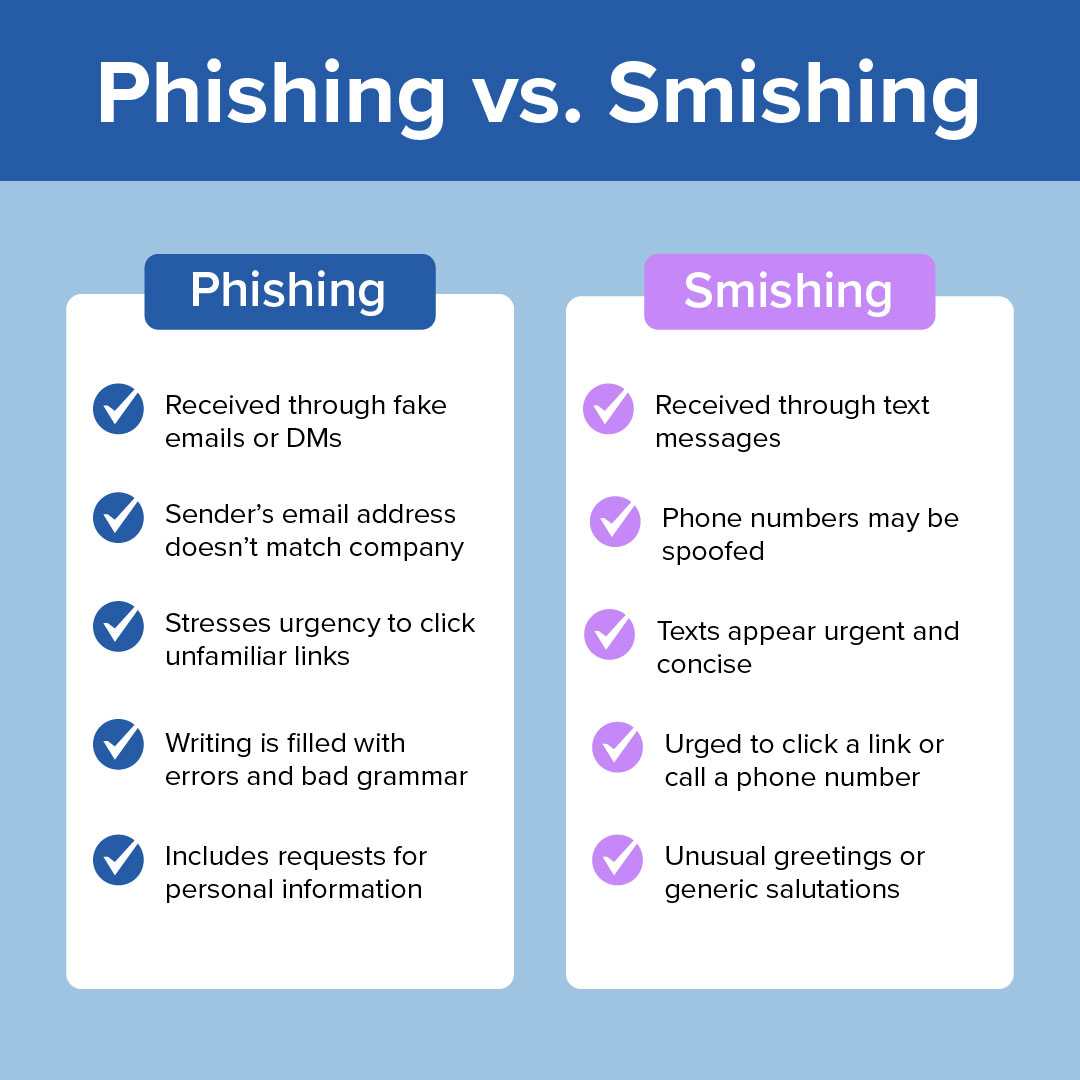
Phishing and smishing are often lumped together, especially since most people receive emails and SMS on the same device. Attackers use similar social engineering methods in both cases to steal information, financial details, or login credentials to commit identity theft, employee or customer account takeover, and other types of fraud.
By creating a sense of urgency or trust, these attacks trick victims into clicking on malicious links that either install malware or harvest PII. The critical differences between smishing and phishing are the delivery method, psychological impact, and how attackers exploit the respective mediums.
Phishing attacks occur through email, where scammers send fraudulent messages designed to look legitimate. These emails often impersonate legit emails from airlines, e-commerce businesses, banks, or internal company departments, using a technique known as clone phishing.
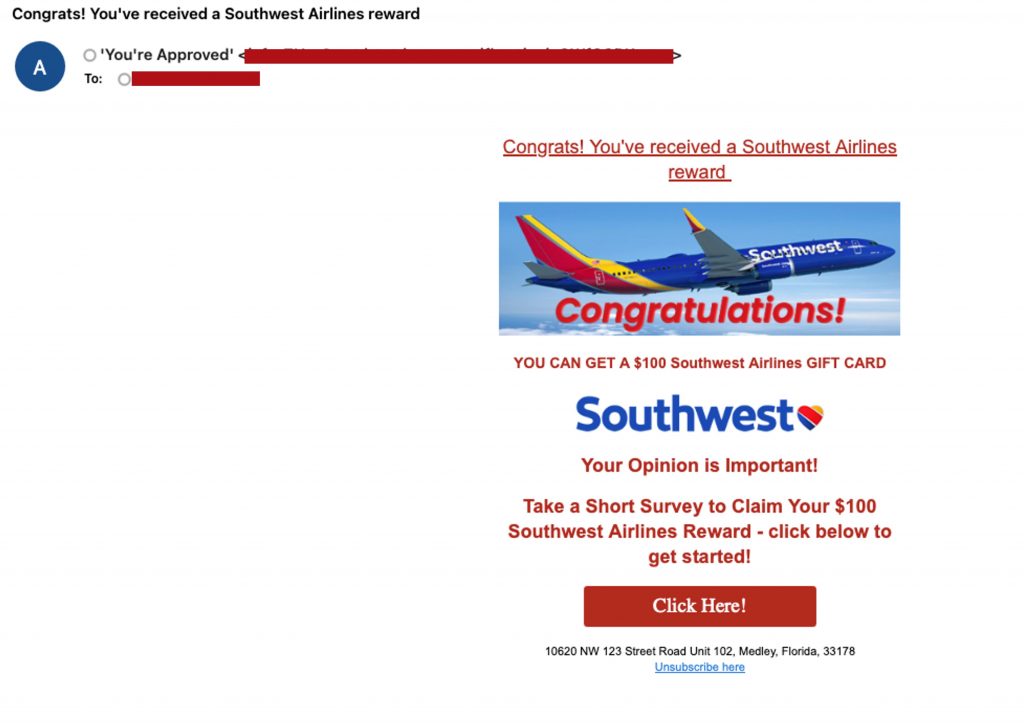
Scammers usually create highly elaborate emails using rich text formatting, official-looking branding, and high-quality graphics to trick recipients into taking action. The sheer volume of emails people receive daily makes it easy for phishing attempts to blend in, as scammers exploit the assumption that convincing messages are rarely questioned.
Smishing, on the other hand, uses text messages via SMS, Whatsapp, Telegram, Facebook Messenger, and other instant messaging communication channels as the attack vector. Since text messages feel more direct and personal than email, smishing attacks rely on short, compelling text bites that push the recipient to click a malicious link or share sensitive information without much thought.
For example, a customer might get an SMS about a package delivery delay, and, concerned that they missed a delivery or eager to see what they got, instantly click on a link and add the requested details without a second thought, only to get them harvested by the bad actor.
As for phishing, an employee might receive an email from “IT” asking them to update their login credentials. Concerned that they will be logged out of their work accounts, they will click the link to update details.
In both cases, the pressure to react quickly, combined with some naivete, often leads people to do the wrong thing.
Some view phishing as the overarching term, with smishing considered a subcategory. Other phishing variants include clone phishing, spear phishing, and whaling, each targeting victims through different methods and levels of personalization.
The Challenges of Protecting Against Smishing and Phishing Attacks
Once easily recognizable by spelling errors or generic greetings, phishing emails have become more personalized and sophisticated. Generative AI and the existence of off-the-shelf phishing kits make it quick and easy for even non-native speakers to create email and SMS messages that are well-phrased in the targets’ languages.
Brand exploitation across channels adds another layer of complexity to the mix. In many of these scams, attackers use fake websites and fake social media profiles that they have created, which mimic your genuine brand – and they can do this quite convincingly.
Human error remains one of the most challenging vulnerabilities to address. Social engineering tactics, which play on emotions like fear, urgency, or trust, can bypass even the best training programs. Companies clearly need real-time fraud detection and intervention rather than relying solely on user vigilance.
5 Examples of Smishing
1. Package Delivery Scams
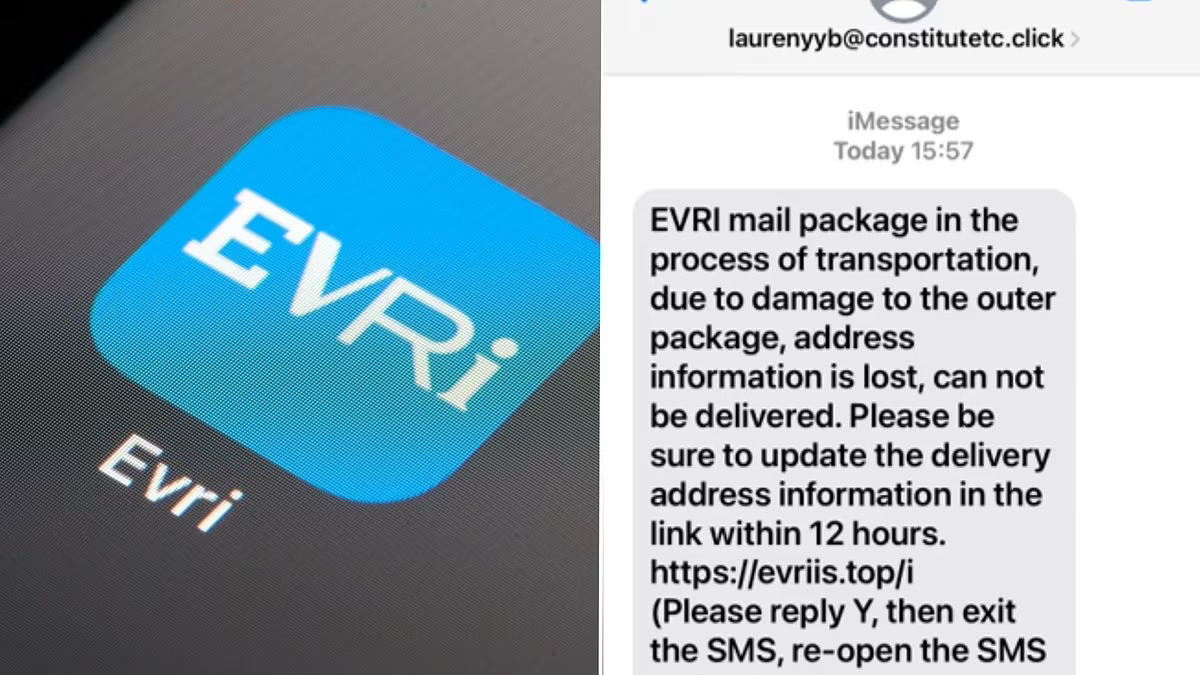
In this common smishing attack, a customer gets a text message claiming their package is delayed and asking them to verify their information. The SMS usually contains a link to confirm delivery details or track an item, but clicking the link leads to a malicious site. Attackers create these fake sites to harvest the customer’s personal information or install malicious code.
In May 2024, parcel service Evri warned customers about a massive rise in scam text messages purporting to be from the company. Evri noted a 174% increase in reported scams from April 2023 to April 2024. It had to close down 5,000 websites that were cloned versions of Evri’s designed to convince people to pay fake delivery fees or share personal information.
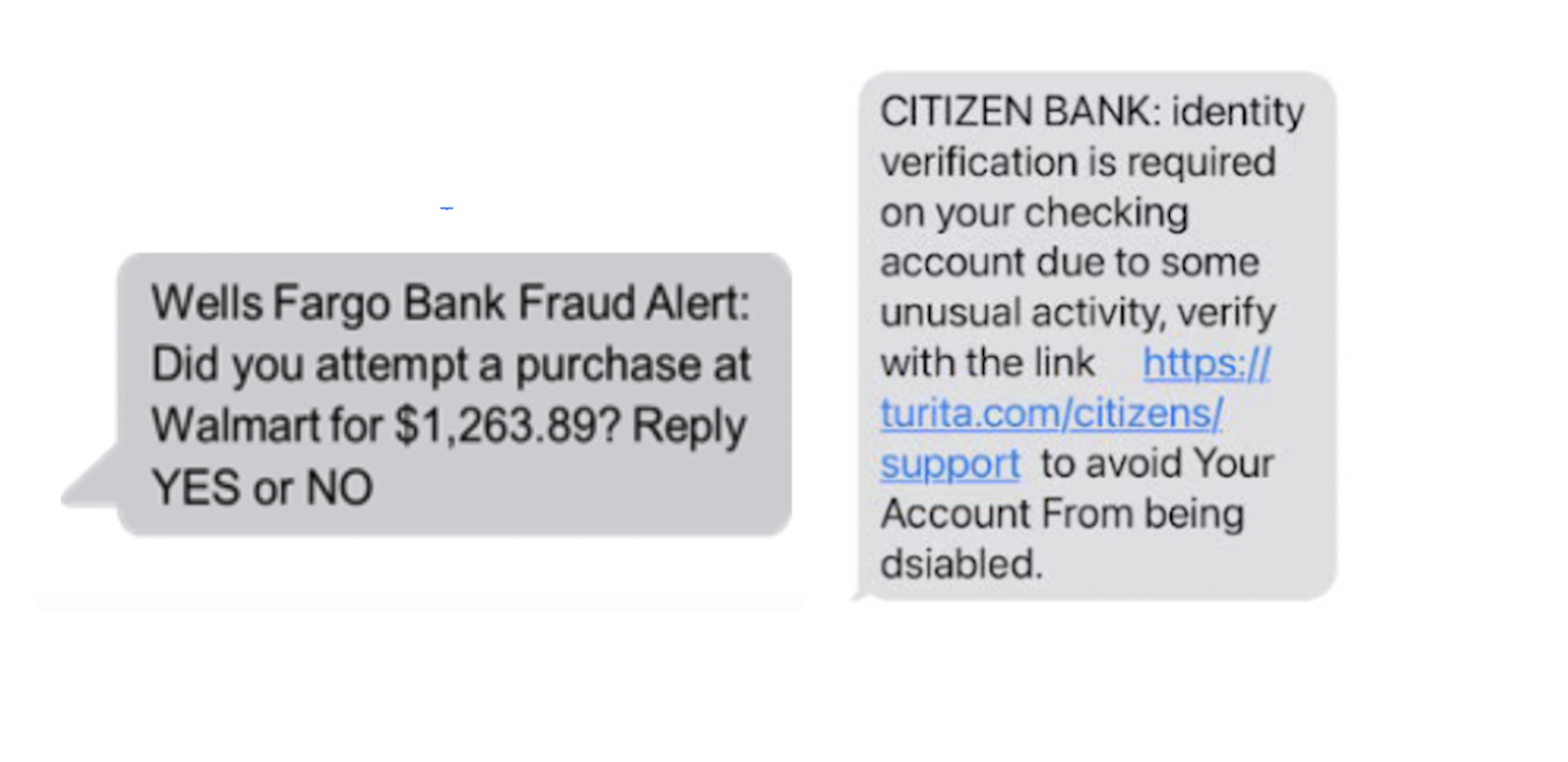
2. Bank Verification SMS Scams
A customer receives a text claiming that their bank account or card has been suspended due to suspicious activity. The message provides a link to “reactivate” the account or confirm transactions. When the user clicks the link, they’re taken to a fake website that looks like the bank’s login page. In their haste to resolve the issue, the victim enters their login credentials, unknowingly giving the attacker access to their real banking account, which they use to perform an ATO.
One person’s story, which appeared in The Guardian in 2023, highlighted how costly these scams can be. The victim received a text saying that someone had tried to set up a payment to a new payee, urging the victim to contact a phone number to resolve the issue. The victim believed this was genuinely their bank, but it ended up being a scam that cost them $22,000.
3. MFA Bypass
MFA (Multi-Factor Authentication) bypass is a sophisticated smishing tactic that targets people who have enabled additional security measures on their accounts. The text message includes a link directing the recipient to a fake website resembling the legitimate service’s login page. Usually, the pretext is the detection of unusual activity on their account or the need for immediate verification for security purposes. When victims click the link, they are prompted to enter their login credentials and 2FA code, which they receive via SMS or an authentication app.
4. Event Ticket Confirmation/Download
In this type of smishing attack, victims receive a text message claiming they have purchased or won tickets to an event, such as a concert or sports match. The message often includes details about the event, such as the date and location, to enhance its authenticity. The text directs users to a website where they can download their tickets.
This site may look similar to a legitimate ticketing platform, tricking people into believing they are interacting with a trusted service. The fraudulent site asks for personal information, such as credit card details or login credentials, to verify the ticket purchase. Victims eager to secure their tickets may enter this information without thinking critically.

5. SMS-Exclusive Promotions
Scammers send texts claiming the recipient has access to a one-time SMS-only promotion with a brand. The message calls for immediate action to claim the offer via a link that leads to a fake version of the genuine brand’s website. This tactic capitalizes on the exclusivity of text communication and uses the classic psychological manipulation of creating scarcity.
5 Examples of Phishing
1. Invoice Phishing Scams
Attackers send an email that appears to come from a legitimate supplier or service provider, complete with branding and invoice details. These scams exploit email’s ability to include attachments and rich formatting, making the invoice look authentic. Also, people expect to receive invoices by email rather than by a text message. Attackers urge the recipient to pay immediately through a link leading to a fraudulent, often cloned version of the supplier or service provider’s site.
In 2022, Toyota Boshoku, a significant supplier to Toyota, was defrauded through a fake invoice scam that cost them nearly $37 million. The fraudsters impersonated a business partner, sending legitimate-looking emails and invoices requesting payment. The finance team, believing the invoices to be genuine, transferred the funds to fraudulent accounts.

2. IT Department Impersonation
In this phishing attempt, the attacker sends an email mimicking the ones you often get from your internal IT department. The message might notify employees about a mandatory software update and direct them to a fake version of an honest software company’s site. It might also contain a malicious attachment masquerading as an executable software update file. This phishing method preys on employees who, without risk assessment training, may unknowingly download malware or enter sensitive login credentials into a fraudulent site.
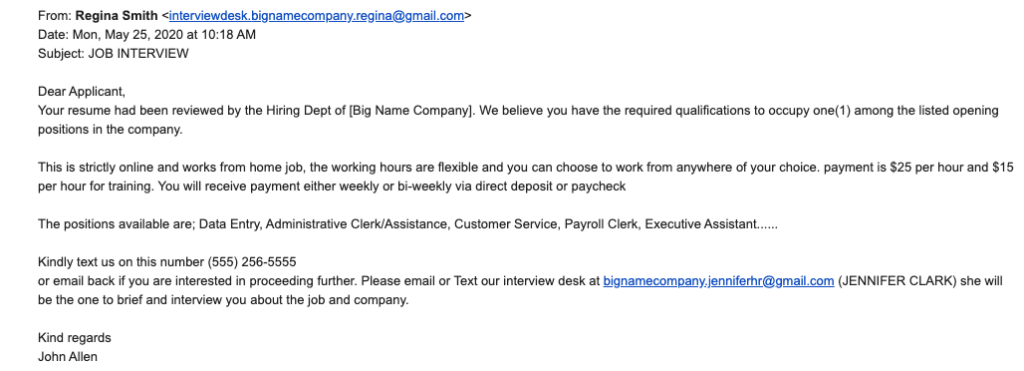
3. Job Offer or Recruitment Scam
In this type of phishing, a scammer sends an email that appears to be about a job with a reputable company. The email is well-written and includes official logos and contact information. It often invites the recipient to download an attachment or visit a link that supposedly contains the job details but, in reality, installs malware or steals info through fake sites. SMS lacks the space and professional tone needed for this type of scam, which is why the attack method used is phishing rather than smishing.
4. Fake Charity Appeals
Scammers create emails that appear to come from legitimate charities, especially during times of crisis or disaster. These emails often include emotional appeals and urgent requests for donations. The attackers might use graphics and branding that mimic well-known charitable organizations. Clicking the link will take the recipient to fake donation pages that capture their personal and financial information. In a way, this is the “perfect crime” since charities don’t ever expect to get a donation from you – as opposed to, say, e-commerce sites or banks, which in many cases have a reason to expect a money transfer.
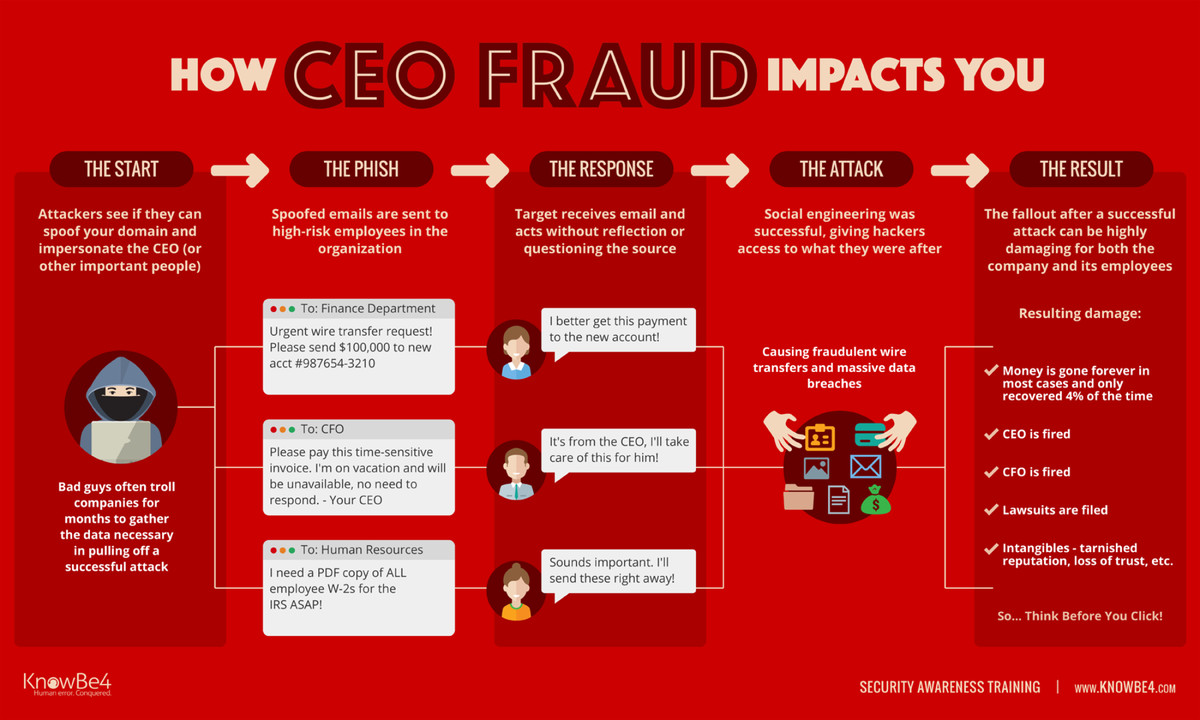
5. CEO Fraud
CEO fraud is when attackers impersonate a company’s chief executive officer (CEO) or another high-ranking official to manipulate employees into transferring money or divulging sensitive information. This tactic preys on the authority and trust associated with receiving emails from those in executive positions. For instance, the email could advise employees that the company’s SaaS data security has been compromised and request they buy a new security tool or wire money to a supplier.
Stop Fraud Before It Starts
A lot of emphasis gets placed on security training and awareness in cybersecurity and with good reason. However, it’s clear that with the growing volume and complexity of smishing and phishing attacks, relying on education alone won’t cut it. You need to complement training with technology-based solutions that get to the heart of these scams and stop them at their source.
A common thread running through these social engineering methods is using fake websites to mimic legitimate sites of reputable companies. Actively monitoring and taking down these impersonated websites is one way to reduce risks for customers and coworkers.
Memcyco is a real-time solution that doesn’t just detect fake sites—it also provides detailed information on the attacker, attack, and each individual victim, and helps you protect your business and your customers during the window of exposure—the time between when the fake site is up and when it is taken down. Learn more here.



















![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)