Most people know not to click on obvious spam emails, but today’s scams are polished, highly personalized, and AI-powered. Whether it’s a fake banking alert, a deepfake customer service call, or a cloned e-commerce website, social engineering fraud often spreads fast.
When customers see familiar branding, hear a confident voice, or receive a message that appears to come from a trusted source, it’s easy to comply and get duped. 98% of cyberattacks rely on social engineering, with phishing schemes being the most popular approach.
Companies wanting to protect customers from these scams face an increasingly challenging task that requires new approaches that move beyond traditional ways to detect fraud.
The Mechanics of Social Engineering Fraud
Social engineering fraud is when bad actors manipulate psychological traits to steal money or personal data from your customers. A fraudster might pose as a customer service agent confirming a refund or a payment processor verifying an urgent transaction. The goal is to exploit trust to get your customers to reveal helpful information, like their login details, card information, or authorization codes that can then be used for fraud.
Not all scams are the same, but the general process starts with gathering info about targets from social media profiles, leaked data from previous breaches, or your company’s communication patterns to craft highly convincing phishing or smishing messages. The fraudsters then try to initiate urgency (such as by warning of account compromises) backed up with authority (e.g., by mimicking your recent email templates or SMS alerts) to trick people.
Unfortunately, fast-moving tech developments make it easier than ever for fraudsters to scam your customers with social engineering fraud. They use deepfake-generated voices that mimic actual call center agents (it’s getting easier to do this with each passing month). Their tactics extend beyond just phishing emails to recreate entire brand experiences, including exact cloned versions of your site or portal that they spin up rapidly and lead unknowing customers to.
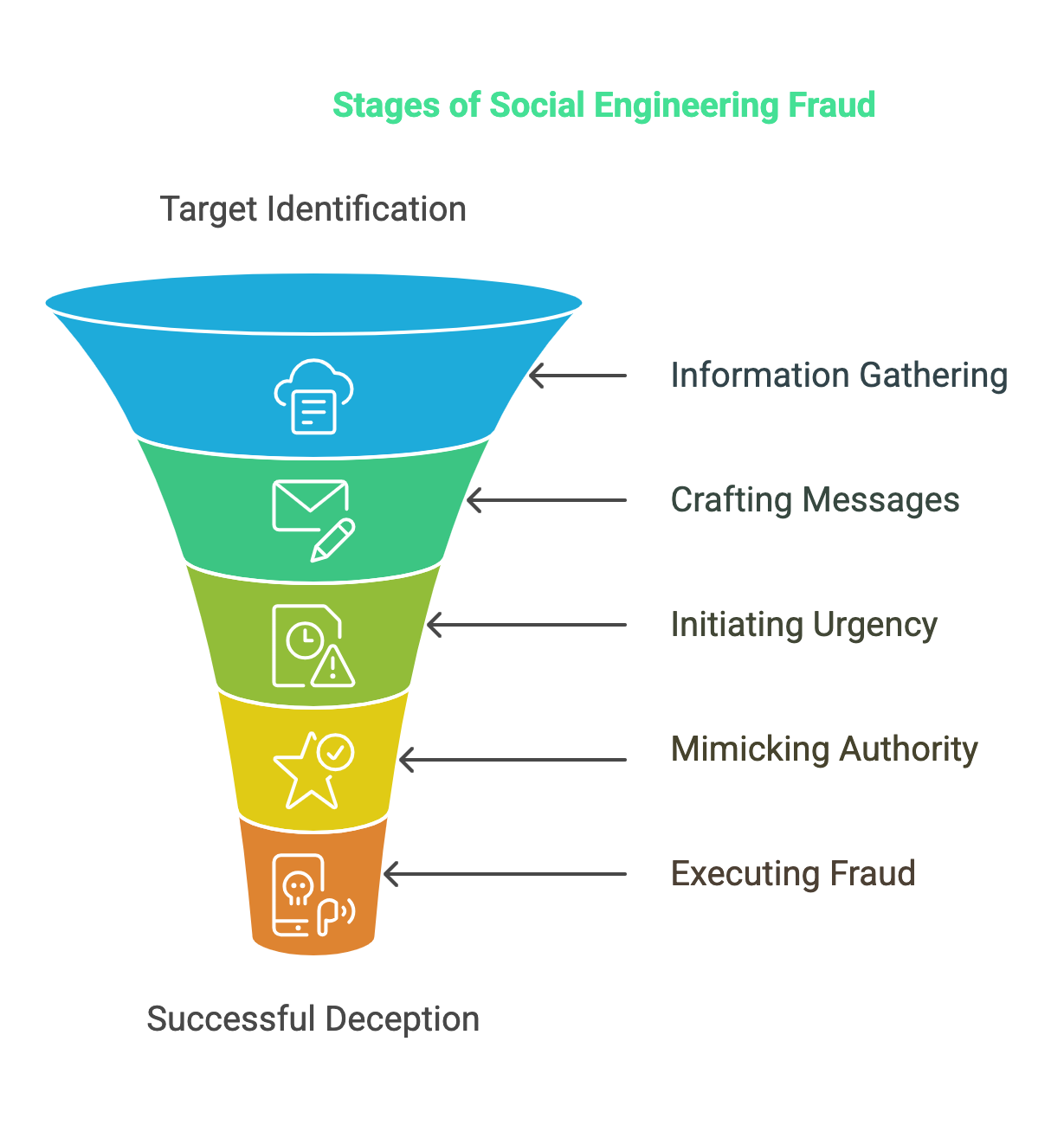
Why Traditional Security Measures Fail to Combat Social Engineering Fraud Effectively
Most typical fraud detection systems analyze transactional patterns, flag anomalies, and respond to social engineering scams once they have occurred. This reactive approach works well for known fraud patterns, such as detecting unauthorized transactions.
However, when an attacker tricks a customer into handing over credentials on a fake site or approving a payment via social engineering tricks, traditional fraud models often see nothing unusual because the eventual fraudulent activity comes from a trusted device or correct credentials.
Some phishing kits, available to buy on dark web marketplaces, now include one-click website cloning tools that allow fraudsters to generate a near-perfect copy of your site rapidly. The people trying to con customers can lead them to these sites, which are beyond the purview of the transaction monitoring tools you already use.
A key flaw in traditional fraud detection is its reliance on post-event analysis. Most anti-fraud tools flag fraud only after transactions occur when it’s too late. Anti-fraud tools might detect a substantial payment and attempt to stop it, but stopping that transaction becomes much more complicated if someone has already tricked your customer into authorizing it.
Social Engineering Fraud: 7 Ways to Protect Customer Accounts and Card Data
1. Real-Time Visibility into Attacks and Impacted Customers
Most fraud teams don’t know social engineering fraud happens until fraudulent transactions happen. By then, hundreds or thousands of customers may have already been deceived. Social engineering fraud scales fast, and defenses need to keep up.
- Use real-time monitoring tools like Memcyco, which detect fraudulent domains and phishing sites in real-time, giving organizations instant visibility into active attacks – and allowing immediate customer protection, before harm is done.
- Deploy customer-side fraud telemetry to identify when users attempt logins from compromised phishing sites or interact with spoofed domains.
- Correlate attack patterns across digital touchpoints and try to identify which customers are most likely to be targeted based on known fraud trends.
2. Monitor for Brand Impersonation Across Channels
Aside from email phishing, scammers use fake customer service accounts, clone entire banking apps, and even buy Google ads to trick customers into trusting fraudulent sites. Customers won’t always visit your website directly; many rely on search engines or social media, where impersonation scams thrive. If you aren’t actively monitoring how your brand is being used outside your owned assets, fraudsters will hijack your reputation to steal from your customers.
Comprehensive Enterprise Fraud Management solutions should give you the multi-channel visibility you need to be proactive in detecting scams and correlate data for effective responses.
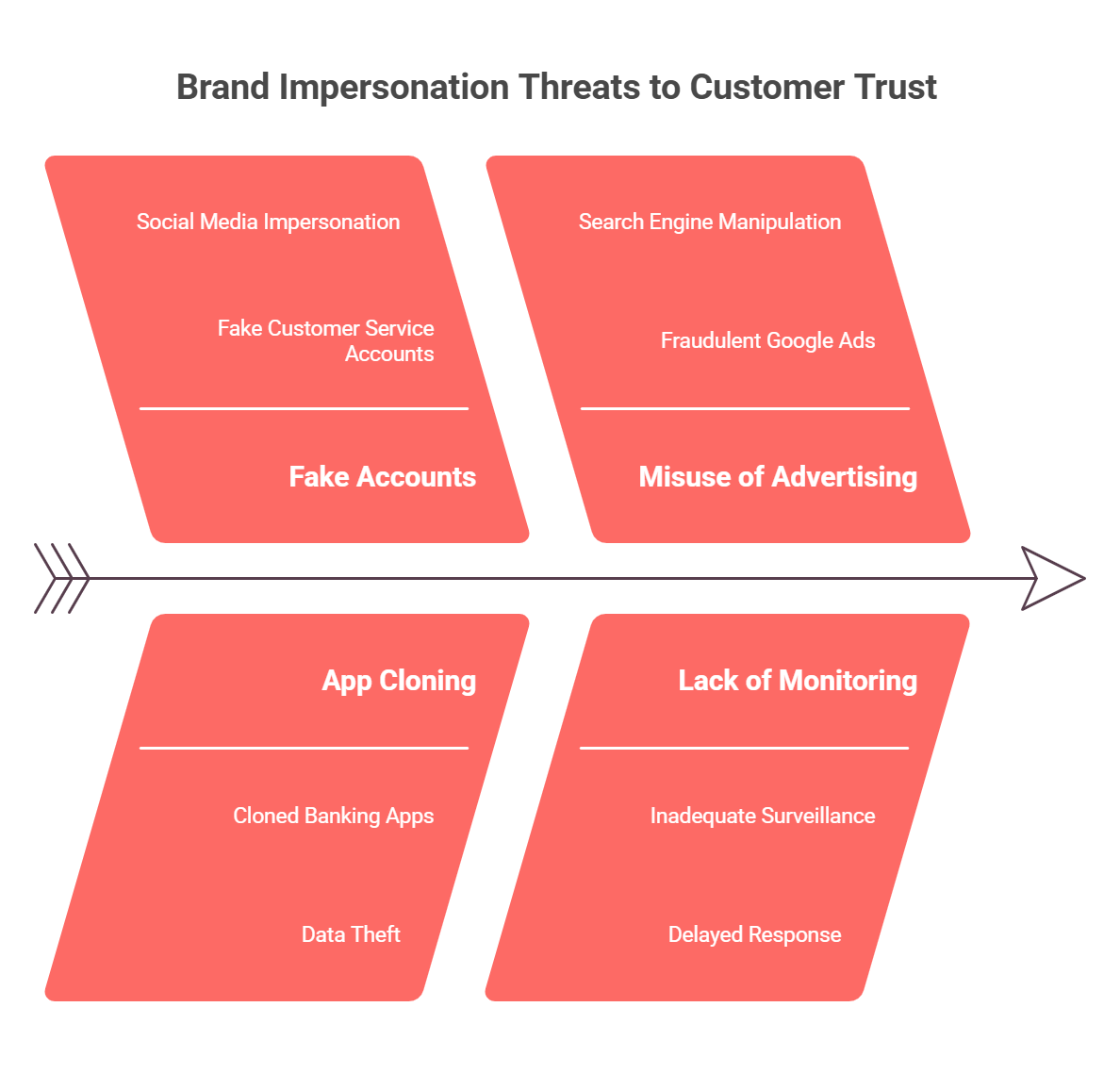
3. Detect and Neutralize Impersonation Scams Before They Go Live
Attackers no longer need weeks to set up phishing infrastructure because they use automated phishing kits that generate fake websites in minutes. You’re too slow if you rely on manual threat investigations to find and remove these sites. Fraudsters will already have stolen credentials and executed ATOs, and they will disappear before your team identifies the threat and quantifies its risk.
Look for tools or solutions that alert you the moment a fraudulent site goes live so you can neutralize the threat before your customers fall for it.
Tools like Memcyco give you instant alerts if your site has been cloned and deeper insights into the attacker, their location, and the customers affected. This enables companies to significantly reduce their exposure window and prevent the attack from escalating.
4. Proactively Secure Customer Data with Real-time Decoy Data
The attack moves beyond your control once a fraudster gets hold of real customer credentials or card data. Account takeovers (ATOs), unauthorized transactions, and identity fraud happen in minutes. A preventative approach that ensures stolen data is useless before attackers can use it to their advantage can save much of the fallout from social engineering fraud.
Using a solution with decoy data is a great way to protect individual customers and actively sabotage scams at scale. The idea is to prevent fraud by ensuring stolen credentials or card details never work in the first place.
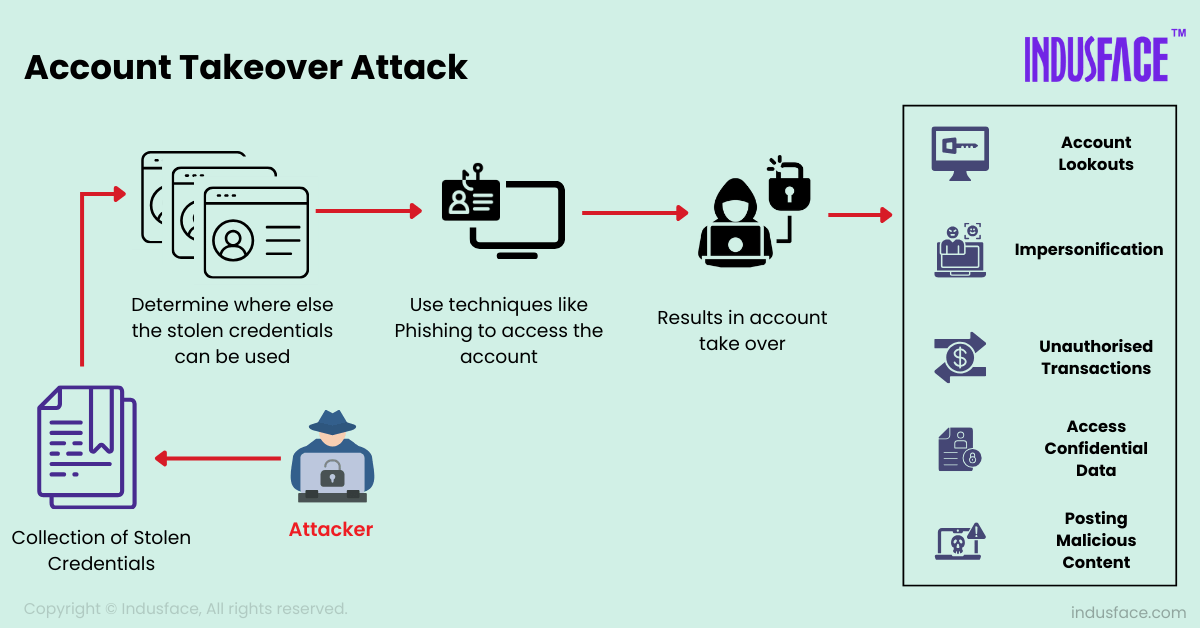
5. Predict Customer Account Takeovers Before They Happen
When a fraudster logs in with stolen credentials, it’s too late for you to act. Account takeovers mean your customer has been socially engineered to approve fraudulent action. You need to spot signs of potential account compromise before login attempts happen.
- Look for early indicators of credential compromise, including phishing telemetry, dark web leaks, and credential stuffing attempts.
- Implement a zero-trust system and deploy dedicated solutions to detect and block unauthorized attempts to extract sensitive customer information (such as login credentials or payment details) from internal systems.
- Choose a tool that blocks account access or requires extra authentication when unknown devices log in to user accounts.
6. Leverage AI-Powered Threat Intelligence to Preempt Cyber Attacks
Social engineering scams are organized, scalable operations that use AI to automate much of the work. Fraud teams can also use the power of AI to fight back, though:
- Use predictive fraud models to identify which customer segments are most at risk of social engineering scams.
- Automate phishing detection with natural language processing (NLP) that continuously improves through reinforcement learning and model validation to minimize false positives.
- Integrate deepfake detection tools to counteract voice-based impersonation fraud.
7. Establish a Dedicated Fraud Awareness & Response Strategy for Customers
Security awareness training is designed for employees, not customers. However, customers are the primary target of social engineering fraud. If your fraud prevention strategy doesn’t include proactive customer education, you expose them when they encounter inevitable scam attempts.
Consider adding real-time security prompts within customer sessions, not just through emails or newsletters that people might ignore. Build adaptive fraud warnings into high-risk transaction flows and remind users to verify the legitimacy of requests. Ideally, look for solutions to warn your customers they’re on the verge of being scammed.
Stopping Social Engineering Fraud Before It Reaches Your Customers
Social engineering fraud has evolved from broad, generic scams into highly targeted, AI-powered deception campaigns that exploit trust at scale. With fraudsters moving faster than ever, businesses can no longer afford to rely on post-event fraud detection. Preventing social engineering fraud means having defenses that help halt scams before customers engage.
Instead of waiting for fraudsters to exploit stolen credentials, Memcyco stops social engineering scams at the source by detecting cloned websites the moment they go live and shutting down impersonation threats across digital platforms. Your customers receive real-time Red Alert banners, warning them before they enter credentials into compelling yet cloned versions of your site or platform.
If attackers manage to steal login details or card numbers, Memcyco neutralizes the threat with decoy data to render stolen info useless. You get deep insights into attack origins, revealing the devices, locations, and specific customers targeted. With continuous brand monitoring, real-time phishing detection, and preemptive fraud prevention, Memcyco ensures fraudsters never reach your customers in the first place. See how Memcyco protects your brand and customers from advanced social engineering fraud. Learn more here.



















