Account Takeover Prevention
Predictive, real-time customer ATO prevention
Know which customer accounts will be targeted by phishing-related scams, reduce customer ATOs by over 50% and slash incident-related OPEX
How most customer ATOs start (and how to make sure they don’t)

Phase 1
The fake site bait
You know how this goes: your customer receives a phishing message with a link to a fake website.

What if you could
Detect ATO attacks before they become attacks
- Stop ATOs before phishing links reach customers
- Detect pre ATO site-code reconnaissance
- Intervene before attacks become PR disasters
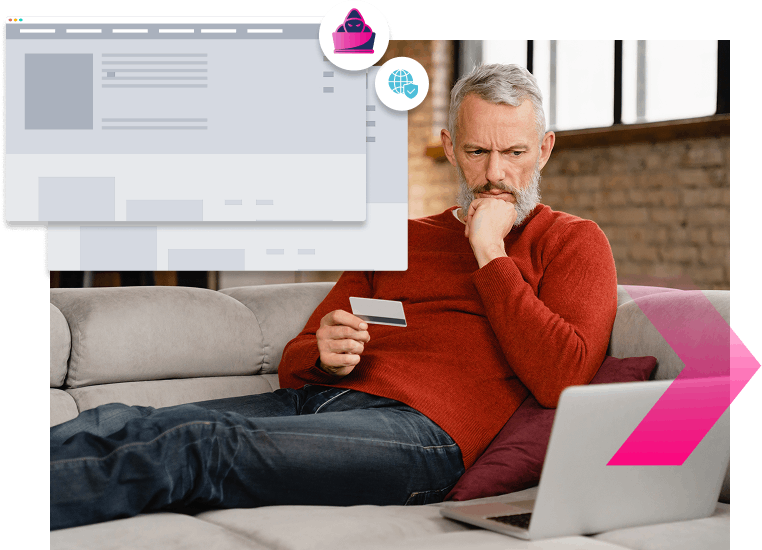
Phase 2
The fake site trap
On clicking link, they arrive at a fake website site dentical to yours. Why suspect anything?
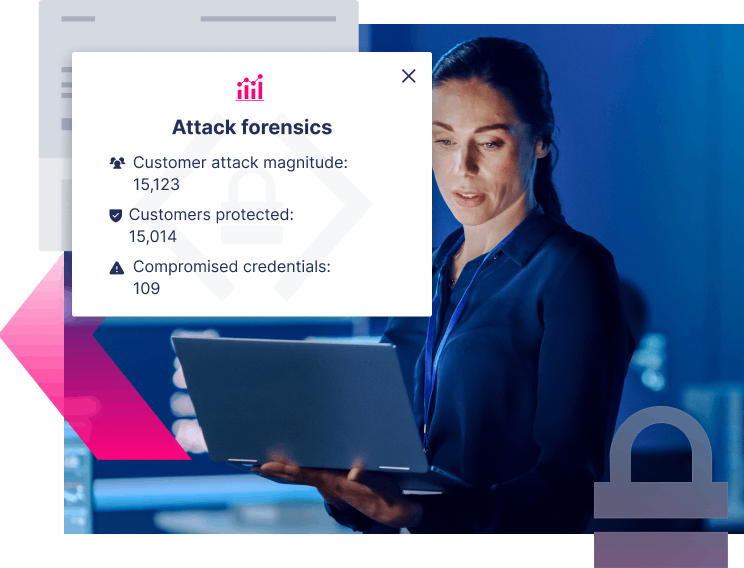
What if you could
Stop customers falling for ATO traps in the first place
- Prevent bloated incident handling costs
- Reducing loss of customer trust
- Avoid ‘social media’ shaming incidents

Phase 3
Credentials harvesting
Convinced the page is authentic, your
customer attempts login, handing their
credentials to attackers in the process.
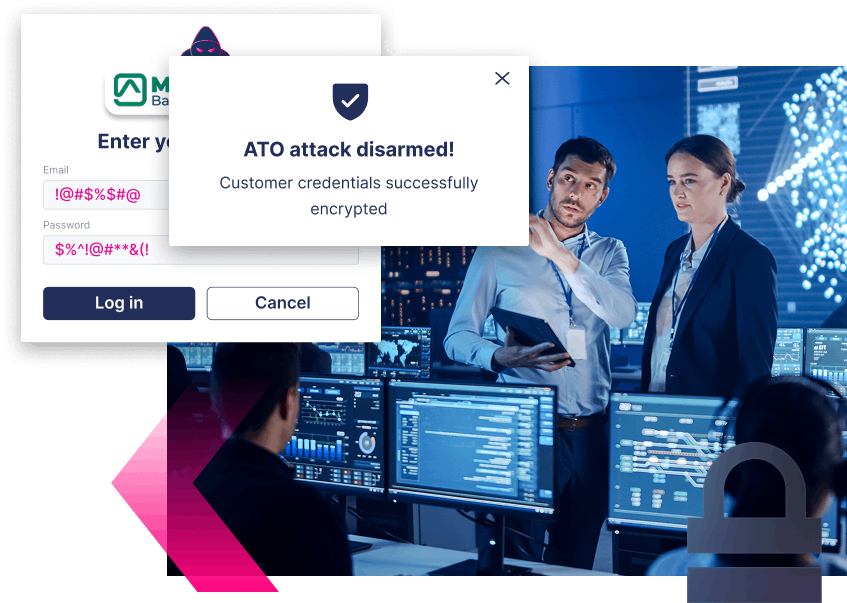
What if you could
Disarm fraudsters when they try to steal customer credentials
- Keep customer accounts locked and airtight
- Turn ATO attacks into auto-counterattacks
- Reduce reliance on customer scam-awareness
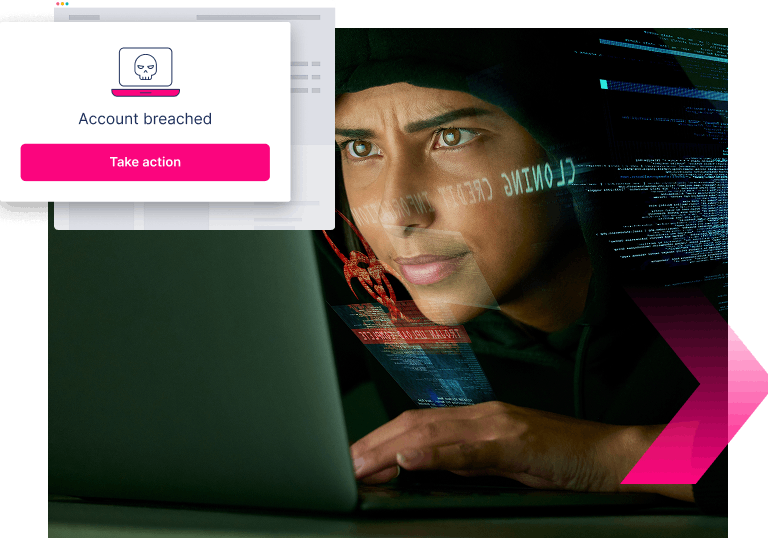
Phase 4
Account takeover
With credentials now in the hands of
fraudsters, bad actors have unfettered
access to your customer’s account.
What if you could
Trick fraudsters into locking themselves out of your website
- Allow ‘known device’ account access
- Block access from unknown devices
- Reveal traceable attack–source data

Phase 5
Exploitation & Exfiltration
Once inside, attackers can lock the door
behind them, exploiting and extracting
customer data and assets.

What if you could
Protect customers longer against future ATO attacks
- Keep accounts safer, even after fake-site takedown
- Shield customer accounts from credential stuffing
- Reduce future ATO incident-handling costs
Accurately predict and prevent customer ATOs
With Memcyco
before phishing messages are sent to customer devices
the moment customers fall for ATO phishing scams
after the initial ATO attack is over, and credentials stolen
Without Memcyco
by only detecting ATOs once they become full-fledged attacks
relying on their ability to detect phishing links and messages
to continual, ongoing ATO risk long after fake-site takedown
Crush Atos Earlier, and Keep Them Crushed Longer
Discover why global brands replace their previous solution with Memcyco

Predict and prevent ATOs
Reduce ATOs
50%
Achieve MTTD of
Zero
Cut expenses by
$Millions
Already solved MitM attacks? Solve more

Man in the Middle (MiTM) Protection

Account takeover (ATO)




Credential Stuffing



Fake e-shops, purchase scams, gift card scams

Get a Custom Demo
See it in action and discover why others switch to Memcyco
Get a demo to learn how Memcyco customer :
-
Identify individual scam victims in real-time
-
Predict and preempt ATO incidents
-
Deceive threat actors
Frequently asked questions
What Is an Account Takeover (ATO)?
An Account Takeover (ATO) refers to unauthorized access to a customer’s online account. This form of identity theft allows cybercriminals to conduct unauthorized transactions, withdraw funds, and access sensitive personal and financial information of the customer. It directly impacts customer trust and can lead to significant financial losses.
Why Is Real-time Account Takeover Prevention So Important?
Real-time prevention is vital for protecting customer accounts from unauthorized access. It provides immediate detection and response capabilities that stop fraudsters in their tracks, thereby preventing them from exploiting stolen credentials. This is crucial in maintaining the integrity of customer transactions and safeguarding sensitive information.
Why Are ATO Attacks Still a Massive Threat for Many Businesses?
ATO attacks pose a massive threat due to the increasing reliance of customers on digital services for banking, shopping, and personal data management. These platforms are lucrative targets for attackers looking to exploit weak security measures and gain access to a wealth of personal data.
How Do Account Takeovers Happen?
ATO primarily happens through techniques such as phishing, where customers are deceived into providing login information, or through malware that records keystrokes. Attackers also use credential stuffing, applying stolen credentials to breach multiple accounts, taking advantage of customers who reuse passwords across services.
Who Do Account Takeovers Impact?
ATO impacts customers by compromising their personal and financial information, which can lead to unauthorized purchases, identity theft, and financial loss. The repercussions extend to businesses, resulting in lost customer trust, reputational damage, and potential financial and legal penalties.
How Can Businesses Prevent More ATOs?
Businesses can enhance their defenses against customer ATOs by implementing Multi-Factor Authentication (MFA), using advanced security solutions like real-time threat detection systems, and by conducting regular security awareness training. These measures help in identifying and mitigating threats before they impact customers.
What Measures Can Businesses Take to Protect Customers from ATO?
To protect customers, businesses should enforce robust password requirements, enable MFA, regularly update security systems, and monitor customer accounts for unusual activities. Additionally, educating customers on the importance of secure online practices and how to identify phishing attempts is crucial.
Why Should You Use a Real-Time Account Takeover Protection Solution?
A real-time ATO protection solution is essential because it monitors customer accounts for signs of unauthorized access continuously. This allows businesses to respond instantly to potential threats, safeguarding customer data and preventing financial losses associated with ATO incidents.
What Account Takeover Techniques Do Fraudsters Use?
Fraudsters employ several techniques targeted at customers, including phishing emails that mimic legitimate requests, credential stuffing with previously breached data, and more targeted attacks like SIM swapping to intercept one-time passcodes. Understanding these techniques helps businesses better protect their customers.
How Much Does It Cost to Remediate ATO Incidents?
The cost of remediating ATO incidents primarily involves direct losses incurred through fraudulent transactions and the operational costs of securing compromised accounts. Additionally, indirect costs such as customer support, legal fees, and efforts to rebuild customer trust can be significant.
By focusing on customer-centric aspects of ATO, these responses aim to provide businesses with clear and actionable insights on protecting their clients and maintaining the security and integrity of their services.