High fidelity, browser-level credential stuffing detection
Detect credential stuffing earlier and more accurately versus server-based detection and expose threat actors
How credential stuffing attacks work and the flaws in server-level detection

Phase 1
Credential harvesting and injection
Fraudsters deploy bots that make bulk login attempts using lists of harvested credentials. Most solutions detect only successful login attempts that reach the server, making them prone to inaccuracy and false positives.
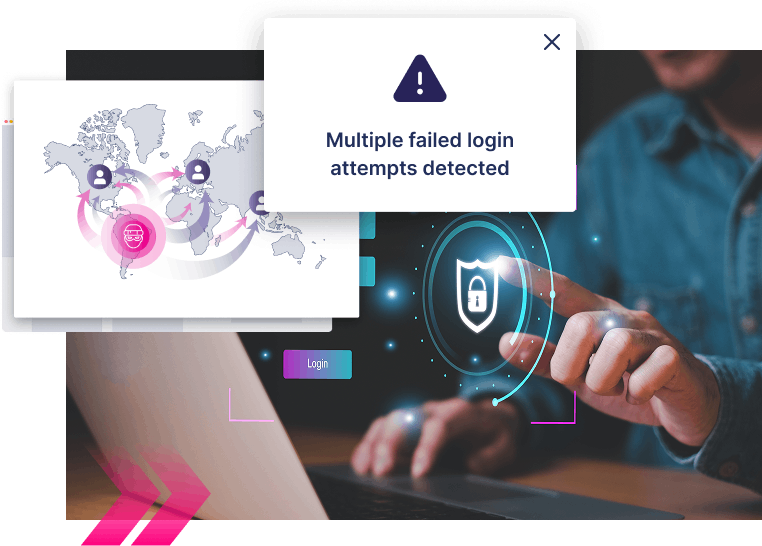
What if you could
Detect not just successful credential stuffing attempts, but also failed attempts at the browser level?
- Supercharge credential stuffing detection accuracy
- Reduce false positives common with server-based solutions
- Take the earliest possible action, as soon as attacks start

Phase 2
Account takeover (ATO)
Once the attack successfully matches a set of credentials, the attacker gains account access
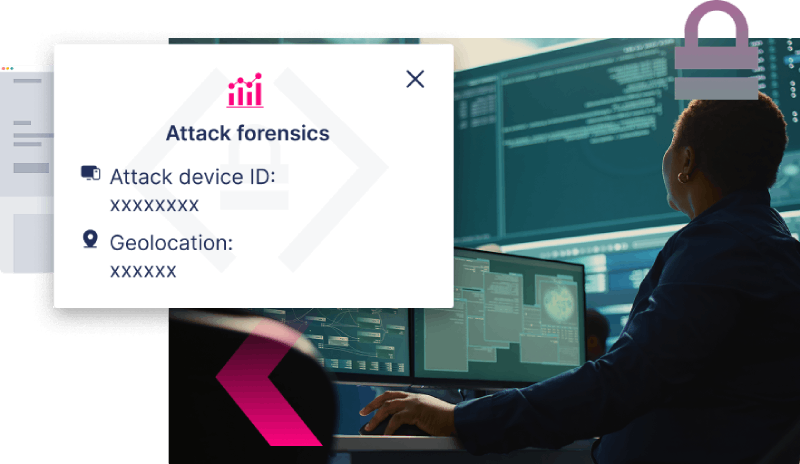
What if you could
Block unauthorized access attempts before they succeed
and reveal forensic insight about the attack device used?
- Lead with prevention, not remediation
- Reduce incident-related expenses
- Strengthen digital trust and customer retention
Phase 3
Exploitation and exfiltration
Once inside, attackers may use the same device to access multiple accounts, or different devices for each account takeover to evade detection.
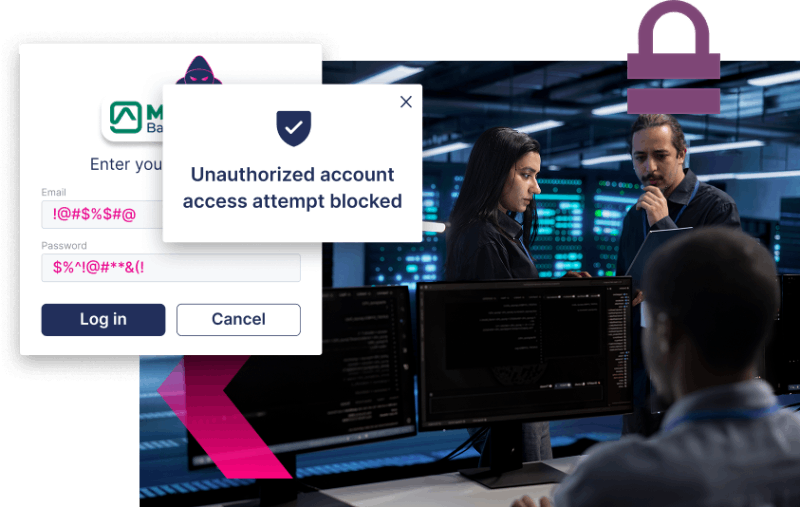
What if you could
Prevent ATOs from spreading to other accounts
- Detect suspicious device usage patterns early
- Block illegitimate access attempts before they succeed
- Deter threat actors from launching future attack
Detect credential stuffing earlier, and block unauthorized access
With Memcyco
Flag more attacks before accounts are compromised
Detect failed and successful login attempts
Reveal attack device data, block unauthorized access
Without Memcyco
Only flag attacks once threat actors compromise accounts
Only detect successful login attempts
No forensic data about the attack device used
Discover why global brands replace their previous solution with Memcyco

Faster, more accurate credential stuffing detection
Improve detection
accuracy by
X2 or more
Reduce false
positives by
> 75%
Reduce successful
ATOs by
> 50%
Already solved MitM attacks? Solve more

Man in the Middle (MiTM) Protection





Credential Stuffing



Fake e-shops, purchase scams, gift card scams

Get a Custom Demo
See it in action and discover why others switch to Memcyco
Get a demo to learn how Memcyco customer :
-
Identify individual scam victims in real-time
-
Predict and preempt ATO incidents
-
Deceive threat actors
Frequently asked questions
What is credential stuffing, and why is it a threat to businesses?
Credential stuffing is a cyberattack where attackers use stolen username-password pairs to access user accounts. This attack can lead to account takeovers, financial losses, and data breaches, making it a major risk for businesses that manage sensitive customer accounts. Studies show that over half of consumers reuse passwords across multiple accounts, significantly increasing their vulnerability to such attacks. Credential stuffing exploits data breaches that expose large volumes of user credentials, allowing attackers to access multiple accounts more easily.
How does credential stuffing differ from traditional brute-force attacks?
Credential stuffing uses actual usernames and passwords, often obtained from data breaches, rather than guessing random combinations. This method bypasses many basic security measures, making it harder to detect without browser-based, real-time monitoring that captures both failed and successful login attempts. Unlike brute-force attacks, which rely on trial and error, credential stuffing takes advantage of reused credentials across platforms, making it especially challenging for conventional security measures.
How can businesses detect credential stuffing attacks early?
Early detection involves monitoring login attempts in real time and analyzing user behavior for signs of suspicious activity, such as login attempts from unfamiliar devices or unusually rapid attempts across multiple accounts. Browser-based detection is particularly effective because it captures both failed and successful login attempts at the client level, allowing businesses to detect credential stuffing patterns instantly and respond before threats escalate.
What’s the difference between browser-based and server-based credential stuffing detection?
Browser-based detection captures suspicious activity directly at the user’s point of login, allowing for real-time detection of both failed and successful login attempts. This provides quicker responses to suspicious activity, reduces false positives, and lowers server load by analyzing user behavior at the client level.
How can credential stuffing solutions reduce false positives?
Advanced solutions use precise behavior analysis to distinguish between genuine and suspicious login attempts, which reduces false positives. Browser-based credential stuffing detection enhances accuracy by capturing successful and unsuccessful login attempts, plus nuanced user interactions at the login point, making it easier to accurately differentiate legitimate users from attackers.
How do adaptive security measures help in defending against credential stuffing?
Adaptive security automatically tightens or relaxes login protocols based on risk levels. During high-risk periods, it increases security checks, protecting accounts from credential stuffing without unnecessarily inconveniencing legitimate users. This approach allows organizations to respond dynamically to changing threat levels.
Why is tracking both failed and successful login attempts important in credential stuffing prevention?
Tracking both failed and successful attempts allows for more accurate detection of credential stuffing. Browser-based detection at the login stage is particularly useful for identifying suspicious successful logins from unrecognized devices or unusual locations, enabling businesses to detect potential account takeovers and respond swiftly.
What are common methods for preventing credential stuffing?
Effective credential stuffing prevention includes using tools that analyze both failed and successful login attempts in real time, applying adaptive security, and recognizing new devices. Multi-factor authentication (MFA) and rate limiting add extra layers of security, but browser-based detection is a critical tool for capturing early signs of credential abuse and building digital impersonation fraud resilience.
How does credential stuffing impact customer trust?
When accounts are compromised, customers lose confidence in a business’s ability to protect their data. Protecting against credential stuffing can help maintain trust by preventing account takeovers and securing sensitive information. Beyond immediate financial impacts, companies that prioritize security are more likely to retain customer loyalty.
Can credential stuffing solutions integrate with my existing security systems?
Yes, many credential stuffing prevention solutions integrate seamlessly with existing security measures like multi-factor authentication (MFA), single sign-on (SSO), and identity verification tools. This enhances the solution’s effectiveness by adding layers of defense without disrupting current workflows. Compatibility with these systems ensures smooth implementation and allows credential stuffing protection to function as part of a cohesive security strategy.
What role does AI play in credential stuffing prevention?
AI-driven detection identifies credential stuffing attacks by analyzing large volumes of login data to spot subtle patterns in user behavior. Machine learning models continuously improve detection accuracy, reduce false positives, and adapt to evolving attack tactics, allowing security teams to stay ahead of credential-based threats. By leveraging AI, businesses can intercept credential stuffing attempts as they happen, rather than merely reacting after a breach occurs.
Which industries are most vulnerable to credential stuffing attacks?
Industries with high-value user accounts, like finance, eCommerce, and media streaming, are especially vulnerable due to the sensitive nature of their data. Businesses in these sectors benefit greatly from real-time, behavior-based solutions to defend against credential stuffing attacks. Their reliance on digital transactions makes them prime targets for cybercriminals seeking quick financial gain.
How Do Account Takeovers Happen?
ATO primarily happens through techniques such as phishing, where customers are deceived into providing login information, or through malware that records keystrokes. Attackers also use credential stuffing, applying stolen credentials to breach multiple accounts, taking advantage of customers who reuse passwords across services.
Who Do Account Takeovers Impact?
ATO impacts customers by compromising their personal and financial information, which can lead to unauthorized purchases, identity theft, and financial loss. The repercussions extend to businesses, resulting in lost customer trust, reputational damage, and potential financial and legal penalties.
How Can Businesses Prevent More ATOs?
Businesses can enhance their defenses against customer ATOs by implementing Multi-Factor Authentication (MFA), using advanced security solutions like real-time threat detection systems, and by conducting regular security awareness training. These measures help in identifying and mitigating threats before they impact customers.
What Measures Can Businesses Take to Protect Customers from ATO?
To protect customers, businesses should enforce robust password requirements, enable MFA, regularly update security systems, and monitor customer accounts for unusual activities. Additionally, educating customers on the importance of secure online practices and how to identify phishing attempts is crucial.
Why Should You Use a Real-Time Account Takeover Protection Solution?
A real-time ATO protection solution is essential because it monitors customer accounts for signs of unauthorized access continuously. This allows businesses to respond instantly to potential threats, safeguarding customer data and preventing financial losses associated with ATO incidents.
What Account Takeover Techniques Do Fraudsters Use?
Fraudsters employ several techniques targeted at customers, including phishing emails that mimic legitimate requests, credential stuffing with previously breached data, and more targeted attacks like SIM swapping to intercept one-time passcodes. Understanding these techniques helps businesses better protect their customers.
How Much Does It Cost to Remediate ATO Incidents?
The cost of remediating ATO incidents primarily involves direct losses incurred through fraudulent transactions and the operational costs of securing compromised accounts. Additionally, indirect costs such as customer support, legal fees, and efforts to rebuild customer trust can be significant.
By focusing on customer-centric aspects of ATO, these responses aim to provide businesses with clear and actionable insights on protecting their clients and maintaining the security and integrity of their services.