The Digital Operational Resilience Act (DORA) is the EU’s answer to ensuring digital operational resilience in financial services. This wide-reaching regulation applies to over 22,000 financial entities and Information and Communication Technology (ICT) service providers operating within the EU. But what does achieving compliance with the EU’s vision for resilience in digital financial operations look like?
With its 79 pages of legal language and ICT requirements, DORA outlines a comprehensive framework that can be overwhelming at first glance. Breaking down the regulation into actionable steps can help simplify compliance.
What Is DORA, and Why Does It Matter?
The DORA (Digital Operational Resilience Act) is the EU’s regulatory framework for ensuring financial institutions can withstand, respond to, and recover from digital disruptions caused by ICT risks.
Unlike prior regulations, which treated ICT risk as part of broader operational risks, DORA directly covers financial institutions’ technological infrastructure, making it central to their overall risk management. Non-compliance can lead to significant fines, legal consequences, and increased scrutiny from EU regulators.
However, beyond avoiding penalties, the focus is securing operations and building trust with customers, investors, and partners. By complying with DORA, institutions can prove their ability to deliver reliable financial services, particularly amid the increased prevalence and sophistication of digital impersonation and other online scams.
Who Needs to Comply with the DORA?
DORA applies to various financial institutions, including banks, insurance companies, investment firms, payment service providers, crypto-asset services, and crowdfunding platforms. It also covers critical third-party ICT service providers that support these institutions. Importantly, non-EU companies operating in the EU must also comply with the DORA, ensuring that any entity involved in the EU financial ecosystem meets the same standards.
Failure to comply with this regulation can lead to severe penalties, including fines of up to 2% of global turnover or 1% of daily turnover. Executives and decision-makers could also face personal fines of up to €1 million if negligence or poor risk management is found to have contributed to a severe disruption.
Breaking Down the Key Requirements of The DORA
The DORA became law in January 2023, with its application starting in January 2025. However, compliance can lag for some businesses due to the complexity of implementing its requirements. After this date, businesses expanding operations to the EU must also promptly start on that compliance journey.
While a DORA Readiness Assessment can help organizations already making preparations identify gaps, a DORA Compliance Checklist (at the end of this article) is useful for those just starting out to set goals and prioritize actions—both essential steps for building digital operational resilience.
Regardless of where you’re at, meeting DORA’s standards requires a structured approach with key steps like:
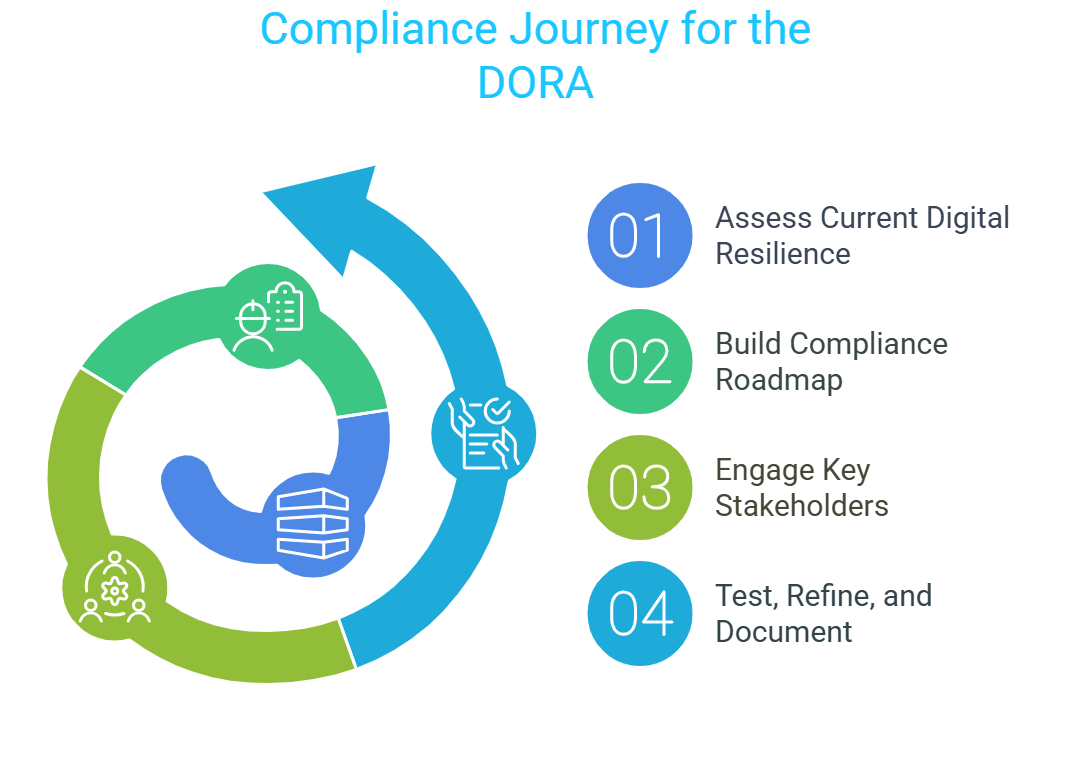
- Assessing your current digital resilience: Start with a gap analysis that checks how well your existing risk management, monitoring, and incident response processes align with the DORA.
- Building a compliance roadmap: Prioritize the changes that need to be made, from updating internal policies to strengthening cybersecurity defenses.
- Engaging key stakeholders: Compliance isn’t just an IT issue. Risk officers, compliance teams, and leadership all need to be involved.
- Testing, refining, and documenting: The DORA emphasizes continuous resilience testing and detailed record-keeping. Regulators will want proof that your institution isn’t just checking boxes.
The Five Main Pillars of The DORA
1. ICT Risk Management
Financial institutions have long been required to manage financial risks, but the DORA formalizes ICT risk management as a core regulatory obligation. You need to identify, assess, and mitigate risks related to cyber threats, system failures, and third-party service disruptions. This means maintaining a detailed risk register, enforcing strict access controls, and regularly updating policies.
2. Incident Reporting
The DORA introduces strict incident reporting rules that require your business to detect, classify, and report major ICT-related incidents within tight timeframes (for example, send an initial notification within 24 hours of an issue being detected). The clause ensures that regulators and, when necessary, affected customers get informed quickly so risks can be contained before they spread across the financial system.
3. Digital Operational Resilience Testing
The DORA expects you to prove your strategy for managing ICT risks works by conducting an operational resilience testing program. Independent parties, whether internal or external to your business, must carry out tests like vulnerability assessments, scenario-based cyber-attack simulations, and disaster recovery exercises. For larger institutions, testing must also include Threat-Led Penetration Testing (TLPT), where ethical hackers test your defenses under real-world conditions every three years at a minimum.
4. Third-Party Risk Monitoring
Financial institutions increasingly rely on external ICT providers for cloud services, cybersecurity, and data processing. Under the DORA, you are responsible for ensuring that your vendors are as resilient as you are. That means setting clear contractual obligations, conducting regular vendor-risk assessments, and ensuring third parties meet compliance standards.
5. Information Sharing
The DORA encourages financial institutions to collaborate by sharing threat intelligence and cyber risk insights. By pooling knowledge, the financial sector can better predict, prevent, and respond to emerging threats. While participation in information-sharing arrangements isn’t mandatory in the regulation, it’s still essential to the EU’s vision for digital operational resilience. Institutions that collaborate will likely have a stronger security posture and a faster response to industry-wide attacks.
These pillars are the foundation of DORA, ensuring that financial institutions don’t just react to threats but actively build resilience against them.

Step-by-Step Guide to Achieve DORA Compliance
Step 1: Deep-Dive Asset Mapping
Financial institutions operate complex IT ecosystems that often span multiple jurisdictions and integrate legacy and modern technologies. Understanding the interdependencies in these systems is crucial for identifying critical points where resilience needs to be strengthened.
Start by scanning your IT assets with automated discovery tools and configuration management databases (CMDBs). Identify and map everything—from on-premise hardware and software to cloud services and third-party dependencies. Catalog every component from endpoints to mainframes, and don’t forget any dependencies.
Step 2: Establish Governance for Digital Resilience
Establish a governance framework that integrates digital resilience into your business strategy. Start by appointing a Digital Resilience Officer or team responsible for DORA compliance, reporting to senior leadership. Define clear policies, roles, and responsibilities for resilience across all departments.
Create reporting structures for monitoring progress, enforcing measures, and addressing gaps so that you can make decisions quickly and consistently. Use this framework to align resilience efforts with overall business objectives.
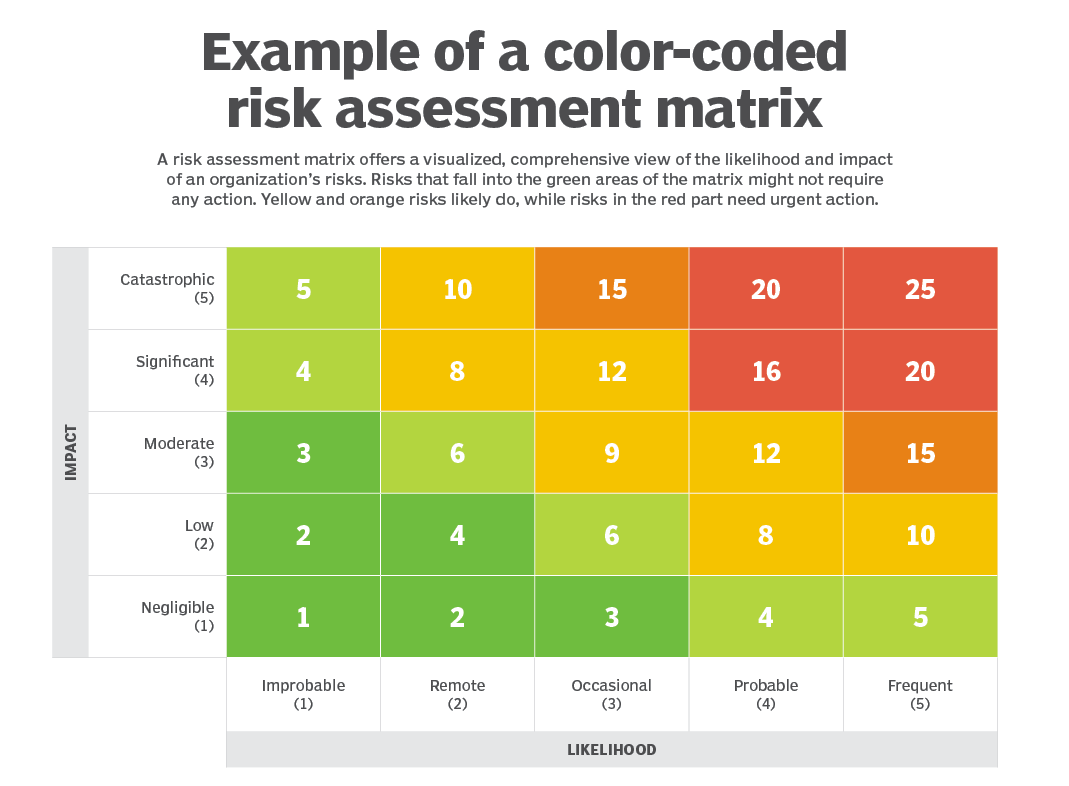
Step 3: Conduct a Risk Assessment
Use specialized risk assessment tools to identify and assess risks within your digital systems effectively. Automated vulnerability assessments, threat intelligence tools, and penetration testing can also help you uncover crucial gaps to address and account for at this stage.
However, it’s equally important to use your judgment and consider your business’s unique characteristics so you can tailor the assessments to unique needs or more pressing goals. Once risks are mapped, rank them based on likelihood and impact using risk-scoring tools.
Step 4: Build Your Incident Response Plan
Under the DORA, financial institutions must report major ICT incidents within strict timeframes. Develop a robust incident response plan detailing how your organization will detect, contain, and recover from cyber incidents. Designate an incident response team with clearly defined roles and ensure team members can access necessary tools like SIEM platforms and threat intelligence feeds.
Conduct regular tabletop exercises and simulated attack drills to test the plan’s effectiveness and identify gaps. Additionally, establish a communication protocol for promptly notifying regulators, stakeholders, and customers.
Step 5: Implement Real-Time Threat Monitoring
Cyber threats evolve quickly, and financial institutions need real-time visibility into their digital ecosystem to catch threats before they cause damage. For example, hackers could spin up a cloned version of your site in minutes and lure customers through phishing, smishing, and other methods.
Deploy real-time threat monitoring solutions that can detect impersonated websites, unauthorized access attempts, and other fast-moving anomalies. Memcyco is one such solution that detects and alerts financial institutions to website impersonation attacks in real-time.
Step 6: Compliance-Driven Vendor Management
Many financial services rely heavily on third-party platforms for critical operations, from cloud-based data storage to fintech solutions. Ensuring these vendors comply with DORA secures your service chain from vendor-related risks and solidifies trust with clients and regulators.
Re-evaluate your third-party vendor relationships through the lens of DORA compliance and set clear criteria and regular audits for third-party digital resilience. Lastly, contingency plans for vendor failures, such as alternative providers or backup processes, should be created to maintain operational continuity in case of disruptions.
Step 7: Create Compliance Reports and Documentation
EU Member State regulators overseeing DORA compliance expect extensive documentation that tracks your risk management, incident response, and compliance efforts. Maintain detailed records of risk assessments, incident reports, and resilience tests. Include version-controlled documentation to track changes over time, and store all compliance-related materials securely so your business is audit-ready anytime.
Step 8: Engage in Industry Collaboration for Intelligence Sharing
A key takeaway from DORA is the EU’s focus on the financial system’s digital interconnectedness and the potential for systemic risks caused by ICT incidents. In this context, sharing threat intelligence is crucial for strengthening digital operational resilience across the sector.
Join cyber intelligence networks, industry working groups, and EU-led threat-sharing initiatives. Establish secure channels to share anonymized attack data with regulators, your peers, and security firms so that valuable insights benefit the entire financial system.
Eliminate a Key Threat to Your DORA Compliance: Digital Impersonation Scams
DORA is driving a shift in how financial institutions approach digital resilience, emphasizing cybersecurity, operational continuity, and third-party risk management. However, one emerging challenge is the rise of digital fraud and website impersonation, which can undermine customer trust and financial stability.
Website impersonation scams and unauthorized access attempts pose risks that align with DORA’s ICT risk management and incident response pillars. Addressing these challenges requires real-time monitoring and proactive threat detection to safeguard digital financial services.
For financial institutions actively working on their compliance strategy, ensuring a strong defense against digital fraud is key.
Ready to improve your digital resilience?
![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)

















