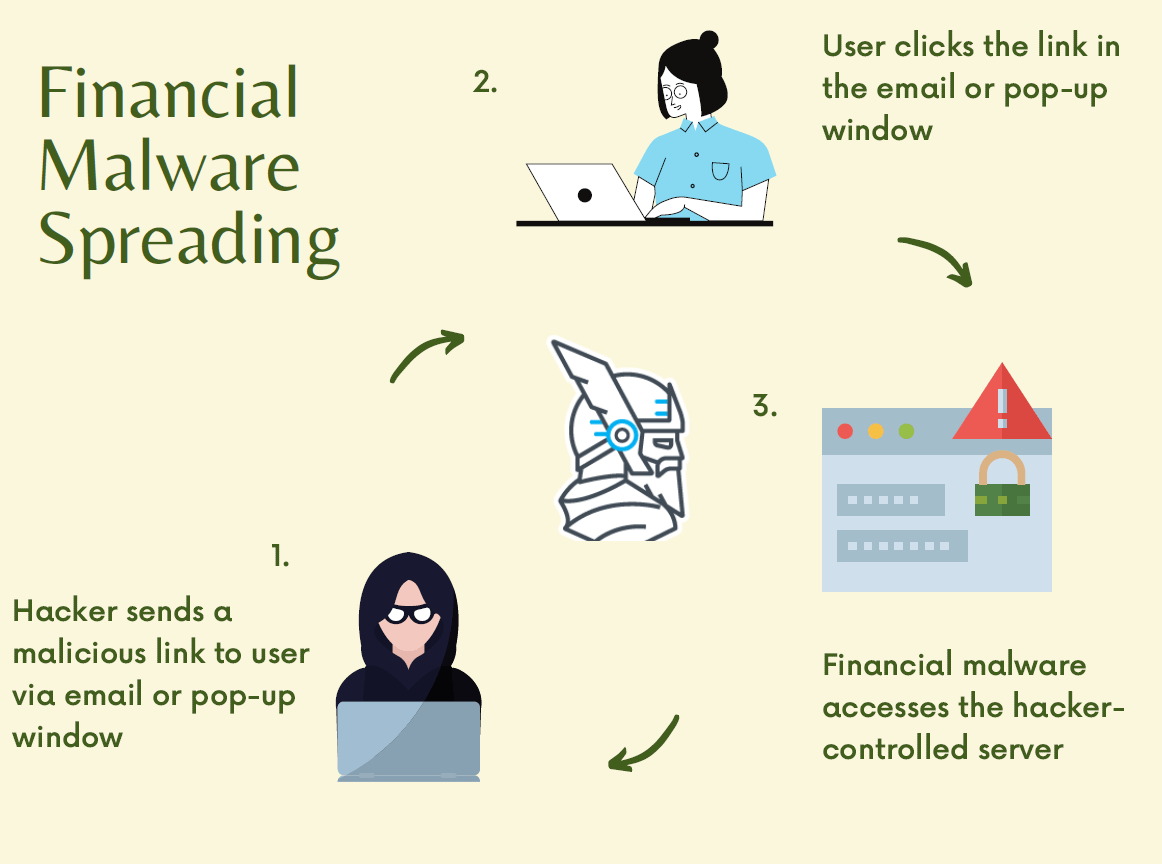
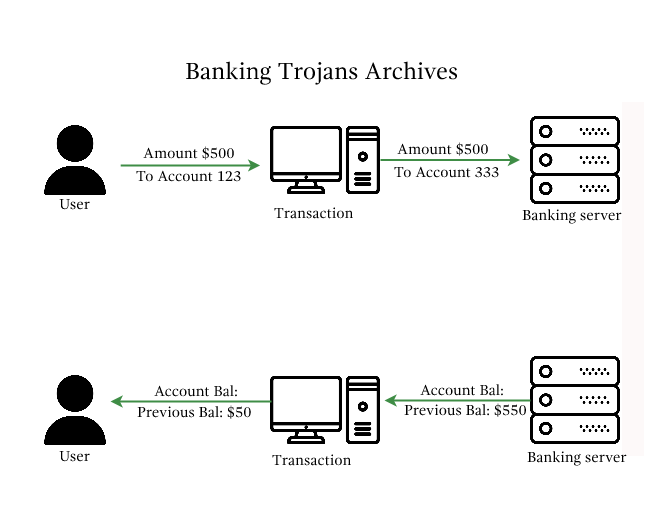
Imagine waking up one day and checking your bank records to find details of transactions you never made. This nightmarish situation can result from the Tiny Banker Trojan (Tinba) malware, which can steal banking credentials to funnel money to external accounts.
There has been a rise in such malicious and fraudulent activities worldwide over the past few years. According to a recent report, in Q2 2023 alone, 59,167 malicious installation packages were identified as related to mobile banking trojans.
With online financial security critical to businesses and individuals, equipping yourself with the knowledge and tools to defend against Tinba is essential. Here’s how to do it.
What is Tiny Banker Trojan (Tinba)?
The Tiny Banker Trojan, also known as Tinba or Zusy, is a malicious software program that specifically targets financial institution websites to steal banking information. It’s a more advanced and compact version of the older Banker Trojans, and is notable for its small size (which makes it difficult to detect) and powerful capabilities. Tinba operates by conducting man-in-the-browser attacks and network sniffing to hijack sensitive financial information from victims.
First discovered in 2012, Tinba made its initial mark by infecting thousands of computers in Turkey. After that incident, it became the smallest known Trojan, at only 20KB. Post-discovery, the Trojan’s source code was leaked online, leading to further propagation and evolution of the malware.
Tinba is particularly threatening to individuals, businesses, and financial institutions due to its ability to capture user inputs during online banking sessions stealthily. This enables it to steal a wide array of sensitive data, such as login credentials and credit card information, often through deceptive means like spam emails and malicious downloads.
How Does Tiny Banker Trojan Work?
The sophistication of Tiny Banker Trojan (Tinba) lies in its stealth and evasion techniques, which make it a formidable opponent in cybersecurity. The Tiny Banker Trojan uses various means to infiltrate the system, including:
- Phishing emails
- Malicious website links
- Malvertising (malicious advertising)
- Software package downloads
Given its tiny size, this malware can hide behind legitimate-looking files and stay disguised. It can also modify websites to disable warning messages to avoid early detection after infecting the applications.
Tinba uses two primary approaches to steal precious user information:
1. Man-in-the-Browser (MITB) Attack
In this case, Tinba uses form grabbing to capture the keystrokes before they are encrypted by HTTPS, stealthily acquiring sensitive user information.
2. Malicious JavaScript Code
Tinba can use JavaScript codes to mimic the legitimate banking website prompts after the user logs in, requesting additional information like social security numbers for identification and credit card details with tricky messages that may mislead the users.
Once the information is captured, Tinba relays this data to a remote command & control server managed by the attacker. It can hide its tracks from antivirus programs and encrypt its intermittent communications with the command & control server.
What are the consequences of Tiny Banker Trojan?
If Tinba infiltrates your system, you may face several adverse consequences, including:
- Financial Losses – Tinba aims to gather financial information, so you may face financial losses caused by unauthorized transactions.
- Legal Consequences – A data breach of sensitive financial information would pose legal challenges and regulatory penalties to companies for compromising customer data and violating regulatory compliance.
- Reputation Damage – A banking trojan attack would risk the company’s reputation, ultimately staining its reliability and decreasing digital trust.
How Can Tiny Banker Trojan (Tinba) Be Detected?
A sneaky and stealthy malware, Tinba hides itself well enough not to show the user any apparent signs of infiltration. But a few giveaways may indicate the possibility of your system being infected by one. These include:
- Irregularities in browser behavior, like unexpected pop-ups or requests for sensitive information when visiting banking websites
- Performance slowdowns
- Unusual changes in financial information and bank statements
- Changes in browser settings
If your organization is involved with financial and banking applications, implementing a proper data security management strategy for your business can help address the vulnerability issues that allow a Tinba attack before it happens.
What Can Be Done To Remediate Tiny Banker Trojan (Tinba)?
If you suspect your system is infected by the Tiny Banker Trojan, use the methods below to confirm your suspicions:
- Regularly update and run full antivirus scans.
- Monitor network traffic to check for unusual patterns that may appear when Tinba communicates with the command & control servers.
- Run regular security audits to manage attack surfaces, identify vulnerabilities and locate potential infections.
If it’s confirmed that your system is under attack:
- Isolate the infected devices from the healthy devices to prevent further complications.
- Go on safe mode, conduct a full scan through reliable antivirus software, and remove the Trojan.
- Change all credentials that may have been compromised.
- In case of a severe infection, restore the system with a complete system backup from a point before the infection and seek professional help.
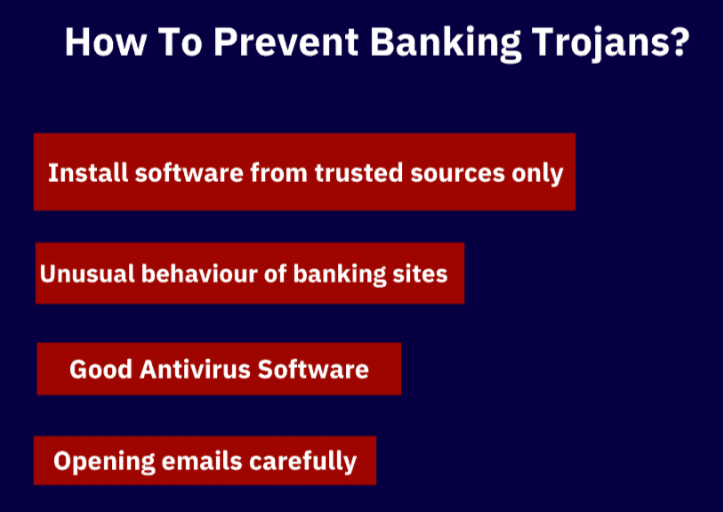
7 Practical Steps To Protect From Tiny Banker Trojan
1. Beware of Phishing Emails
Phishing emails are one of the most common ways banking trojans can find their way into your system. You can minimize malware attack risks by implementing advanced email filtering technologies like:
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
- Domain-based Message Authentication, Reporting, and Conformance (DMARC)
These protocols help verify the authenticity of email senders, reducing the likelihood of phishing emails reaching end-users.
The below code shows an example SPF record in DNS. It specifies that only hosts designated in the “_spf.example.com“ domain are authorized to send emails on behalf of the domain.
v=spf1 include:_spf.example.com ~all
2. Monitor for Website Behavior Irregularities
Look for any unusual behavior in financial and banking applications to identify Tinba beforehand. Try the following:
- Use Memcyco to prevent website spoofing attacks. Cybercriminals use these duplicate, fraudulent websites to spread malware like Tiny Banker Trojan and to steal Personally Identifiable Information (PII). Memcyco provides real-time protection against website spoofing and brandjacking. The end-to-end solution ensures immediate attack detection and alerts, in-depth forensics, and innovative mitigation measures.
- Monitor user sessions for unusual patterns.
- Use anomaly detection algorithms.
- Implement rate limiting on critical actions.
- Verify the geolocation of users during login and transactions.
3. Secure Native Devices
Ensure you deploy comprehensive security solutions to all native devices, such as mobile, laptop, and desktop. Here’s what to do:
- Enable full-disk encryption using tools like BitLocker (Windows), FileVault (macOS), or device encryption (Android/iOS).
- Implement MDM solutions like MobileIron or VMware AirWatch for centralized device management.
- Establish a robust patch management system.
- Enforce the use of biometric authentication methods (fingerprint, facial recognition).
4. Regular Data Backups
Regularly backup your system’s sensitive data using an external device or a reliable cloud storage service. It will help prevent data loss even if Tinba denies your access to the application data.
Best practices to follow:
- Implement automated backup scripts using rsync, Robocopy (Windows), or cloud-native backup solutions.
robocopy “C:\Path\To\Source” “D:\Path\To\Backup” /MIR
- Use protocols like SSL/TLS for data in transit.
- Enable two-factor authentication (2FA) for access to cloud storage accounts.
- Keep offline backups in addition to cloud backups.
5. Comprehensive Antivirus and Security Solutions
Antivirus is a safety net that protects your system from many external threats. However, traditional antivirus solutions primarily use signature-based detection mechanisms to identify known malicious code patterns.
With the increasing threats of cyber attacks, you need to adopt a more comprehensive solution with new features, such as:
- Behavior-based threat hunting and detection
- Sandboxing for dynamic analysis
- Memory exploit prevention
- Fileless malware detection
- Zero-Day vulnerability protection
- Digital Brand Watermark – Memcyco offers Proof of Source Authenticity (PoSA), a forge-proof authenticity watermark shown to every website visitor that proves that the content they’re seeing and interacting with is genuine and safe.
6. Web Application Firewalls (WAF)
Add an extra layer of security to your web applications by implementing Web Application Firewalls (WAF). These can help you fight against website attacks that could introduce Tinba to your system.
When implementing a WAF:
- Configure rule-based security policies within the WAF to detect and block specific patterns.
- Implement request filtering and parameter validation.
- Integrate the WAF with SIEM solution to centralize log data and enhance visibility.
- Customize WAF configurations to address application-specific risks and requirements.
7. Strong Password Policies
Using a strong password is a must for any account. The complexity of your password determines how easy or difficult it is for attackers to guess it using brute force attacks, credential surfing, and dictionary attacks.
Here are tips for a robust password policy:
- Enforce periodic password rotations.
- Prevent users from reusing recent or commonly used passwords.
- Set up account lockout policies to temporarily lock accounts after a designated number of failed login attempts.
- Use robust password hashing algorithms and salting techniques like bcrypt or Argon2.
import bcrypt
Hash a password
password = “user_password”
hashed_password = bcrypt.hashpw(password.encode(‘utf-8’), bcrypt.gensalt())
Verify a password
if bcrypt.checkpw(“user_password”.encode(‘utf-8’), hashed_password):
print(“Password is correct”)
else:
print(“Password is incorrect”)
Fortify Your Financial Frontline with Memcyco
Tiny Banker Trojan presents a formidable challenge to online banking and payment system security. By following these seven practical steps, you’ll significantly increase your organization’s security perimeter against it and other cyber threats. But with the constant evolution of the threat landscape, it’s best to combine these steps with sophisticated security tools to ensure maximum protection.
That’s where tools like Memcyco come in. It provides real-time protection against website spoofing and brandjacking attacks that use fake websites to trick customers into entering their credentials. It’s the only solution that addresses the critical “window of exposure” between when a fake site goes live and when it is taken down. Memcyco issues real-time Red Alerts to users visiting spoofed websites and provides organizations with complete visibility into the attack, allowing them to take remediating actions quickly.
Don’t wait for Tinba to Tinba to infiltrate your system from a spoofed website. Get started with Memcyco today to protect your financial data and your customers.