Phishing attacks are a huge threat. They prey on human trust and manage to trick even the most tech-savvy users. A successful attack on a company’s customers can weaken it financially, create compliance issues, and cause long-lasting reputational damage.
Scammers have stolen over $1 trillion globally in just the past year – a staggering figure that rivals the GDP of some nations. While organizations of all sizes have their customers targeted, high-profile companies often dominate the headlines – for good reason. With their extended user bases, the ripple effects of an attack can be catastrophic.
In 2025 and beyond, it’s crucial to consider these real-life examples to understand how attackers conduct their intricate schemes and define the level of protection you need.
Key Methods Used in Phishing Attacks
All phishing attacks involve tricking users into sharing sensitive information by pretending to be someone or something else. However, attackers use various methods and channels to conduct these attacks.
Email Phishing
Email phishing involves sending mass emails to trick recipients into clicking malicious links or sharing personal details. While some scam attempts are evident due to spelling errors, poor grammar, or generic greetings, some emails are expertly crafted to mimic legitimate communications.
Smishing
Smishing is like phishing but in the form of text messages. It often masquerades as urgent communications, tricking users into clicking on malicious links or sharing sensitive details.
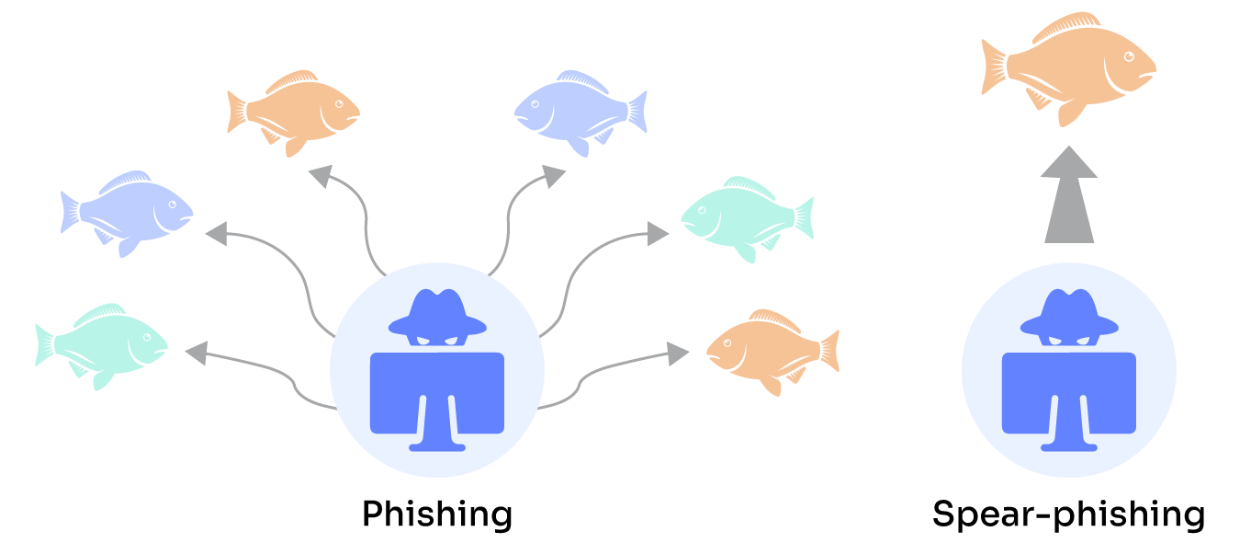
Spear Phishing and Whaling
Attackers use spear phishing to target specific individuals or groups, often utilizing details from prior breaches to craft personalized emails that trick recipients into complying with their demands. Whalers focus on company executives, mimicking legal or financial communications to extract critical corporate information.
Vishing
Vishing scams involve attackers posing as trusted representatives over the phone. They may claim, for example, to fix a virus on your computer only to steal your payment information or install malware.
Web Spoofing
Attackers can create fake websites to lure victims into entering credentials and payment details. These authentic-looking sites mimic the designs of well-known sites, often using fake adverts and emails to entice visitors.
Social Media Phishing
Hackers leverage social media platforms like Facebook or LinkedIn to impersonate trusted friends, colleagues, or brands. They send direct messages or comments containing malicious links or fake offers, luring users into sharing credentials or personal data.
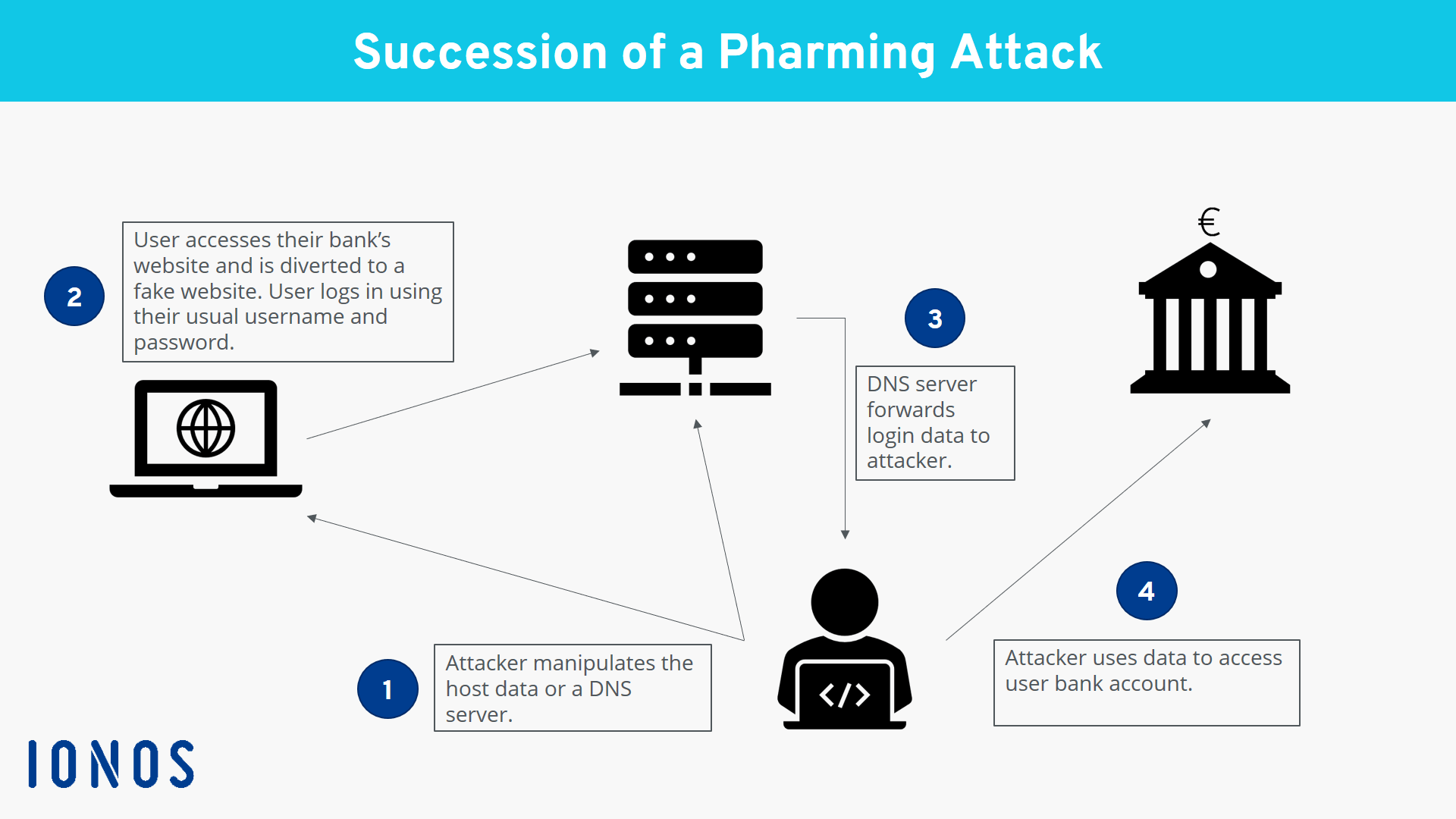
SEO and Pharming Attacks
Unlike direct message scams, these methods are based on redirecting users to fake sites. SEO poisoning manipulates search rankings to direct users to fake websites resembling legitimate ones, and which rank above their genuine counterparts. Once on these fake websites, users are enticed to sensitive information. Pharming takes this further by compromising the DNS cache on a victim’s device, redirecting them to fraudulent sites even if they type the correct URL.
Why Phishing Attacks are More Dangerous Than Ever
Phishing attacks have become more sophisticated, driven by easy access to phishing tools and AI’s ability to automate and scale attacks. For example, AI takes just a few seconds to generate emails that seem totally legit (as opposed to “traditional” phishing emails, with typos and weird syntax, which look suspicious up front).
In addition, AI and machine learning (ML) power techniques like deepfake and synthetic identities, which blur the line between real and fake. These techniques make it harder to distinguish authentic communications from fraud, putting even cautious users at risk.
Lastly, tools for launching phishing attacks are so widely available that they have become a commodity, even propelling the creation of a new market segment: Phishing-as-a-Service (PhaaS). Dark web marketplaces now offer ready-made phishing kits with templates, tools, and step-by-step guides, allowing even novices to execute highly effective campaigns.
The 5 Biggest Phishing Attacks of 2024
1. Change Healthcare Attack
In February 2024, Change Healthcare fell victim to an attack that impacted over 100 million users of the company’s services. ALPHV/BlackCat carried out the breach by gaining access to Change Healthcare’s systems through compromised login details harvested by phishing.
Once inside the system, bad actors launched an attack and then disrupted critical healthcare operations, including billing, insurance claims, and pharmacy services. This led to nationwide outages, severely impacting the healthcare sector. Despite UnitedHealth paying a $22 million ransom in March, the attackers disappeared without returning the stolen data.
The breach exposed medical data for approximately one-third of the U.S. population, causing significant financial and reputational damage to Change Healthcare. While the full economic impact is still under investigation, the attack has raised serious concerns about cybersecurity in the healthcare industry, particularly within clinics leveraging sensitive tools like embryo grading systems. Such systems rely on secure data storage and transfer; any compromise, like the one faced by Change Healthcare, could expose critical patient information.
2. Pepco Group Attack
In February 2024, Pepco Group lost around €15.5 million in a phishing attack that targeted the company’s Hungarian branch. Bad actors crafted and sent phishing emails designed to facilitate fraudulent money transfers.
The attack is thought to have been executed using advanced AI tools to craft convincing messages without spelling errors and mirroring the tone of previous correspondence. The similarities with authentic communications made it difficult for victims to recognize the scam and reject money transfer requests.
Pepco Group, which owns the Pepco, Dealz, and Poundland brands, operates 3,600 stores across 19 European countries, serving over 30 million customers each month. While the Pepco Group executives stated that no customer was affected, investigations are ongoing, and the lost funds may never be recovered.
This potential case of Business Email Compromise (a highly targeted and sophisticated phishing attack where cybercriminals use hacked email accounts to trick employees) isn’t uncommon. According to the FBI, global BEC losses have totaled over $50 billion across nearly 278,000 incidents in the past decade.
Pepco Group said it had taken the necessary steps to investigate and respond to the incident. It conducts a group-wide review of all systems and processes to secure the business more robustly.
3. Fake Bank Payment Notification Scam
In March 2024, a phishing campaign sent out phishing emails disguised as bank payment notifications, which actually contained an archive file that activated a loader for the information stealer and keylogger Agent Tesla.
The loader used obfuscation, polymorphic behavior, and advanced techniques to bypass antivirus defenses, including patching the Windows Antimalware Scan Interface (AMSI). It then deployed Agent Tesla to transfer sensitive data via SMTP using a compromised email account.
The loader was written in .NET and included two variants with distinct decryption routines. It dynamically retrieved and decoded a XOR-encoded Agent Tesla payload. The campaign leveraged stealth techniques to avoid detection and make tracing difficult.
4. StrelaStealer Campaign
Between June and August 2024, the StrelaStealer phishing campaign targeted over 100 U.S. and European organizations. It affected sectors ranging from finance and government to manufacturing.
Attackers sent out phishing emails with ZIP attachments containing a JavaScript file that deployed the StrelaStealer. Once downloaded, this file extracts email credentials from popular email clients like Microsoft Outlook and Mozilla Thunderbird, posing significant risks to organizational security.
StrelaStealer has been active since 2022. Its main objective is to steal email login data, which can be exploited for further attacks. Email attachments are constantly updated to evade detection, using advanced obfuscation and anti-analysis techniques.
This ongoing campaign highlights the critical need for robust cybersecurity measures. User education on phishing threats, implementation of advanced email filtering solutions, and regular security training to mitigate the risks associated with such attacks are all vital.
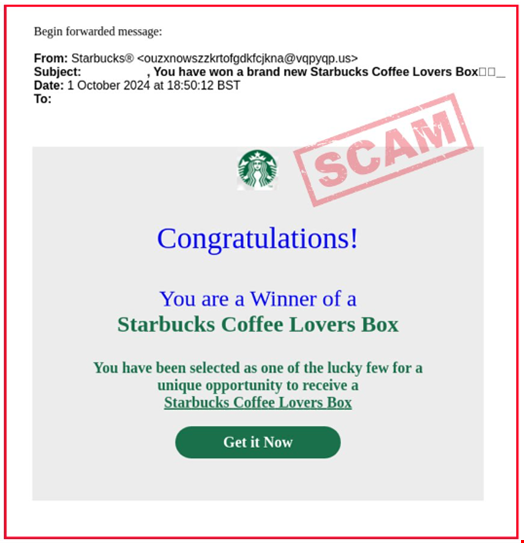
5. Starbucks Phishing Email Campaign
In October 2024, coffee aficionados were warned about emails purporting to be from the retailer offering customers a free Starbucks Coffee Lovers box. Action Fraud, the UK’s national fraud and cyber reporting center, received over 900 reports about the scam in two weeks. The emails contained links to steal personal and financial information.
A similar fake Starbucks Coffee Gift offer made the rounds earlier in the year. The email claimed that a friend had ordered coffee at the company and had selected the recipient for a special gift. In this case, the email contained the banking Trojan ZeuS, which would install itself and, if opened, run an instance of the hard-to-remove rootkit.
Security analysts quickly reminded customers that organizations like Starbucks seldom request sensitive information via email and that a healthy level of skepticism towards offers that seem too good to be true is a good defense.
Protecting Against the Next Wave of Phishing Attacks in 2025
Phishing attacks have become more sophisticated and pervasive, evolving from simple scams to highly targeted, large-scale campaigns. The incidents highlighted in 2024 show just how far-reaching and devastating these attacks can be, from healthcare and finance to global retail brands. As attackers increasingly leverage AI, automation, and new methods like web spoofing and PhaaS, and with the growing impact of new regulations focusing on protecting customers, companies must proactively look for more sophisticated solutions.
Memcyco uses AI and its proprietary nano-defender and device DNA technologies to detect when attackers impersonate your website. This helps prevent large-scale phishing scams that mislead users into visiting such sites, which can lead to further attacks like account takeover (ATO) scams.
With real-time protection and complete visibility into the attacker, the device they are using, and any potential victim that has visited the fake site since it went live, Memcyco gives you the complete picture of the threat you are facing and empowers you to mitigate it quickly before it impacts more users. Prevent large-scale phishing attacks at the source. Learn more here.



















