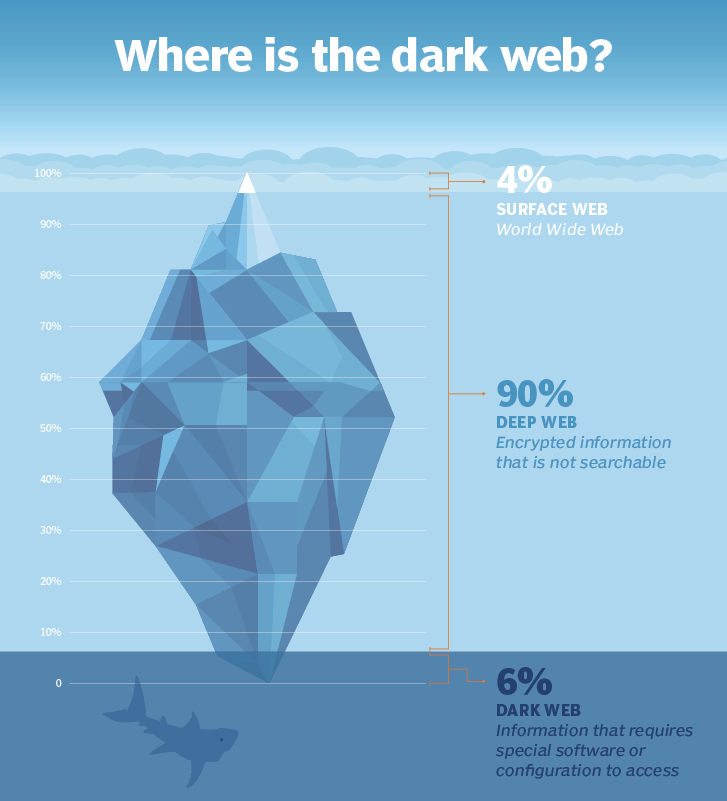
Your customers’ stolen data could be for sale right now – and you might not even know it. The dark web is a thriving, shadowy marketplace where fraudsters trade credit card numbers, account details, session cookies, and even entire identities. On average, there were more than 2.5 million daily visitors to the dark web in 2023, showcasing the scale of this underground economy.
Knowing that your customers’ data might be lurking on the dark web, you may want to go out and find it. However, while the surface web is easily searchable and accessible, the dark web thrives in anonymity and requires unique tools to navigate its maze of encrypted networks. In order to find the data you’re looking for, you will need to employ dark web monitoring. This is a set of tools that scan hidden forums, marketplaces, and chatrooms for leaked data tied to your business or customers.
How Dark Web Monitoring Works
Anonymity and privacy make the dark web a haven for illicit activities, including selling stolen data, counterfeit documents, and malware-as-a-service. While there are legitimate reasons for someone to want to anonymize their online activities on the dark web (like whistleblowing), over 56% of dark web content is illegal.
The surface web is easy to navigate, but the dark web requires unique browsers like The Onion Router (Tor) for that. Tor routes traffic through multiple volunteer-operated nodes (“relays”) across the world. It uses a process known as onion routing, which encrypts data in layers, like the layers of an onion, to mask the origin and destination of internet traffic.
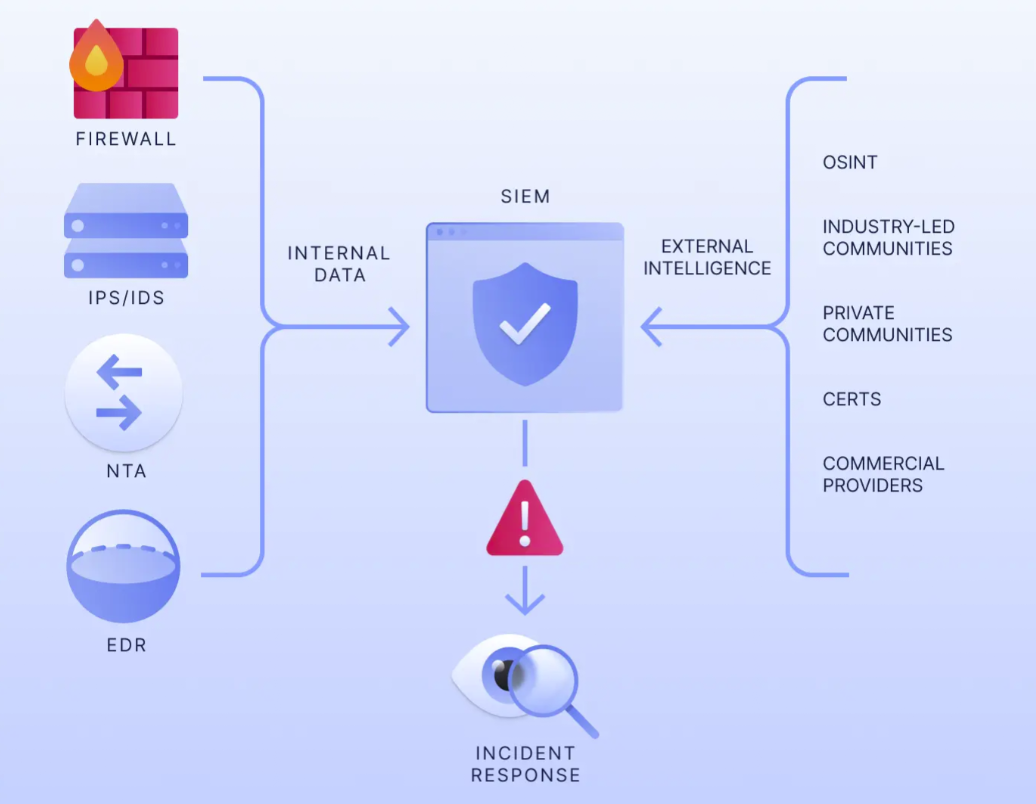
Dark web monitoring surmounts these obstacles and is able to conduct detailed searches and scan hidden web sections for threats and compromised assets related to your company or customers. It uses automated tools and human intel to sift through forums, black markets, and encrypted communication channels like IRC or Telegram. Cybercriminals use these channels to trade stolen credentials and leaked data, often obtained from luring people into fake versions of your site.
The monitoring tools are powered by algorithms that identify and extract relevant data, such as compromised credentials, personal identifiable information (PII), and discussions of planned cyberattacks. Machine learning models further analyze extracted content for context, filtering out noise and prioritizing threats based on relevance and potential impact.
The scope of monitoring includes
- Compromised usernames and passwords
- Social security numbers and home addresses
- Stolen credit card details
- Session cookies and authentication tokens
- Internal documents, trade secrets, source code
- Mentions of your company’s name or employees
Why Should InfoSec Teams Invest in Dark Web Monitoring?
The stats and headlines paint a grim picture of the scale of problems the dark web presents. As an example, stolen credit card details with balances of $5,000 cost potential buyers just $110 on the dark web. Large-scale breaches constantly keep flooding the dark web with new data: a massive 2024 breach of online ticketing company Ticketmaster saw 3 billion Americans’ social security numbers and other personal info posted on a dark web forum.
In the face of these threats, dark web monitoring solutions are crucial. Here’s how they can help:
1. Incident Response Preparation
To improve readiness, you can integrate dark web monitoring feeds into your incident response plan. By identifying compromised data early, incident response teams can trigger containment and remediation actions before attackers exploit a breach. For example, finding leaked credentials for sale on a dark web forum allows for immediate password resets or account lockdowns to prevent further escalation.
2. Cut Financial Risk
When you catch breaches early – before cybercriminals exploit stolen information from your systems or customers – you drastically reduce the potential financial fallout. Dark web monitoring helps you identify sites or forums where data is for sale and prevent costly fraud, legal repercussions, and fines, by intervening earlier. While it’s not a fully proactive stance (since dark web monitoring doesn’t stop the data from being stolen in the first place), it does help limit the damage of the scams people fall for (like inputting information into fake versions of your site) or the opportunistic ways threat actors hack into your systems.
3. Insights for Security Improvements
With insights from dark web monitoring, you’re always learning what cybercriminals are after and how they operate. Being in the know allows you to refine your security defenses and focus on the areas or types of data most likely to be targeted. The intelligence gathered is critical to your cyber resilience framework, enabling your organization to continuously adapt and improve security measures to stay one step ahead of attackers.

4. Competitive Differentiation
For e-commerce and financial services companies, offering dark web monitoring as part of a customer protection package can be a unique selling point. Protecting customers from potential fraud by detecting their compromised data before it’s exploited demonstrates extra care and vigilance about their data, which can set your business apart in a competitive market.
5. Fraud Prevention
Protecting against fraud is mission-critical for e-commerce and financial services companies. Dark web monitoring helps detect the sale of stolen credit card numbers, bank details, and compromised customer accounts. By monitoring for specific financial data and fraudulent activity, you can flag and respond to fraud attempts, protecting financial assets and customer transactions from being compromised.
Implementing an Effective Dark Web Monitoring Strategy
1. Customizable Monitoring Profiles
Tailor your monitoring parameters to fit your company’s specific risks and assets. Rather than relying on generic monitoring, configure profiles that track particular keywords, domains, customer data, and proprietary assets relevant to your industry. For e-commerce or financial services businesses, this could include tracking for mentions of payment gateway credentials, fraud techniques, or even brand mentions in underground forums. Customization ensures you catch relevant threats while avoiding data overload.
2. API Integration for Automated Response
Integrating dark web monitoring tools with your existing security stack via APIs ensures that threat intelligence is actionable faster. For example, when dark web monitoring discovers compromised credentials or sensitive data, an automated workflow can trigger actions like password resets, account lockouts, or multi-factor authentication enforcement. This automation speeds up response times and reduces the burden on your security team.
By integrating dark web monitoring into a SIEM system, you can ensure alerts automatically correlate with other events to get deeper context on potential attacks. Splunk and Elastic Stack are popular SIEM tools that allow seamless integration with external monitoring feeds to automate and enhance threat detection.
3. Regular Threat Intelligence Updates and Feeds
Dark web environments evolve rapidly, with new forums, marketplaces, and communication channels emerging frequently. As quickly as law enforcement manages to infiltrate an underground marketplace, new ones pop up. Ensure that your dark web monitoring solution continuously updates its intelligence feeds and keeps pace with the latest trends in cybercrime. Regular updates improve the relevance and accuracy of the detected threats, and your team needs the freshest information to act on them.
4. Incident Playbooks for Discovered Leaks
Develop incident response playbooks specifically tailored to dark web-related discoveries. When dark web monitoring tools or services find stolen credentials or sensitive data, your team should have predefined steps to follow, such as notifying affected customers, revoking access, or filing compliance reports. Clear playbooks reduce response times and ensure that actions align with compliance regulations and your overall business priorities.
5. Cross-Channel Monitoring – Not Just the Dark Web
Last but not least – while the dark web is a significant cyber threat landscape, it’s not the only place where data leaks happen. A comprehensive monitoring strategy should also include scanning for threats across various web channels, social media platforms, Pastebin sites, and even public cloud storage that could expose your data. By widening your monitoring scope, you can catch threats that might initially surface in more accessible parts of the internet before they move deeper underground.
The Missing Piece in Your Dark Web Defense Strategy
Throughout this article, we’ve explored the hidden world of the dark web and its impact on your business, customers, and brand. We discussed the critical role of dark web monitoring tools in uncovering stolen data. But here’s the truth: even the best dark web monitoring strategy might not be enough. In many cases, by the time you find stolen data lurking for sale on a dark web market or being discussed by threat actors on a forum, the damage might already be done.
When discussing impersonation-based attacks, many businesses mistakenly believe that the combination of scan-and-takedown services together with dark web monitoring offer complete protection. But think about it – while these solutions provide insights into threats, they have a hard time stopping the fraud from unfolding in real-time. They won’t necessarily block a brand scam the moment it hits or prevent a customer from falling victim to account takeover (ATO) fraud before they even realize they’re under attack.
That’s where Memcyco’s real-time digital impersonation protection comes in. Memcyco enables you to detect, counter, and disrupt fraud as it happens, rendering dark web data almost irrelevant to countering this type of fraud. Learn more about Memcyco.



















