The bad news – if you’re wondering about the DORA compliance date, it already passed on January 17th 2025. The good news? If you’ve been too busy to even think about the EU’s Digital Operational Resilience Act, it’s not too late to score some quick compliance wins. This DORA compliance checklist is your blueprint for establishing not just compliance, but checks and balances for maintaining it.
While The DORA largely consolidates pre-existing guidelines and frameworks, its enforceability introduces a new level of risk and accountability. It will come as no surprise to anyone reading this that financial institutions that fail to meet its standards risk hefty fines, increased regulatory scrutiny, and reputational damage. But that’s not happening, right?
To help, we’ve created a practical checklist outlining the three foundational steps of DORA compliance. The full checklist – covering all aspects of the regulation – is available for download below.
For those of you with a racing pulse who are just discovering The DORA, let’s start with the key basics.
What Is The DORA and Why Does It Matter?
The Digital Operational Resilience Act (The DORA) is an EU regulation designed to standardize and strengthen financial institutions’ resilience against ICT-related incidents. It applies to banks, insurance firms, investment companies, and third-party ICT providers servicing the financial sector.
Why Should You Care?
- Firstly, the fines are significant – Non-compliance can result in penalties of up to 2% of total annual worldwide turnover or €1 million for individuals.
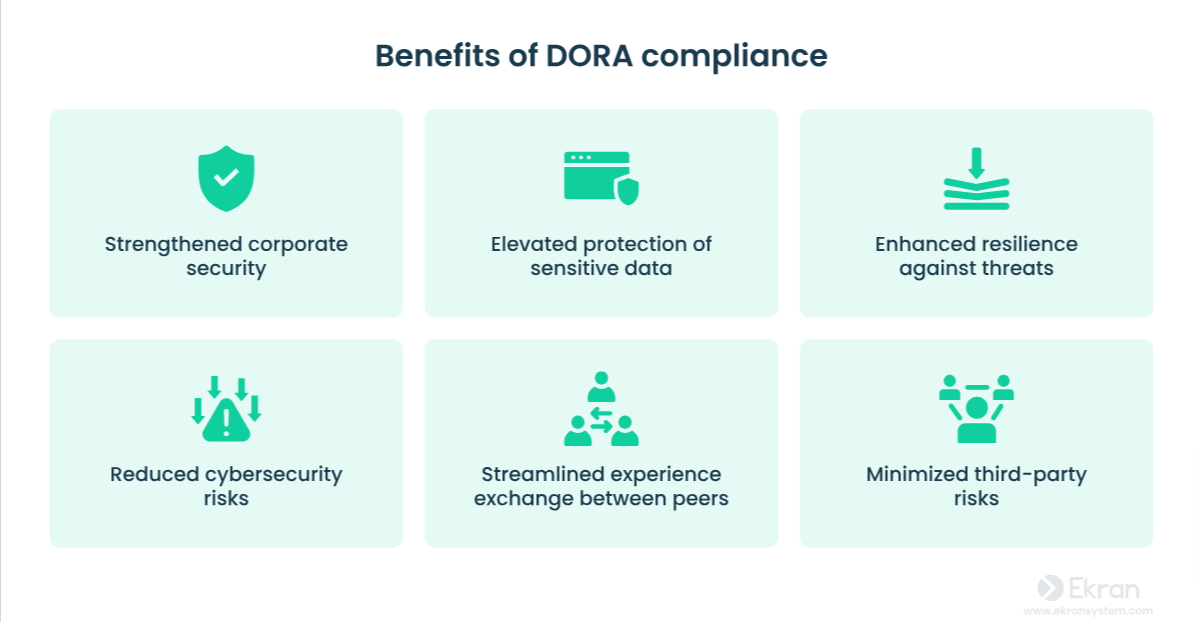
- But the DORA is about more than just avoiding fines – ultimately, the incoming regulation is aimed at helping business maintain business continuity.
- Digital trust takes years to build – But only seconds to lose after a single incident. For customers, partners and investors, cyber resilience is a trust signal. Failing to comply could drive clients and investors elsewhere.
- DORA is stricter than previous frameworks – Unlike voluntary guidelines like GDPR, The DORA imposes mandatory operational resilience requirements, making it a proactive, rather than reactive, regulation.
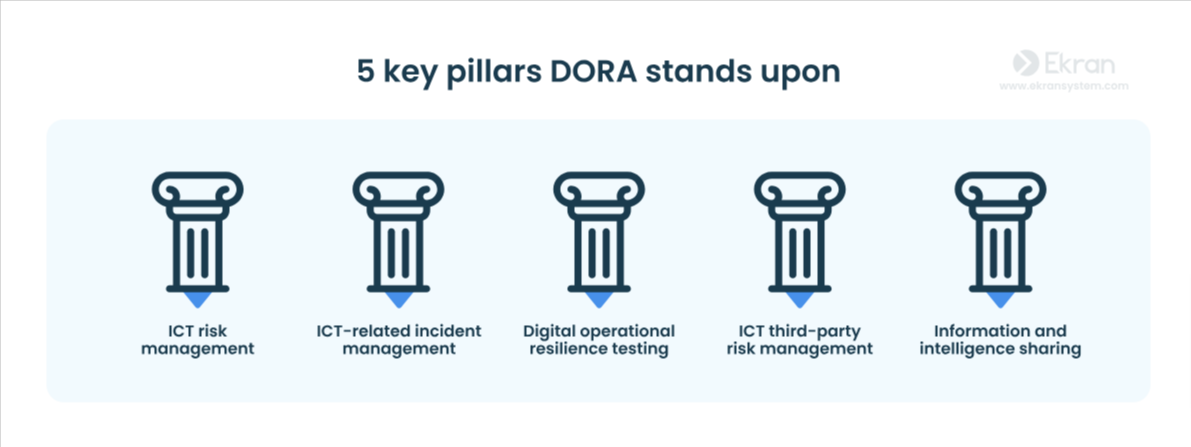
What Are the Key DORA Compliance Areas?
✔ ICT Risk Management – Establishing robust risk frameworks
✔ Incident Reporting – Standardizing reporting procedures and response timelines
✔ Resilience Testing – Conducting regular penetration testing
✔ Third-Party Risk Oversight – Ensuring ICT providers meet DORA standards
Now, let’s break down the first three critical compliance steps.
 Source
Source
The DORA Compliance Checklist [Downloadable]
To get the full DORA compliance checklist – with extra guidance pitfalls to avoid – click the download banner below. Here are the first three checklist items summarized.
1. Establishing a Strong ICT Risk Management Framework
- Develop a formal risk management framework with clear policies and procedures.
⚠️ It’s worth emphasizing that a policy on paper isn’t enough – enterprises must prove risk management is actively enforced through audits, testing, and real-time monitoring. - Assign governance responsibilities at the senior management level.
⚠️ Here, board involvement will be critical – many compliance failures stem from a lack of senior oversight, so try to advocate for DORA compliance as a C-level priority. - Implement a continuous improvement cycle based on audits and incidents.
⚠️ Expect to encounter third-party dependencies – financial entities must ensure that outsourced ICT providers also follow the same risk management framework.
2. Incident Detection and Reporting Protocols
- Implement standardized procedures for identifying and reporting ICT incidents.
⚠️ “Significant incidents” must be clearly defined – not every cybersecurity issue requires regulatory reporting, but failing to report serious ones can result in penalties. Ensure your anti-phishing tools are able to quickly provide comprehensive reports. - Define incident reporting timelines and ensure compliance with regulatory authorities.
⚠️ Time is a factor – regulators expect swift reporting. Ensure an incident response plan is in place and frequently tested. - Set up real-time monitoring for proactive risk mitigation.
⚠️ Data quality matters – vague or inconsistent reports increase regulatory scrutiny. Standardized reporting formats should be clear, concise, and detailed.
3. Digital Resilience Testing and Continuous Monitoring
- Conduct penetration testing, vulnerability scans, and scenario-based stress tests.
⚠️ Testing isn’t one-size-fits-all – not every organization has the same risk profile. Ensure testing is tailored to the company’s infrastructure and threat exposure. - Ensure annual testing for all critical ICT systems.
⚠️ Avoid “check-the-box” compliance – regular testing should be more than a formality. It should actively improve security posture. - Use test results to prioritize remediation efforts and strengthen resilience.
⚠️ Think carefully about third-party testers vs. internal testing – The DORA encourages using external penetration testers for unbiased evaluations.
DORA Myths Debunked: Fact vs. Fiction
Now that you’re familiar with the basics, it’s worth busting some common misunderstandings about DORA compliance.
Myth 1: “The DORA doesn’t apply to financial institutions based outside the EU.”
Reality: Wrong. Even financial institutions located outside the EU must comply if they provide services to EU-based clients or operate within the EU financial ecosystem.
Myth 2: “The DORA is just a recommendation, not a legal requirement.”
Reality: The DORA is now legally binding across the EU financial sector.
Myth 3: “If we follow existing cybersecurity frameworks, we’re already compliant.”
Reality: While The DORA integrates pre-existing guidelines, it has stricter enforcement mechanisms, so adherence to related cybersecurity frameworks isn’t enough.
Myth 4: “DORA compliance only applies to banks.”
Reality: The regulation affects all financial entities, including insurance firms, investment companies, and critical third-party ICT providers.
Myth 5: “The DORA only focuses on cybersecurity.”
Reality: While cybersecurity is a core component, The DORA covers broader operational resilience, including third-party risk management, incident response, and business continuity planning.
Myth 6: “Once we achieve compliance, we’re done.”
Reality: DORA requires ongoing compliance, including regular audits, testing, and continuous monitoring to stay ahead of evolving threats.
Fast Track Your DORA Compliance
DORA compliance isn’t just about avoiding fines and checking boxes – it’s about business continuity and ensuring your financial institution is prepared for operational disruptions, cyber threats, and regulatory scrutiny.
Here are your next steps:
- Download the full compliance checklist (via the banner above) to cover all remaining regulatory requirements.
- Book a demo and discover how Memcyco delivers unique real-time data you can use to establish, prove and sustain DORA compliance.
- Conduct an internal audit to assess current compliance gaps.
- Assign a compliance lead responsible for overseeing DORA implementation.
With the right strategy, technology, and guidance, you can achieve DORA compliance sooner rather than later, without delay and complexity.