Today’s cyber criminals deliver waves of highly coordinated, advanced, and frequent attacks. Endpoint attacks have become complex multi-stage operations, and the threat landscape has become complicated and vast. Characterized by massive data leaks, expensive ransomware payouts, and substantial regulatory penalties, detecting these attacks before they lay waste to an organization has become a critical challenge.
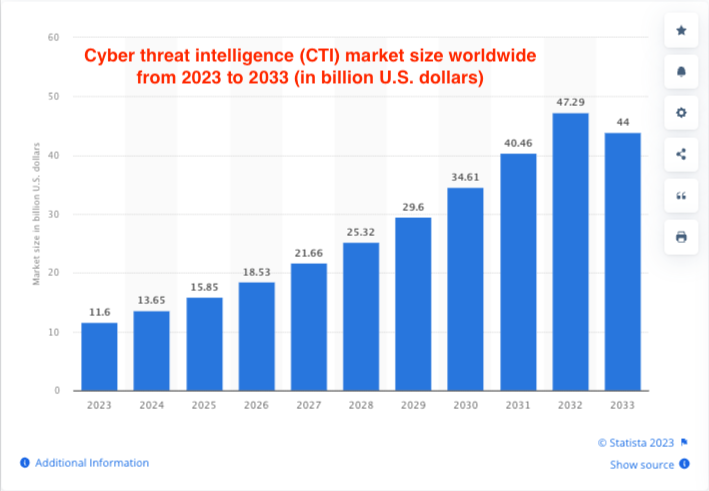
Organizations can achieve effective threat detection by collecting and analyzing threat intelligence that reveals potential malicious activities in your network. The problem is so acute that the market for cyber threat intelligence is expected to grow from $11.6 billion in 2023 to an astounding $44 billion in the next ten years.
Fortunately, there is another, multi-faceted solution. Using proper threat detection techniques, businesses can take proactive action before malicious actors launch attacks that cause significant damage. In this post, we’ll survey eight techniques you need for a comprehensive threat detection program and how to employ them to keep attackers guessing.
What is threat detection?
Threat detection refers to the methods, technologies, and processes employed to identify and analyze threats or malicious activities within an environment, such as a computer network. This can include monitoring for unusual system behaviors, analyzing network traffic for suspicious patterns, and identifying known malware or vulnerabilities.
Threat detection is crucial for cybersecurity as it enables you to proactively identify and respond to cyber threats, minimizing the potential impact of attacks and safeguarding sensitive data, personal information, and digital assets.
A proactive approach to detecting threats helps maintain business continuity and avoids significant operational disruptions. As an integral component of a comprehensive cybersecurity strategy, threat detection seamlessly integrates with response and mitigation processes, ensuring that threats are identified and promptly addressed.
8 Threat Detection Techniques to Keep Cyber Attackers Guessing
Technique 1: Proof of Source Authenticity (PoSATM) from Memcyco
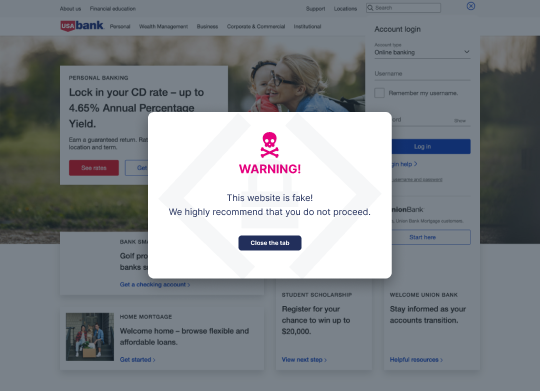
Businesses in all industries are fighting the scourge of website spoofing and brandjacking attacks. 50% of cybercrime in the USA alone stems from brand impersonation, and suffering this kind of attack can be fatal to your organization: 81% of consumers would cease engaging with a brand online after an attack.
Memcyco fills this gap with its out-of-the-box solution based on agentless PoSATM technology, offering automatic Zero Day protection and real-time detection that pinpoints website spoofing attacks at their inception. It grants organizations full attack details for transparency and recognizes unusual activities. Memcyco enhances security by:
- Sending an immediate Red Alert to users accessing a counterfeit site.
- Offering comprehensive insights into the attack.
- Authenticating your websites with a unique, customizable watermark.
- Being an agentless solution, it spares your customers from any registrations or installations.
- Ensuring a hassle-free setup—just a few lines of code bring value within hours.
Memcyco’s strength lies in halting fraud before its onset, thus preventing any initial customer engagement. Crucially, Memcyco protects during the critical period between the attack’s beginning and the fraudulent site’s removal—reducing data breaches and financial risks while aiding in regulatory compliance. It’s a solution sure to frustrate cyber criminals and keep them guessing while protecting your brand.
Technique 2: Anomaly Detection
Organizations can deploy tools and techniques to identify abnormal behavior based on an established pattern in a system. Any user or system events deviating from an established baseline pattern are treated as anomalies in this case. Businesses can use anomaly detection techniques to identify critical incidents, such as the following:
- Cyber-attacks
- Network errors
- System malfunctions
- Technical bugs
- Unexpected business-altering changes from insiders
You can install anomaly detection systems that alert security analysts of unusual changes from established patterns. This capability allows your organization to assess security risks, resolve gaps, and enhance security posture before data exposure occurs. Better still, the solutions can take automated actions, such as blocking a user session or shutting down an application.
Besides preventing attacks, anomaly detection offers logs and reporting capabilities vital for regulatory compliance and data privacy laws. Data anomalies may not always signify critical issues, but it’s worth inspecting them to understand why a deviation occurred. Quality training sample data can improve anomaly detection techniques to avoid relaying fake alerts while capturing all glaring outliers.
Technique 3: Signature-based Detection
Signature-based detection is a foundational detection technique in intrusion detection systems (IDS). The technique allows IDS systems to detect unauthorized access or malicious activities in the network by identifying known threat indicators.
With signature-based detection systems in your network, you can examine traffic, compare it to known signatures, and send alerts when a match is made. You are likely using this threat detection technique if you have antivirus and other endpoint security tools as part of your cybersecurity solutions.
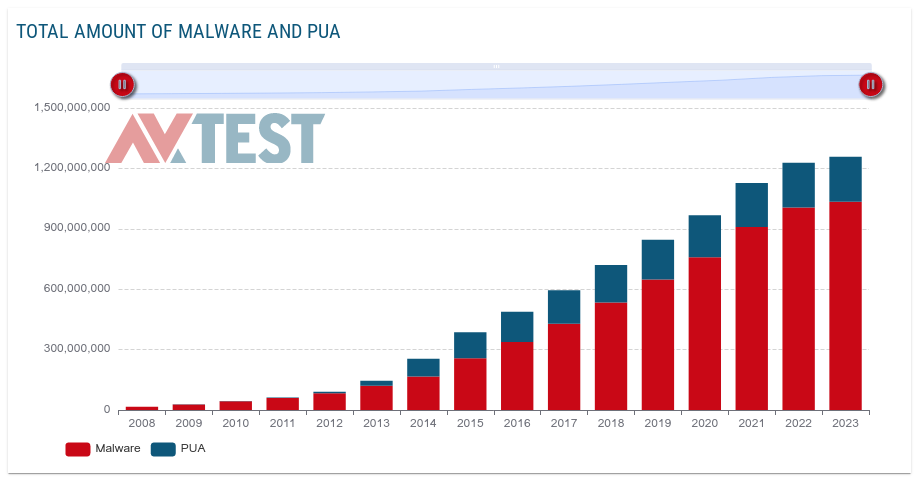
Combining the signature-based detection method with other techniques is beneficial due to some limitations, such as being unable to detect emerging and unknown threats. For illustrative purposes, security analysts register 450,000 new malware and potential unwanted applications (PUA) daily.
Technique 4: Heuristic Analysis
Threat detection may also require you to examine code for suspicious features, a process called ‘heuristic analysis.’ The technique is helpful in malware detection since it allows security analysts to decompile suspicious programs and compare them with known malware code recorded in a heuristic database. The program is flagged as a possible threat if its source code matches a virus in the database to a predefined percentage.
Security teams can deploy dynamic heuristic methods to identify unknown cyber threats. The technique isolates suspicious code inside a sandbox to simulate and observe what happens if it runs. The process sends an alert if the code demonstrates suspicious behavior, such as overwriting files, self-replication, mutability, or deleting files.
You can deploy heuristic analysis to detect commands that deliver payloads disguised within Trojan horse programs or worm viruses. The technique also allows you to detect a classic computer virus that remains resident in memory after execution or a malicious program that decrypts itself when running to avoid detection by signature-based scanners.
Technique 5: Sandboxing
Sandboxing involves running and analyzing code in a safe, isolated area in your network. For better results, it is good practice to implement a sandbox that mimics the actual end-user operating environment.
You can use sandboxing to test untrusted code without causing damage to your systems, as well as detect and respond to threats before they enter your network. The technique is useful when testing new third-party software before implementing it. You can also deploy sandboxing to evaluate new code for potential vulnerabilities before taking it live.
Using the sandboxing technique, security analysts can quarantine and eliminate zero-days and advanced persistent threats (APTs). But while sandboxing is an effective threat detection method, some advanced malware can evade detection by delaying execution or altering behavior. Therefore, implementing a multi-layered security approach is needed for effective protection.
Technique 6: Honey Pots and Honey Nets
Honeypot is an intriguing security technique that features virtual or intruder traps to lure hackers. Security analysts set up an intentionally vulnerable system that allows attackers to exploit flaws straightforwardly. Meanwhile, the security team can study the threat actors’ tactics, techniques, and procedures to enable them to improve their cybersecurity posture.
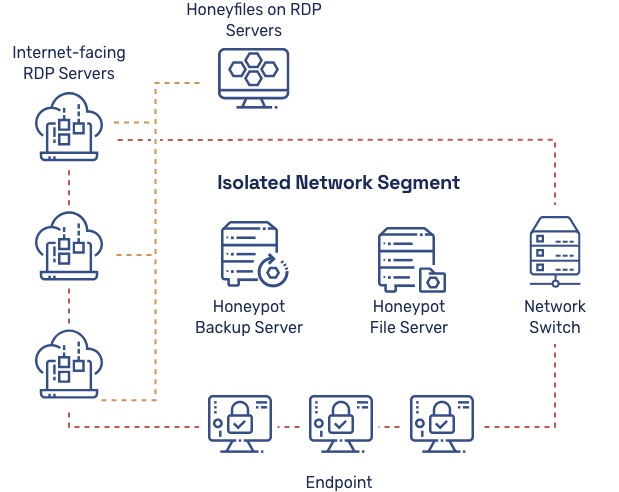
The diagram above shows an example of a honeypot and honey files system for detecting ransomware actors. You can apply honeypots and honeynets to any infrastructure, including software, endpoints, networks, routers, and servers.
Technique 7: Endpoint Detection and Response (EDR)
The saying “time is money” rings truer in today’s evolving threat landscape. The faster you detect, respond, and recover from potential threats, the better, and EDR is your go-to technique for both automated detection and response rolled into one.
EDR is an integrated security technique blending real-time endpoint event monitoring and logging with rule-based analysis and response capabilities. Notably, EDR solutions employ a high degree of automation, allowing security analysts to rapidly detect and respond to threats. Implementing EDR in your network helps you achieve the following security capabilities:
- Monitor and log endpoint events and activities, including potential threats
- Analyze data to distinguish normal behavior from anomalies
- Prioritize threats based on their likely impact
- Automatically send alerts and respond to threat patterns
- Generate reports and forensic data for further research on suspicious activities
Technique 8: Artificial Intelligence and Machine Learning
Before AI and machine learning, IT systems relied only on rule- and signature-based threat detection systems to identify tested and known threats like malware and viruses. Unfortunately, these traditional security approaches are limited in detecting evolving and sophisticated attacks. Security analysts experienced delayed detection and missed security incidents.
Now, AI and machine learning can analyze vast data to identify patterns that might indicate any malicious programs present, allowing your organization to detect and respond to threats quicker and more accurately.
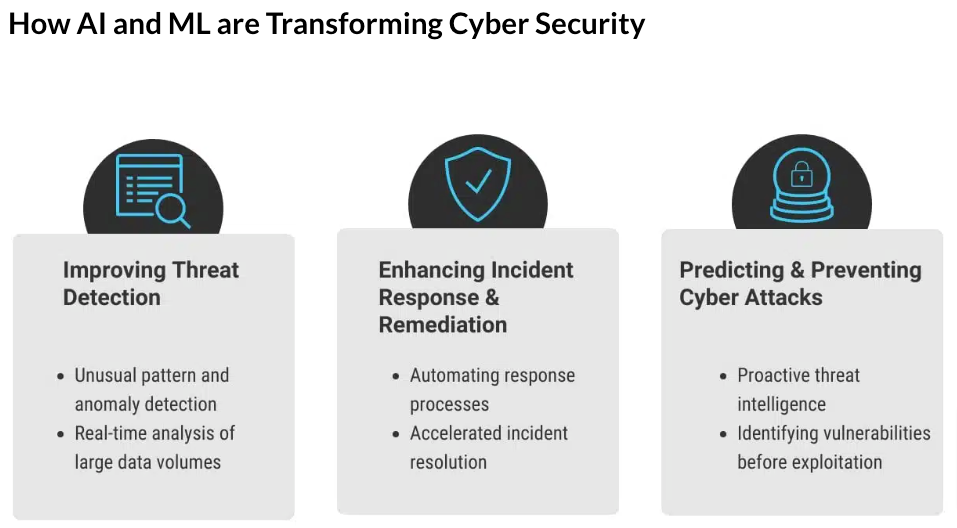
AI and machine learning bring a paradigm shift in cybersecurity by providing proactive detection, behavioral analysis, pattern recognition, adaptive learning, and real-time response. The technique learns from new data to adapt to changing threat patterns, allowing your security posture to stay ahead of cybercriminals.
This method excels at identifying complex attack patterns in diverse data sources. You can automate real-time response by instantly alerting and countering suspicious activities.
Overcoming Challenges in Threat Detection
Cybersecurity is increasingly becoming a game of cat and mouse between threat actors and security analysts. Even with threat detection techniques in place, threat actors are advancing and using more sophisticated attacks over time.
Due to the dynamic nature of attacks, you’ll need to continuously update threat intelligence in your business to protect your digital assets successfully. You need to know emerging channels and techniques hackers may use and leverage the information to prevent harmful damage to your organization.
Ultimately, understanding the threats that put your business at risk is vital as it allows you to determine the techniques, tools, and processes that identify, assess, and mitigate attacks unfailingly—like Memcyco.
Contact us today to schedule a complimentary demo and learn how we defend your brand.



















