If there’s one fraud statistic worth dwelling on as Fraud Awareness Week 2024 passes, it’s this – in the past year, scams of one type or other siphoned $1 trillion globally, according to the Global Scam Alliance’s State of Scams Report 2024. But this figure only scratches the surface of cybercrime’s total global cost, projected to reach $10.5 trillion in 2025, according to Cybersecurity Ventures, the world’s leading source of cyber research.
These numbers paint a clear picture: fraud is no longer just a risk to manage; it’s a full scale innovation-driven industry complete with illicit suppliers selling off-the-shelf scams – just Google ‘phishing-as-a-service’ or ‘FraudGPT’.
This is the scale of the challenges that scam-prone industries now face and all the fraud awareness in the world is worth little unless backed by the right action. Not least thanks to the threat of AI-enhanced scams and creeping regulation increasingly holding enterprises accountable for customer fraud losses.

Fraud Awareness Has Triggered Action. But Newly Adopted Approaches Remain Flawed and Ripe for Disruption
Fraud, security, and cyber teams don’t need reminding of the threats, or the urgent need to reinforce fraud prevention measures. What’s less obvious is how flawed those measures actually are.
Here are three familiar (and pervasive) anti-fraud measures that are ripe for disruption:
1. Scanning and Takedown
Scanning and takedown services are a staple of fraud prevention strategies, often deployed to identify and remove fraudulent websites impersonating legitimate brands. However, their limitations are striking:
- Reactive by design: Scanning and takedown services focus on mitigating the impact of scams after they’ve already occurred, offering zero pre-takedown protection. Businesses and customers remain completely exposed during the critical window when damage is most likely.
- Only partial coverage: Scanning tools can’t detect all offending sites, particularly those hosted on obscure domains or constantly shifting infrastructure. Many scams are still detected by users themselves, not automated systems.
- Lack of investigable data: Takedown services don’t provide actionable intelligence on how fraud campaigns are executed, limiting organizations’ ability to learn and adapt.
The Result: While takedowns temporarily weaken threats, they fail to offer the real-time visibility and protection businesses need to stay ahead of fraud.
It’s worth emphasizing that takedown is a useful tactic – one that Memcyco automates. But, for the reasons mentioned it’s flawed without real-time visibility and protection from phishing-related scams while they’re active.
It’s also worth knowing that Memcyco detects digital impersonation attempts, fake site URL registration, and fake-site-live events, all in real-time without scanning.
2. Multifactor Authentication (MFA)
MFA has become a cornerstone of digital security, adding an additional layer of protection for user accounts. But it’s far from infallible:
- Friction for legitimate users: Repeated authentication requests disrupt the user experience, creating customer frustration.
- Vulnerabilities to advanced attacks: Social engineering tactics, such as Man-in-the-Middle (MitM) attacks, allow fraudsters to bypass MFA by intercepting authentication codes in real time.
- Not a phishing solution: MFA may protect against brute-force logins, but it offers little defense against phishing campaigns that trick users into voluntarily sharing their credentials.
The Result: While MFA provides essential guardrails, its vulnerabilities and the user friction it introduces highlight the need for more advanced, seamless solutions.
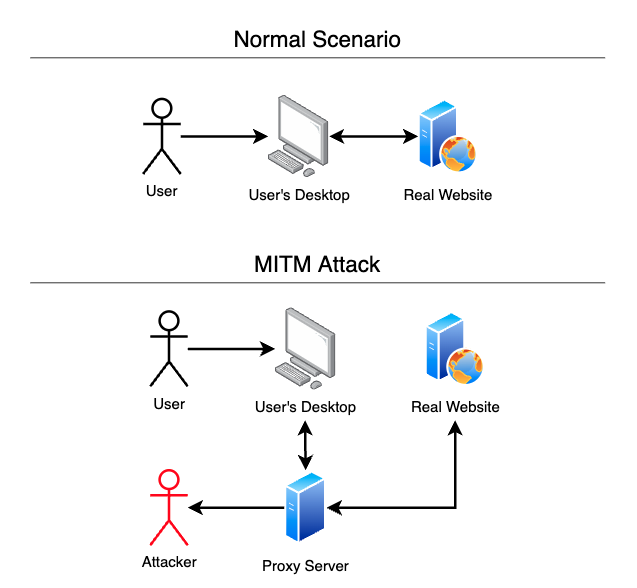
3. Suspicious Login Verification
Many businesses implement suspicious login verification to identify and challenge anomalous login attempts. While this can help flag potential Account Takeover (ATO) attempts, it comes with significant drawbacks:
- High false positives: Behavioral algorithms often misclassify legitimate users as suspicious, leading to unnecessary disruptions and reduced trust.
- Blind to phishing attacks: These systems focus solely on user behavior, offering no protection against scams where fraudsters deceive users into handing over credentials.
- Reactive, not predictive: Suspicious login verification triggers after login attempts, meaning it cannot predict or preempt ATO attacks.
The Result: Businesses operate under a false sense of security, leaving critical gaps in their defenses that fraudsters are quick to exploit.
From Flaws to Fixes: Re-Thinking Traditional Anti Fraud Measures
The flaws in traditional fraud prevention measures represent risk gaps and, where there are gaps, there’s opportunity for innovation. Each of the approaches discussed (Takedown, MFA and suspicious login verification) offer safeguards with low insight that burden the user. As we discussed, they can also be bypassed.
Memcyco’s agentless solution helps enterprises add a comprehensive, frictionless layer that focuses on pre-emptive, real-time visibility, frictionless protection, and proactive disruption.
Here’s how:
From ‘Detection’ to ‘Pre-emption’
With the unprecedented frequency, sophistication and cost of phishing-related scams, fraud mitigation is now about pre-empting where, when and how events like customer credential theft and ATO will occur. Memcyco’s device analytics not only turns a pre-emptive posture into a daily standard; it also provides a level of precision above and beyond competitor equivalents.
Here’s how it works:
Accurate Device ID Attribution: Memcyco assigns each device a unique ID, avoiding the overlaps common in competitors’ solutions (e.g., multiple devices sharing the same ID).
- Separate Monitoring of Devices, Users, and Relationships: Unlike systems that equate a device to a user, Memcyco independently tracks:
- Suspicious or malicious devices: Devices with a history of anomalous or malicious behavior remain flagged, even if they are later associated with new users or different contexts.
- Dynamic device-user relationships: Memcyco analyzes the relationship between devices and users, monitoring shifts in behavior that may indicate risk. For instance, if a trusted user logs in from a flagged device, the system raises an alert.
- Trusted and untrusted connections: Devices and users are continuously evaluated within their specific contexts, ensuring that risk assessments adapt as behaviors and associations change
Contextual Decisions: Memcyco’s device analytics elevates proactive fraud pre-emption further by continuously evaluating device behavior and risk profiles. For instance:
- Flagging malicious devices: If a trusted user logs in from a device previously flagged for malicious behavior, the system raises an alert, ensuring risks are addressed before fraud occurs.
- Real-time risk adjustments: A device’s historical behavior dynamically influences its risk profile, enhancing fraud detection beyond static login-based triggers.
The Advantage: These capabilities empower businesses to take preemptive actions against phishing attacks, reinforcing both ATO and anti-impersonation protection by identifying threats before they escalate.
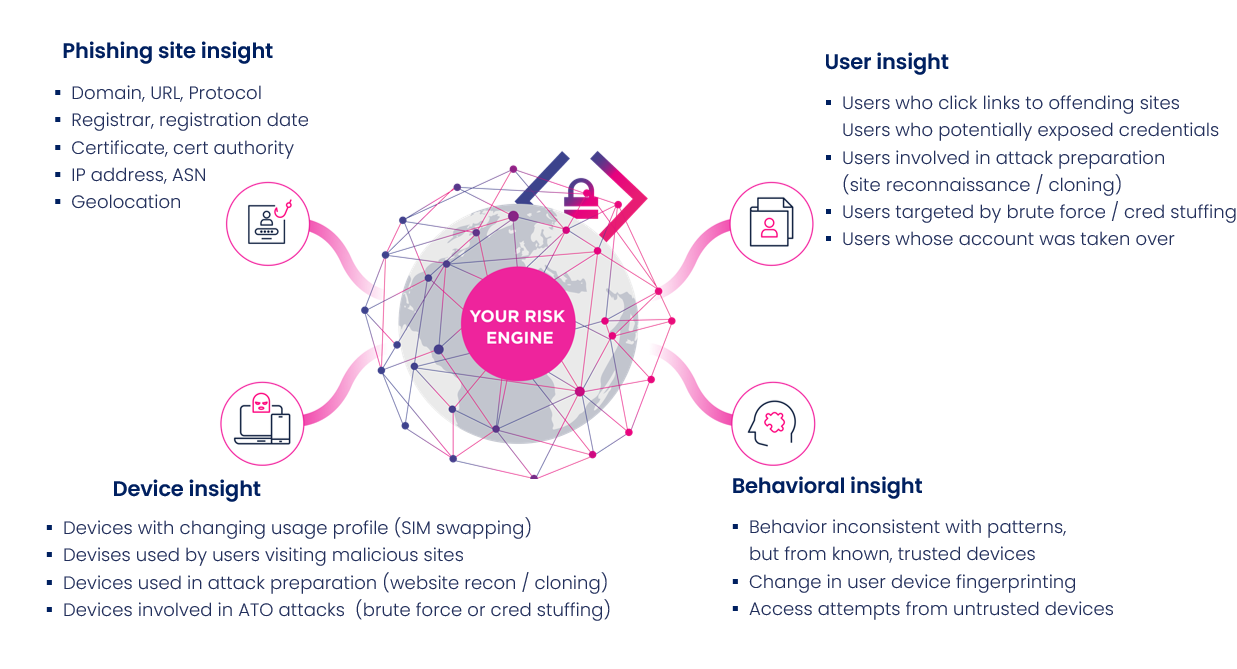
Additionally, Memcyco continually feeds real-time digital impersonation attack data into fraud risk engine environments, enriching the accuracy of predictive models with each passing attack.
Memcyco’s Risk Engine Enrichment
Pivoting to Disruption as a Strategy
Memcyco goes beyond detection to actively disrupt fraud operations, making scams less profitable and harder to execute:
Memcyco employs decoy data as a strategic tool to disrupt fraud operations at their core. Here’s how it functions:
- Creation of Decoy Data:
- Memcyco generates realistic but entirely fake marked credentials or information that mimic real user credentials or card data. The decoy data is marked in the same way as stolen marked money that’s traceable.
- These decoy data (decoy credentials or decoy card data) are intercepted on impersonated phishing sites or during credential harvesting or card data theft attempts.
- Threat Actor Engagement:
- When attackers interact with the decoy data, they believe they’ve successfully compromised valid credentials or card data.
- Fraudsters may attempt to reuse these credentials in automated systems (e.g., credential stuffing attacks), wasting their resources and effort.
- Detection and Monitoring:
- When fraudsters use the decoy data to attempt to log into accounts or commit card-not-present fraud, Memcyco picks up the signal, flagging the fraudster’s activities for further tracking.
- These interactions provide insights into attack methods and fraud attempt patterns, enhancing broader fraud prevention strategies.
- Active Disruption:
- As fraudsters attempt to use decoy data, they experience repeated failures in compromising real accounts and are actively locked out of the legitimate website, effectively neutralizing their campaign.
- Over time, the cost and effort associated with these attacks increase, deterring further activity.
- Automated Takedown Initiation: Memcyco’s automation significantly reduces the operational lifecycle of phishing sites, providing a faster response than traditional takedown services.
The Result: Fraudsters face mounting obstacles and diminishing returns, forcing them to abandon campaigns or refocus their efforts elsewhere.
Beyond Fraud Awareness Week: Gear Up for All–Year- Round Customer ATO Pre-emption, with Memcyco
Fraud Awareness Week has always been about highlighting the risks and encouraging action, but this year, it’s time to go further.
Book a demo to discover how Memcyco’s real-time capabilities and proprietary technology is helping global enterprises cut tens-of-millions in annual incident-related costs.



















