Picture this: a critical security breach has exposed your company’s data. Your IT team scrambles to identify the compromised device but needs a clear picture of all the laptops, servers, and mobile devices connected to your network. Without one, your systems and reputation are at risk.
Unfortunately, this scenario isn’t just hypothetical. The sheer volume of IT assets—from laptops and servers to mobile devices and cloud applications—has exploded in recent years. But with that increase in size, there’s a dramatic increase in risk. A recent study found that the amount of assets increased by 133% in 2023, but the number of security vulnerabilities increased by a staggering 589%. This tangled web poses a significant challenge: how can you secure what you can’t fully see?
Here’s where asset discovery tools become a game-changer. By shedding light on your entire IT ecosystem, these tools empower businesses to navigate the digital landscape confidently, laying the groundwork for robust cybersecurity, streamlined compliance, and efficient resource management.
What are asset discovery tools?
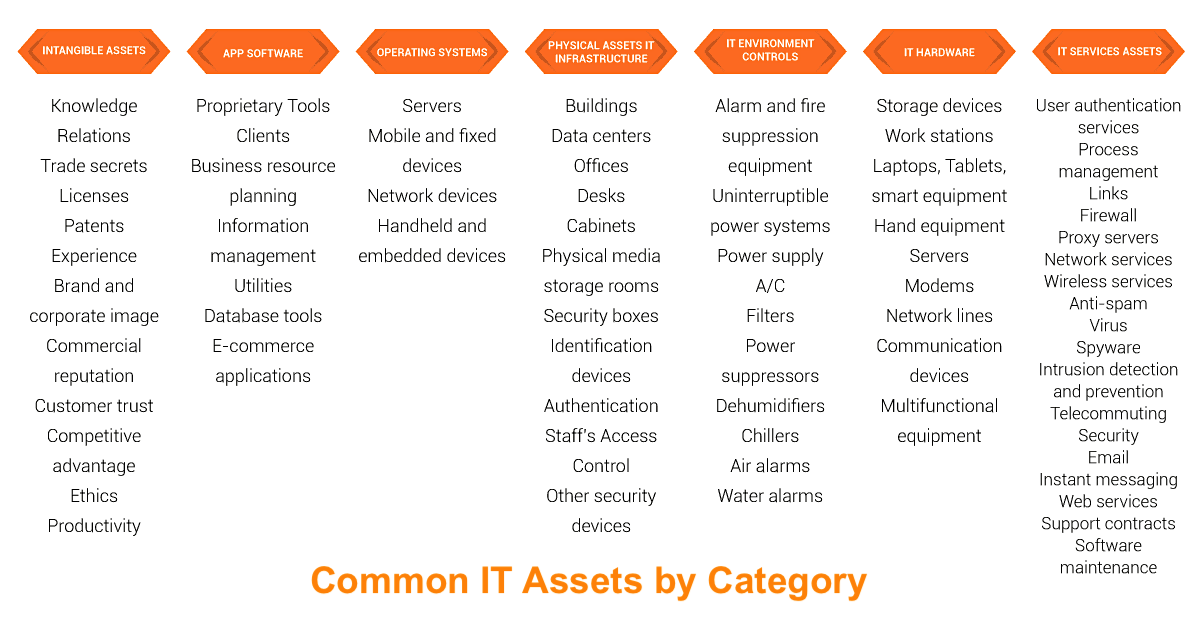
Asset discovery tools are digital solutions that help IT teams identify, catalog, and monitor all the IT assets—software and hardware—connected to the organization’s network. These tools enable enterprises to be aware of every asset that can compromise the system’s security or pose a cyber threat. In the current tech-driven ecosystem, it’s essential for organizations to continuously discover and monitor IT assets that are either archived, in use, or need upgrades.
Scanning a company-wide network to detect and map devices can be complex, time-consuming, and resource-intensive. Asset discovery tools are configured to scrape through your network to spot IT assets, including pre-installed software and SaaS products.
Types of Asset Discovery Tools
There are two main types of asset discovery tools:
Active Discovery Tools utilize various methods to scan your network to identify devices and assets. These include:
- Ping sweeps: Sending ping requests to every IP address on your network to see which ones respond.
- Agent deployment: Installing a lightweight software agent on devices that can report information about the device and its configuration.
- WMI and SNMP queries: Using industry-standard protocols to query devices for information about themselves.
Passive discovery tools collect information about assets from existing network traffic using techniques like:
- Network traffic analysis (NTA): Monitoring network traffic to identify devices and applications that are communicating.
- Log analysis: Analyzing log files from various network devices and systems to identify connected assets.
- DNS traffic analysis: Monitoring DNS traffic to identify any devices querying your DNS servers.
Many asset discovery tools combine active and passive techniques to provide a detailed, comprehensive view of your IT assets.
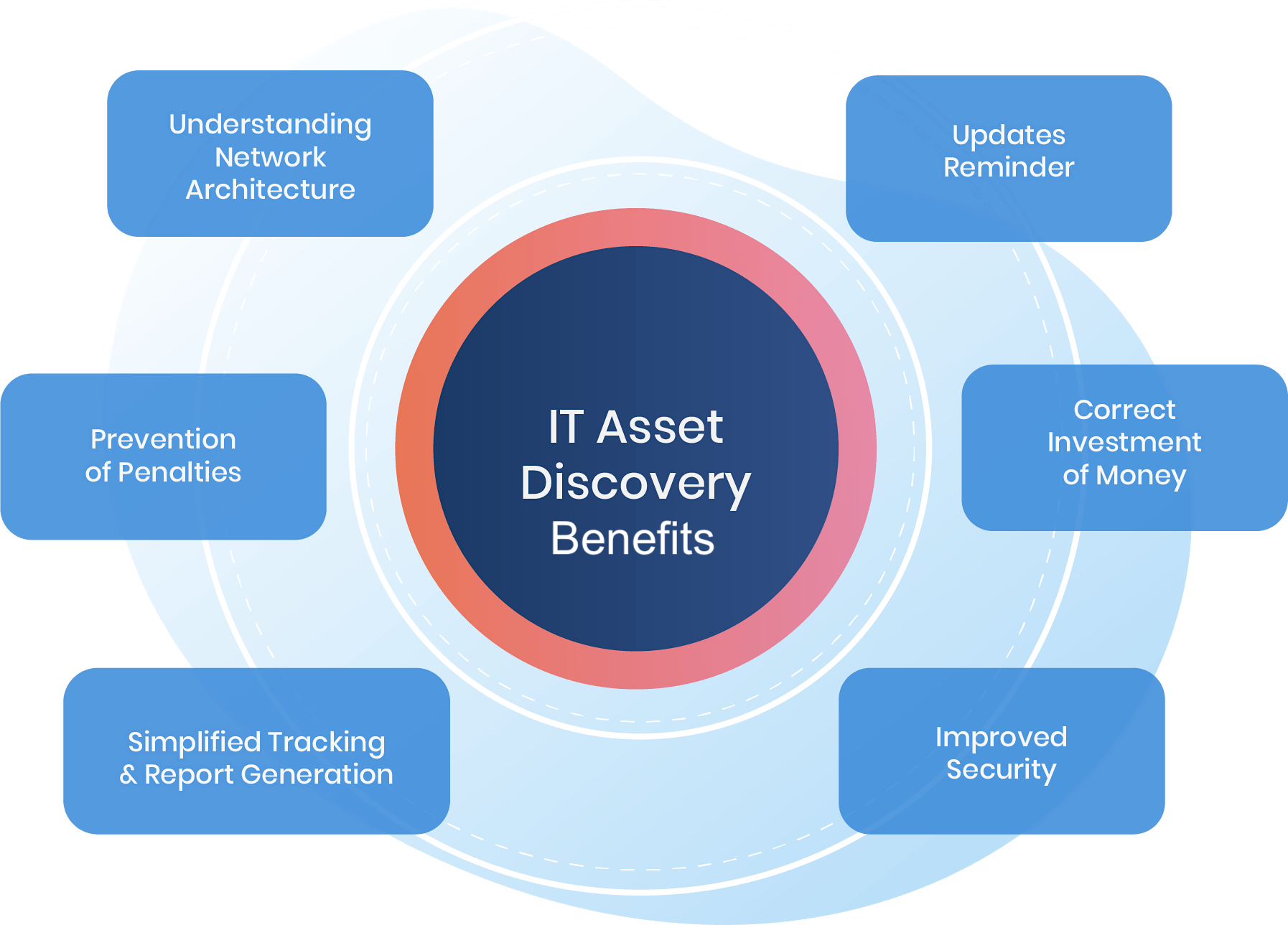
Benefits of Asset Discovery Tools
Quicker Recovery from Cyber Incidents
Asset discovery tools empower your IT team to swiftly identify the compromised asset(s) and isolate the attack. By providing a comprehensive map of your IT environment, these tools eliminate guesswork and cut through the chaos of unknown devices. With fast action, you can minimize damage and reduce downtime—essential for safeguarding your company’s reputation and bottom line.
Automating Asset Cataloging
Discovery tools use highly effective automation in discovering assets, including mobile devices that are constantly moving.
Centralizing Your Asset Database
These tools create a database of all the information about your IT assets, centralizing your asset management practices.
Detecting Anomalies and Irregularities
By continuously monitoring, tracking, and recording data, asset discovery tools spot any data security anomalies or irregularities while they are still in their early stages.
Visualizing Network Setups
Many tools present their findings in visuals to help you quickly comprehend IT asset information, allowing you to spot patterns and interconnected details.
5 Key Features of Asset Discovery Tools
Certain features are essential for asset discovery tools to do their job effectively. When considering one for your organization, look for the following abilities:
- Diligent Network Scanning locates every device and records their details so you can use the resulting map to spot every asset in your system.
- Management of Software Licenses monitors your software and SaaS licenses to track upgrade requirements.
- Detailed Inventory Management provides you with details of all your assets in an organized fashion for easy accessibility.
- Monitoring Network Security evaluates your assets continuously to identify security risks such as unauthorized access.
- Visualization – Many tools offer visual representations of your network infrastructure, such as network maps, dependency graphs, and dashboards. These visualizations help you quickly grasp complex relationships between assets, identify potential bottlenecks, and spot anomalies that might indicate a security risk.
Top 10 Best Asset Discovery Tools
1. Ivanti
Ivanti Neurons for Discovery offers a unified view of everything you own, from licenses to active devices. This comprehensive approach centralizes all your contracts with built-in software license management. A mobile app with barcode scanning simplifies asset tracking throughout its lifecycle from receipt to disposal.
Best for: Large organizations with complex IT environments requiring unified asset management and service delivery
Review: “It demonstrates accurate assets inventory, thus enabling it to meet compliance requirements.”
2. Memcyco
While not an asset discovery tool per se, Memcyco can help you understand where your network may have vulnerabilities and threats. It provides greater visibility into potential attack vectors, including brand impersonation via website spoofing.
An agentless, end-to-end security solution, Memcyco is AI-powered and employs a unique ‘nano defender’ embedded sensor that protects your assets from digital impersonation threats by providing real-time monitoring and alerts.
There’s a forge-proof digital watermark to establish proof of your website’s authenticity, and the solution offers maximum attack visibility while embracing a robust detect > protect > respond paradigm.
Best for: InfoSec, Fraud, SOC, and Business Teams who want a powerful solution to secure their company’s authentic websites and protect their assets.
Review: “Memcyco has already proven its worth and saved us much more than its price. We give it a ringing endorsement.”
3. Cacti
Cacti is a free, open-source tool that provides essential IT asset monitoring. It maps your network infrastructure, including laptops, routers, and servers. Pre-defined templates simplify adding devices and graphs, while role-based access ensures user security.
Best for: Small businesses or IT departments with limited budgets needing a basic overview of network devices.
Review: “If your network needs traffic plotting and you depend on it, it is a great tool and is straightforward to set up, too.”
4. Armis Centrix
Armis Centrix is a cloud-based solution combining asset discovery with AI-driven security. It scans, protects, and manages various IT devices. Its AI engine predicts, prevents, and resolves security risks for these assets. Armis Centrix offers detailed asset profiles, classifying managed, unmanaged, and rogue devices. It empowers teams with in-depth information like device type, installed applications, and network activity.
Best for: Organizations with a strong focus on IoT security that want a unified platform for device management and threat detection.
Review: “The way Armis can find out about devices in all corners of our network and reference integrations to make accurate Risk Assessments on our devices is extremely invaluable.”
5. Zluri
Zluri’s cloud-based solution tracks your entire IT environment, aiding in effective asset management. It uses various methods (Such as spend management tools, APIs, agents, and extensions) to ensure accurate asset identification—even uncovering shadow IT. Zluri offers five distinct discovery methods for efficient scanning and conducts regular audits for real-time asset visibility.
Best for: Organizations needing comprehensive IT asset tracking focusing on workspace management and optimizing resource allocation.
Review: “The platform is very user-friendly, and the setup was not very hard at all.”
6. Certero for Enterprise ITAM
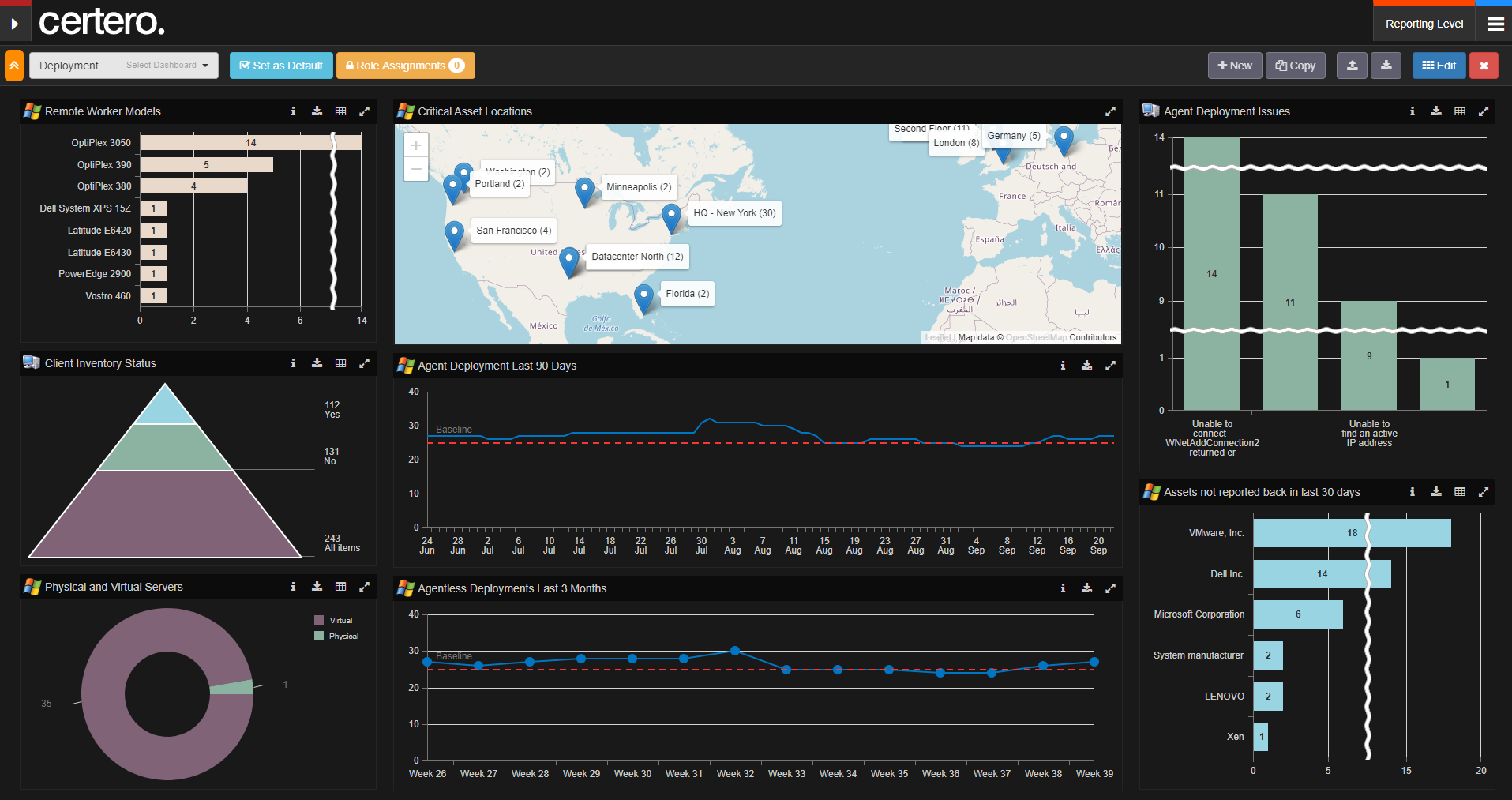
Certero for Enterprise ITAM features a powerful discovery solution that grants comprehensive visibility across all IT assets, including virtualized and cloud environments, for full asset coverage. Certero automates software discovery, identifying applications on your systems. Additionally, it tracks application usage with metrics like active users and installations.
Best for: Enterprise-level organizations that need a comprehensive, secure, and flexible IT asset management solution.
Review: “Certero for Enterprises ITAM is the easiest, fastest, and most resource-efficient way to discover, inventory, and manage IT assets from mobile to desktop.”
7. Paessler PRTG
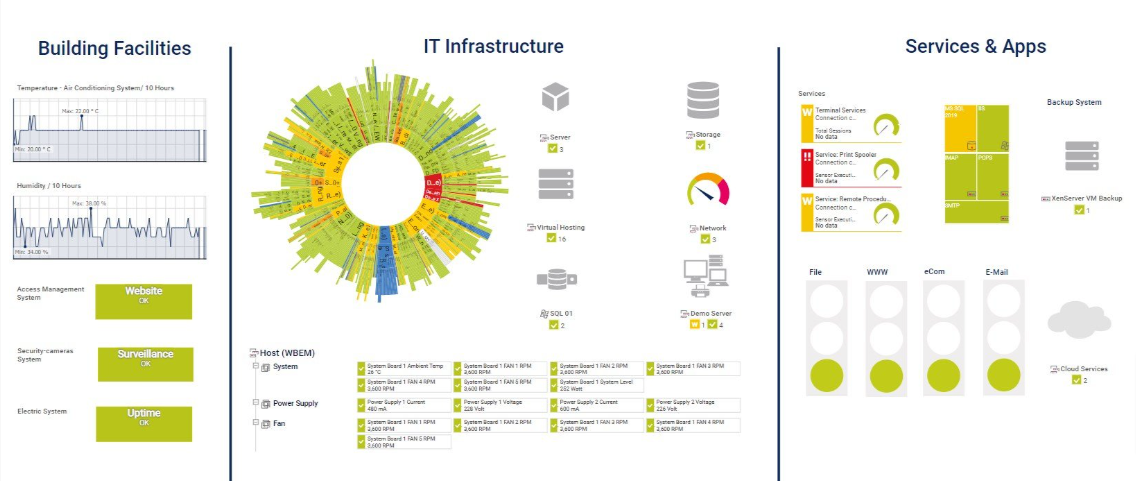
Paessler PRTG offers a combined solution for network monitoring and asset discovery. Its pre-configured sensors automatically locate devices like routers and servers within your network. This functionality allows you to monitor performance metrics, track device uptime, and use real-time maps with live status information.
Best for: Organizations that require comprehensive, real-time monitoring and visibility of their entire IT infrastructure.
Review: “It was easy to install and manage, it’s helping a lot with monitoring and alerting, and it’s easy to use.”
8. NinjaOne
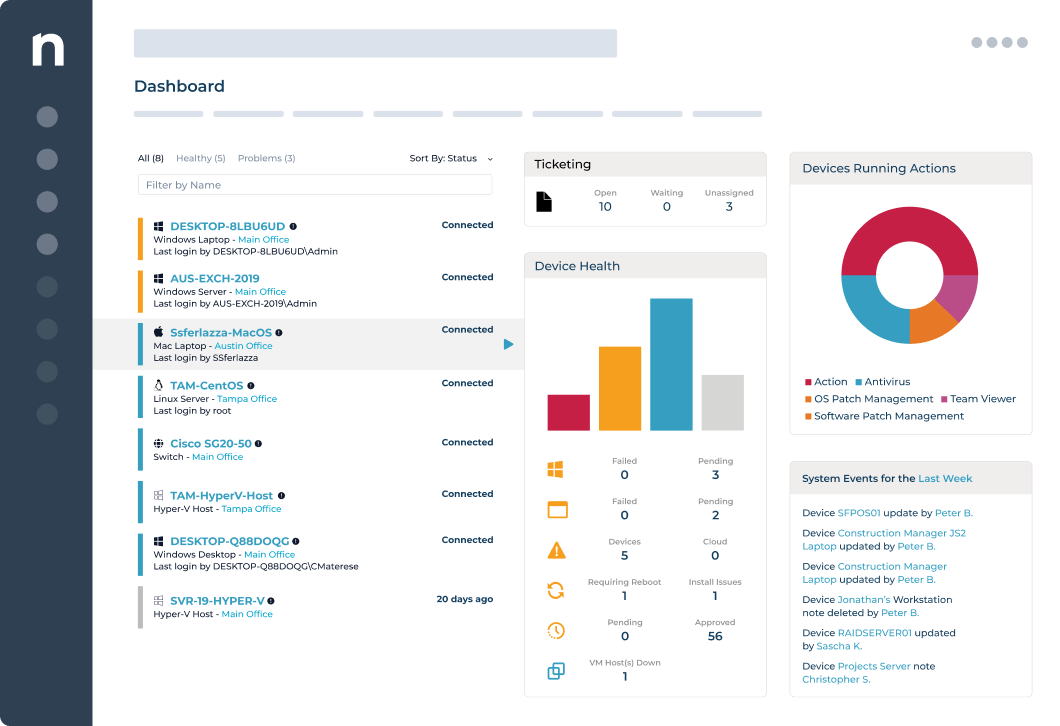
NinjaOne offers a unified IT asset management solution that uses real-time data to identify unmanaged devices, improving your security posture. This comprehensive solution covers your entire IT ecosystem, including devices, software, and remote access. NinjaOne automates asset discovery to ensure all connected devices are managed. It also gathers detailed asset data, enabling proper classification and grouping.
Best for: Managed Service Providers (MSPs) and IT departments needing a comprehensive RMM solution with built-in asset discovery.
Review: “Ninja is super lightweight and robust; we have had little to no issues deploying it, and managing computers and servers via Ninjas capabilities.”
9. Auvik
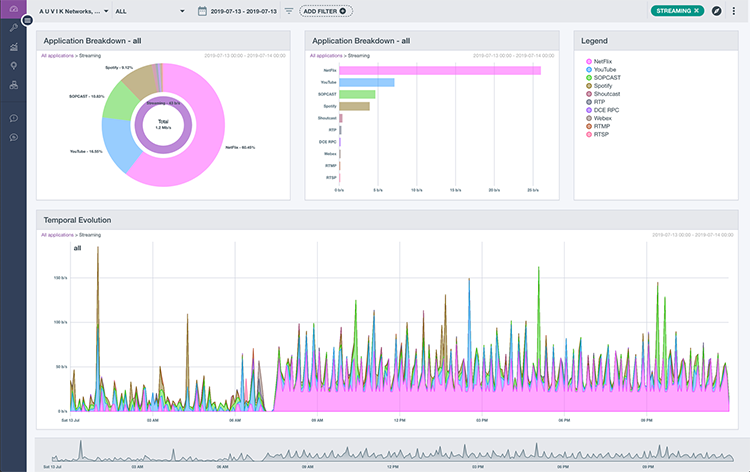
Auvik streamlines network management through automated asset discovery. It deploys a lightweight agent to gather information and map all your network devices. This creates a centralized inventory with detailed asset data, simplifying tracking and management. Auvik also monitors the status of discovered devices, triggering alerts for any changes to keep you informed.
Best for: IT departments managing complex networks that require automated discovery, configuration management, and detailed asset insights.
Review: “Good visual mapping of product. Great platform integration with various device types.”
10. InvGate Insight
InvGate Insight offers a comprehensive approach to asset inventory. It utilizes both agent-based and agentless scanning to discover all your IT assets on the network. InvGate automatically identifies endpoint devices on your network and builds a central repository with detailed asset data—providing a thorough analysis of each asset it identifies.
Best for: Organizations needing a centralized solution for endpoint management focusing on security and patch management.
Review: “A very effective tool to gain complete visibility of your assets.”
Secure Your Assets with Powerful Discovery Tools
In today’s sprawling IT landscapes, organizations are flying blind without asset discovery tools. These tools act like a map, revealing every device, application, and server on your network. This newfound visibility is crucial for cybersecurity because unidentified devices create security holes, and unmanaged software licenses create vulnerabilities.
Asset discovery also simplifies compliance by ensuring all assets are accounted for. Ultimately, these tools empower smarter IT decisions, optimize resource allocation, and minimize security risks—advantages no modern business can afford to ignore.
By employing Memcyco’s robust digital impersonation protection solution, you can take a proactive stance in fraud-proofing your website and its digital assets. Memcyco operates entirely agentless, meaning there’s no software for your users to install or register. This streamlined approach lets you get up and running with Memcyco’s protection suite in minutes.
Take the first step toward building a trusted IT infrastructure by contacting Memcyco for a free demo.







![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1-300x169.png)








![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)