Passwords are broken. They’re the weakest link in our digital security chain, costing businesses billions.
According to a study by Forbes Advisor, 46% of Americans have had their passwords stolen in the past year. Traditional password-based authentication is weak and makes individuals and businesses vulnerable. But what if we didn’t have to use passwords at all?
Passwordless authentication isn’t just a technological upgrade; it’s a fundamental shift in protecting our digital identities and assets. It’s time to move beyond passwords and embrace a more secure, user-friendly approach.
What are passwordless authentication solutions for customers?
Passwordless authentication enables customers to log into services, devices, or applications without traditional passwords, often using methods like biometrics or temporary passcodes. Common examples include smartphones’ fingerprint scanners or face IDs. Besides improving user experience, passwordless authentication has increased security over passwords. Passwordless authentication stops users from sharing or reusing weak passwords.
However, it’s important to remember that passwordless authentication is not foolproof and should be fortified with additional security measures to ensure maximum protection against cyber threats.
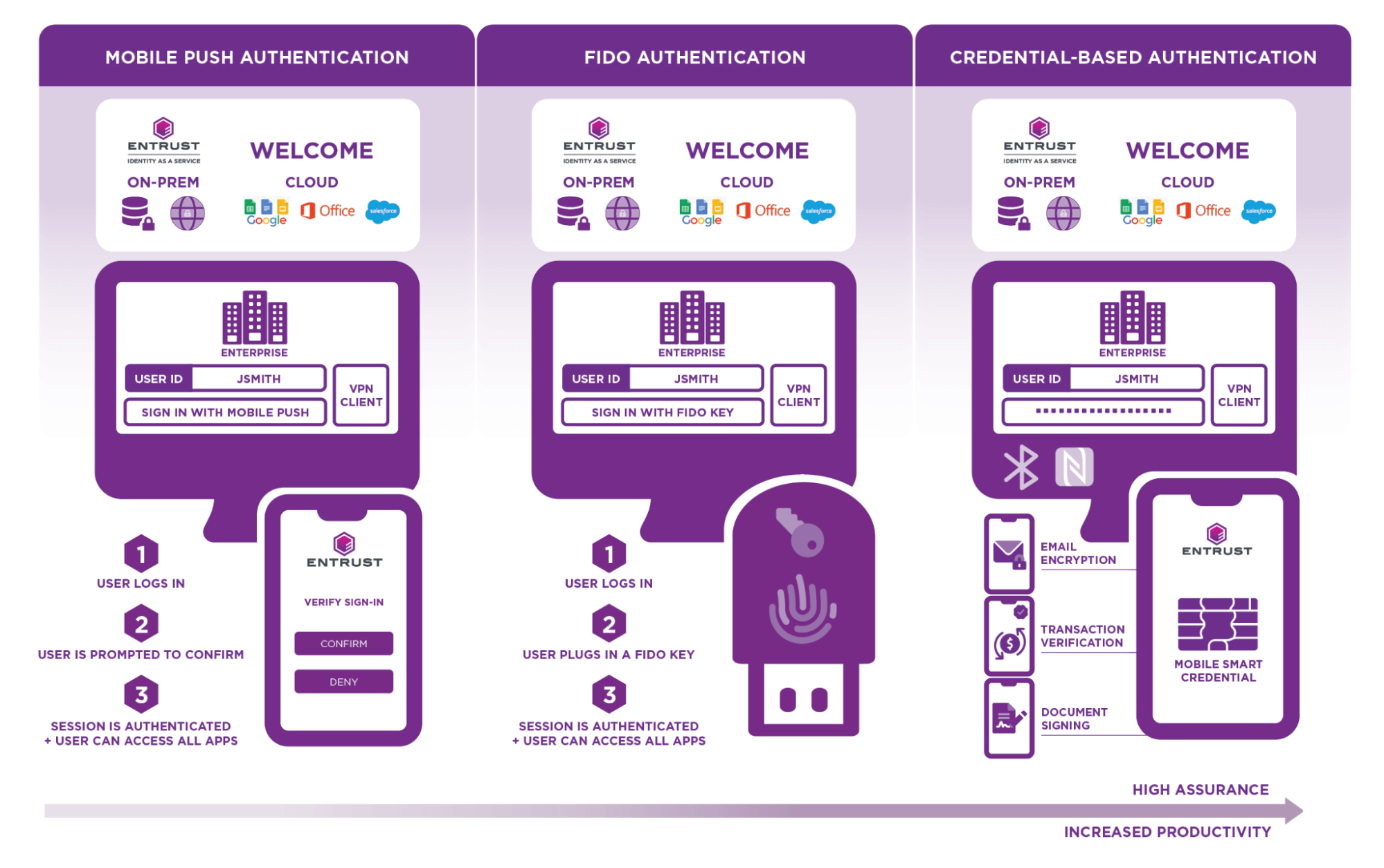
5 Types of Passwordless Authentication Solutions for Customers
Here are five common types of passwordless authentication solutions that are changing the way we log in.
- Biometrics (Fingerprint, Facial Recognition): Biometric authentication uses unique physical traits like fingerprints or facial features to verify users. Advancements in AI are making these systems a more reliable and secure way to log in.
- Magic Links (One-Time Codes): Magic links are temporary codes sent via email or SMS that allow users to log in without passwords.
- Authenticator Apps: Authenticator apps generate time-based codes that users enter along with their credentials for added security.
- Hardware Tokens: These small physical devices generate one-time codes that users enter for authentication, adding an extra layer of security.
- Passkeys: Passkeys are digital credentials tied to user accounts, offering improved phishing resistance but still vulnerable to certain attacks, highlighting the importance of robust security measures even in passwordless environments.
Benefits and Drawbacks of Passwordless Authentication Solutions for Customers
Benefits:
- Reduced Phishing Risk: Passwordless authentication eliminates the primary target of phishing attacks: the password itself. Biometric factors (fingerprint, facial recognition) and possession factors (one-time codes, security keys) are significantly harder to steal or replicate remotely.
- Enhanced Multi-Factor Authentication (MFA): Passwordless methods seamlessly integrate into MFA schemes, replacing the knowledge factor (password) with something the user is (biometric) or something the user has (OTP, security key). This significantly strengthens overall account security.
- Reduced Account Takeover (ATO) Risk: While not eliminating ATO entirely, passwordless authentication raises the bar significantly. Attackers can no longer rely on stolen credentials alone. They would need to compromise additional factors, making attacks more complex and less likely to succeed.
Technical Challenges & Mitigations:
- SIM Swapping: Attackers can gain control of a user’s phone number to intercept one-time codes (OTPs). Mitigations include app-based OTP generators, push notifications, or hardware security keys.
- Biometric Spoofing: Sophisticated attackers can bypass biometric authentication using fake fingerprints or facial replicas. Mitigations include liveness detection (checking for genuine biological traits), multi-modal biometrics (combining multiple biometric factors), and behavioral biometrics (analyzing user interaction patterns).
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept communication between the user and the authentication server to steal authentication tokens or session cookies. Mitigations include strong encryption, secure channels (HTTPS), and device binding (linking authentication sessions to specific devices).
- Malware and Phishing: Malware can steal biometric data or OTPs stored on a device, while phishing attacks can trick users into revealing sensitive information. Mitigations include:
-
- Educating users about safe practices.
- Using anti-malware software.
- Employing robust authentication methods for sensitive operations.
-
Key Features of Passwordless Authentication Solutions for Customers
When choosing a passwordless authentication solution, prioritize the following key features:
- Security Strength: Assess the security measures such as encryption standards, resistance to phishing attacks, and the robustness of authentication protocols. Data security posture management (DSPM) can be a valuable tool to assess and maintain the security posture of your authentication solution.
- User Adoption: Prioritize intuitive and familiar solutions that don’t require technical expertise. A complex authentication system may lead to customer churn.
- Scalability: Always be prepared for growth. You want to choose a solution that can scale when business comes in. Ensure the solution can accommodate increasing numbers of users and transactions without compromising performance or security.
- Compatibility: Adopting a passwordless solution incompatible with your existing systems is cost-prohibitive. Look for solutions that offer robust APIs, SDKs, and support for industry-standard protocols.
- Regulatory Compliance: Consider regulatory requirements and compliance standards relevant to your industry and geographic location. Your compliance with GDPR, HIPAA, or PCI DSS relies on any third-party solutions you integrate into your systems. A strong IT security policy can help ensure compliance and mitigate risks associated with passwordless authentication.
- Reliability and Uptime: Choose solutions with high availability and resilience to ensure uninterrupted customer access. Look for providers with a proven track record of reliability and uptime backed by robust infrastructure and disaster recovery capabilities.
- Cost and Value: Consider upfront costs, ongoing maintenance fees, and potential savings from reduced support overhead and security incidents.
Top 10 Passwordless Authentication Solutions for Customers
1. Okta Customer Identity Cloud
Okta is a popular solution in enterprise organizations. It offers a wide range of services in addition to passwordless authentication. The customizable universal branded login and social and enterprise authentication make Okta a prime candidate for enterprise solutions. Okta boasts a robust API and SDK for easy development and scalability.
Best for: Enterprise applications marketed to organizations that already use Okra.
Review: “I enjoy that Okta is a one-stop shop for all tooling and software necessary for my position.”
2. Memcyco
Memcyco’s Digital Impersonation Protector (DIP) is a comprehensive security solution designed to safeguard against the growing threat of website impersonation scams, a significant vulnerability in passwordless authentication.
By utilizing advanced algorithms to detect website spoofing, DIP provides real-time threat intelligence and customizable protection options to enhance the security of your passwordless authentication implementation. Incorporating DIP into your cybersecurity strategy adds a robust layer of defense against evolving cyber threats, ensuring the resilience of your authentication processes and safeguarding your sensitive data.
Best for: Web-based applications that require robust security measures.
Review: “Memcyco’s already proved its worth and saved us much more than its price. We give it a ringing endorsement.”
3. HYPR
The HYPR platform enhances security, usability, and scalability by decentralizing the authentication process. It leverages biometric data and device-based credentials stored locally rather than centrally. Compliant with FIDO2 and WebAuthn standards, it offers multi-factor authentication and adaptive security, enhancing user experience and protection against conventional phishing and credential-related attacks.
Best for: Unified security of devices and applications.
Review: “With a TAP on your smartphone or a touch on your Security Key, you will have immediate access to everything.”
4. Google Cloud Identity
Google Cloud Identity offers Single Sign-On capabilities, allowing users to access multiple applications and services with their existing Google identities. It offers robust multi-factor authentication, single sign-on capabilities, and advanced threat detection. Supports various identity protocols and ensures compliance with industry standards. Google Cloud Identity, through its integration with Identity Platform, does support passwordless authentication. It can be implemented using passkeys, which allow users to sign in with biometrics, PINs, or patterns instead of traditional passwords.
Best for: Google cloud-integrated applications.
Review: “Implementing advanced features for auditing purposes was not built into the system, and we had to build them ourselves.”
5. Microsoft Entra ID
Microsoft Entra ID, formerly Azure Active Directory, is a robust identity and access management solution providing secure access to applications and resources. It offers extensive support for identity governance, compliance with industry standards, and powerful tools for managing user identities and access rights, enhancing security and operational efficiency for organizations.
Best for: Applications marketed to Microsoft Entra ID users.
Review: “I can say it is one of the best security features from Microsoft previously Azure active directory. Imagine having one key for your work life..”
6. AuthID Customer Identity
AuthID’s main product, Verified™, uses a combination of factors to confirm a user’s identity, such as FIDO2 passwordless authentication, cloud biometrics, and Liveness detection. It offers adaptive authentication that adjusts security measures based on risk. AuthID is a scalable and flexible identity management system that is suitable for a wide range of businesses and applications.
Best for: Financial industry.
Review: “authID’s identity solution delivers enhanced security to our
platform and a seamless candidate authentication process.”
7. Frontegg
Frontegg is a comprehensive platform designed to enhance passwordless authentication for SaaS companies. It incorporates multi-factor authentication and various passwordless methods, such as biometric authentication, magic links, and single sign-on (SSO). It is designed for scalability and provides consistent performance as user bases grow, making it an ideal choice for startups seeking an efficient passwordless authentication solution.
Best for: Startups and small developers.
Review: “ I have the flexibility to choose the authentication factors I want to implement, including SMS, authentication apps, built-in authentication, and security keys.”
8. Authsignal
Authsignal prioritizes security and compliance, implementing robust security measures such as encryption, secure protocols, and compliance with industry regulations. Its advanced features include real-time fraud detection and behavioral analytics. With flexible integration options and a user-friendly interface, Authsignal caters to administrators and end-users.Best for: Enterprise and mid-market businesses.
Review: “It’s been extremely refreshing to have a provider with a similar approach to ourselves in that they were transparent and tried to understand our needs […]”
9. PingOne for Customers

PingIdentity offers customizable registration flows with branding and user profile management capabilities. PingOne for Customers also emphasizes compliance with industry standards, providing peace of mind for businesses handling sensitive customer data.
Best for: Single Sign On.
Review: “It is managed and cloud-based so that we could save up on dedicated infrastructure.”
10. TrustKey
TrustKey stands out with hardware-based security solutions that comply with FIDO standards. By supporting multi-factor authentication and prioritizing a user-friendly experience, TrustKey offers a balance between security and usability. TrustKey enhances your authentication processes and bolsters your security against evolving cyber threats.
Best for: Physical passwordless authentication.
Review: “All provided security keys are working properly with Azure AD. All keys with fingerprint sensors are also Windows Hello for Business certified.”
Add Security to your Passwordless Authentication Implementation with Memcyco
Passwordless authentication is here, but the same old security problems still exist—just under a different guise. While it eliminates password-related vulnerabilities, it opens the door to new threats like account takeover and sophisticated phishing attacks.
Memcyco addresses these challenges head-on. Our AI-powered platform provides robust protection against digital impersonation and account takeover attempts, effectively mitigating the risks associated with passwordless authentication. By continuously monitoring suspicious activity and employing advanced detection techniques, Memcyco enables real-time threat response, ensuring your customers’ accounts remain secure and your brand reputation stays intact.
Incorporating Memcyco into your security infrastructure is a proactive approach that goes beyond passwordless authentication. It provides comprehensive protection against the evolving landscape of cyber threats. With Memcyco, you can confidently embrace the benefits of passwordless authentication while ensuring the highest level of security for your business and customers.
Book a demo today and learn how Memcyco can fortify your passwordless authentication and protect your customers from evolving cyber threats.



















