In a world that’s gone digital, it’s no surprise that so have our assets. Protecting digital assets is crucial to maintaining an organization’s operations and revenues, whether it’s sensitive personal identifiable information (PII), business data, or intellectual property.
Online threats rapidly evolve to employ complex counterfeiting and spoofing of digital assets and new means to break down the software gates they hide behind. This scenario calls for effective digital asset protection methods to secure the critical data that makes businesses go.
It’s essential to recognize the value of digital assets; they’re not just virtual entities but significant income generators. In 2024, revenue from digital assets is anticipated to surge to $80,080m USD, with expectations for continued growth. To safeguard these vital assets, organizations must arm themselves with a comprehensive suite of digital asset protection methods capable of combating a broad spectrum of threats.
Let’s explore the world of digital assets and discover how to better protect every organization’s valuable digital treasure chest.
What are digital assets?
Digital assets are any form of electronic data that holds value to an individual or organization. Common types of digital assets include:
Intellectual Property
This category includes patents, trademarks, copyrights, software, music, films, and books. These assets hold significant value due to the exclusive rights granted to their owners.
Marketing Assets
These assets are where organizations communicate and transact with their customers. They are closely related to intellectual property but are more defined. They include digital properties such as websites, mobile applications, social media profiles, email lists, and more.
Personal Data
Representing customers’ sensitive information and personal data serves as an asset by generating insights and enabling personalized service. It may include health, financial, or account data. Privacy and security measures are necessary for risk mitigation and ensuring regulatory compliance with GDPR, HIPAA, and other rules when dealing with personal data assets.
Digital Media
Digital content such as images, videos, eBooks, and electronically-accessible presentations serve as assets by providing entertainment, education, and information dissemination. Digital media generates revenue through purchasing, renting, licensing, and advertising.
Business Assets
Critical documents, client databases, and proprietary information are assets enabling productivity, innovation, and competitiveness. They also contribute to revenue generation and strategic decision-making in business operations.
Digital Currencies
NFTs, cryptocurrencies such as Bitcoin and Ethereum, smart contracts, and DApps are becoming an essential part of culture and business activity today. They’re the backbone of a decentralized financial system that’s growing alongside the traditional one.
What is digital asset protection, and why is it important?
Digital asset protection encompasses the strategies and tools organizations use to secure their valuable digital holdings from cyber attacks. Securing your digital assets isn’t just a wise choice—it’s necessary in a threat landscape where it’s common for malefactors to target digital assets. Here are a few examples of attack methods:
- Malware is malicious software deployed to disrupt or gain unauthorized access to computer systems. Malware can range from trojans and spyware to viruses and worms, each designed to infiltrate, damage, or take control of a target device. It spreads through compromised downloads, malicious email attachments, or infected external drives.
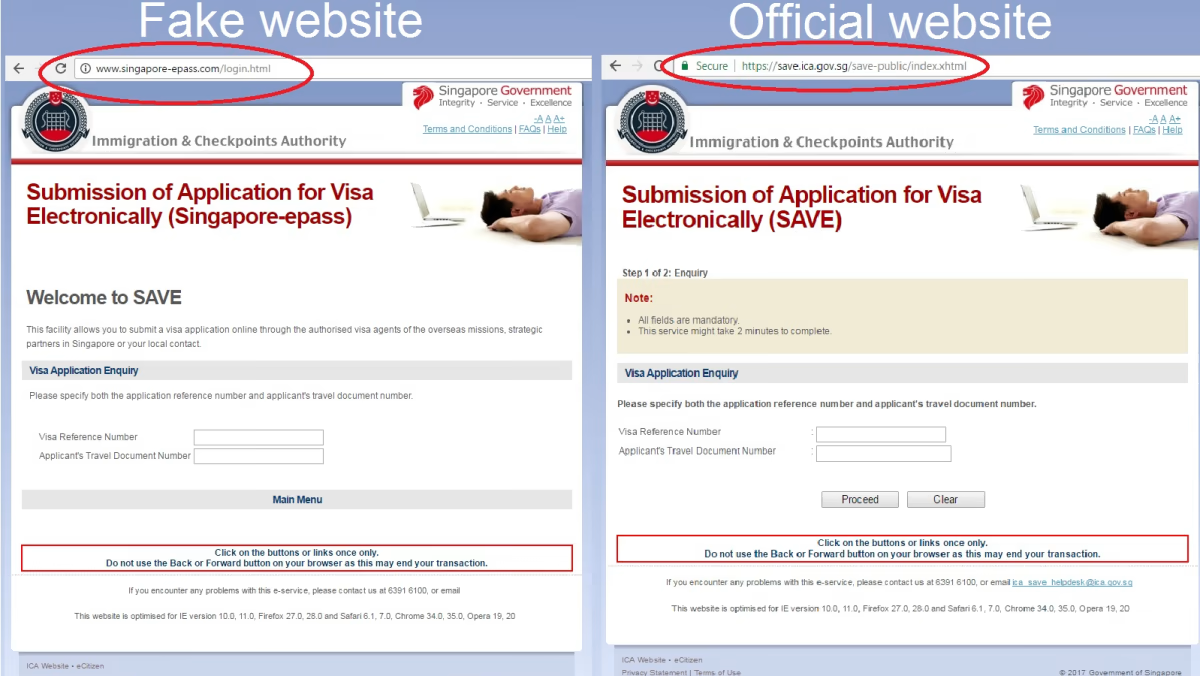
- Phishing uses deceptive emails or websites to steal sensitive information such as passwords, usernames, and payment details. Phishing attacks often involve tricking the recipient into believing the request comes from a trusted source through a fake website, compelling them to part with confidential information or download malware.
- Ransomware is malware that locks and encrypts data and then demands payment for its release. This attack can incapacitate organizations by rendering critical data and systems inaccessible, often forcing victims to pay a hefty ransom to restore access.
- DDoS (Distributed Denial of Service) attacks overload systems, servers, or networks with traffic to render them unusable. They typically involve a botnet (a compromised computer network) that floods the target with excessive requests, leading to service interruptions or total shutdowns.
- Password Attacks attempt to crack or guess passwords to gain unauthorized system access. These attacks can use techniques like brute force, where attackers try every possible password combination, or credential stuffing, where stolen account credentials are used to gain unauthorized access to other accounts. Memcyco’s Digital Impersonation Protector solution protects against brute force and credential stuffing, regardless of whether this data was harvested through impersonating websites.
Employing digital asset protection tools and strategies is crucial to thwarting these threats and mitigating risks by ensuring the security of your entire digital ecosystem. These protective measures help organizations prevent data breaches, ensure their competitive advantage, enhance customer trust, and reduce financial losses.
Top 11 Digital Asset Protection Methods
When considering how to protect your digital assets in 2024, organizations have many powerful protection methods to choose from:
1. Access Control
Access control regulates who or what can view or use specific resources in a digital environment. It is a critical component of information security that helps protect digital assets—such as data, applications, services, and the systems that store or process information—by ensuring that only authorized users, systems, or processes can access or perform actions on them.
To protect digital assets effectively, organizations must implement robust access control policies that include strong authentication methods, least privilege access (providing users with the minimum access level needed to perform their duties), and regular user access reviews.
Integrating access control with other security measures, such as encryption and intrusion detection systems, creates a more comprehensive defense against cyber threats.
2. Antivirus and Antimalware Software
Antivirus and antimalware software are essential defenses against malicious software threats like viruses, worms, Trojans, and ransomware. These security solutions safeguard computers, networks, and devices from compromise, by scanning, detecting, and removing malware infections. Regular updates to virus definitions and system scans are crucial for preventing malware from stealing data, damaging critical assets, or causing system outages.
3. Backup Solutions
Backup solutions act as a digital insurance policy by creating duplicate copies of sensitive files and data, ensuring the resilience and continuity of an organization’s digital assets during incidents like hardware failures, data corruption, or ransomware attacks.
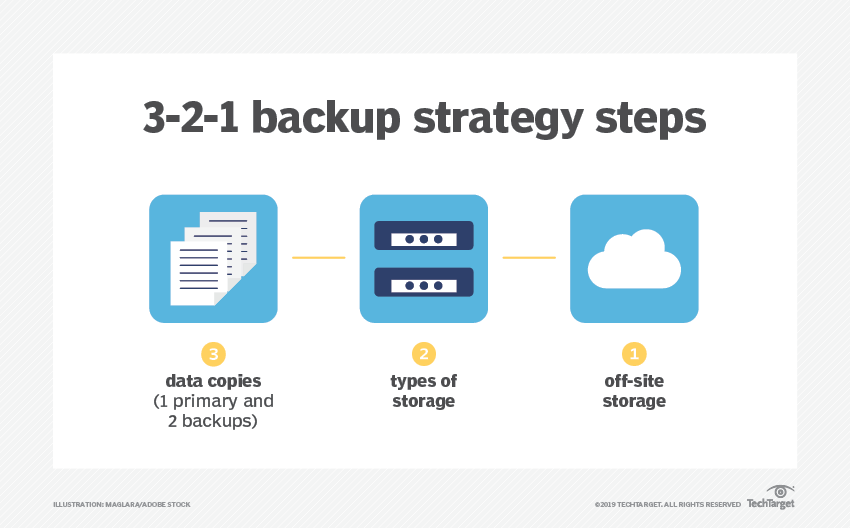
When selecting backup solutions, it’s essential to adhere to the 3-2-1 backup strategy:
- Maintain three versions of any crucial document—a primary and two duplicates.
- Use two distinct forms of storage media to safeguard against various risks.
- Ensure one copy is kept in a separate location away from your home or office.
4. Data Loss Prevention (DLP) Solutions
DLP solutions protect sensitive information within an organization’s network and on its endpoints. By monitoring, scanning, and categorizing data—whether in transit or at rest—DLP systems help prevent unauthorized access to confidential data, its sharing, or its leakage. DLP solutions swiftly address data security incidents through content analysis, contextual understanding, and strict policy enforcement.
5. Digital Rights Management (DRM)
DRM tools are indispensable for managing access to digital content and safeguarding intellectual property rights. These solutions prevent unauthorized copying, distribution, or piracy of digital content by employing encryption and watermarking.
DRM enforces access controls and usage policies to make sure that only authorized users can access or use digital materials, protecting against revenue loss and preserving the value of digital assets.
6. Encryption Software
A critical component for securing digital assets, this software encrypts sensitive data using cryptographic algorithms, turning it into an unreadable format to unauthorized users. It ensures the confidentiality of information during network transmission or data storage. Encrypted information remains secure without the proper decryption key, even in the event of data interception.
7. Firewalls
Firewalls control and monitor network traffic according to predefined security rules, effectively acting as a barrier between internal and external networks. These robust barriers scrutinize data packets to permit or deny access based on security criteria, preventing unauthorized access and malicious traffic while allowing legitimate communication.
By enforcing security protocols at the network’s edge, firewalls are fundamental in thwarting unauthorized entries, data breaches, and cyber attacks.
8. Healthy Password Management
A recent Google study found that 54.8% of cloud compromise factors were attributed to either having a weak password or none at all. Promoting strong password practices is crucial for securing digital assets and user accounts. Encouraging complex passwords, avoiding reuse across multiple platforms, and regularly updating passwords can significantly reduce the risk of breaches.
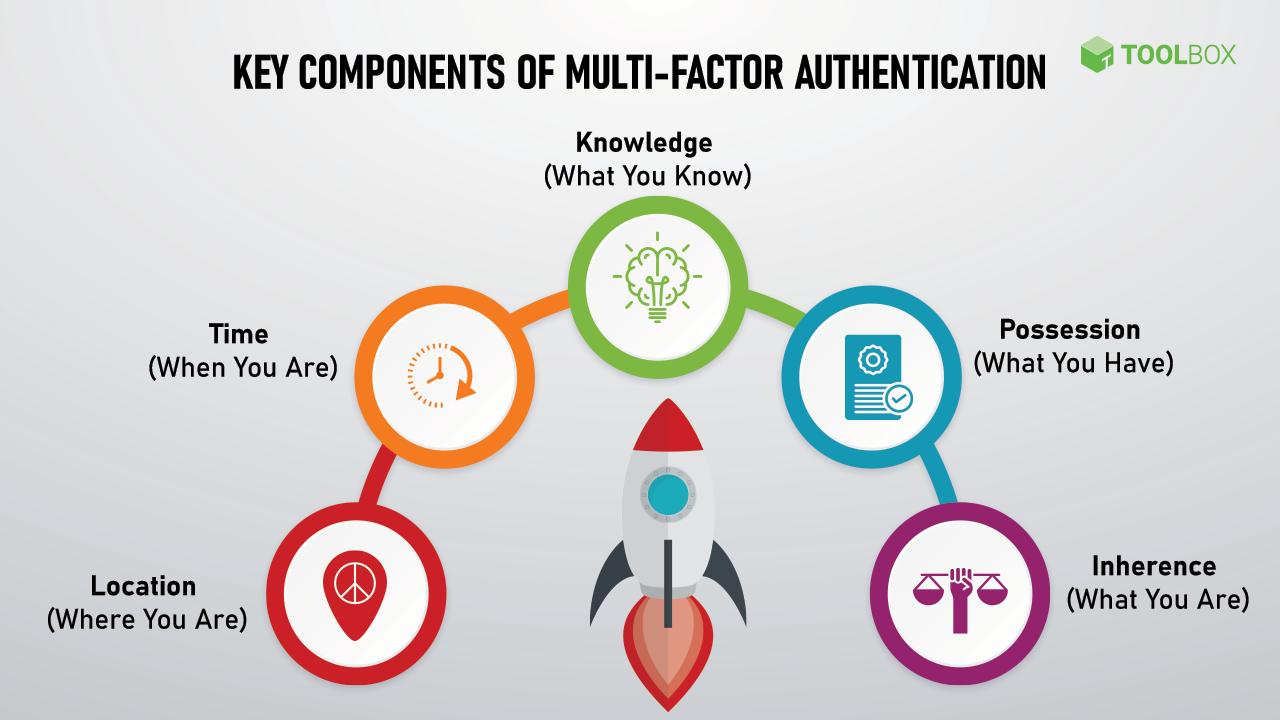
9. Multi-factor Authentication (MFA)
MFA significantly reduces the risk associated with stolen or compromised credentials by requiring additional forms of verification, making unauthorized account access much more challenging. Unfortunately, it’s not foolproof, as some advanced phishing attacks can bypass MFA.
To bolster MFA, diversify authentication factors by incorporating something you know (passwords), something you have (security tokens), and something you are (biometrics). Opt for adaptive MFA to tailor authentication needs based on risk and favor authenticator apps over SMS to avoid interception.
Educating users on MFA security and phishing prevention, regularly updating MFA systems, and monitoring for suspicious activities is critical. Finally, ensure MFA is a requirement across all access points and periodically audit its effectiveness.
10. Watermarks
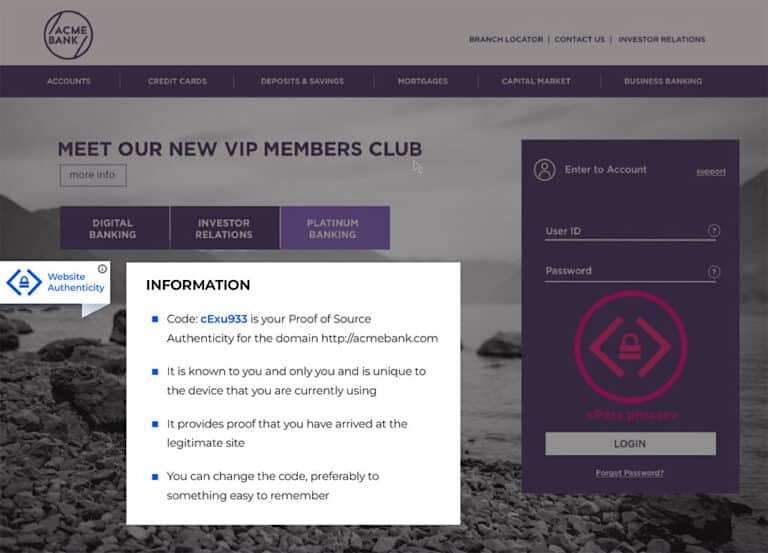
Watermarks have long been a method of asserting authenticity. They have evolved from artist signatures on paintings to digital markers that validate the genuineness of images, videos, and websites. In the digital age, watermarking technology ensures that digital assets are recognized as authentic, fostering trust among viewers and customers while combatting digital impersonation and theft.
As an example, Memcyco uses a watermark to protect against website impersonation. A customizable, tamper-resistant digital watermark is placed on your website, signaling to employees that this is the real deal, just like physical watermarks used to authenticate banknotes.
11. Website Security
Website security is paramount for protecting digital assets when your business relies on websites to interact with customers, process transactions, or deliver services.
Organizations employ security measures to safeguard against these threats, including regular website patches and updates to address known vulnerabilities, implementing secure communication protocols such as HTTPS, and deploying web application firewalls (WAFs) to monitor and filter incoming web traffic.
Memcyco offers the only real-time website security solution that protects against malicious spoofed websites that defraud customers. Memcyco embeds an active ‘nano defender’ tracking sensor in your company’s authentic site to provide maximum attack visibility in real-time and full protection for your company and its customers.
Protect Your Digital Assets with Memcyco
Digital assets are valuable targets for cybercriminals. To safeguard their integrity and availability against ever-evolving cyber risks, organizations must utilize robust digital asset protection tools and strategies to protect their business and customers.
Memcyco is at the forefront of digital risk protection, leveraging cutting-edge AI technology to protect businesses from digital impersonation fraud. With Memcyco’s innovative technology, companies can rest assured that their digital assets are shielded from the devastating consequences of website spoofing attacks, financial losses, data breaches, and ransomware.
Try a free demo today to experience Memcyco’s digital asset protection capabilities firsthand.



















