Every step you take, every move you make, some company will be watching you. While user activity monitoring may sound invasive at first, the growing number of insider and external threats makes it compulsory for companies to understand how users interact with their systems.
43% of workers report their employer monitors their online activity, and this percentage rises to 48% for hybrid employees. Tracking user behavior from internal personnel, third parties, and external website visitors is the only way to detect security issues promptly and prevent sensitive data from reaching the wrong hands. Thankfully, user activity monitoring tools can do all the heavy work for you.
What does User Activity Monitoring (UAM) Entail?
User Activity Monitoring (UAL) tracks and analyzes user activity on a computer or network. User activity encompasses any activity a user engages in within the company’s systems, such as accessing files, sending emails, or visiting a website page.
UAM can be used to monitor both individual user activity and activity at the organizational level. To do this, organizations can track which users are accessing which files and when and how much data they transfer to and from which systems. By tracking and documenting every digital interaction within a system or network, UAM helps ensure that users comply with company policies and prevent outsider threats like website spoofing.
Why is UAM Important For E-commerce?
UAM can be incredibly beneficial for e-commerce businesses because they rely on users interacting safely with their websites. For example, an attack like website spoofing, where bad actors create a fake website to sell counterfeit goods and steal customer data or money, can be detrimental to e-commerce shops, leading to loss of business, weakened customer trust, and potentially severe legal implications.
Not only does UAM help e-commerce businesses protect their digital assets, but it also helps them protect their customers. By adopting a proactive security approach, businesses can detect threats timely and prevent their customers from giving away personal information or making transactions to attackers’ bank accounts.
For employees, UAM can help improve productivity by providing visibility into how they access and use sensitive data. However, organizations must be careful when collecting and storing user activity data, as this data can be sensitive. Strong policies ensure that your organization only leverages user and employee activity data for legitimate purposes. Employees should also be aware of the company’s approach to cybersecurity and consent to having their activities monitored while operating on the corporate network.
How Automated Tools Can Help Solve Current UAM Challenges
UAM can be challenging to implement and manage because it requires collecting and analyzing large amounts of data. Think of an e-commerce site like Amazon, which had 425 million UK visitors in the first two months of 2024. Now, imagine having to track every visitor interaction with this website. Even if you are not an Amazon private label seller, you can quickly adapt this scenario to your e-commerce site to understand the breadth of data you would have to handle.
Monitoring these interactions manually isn’t just time-consuming and resource-intensive – it’s simply impossible. Automation with specialized software can help make UAM more efficient and effective. Some of the criteria e-commerce companies should keep in mind when selecting UAM solutions include:
- Coverage for all devices, including computers, laptops, smartphones, and tablets (especially as remote working is now more common)
- Coverage for all software applications, including web browsers, email clients, chat clients, and file-sharing applications
- Real-time user tracking and instant alerts
- Insights and detailed reporting
Top 7 User Activity Monitoring (UAM) Tools for 2024
1. Digital Guardian
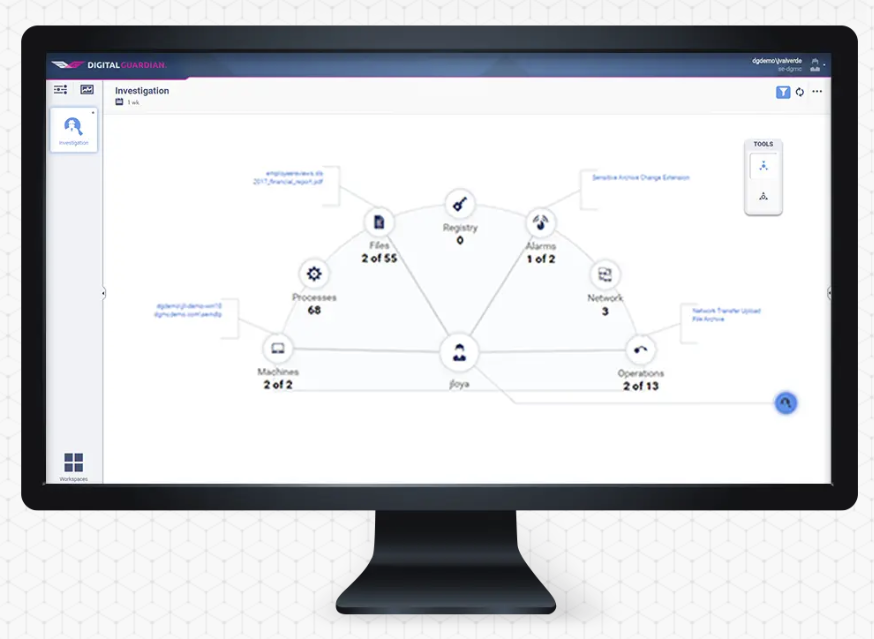
Digital Guardian provides visibility on who’s using what, when, and where–along with where your data travels. It covers hardware and software, helping you track data from creation to distribution across any system. It also offers automatic data classifications and customizable policies, all within a lightweight application. However, users often complain about its dashboard being complex and not intuitive.
Best For
Businesses looking to improve employee monitoring and insights.
Customer review
“What I like most about Fortra’s Digital Guardian is that information is provided via analytics, graphs, etc. With that, it is much more understandable.”
2. Memcyco
Memcyco’s Digital Risk Protection (DRP) solutions enable continuous website monitoring to detect brand identity threats such as website spoofing, cloning, account takeovers, and phishing attempts. If any suspicious activity is detected, companies get instant alerts and detailed insights into the evolving attack. This can benefit e-commerce sites and supply chain flows, where unauthorized access or spoofing attacks can result in stolen data, financial losses, and reputational damage.
Best for
Companies looking to protect against brand identity and impersonation attacks.
“Unlike common threat-intelligence scanning solutions, Memcyco stands out with its ability to detect and protect from digital impersonation attacks in real-time, as well as analyze the impact of the attacks at the individual victim level.”
3. SEON
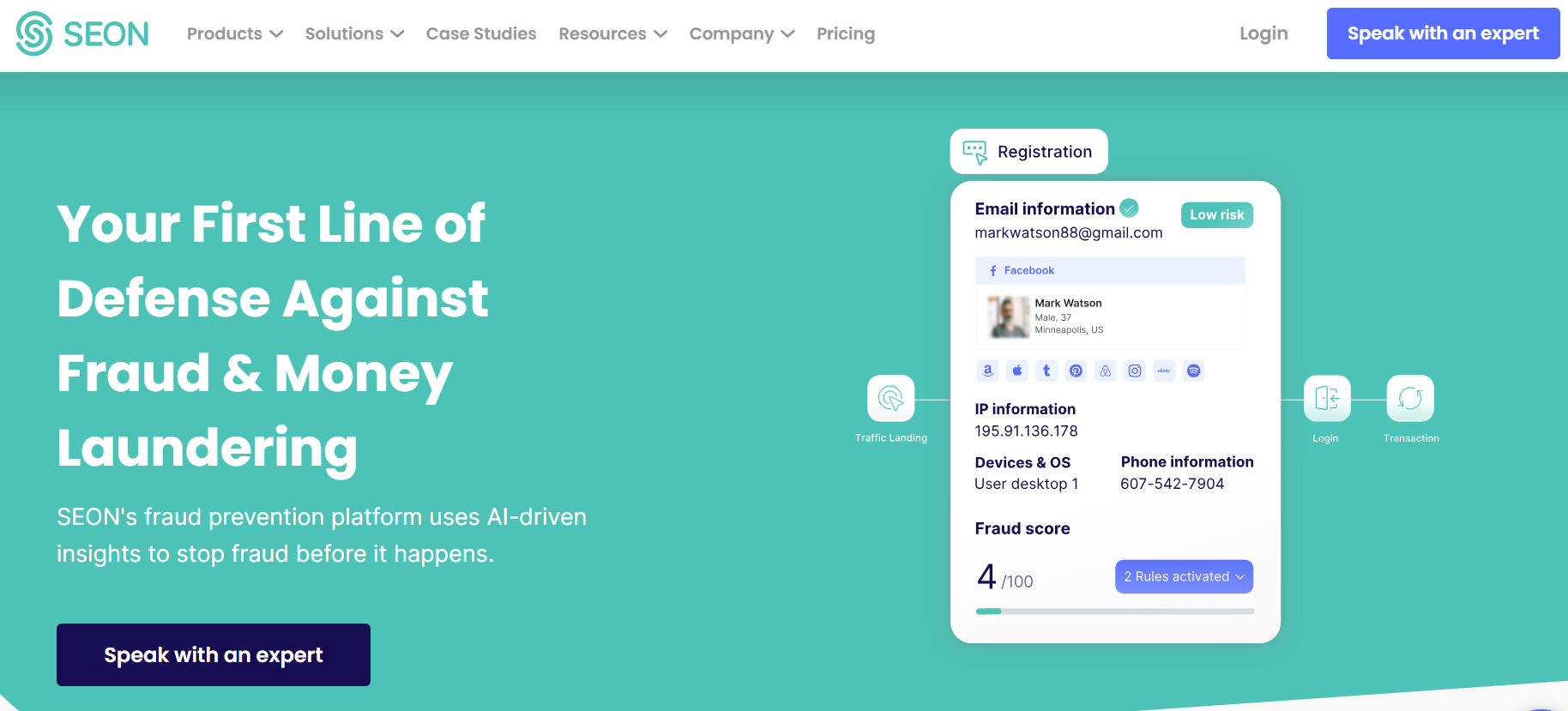
Seon is a fraud detection platform that produces a risk score for each user based on digital and social media lookup. It offers automated digital profile checks for customer onboarding, enabling your business to prevent insider threats and other large-scale bot scams and attacks. Streamlined identity verification can be beneficial for financial services businesses.
Best for
Businesses looking for an automated identity verification solution.
Customer review
“It is truly a machine-driven workflow. SEON Sense gives fraud managers a complete end-to-end solution with flexible features to fit how you do business and has lowered our fraudulent chargeback rates by almost 90% since we first started using it.”
4. Teramind
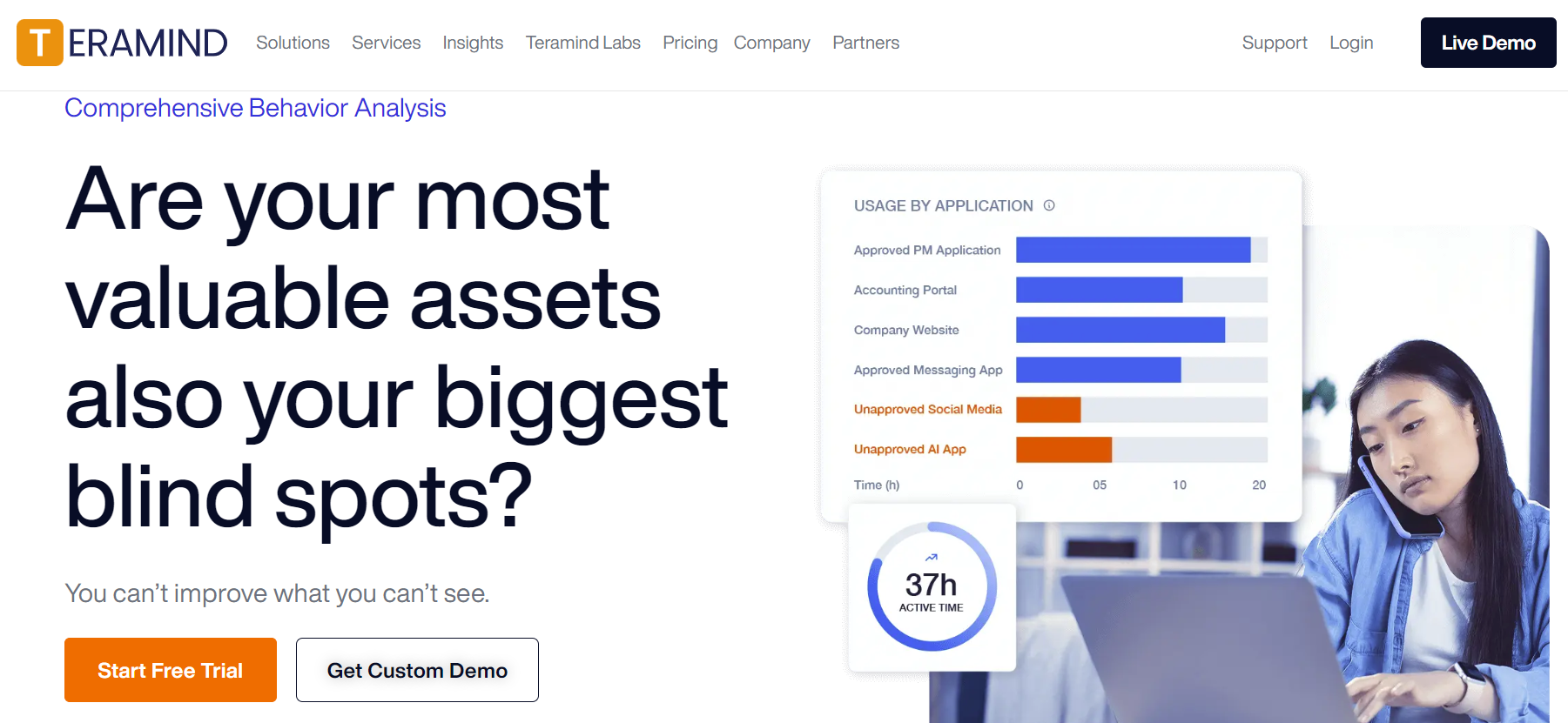
Teramind is user behavior-tracking software that can improve business processes and implement security compliance by capturing, analyzing, and controlling user desktop activities. The tool lets you modify sensitive documents and data access levels for employees and contractors. You can also monitor employee engagement and productivity, which is particularly useful for remote teams.
Best for
Remote teams looking to track workforce activities and productivity
Customer review
“Teramind is a fantastic tool for monitoring user activity/productivity but can also help troubleshoot IT issues. We implemented it over five years and use it daily. There is a rich feature set, and the support is second to none.”
5. Ekran System
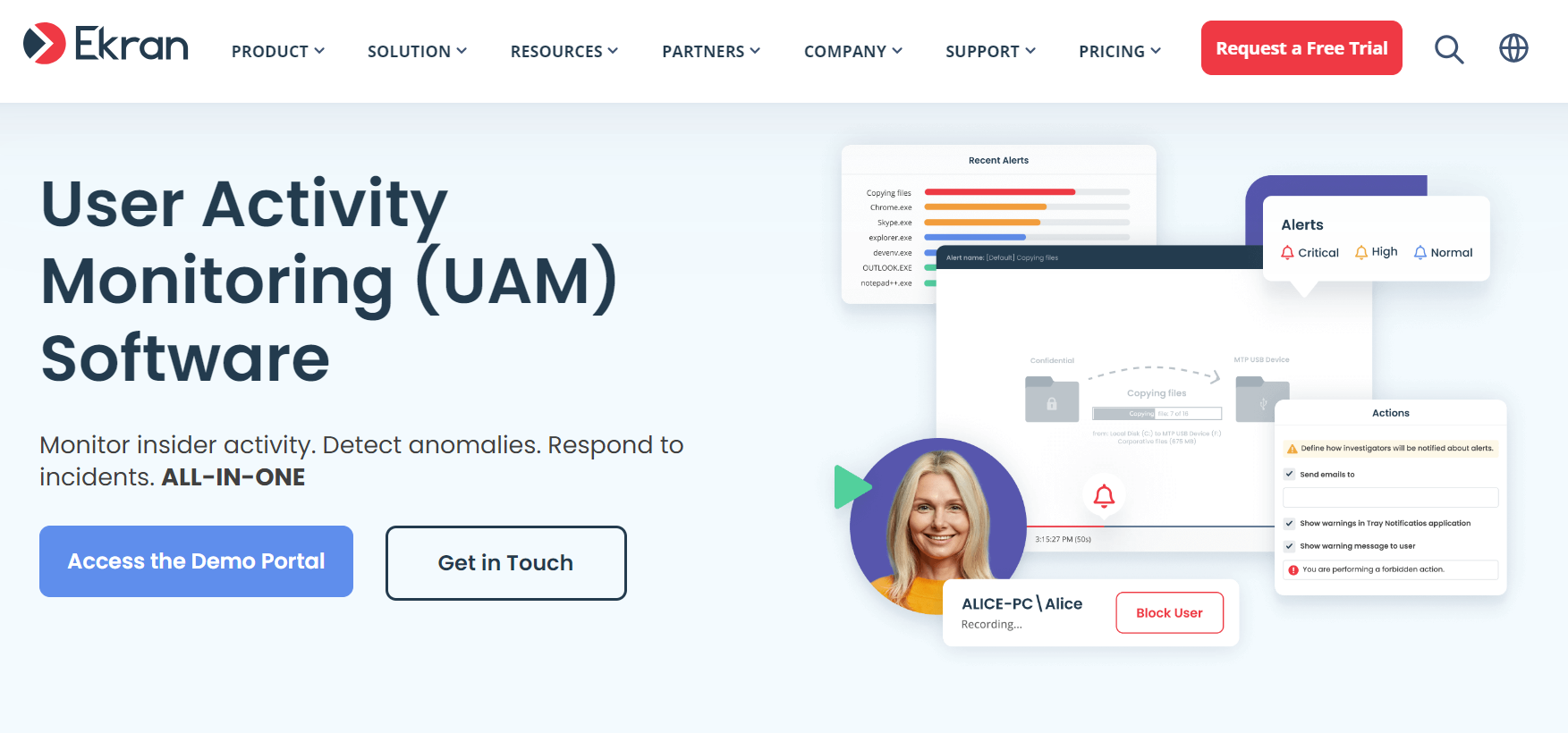
Ekran System (soon to be called Syteca) is a monitoring system that prevents insider risk by increasing visibility over employee activities. Its easy-to-use functionality lets you watch screens, manage remote projects, and collect data to support internal behavioral risk analysis. The tool also integrates seamlessly into existing systems for improved HR workflows.
Best for
Companies looking to automate HR workflows and increase internal security.
Customer review
“Overall, Ekran Software’s RDS Recording application has exceeded our expectations. It’s reliable, efficient, and essential for any organization serious about security and monitoring in an RDS environment.”
6. Suridata

Suridata is a complete SaaS security tool that monitors user activity across all your SaaS apps and provides real-time alerts if suspicious behavior occurs. With rich insights, you can activate the proper workflows and ensure your team can mitigate any SaaS vulnerability before it is exploited.
Best for
Companies relying on multiple SaaS app integrations.
Customer Review
“One of the things we liked most about Suridata was its ease of deployment. It had API integrations for many common business apps and easy-to-follow documentation for each one. Setup rarely took more than 5-10 minutes per app.”
7. Data Resolve
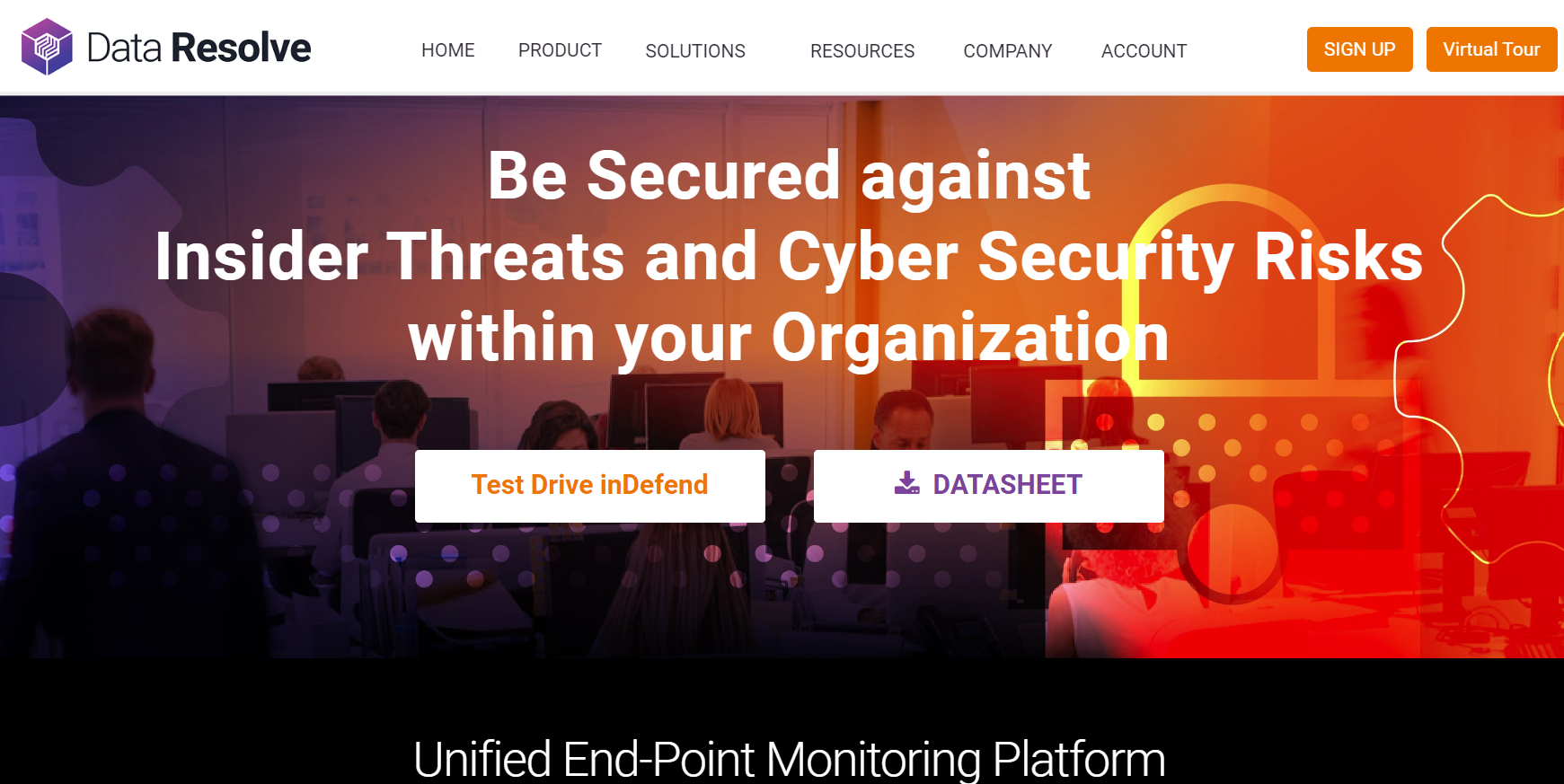
Data Resolve focuses on data leak prevention. It offers enterprise-grade monitoring that covers workstations, cloud apps such as Office 365 and emails, and hardware devices such as local printers. The platform ensures you have full visuals of your confidential data, where it sits, and when and where it moves.
Best for
Monitoring data usage across various internal and external channels.
Customer review
“My overall experience is excellent. It is easy to use, very light, and working. Provides robust data leak protection & comprehensive monitoring tool desksight.ai feature is also a very nice and productive tool.”
Transacting Online in Full Confidence
User activity monitoring may initially sound invasive, but it can protect individual users and businesses from large-scale data leaks and their endless consequences when done correctly.
If you are looking for a tool to protect your website from brand scams or impersonation attacks, Memcyco can help. Memcyco’s Digital Risk Protection (DRP) solution continuously monitors user activity on your website, detecting suspicious behavior and alerting you in real-time. It also offers real-time insights into identity-based risks to improve visibility into every attack, bad actor, and individual victim. Explore more here.



















