In today’s ever-changing threat landscape, organizations face the daunting task of keeping up with cybersecurity risks. Threat detection plays a crucial role in safeguarding businesses against these threats.
However, staying ahead of the game is no easy feat. For businesses, this means grappling with budget allocation and aligning security priorities with business needs. 2023’s surveys suggest that 52% of organizations plan on increasing IT spending this year, with cybersecurity being a top priority.
We will delve into the key factors driving the changes in threat detection in 2023 and provide you with the essential insights to navigate the shifting landscape effectively.
Threat Detection Techniques
Threat detection involves analyzing an organization’s security perimeter to identify vulnerabilities that could compromise the network. Various techniques come into play, including:
- Harnessing Threat Intelligence: This technique entails examining data from past attacks and comparing it with enterprise data. By looking beyond the organization’s perimeter, this approach involves scanning the web and even the dark web to uncover attack behavior and potential avenues that malicious actors may exploit.
- Behavior Analytics: Leveraging threat detection software, this technique focuses on studying the baseline behavior of users. When any abnormal activities occur, they are promptly detected, allowing for swift action.
- Intruder Traps: These are like honey-pots strategically placed by the security team to lure attackers and gather intelligence on their attack plans.
- Threat Hunts: Security analysts proactively search for potential attackers across the network, endpoints, and technology infrastructure.

10 reasons why threat detection is changing in 2023
1. The Ever-Evolving Landscape
In the past, security experts relied on databases containing signatures of known threats. However, this approach is becoming less effective with the rapid emergence of new vulnerabilities. As an illustration, a staggering 450,000 new malware instances are registered daily in 2023. To combat this challenge, modern tools have emerged, integrating artificial intelligence (AI) and global threat intelligence services.
These tools include:
- Endpoint Detection and Response (EDR): An advanced version of antivirus applications, EDR collects and analyzes data on endpoint device health to identify threats. It provides historical visibility of attacks and offers AI-derived threat mitigation steps.
- Network Detection and Response (NDR): NDR platforms utilize AI to track baselines and identify suspicious network communication behavior that threatens the network and connected devices.
- Extended Detection and Response (XDR): XDR is a Security-as-a-Service (SaaS) based threat detection and incident response tool. It employs robust AI and enhanced automation capabilities, collecting security information from multiple sources beyond just endpoints.
- Managed Detection and Response (MDR): MDR eliminates the need for in-house management by outsourcing detection and monitoring to dedicated service providers.
2. The Mounting Volume of Data
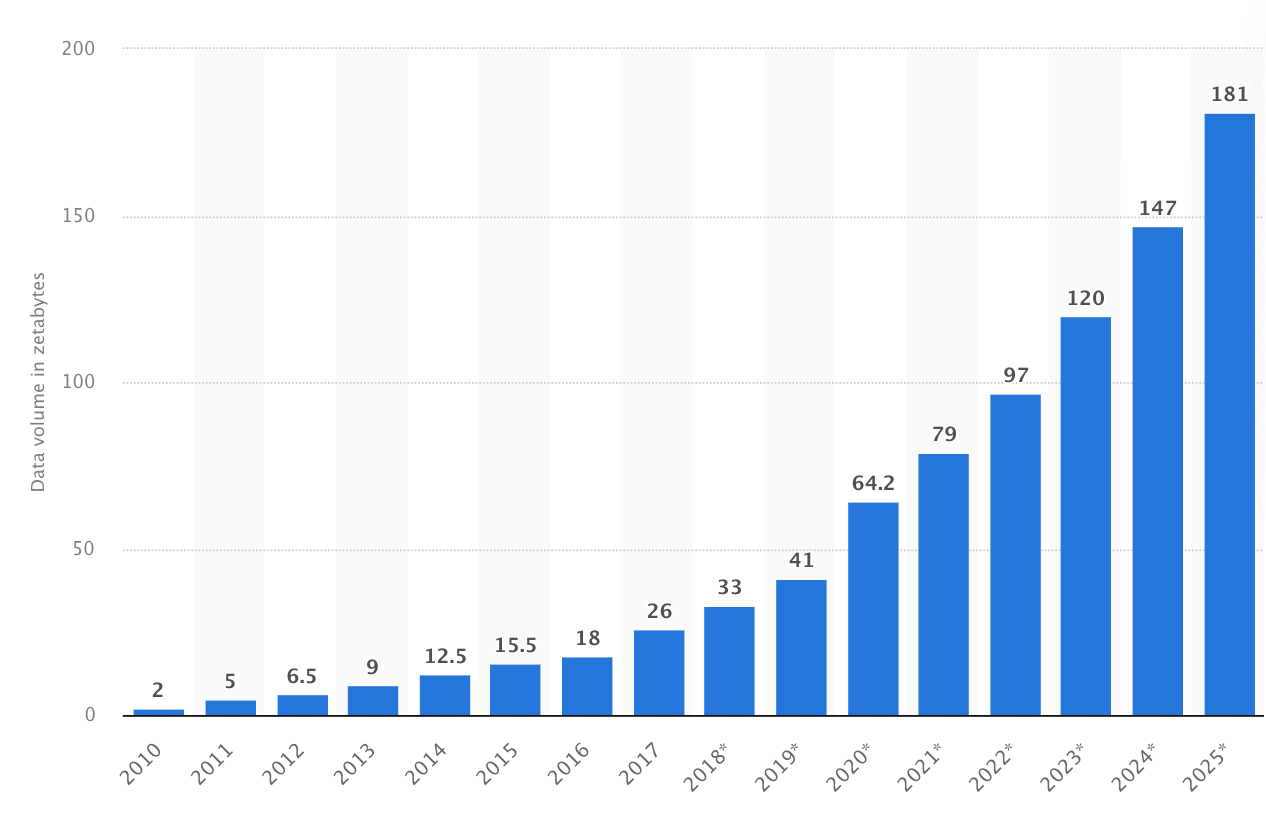
Source: Statista (Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2020, with forecasts from 2021 to 2025)
In recent years, the volume of data has surged exponentially, surpassing the number of skilled professionals available to analyze it. A 2023 survey revealed that 64% of security professionals witnessed an increase in the volume of alerts, with 48% of engineers and analysts reporting a growth rate of up to five times within the same period. Threat detection solutions must prioritize and contextualize alerts efficiently to address this challenge.
3. The Complexity of IT Environments
Today’s IT landscape encompasses diverse elements such as cloud computing, mobile devices, and the Internet of Things (IoT). Unfortunately, the sheer number of threats targeting each endpoint can overwhelm organizations and lead to false positives. Consequently, CISOs must focus on isolating relevant data by employing advanced tools and techniques.
4. Technological Advancement
Advancements in AI, Machine Learning (ML), Big Data, and User and Entity Behavior Analytics (UEBA) are revolutionizing threat detection. AI-based solutions can identify patterns that indicate potential threats and automate response mechanisms. ML enables systems to learn from mistakes, minimizing false positive alerts over time. Big Data consolidates information from multiple sources and utilizes AI tools to identify vulnerabilities and propose fixes. UEBA specializes in detecting compromised credentials, monitoring unusual activities, and identifying malicious behavior.
5. Real-Time Detection Imperative
With the surge in data, organizations must adopt a proactive approach to threat detection. Hackers leverage AI and machine learning to carry out attacks in real-time, making it crucial for organizations to respond swiftly. Modern technologies merge AI-powered threat intelligence and intrusion traps, enabling real-time threat identification. These solutions scan vast datasets and promptly identify potential risks, allowing organizations to remain vigilant and continuously alert users to suspicious behaviors.
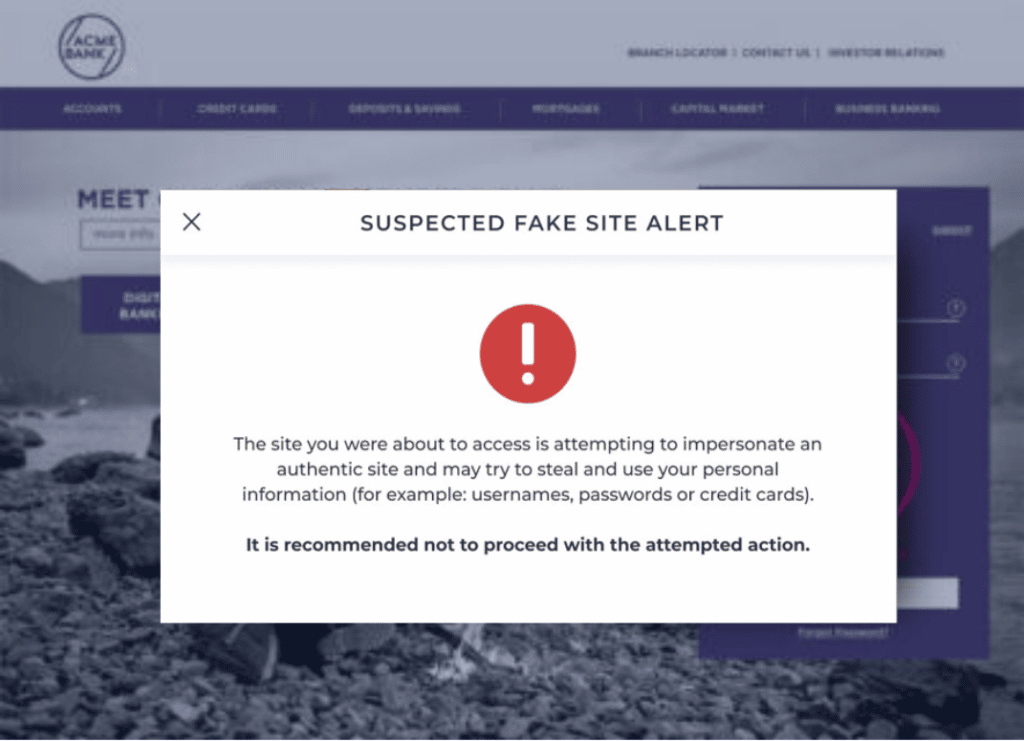
6. Escalating Social Engineering Attacks
Social engineering attacks leverage psychological manipulation to deceive users and extract sensitive information. In 2022, IBM revealed these attacks proved more successful than the average data breach, taking companies nearly nine months to identify and contain.
As cyberattacks become more sophisticated, they have found ways to bypass Multi-Factor Authentication (MFA) measures, such as employing tactics like man-in-the-middle attacks and utilizing “short-lived domains.” These deceptive domains are designed to remain active for only a brief period, usually a couple of hours. This duration is long enough to deceive unsuspecting customers and trick them into falling for fraudulent activities.
To combat this problem, Memcyco has developed an innovative solution: a visual digital watermark. This cutting-edge technology enables all end-users to verify the authenticity and legitimacy of a website. By incorporating a visual marker unique to each website, users can easily distinguish between genuine websites and fraudulent ones. This approach empowers individuals to make informed decisions and avoid falling victim to malicious online activities.

7. The Rise of Sophisticated Impersonation Attacks
Impersonation attacks exploit victims’ trust in reputable organizations. Scammers impersonate government entities, charities, executives, and brands, with banks and financial services being popular targets. Traditional threat detection platforms often fail to detect these attacks since they occur through legitimate channels like email and social media. Solutions like Memcyco’s Proof of Source Authenticity provide foolproof seals of genuineness for brands’ websites and enable prompt mitigation actions against impersonation attacks.
8. Regulatory Requirements
Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) impose strict guidelines on how organizations handle personal data. Compliance with these regulations is critical, as non-compliance can result in hefty fines. AI, ML, and behavior analytics enable companies to meet these regulatory obligations by providing visibility, audibility, and robust documentation of processing activities.
9. The Rise of Insider Threats
Insider incidents have significantly increased in recent years, with 66% of organizations considering malicious insider attacks or accidental breaches more likely than external attacks. Dealing with insider threats necessitates implementing stringent access controls, data encryption, and advanced network analysis capabilities. Analytics powered by AI, ML, UEBA, and Big Data are vital for swiftly identifying and neutralizing breaches.
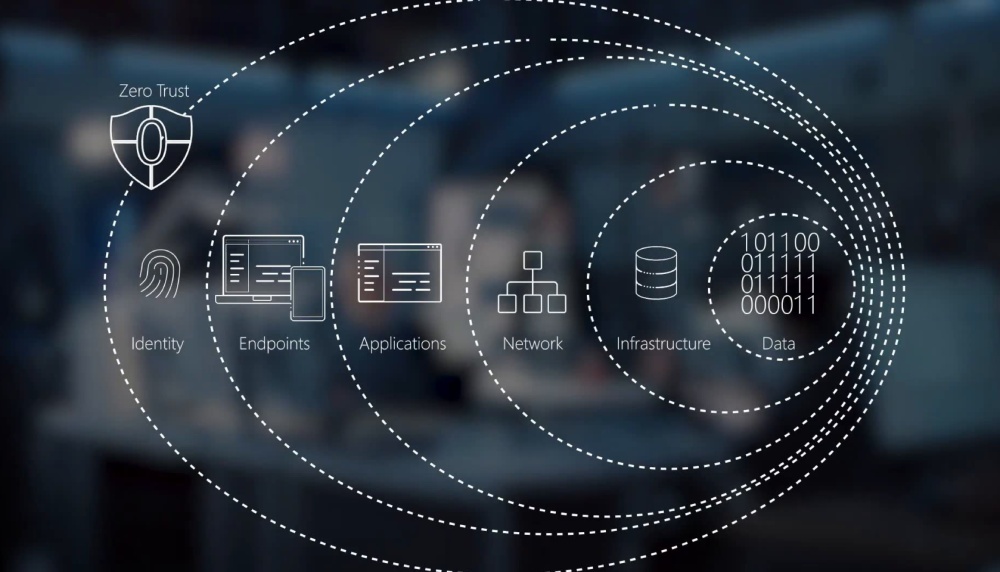
10. Embracing Zero-Trust Security
Cybercriminals often find vulnerabilities to exploit due to the continuous movement of data across various platforms, including SaaS applications, IaaS, data centers, and IoT devices. The concept of Zero Trust emphasizes verifying the identity of every user, device, or system before granting access to data. Rigorous event logging and verification processes underpin this approach, ensuring real-time visibility of user identities and credentials. To handle the increasing volume of events, threat detection algorithms need to be constantly improved.
The Road Ahead
Threat detection has come a long way since the days of relying solely on signatures. With the advent of AI, ML, Big Data, and behavior analytics, Organizations have powerful tools at their disposal.
However, the ever-evolving nature of threats necessitates continued innovation. Some of the biggest challenges is protecting your organization and customers against malicious events outside your corporate perimeter, such as brand impersonation.
Memcyco exemplifies this drive for innovation, employing cutting-edge technology to protect brands, secure end-users, and restore digital trust.
Learn more about proactively securing end-users outside your security perimeter with Memcyco.






![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1-300x169.png)








![A Step-by-Step Guide to DORA Compliance [XLS download]](/wp-content/uploads/2025/03/A-step-by-step-guide-to-DORA-compliance_1024x576-1.png)