With personal data or business communications, our vast digital footprint is vulnerable to malefactors.
Consequently, safeguarding sensitive information has become a pressing concern for companies of all sizes. The cost of cybercrime was $8 trillion globally in 2023 and is projected to hit $10.5 trillion by 2025. This alarming statistic emphasizes the escalating threat and the critical need for robust cybersecurity measures.
That’s where the US National Institute of Standards and Technology (NIST) steps in to offer a solution for complex data security challenges with NIST SP 800-53.
What is NIST SP 800-53 compliance, and why is it Important?
The National Institute of Standards and Technology (NIST) is the US federal agency responsible for developing standards to enhance the nation’s technological competitiveness. One of NIST’s key contributions to cybersecurity is the Special Publication (SP) series, which includes SP 800-53.
NIST SP 800-53 provides a detailed set of security controls organized into families. Although it was initially developed for US federal agencies, NIST SP 800-53 has gained popularity in both public and private sectors, addressing different aspects of information security and privacy.
For example, the “Access Control” family includes controls that are useful for organizations, such as:
- AC-2: Account Management – Ensure that accounts are created, modified, and disabled or removed securely and timely.
- AC-3: Access Enforcement – Enforces access controls to prevent unauthorized access to data.
NIST SP 800-53 compliance holds significant importance for organizations because it serves as a crucial safeguard for data and information systems, shielding them from potential cyber threats and unauthorized access. Compliance also plays a pivotal role in meeting legal and regulatory obligations, ensuring organizations do not face legal consequences, fines, or contract losses.
Adhering to NIST SP 800-53 enables effective risk mitigation by providing a robust framework of security controls and best practices. This proactive approach reduces the likelihood of cybersecurity incidents and associated financial losses, enhancing an organization’s reputation, fostering stakeholder trust, and ultimately leading to long-term cost savings.
What are the benefits of NIST SP 800-53 compliance?
1. Enhanced Security Posture
NIST SP 800-53 compliance involves implementing over 300 security controls, resulting in a systematically strengthened security posture. These controls cover management policies, daily operations, and technical infrastructure.
2. Streamlined Regulatory Alignment
Achieving NIST compliance provides significant overlap with other major standards like ISO 27001. This alignment offers a streamlined path for demonstrating adherence to multiple frameworks.
3. Proactive Risk Management
Continuous risk assessments mandated by NIST ensure the proactive identification and resolution of control issues before they escalate into major incidents.
4. Optimized Security Spending
NIST SP 800-53 guides organizations in making smart, risk-based investments in security measures. This spending optimization ensures that resources are directed where they are most needed.
5. Customer Trust and Confidence
NIST compliance serves as verified proof that an organization adheres to stringent government standards for data protection. This commitment to security enhances customer trust, as clients feel assured that their personal information is secure.

Who is NIST SP 800-53 Compliance for?
NIST SP 800-53 compliance is relevant for a broad spectrum of organizations and individuals handling sensitive information or seeking to bolster their cybersecurity measures:
- Federal Agencies – Mandatory for federal agencies, ensuring a standardized information security approach across government systems.
- Government Contractors – Required for organizations contracting with federal agencies, adhering to NIST SP 800-53 standards.
- Private Sector Organizations – Organizations handling sensitive data, financial information, or intellectual property
- Healthcare Providers – Ensures security and confidentiality of health records, aligning with broader healthcare compliance regulations.
Moreover, various organizations dealing with sensitive information can voluntarily benefit from the NIST SP 800-53 framework, including:
- Software development companies for handling intellectual property safely.
- Companies managing power grids for risk management.
- Large retail chains to protect customer information and build digital trust.
- Universities to secure academic and research information.
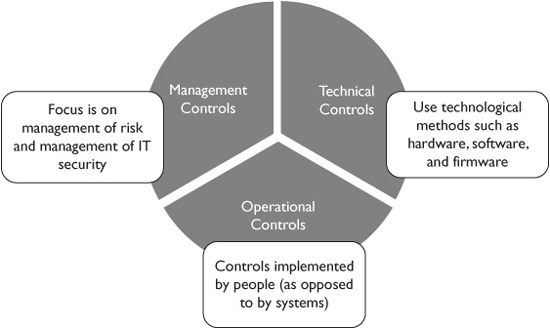
What are the NIST SP 800-53 Security Controls?
NIST SP 800-53 controls are categorized into Management, Operational, and Technical. Combined, these three control types create layered defenses known as “defense in depth.” If one fails, the others still provide protection.
Management Controls
These controls govern information security governance, planning, and management. They ensure security is ingrained in business objectives from the start to influence strategic decisions.
Examples:
- Security policies
- Risk management procedures
- Training programs
- Contingency plans for business continuity
Operational Controls
Instead of relying solely on technology or policies, operational controls focus on people, translating security guidance into day-to-day behaviors and tasks.
Examples:
- Conducting background checks before hiring
- Secure access provisioning
- Proper disposal of retired hardware
Technical Controls
These controls leverage technology to safeguard networks, endpoints, servers, and other infrastructure. The aim is to prevent unauthorized access while allowing seamless access for authorized users.
Examples:
- Encryption
- Multi-factor authentication
- Firewalls
- Endpoint security tools
- Network intrusion detection capabilities
- Memcyco’s website spoofing prevention solution – The only solution that addresses the critical “window of exposure” between the moment a fake website goes live and until it is taken down, Memcyco’s agentless solution issues real-time Red Alerts to users visiting fake sites, provides organizations with complete visibility into the attack, and allows them to take remediating actions quickly. Securing your website’s data helps ensure regulatory compliance.
5 Necessary Steps to NIST SP 800-53 Compliance
With numerous security controls to implement, the journey to full NIST SP 800-53 compliance can become overwhelming. Breaking it down into five manageable steps and seeking expert help can make the process smoother. Here’s how to do it:
Step 1: Get Familiar with Your Data Landscape
Thoroughly explore your organization’s data landscape to identify and classify sensitive information, commonly called the “crown jewels. You need to understand the types of data you handle, where it’s stored, who has access, and its movement patterns.
This initial step lays the foundation of effective security by pinpointing critical assets, facilitating targeted security measures, and prioritizing risks.
Typical examples for online businesses include:
- Customer personally identifiable information
- Payment card data
- Bank account details collected for payouts
- Proprietary business data like financials or product designs
- Employee information like salaries and health records
Actionable Tips:
- Utilize automated tools for data discovery and classification to streamline the process.
- Assign confidentiality, integrity, and availability ratings to assess the impact level if sensitive data is exposed.
Step 2: Uncover Your Risks
This step uncovers operational and technical shortcomings, providing insights into areas that need improvements. Conduct a comprehensive risk assessment spanning people, processes, and technology to identify potential vulnerabilities. This includes analyzing:
- Access management policies
- Endpoint and network safeguards
- Vendor risk management
- Security awareness training completion rates
- Incident response preparedness
Actionable Tips:
- Seek external consultants for unbiased risk reviews, bringing in an outside perspective.
- Regularly update your risk assessments to counter evolving threats.
Step 3: Define Your Compliance Roadmap
Define a detailed NIST alignment strategy, crafting an implementation roadmap over a 1-3 year timeframe. Identify milestones by priority, including quick wins for high-risk gaps, long-term engineering efforts, security policy updates, and adopting new tools.
Actionable Tips:
- Prioritize fixes based on data sensitivity and risk levels to maximize impact.
- Regularly update the roadmap to adapt to changing circumstances or emerging threats.
Step 4: Make Security Visible Company-Wide
Execute the detailed roadmap, ensuring the adoption of security controls across all levels of the organization. Foster security as a cultural mindset through awareness campaigns that utilize visuals and incentives to encourage training completion.
Actionable Tips:
- Collaborate with non-IT teams to emphasize security as an organization-wide commitment.
- Conduct practical sessions that include simulated phishing tests and short instructional videos.
- Display posters and digital signages where they are visible to employees.
- Use a website spoofing prevention solution that displays a visible mark assuring users they are on your authentic website.
Step 5: Measure and Optimize
Your task isn’t complete after implementing NIST SP 800-53 security controls. Schedule periodic assessments to ensure controls function as expected and identify issues like waning compliance due to neglect. You don’t need to start from scratch; instead, pinpoint incremental improvements to fortify defenses and demonstrate due care.
Actionable Tips:
-
- Create a NIST SP 800-53 control matrix mapping inventory for efficient assessments, focusing on critical controls more frequently.
- Use assessment results to inform updates and optimizations to your security controls.
Secure Your Data with NIST SP 800-53 and Memcyco
With the increasing threats of cyber attacks, the demand for robust solutions has never been more urgent. Compliance with the NIST SP 800-53 framework bolsters security and data protection and increases an organization’s preparedness against evolving cybersecurity threats. However, innovative and specialized solutions are often required given the continuous emergence of new threats.
While NIST SP 800-53 addresses broader data security concerns, Memcyco’s solution acts as a specialized guardian, ensuring real-time protection against the dangers of website spoofing—a critical aspect often left vulnerable by conventional measures. The end-to-end solution embeds an active tracking sensor in the company’s authentic site that ensures immediate attack detection and alerts, and features in-depth forensics and innovative mitigation measures.
Don’t just meet regulations; surpass them by protecting your data with NIST SP 800-53 and Memcyco. Schedule a demo today.